The document discusses the development of a LAN-based communication tool called IP Messenger, which facilitates instant messaging and file sharing among users within an organization without the need for internet access. The application, built using C# and a client-server architecture, allows users to chat and share files securely while providing features like chat logs and a user-friendly interface. It also reviews network traffic classification using machine learning and emphasizes the importance of communication technology in enhancing collaboration and efficiency.



![IDL - International Digital Library Of
Technology & Research
Volume 1, Issue 6, June 2017 Available at: www.dbpublications.org
International e-Journal For Technology And Research-2017
IDL - International Digital Library 5 | P a g e Copyright@IDL-2017
Physical design represents physical behavior of the
system. Physical design is related to the input and
output process of the system. Physical design will
gives how to input the data into system, how can it is
authenticated, how does it is processed and how it is
displayed. The requirement of the physical design is:
Input requirements, Output requirements,
Storage requirements, Process requirements,
System Control and back up or recovery is
required to design physical design.
The physical design is categorized into three sub task.
User interface
Data design
Process design
User Interfaceis designed to describe how user will
give input to the system and how system process the
information and return back to the users.
Data design is concerned in representing about how
data represented in the system do and how those data
are stored into the system.
Process design concerned about the movements of
the data in the system, and how and where these data
are validated. Also concerned about the how data is
secured and transformed through and the system and
out of the system.
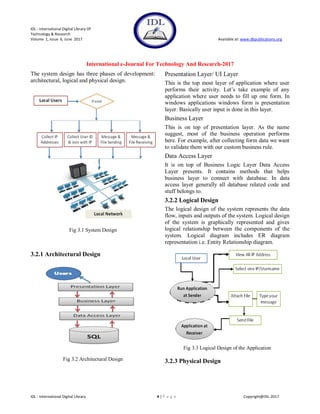
IV. SYSTEM ARCHITECTURE
The IP Messenger and the File Transfer Interface
Design works as follows
List form: In this form, all the computer
names and IPs of the systems connected to a
network that runs the IP Messenger and File
Transfer application are enlisted. List Form
contains the IPs and names of all the system
connected to the LAN which runs the
application otherwise the application not
enlist the IPs and Computer names of those
system which not run the application. These
names and IPs can later be used for
communication with the help of mouse event,
or in simple language: a click or a double
click.
Chat form This form is called only when an
element is selected from the List form. In this
form, a connection is created between the
host system and the selected system with the
help of a socket.
When the Connect button is clicked or a
name is double clicked, the chat form is
initialized with a connection between the host
and the client machine.
Log files is a concept that has been added to
the application so that you can track each and
every transaction over the LAN between
machines that run this Application and
communicated among each other.
V. CONCLUSION
This paper is a survey of how to build an Instant
messaging over Ethernet LAN without having any
Internet connection and also having a portable
application for transferring files over Ethernet LAN.
The advantage of this application is used within an
organization between employees regardless of having
Internet connection and need to open the mail for file
transferring or exchanging the files over USB devices
or texting with each other.
VI. REFERENCES
[1] Kazuki Ueda, TatsushiKikutani, and Takahiro Yakoh
―Parallel Implementation of Real-Time
Communication and IP Communication by using
Multiple Ring Buff ers‖
[2] Marius Marcu and Adela Bascacov ―Tariff System
Design for IP Conference Communication Solutions‖](https://image.slidesharecdn.com/tr00119-170625142314/85/IP-Messenger-And-File-Transfer-over-Ethernet-LAN-5-320.jpg)
![IDL - International Digital Library Of
Technology & Research
Volume 1, Issue 6, June 2017 Available at: www.dbpublications.org
International e-Journal For Technology And Research-2017
IDL - International Digital Library 6 | P a g e Copyright@IDL-2017
[3] Lilin Zhang, Ali Tizghadam, HadiBannazadeh and
Alberto Leon-Garcia ―Iterative Traffic Engineering in
the Data Plane of Multimedia IP Communication‖
[4]
http://csharp.netinformations.com/communications/cs
harp-socket-programming.htm
[5] N. Wang, K. H. Ho, G. Pavlou, and M. Howarth, ―An
overview of routing optimization for internet traffic
engineering,‖ 2008.
[6] A. Tizghadam and A. Leon-Garcia, ―On Robust
Traffic Engineering in Transport Networks.‖ in
GLOBECOM. IEEE, 2008, pp. 2372–2377.
[7]―AGraphTheoreticalApproachtoTrafficEngineeringand
NetworkControl Problem.‖ in International
Teletraffic Congress. IEEE, 2009, pp. 1–8. [4] ——,
―Autonomic Traffic Engineering for Network
Robustness,‖ IEEE J.Sel. A. Commun., vol. 28, no. 1,
pp. 39–50, Jan. 2010.
[8] Intel82574GbEControllerFamilyDatasheet.
Intel,2011.
[9] J.-D. Decotignie.Ethernet-based real-time and
industrial communications. Proceedings of the IEEE,
93(6):1102– 1117, 2005.
[10] B. Feng, D. Ghosal, and N. Kannappan.Impact of
ATM ABR controlontheperformanceofTCP-Tahoe
and TCPReno. IEEE Global Telecommunications
Conference, GLOBECOM ’97, 3:1832–1837,
November 1997.](https://image.slidesharecdn.com/tr00119-170625142314/85/IP-Messenger-And-File-Transfer-over-Ethernet-LAN-6-320.jpg)