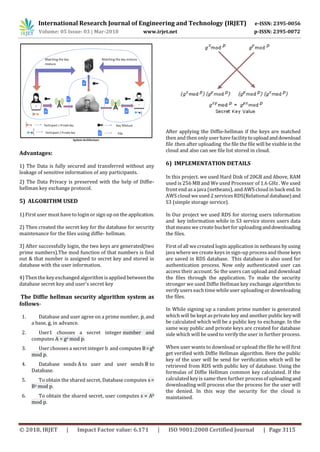
This document proposes a key exchange privacy preserving technique for cloud computing using Diffie-Hellman algorithm. It discusses issues with existing cloud security methods like data encryption. The proposed system uses Diffie-Hellman key exchange between users and cloud database to securely store and access files. When a user wants to store or access a file, prime numbers are used to generate secret keys for the user and database. These keys are exchanged and matched using Diffie-Hellman to authenticate the user before allowing file operations. This approach securely shares secret keys to preserve privacy in cloud storage and transfers without leaking sensitive user information. The system was implemented using Java and Amazon Web Services for cloud storage and database.