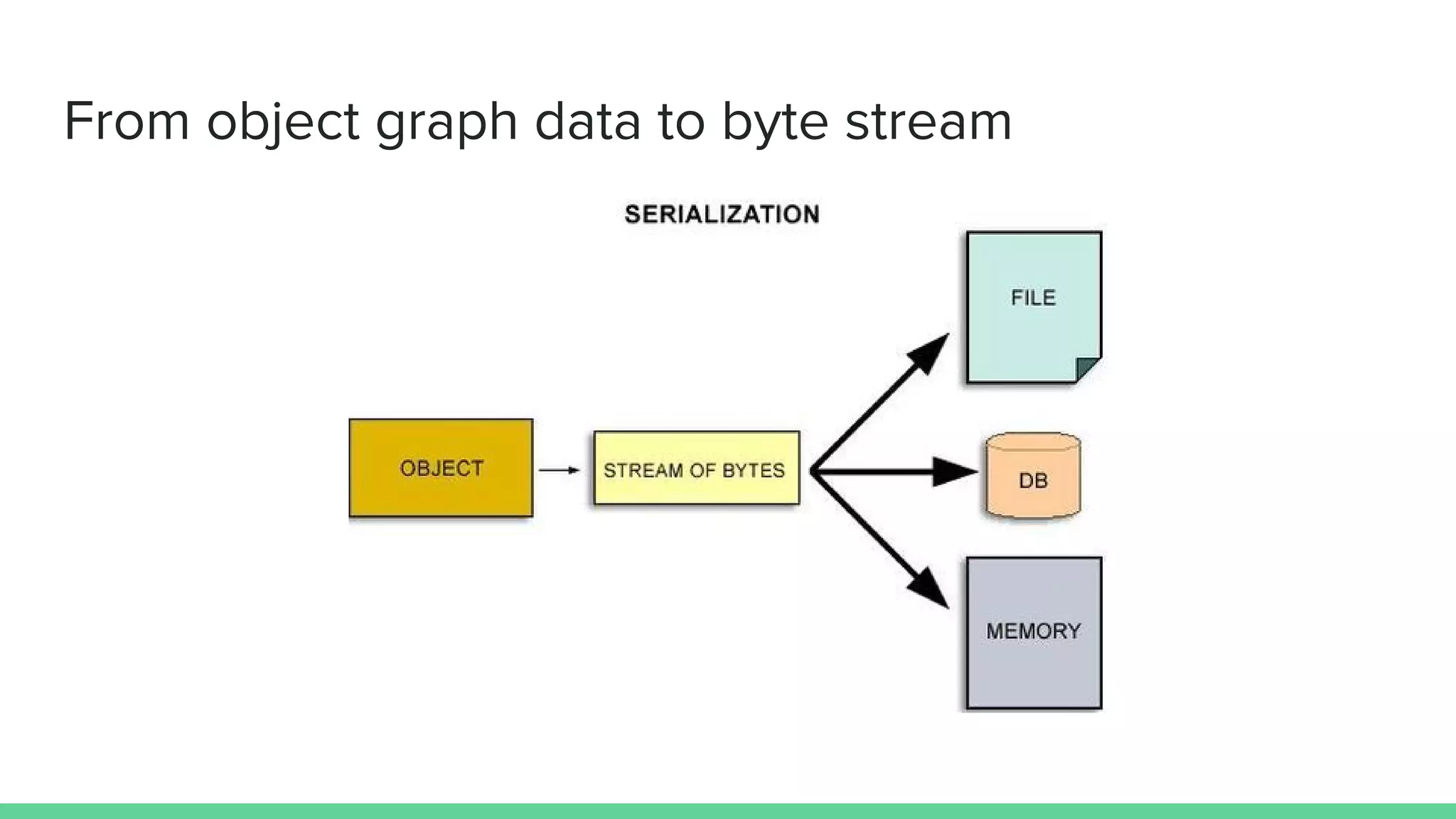
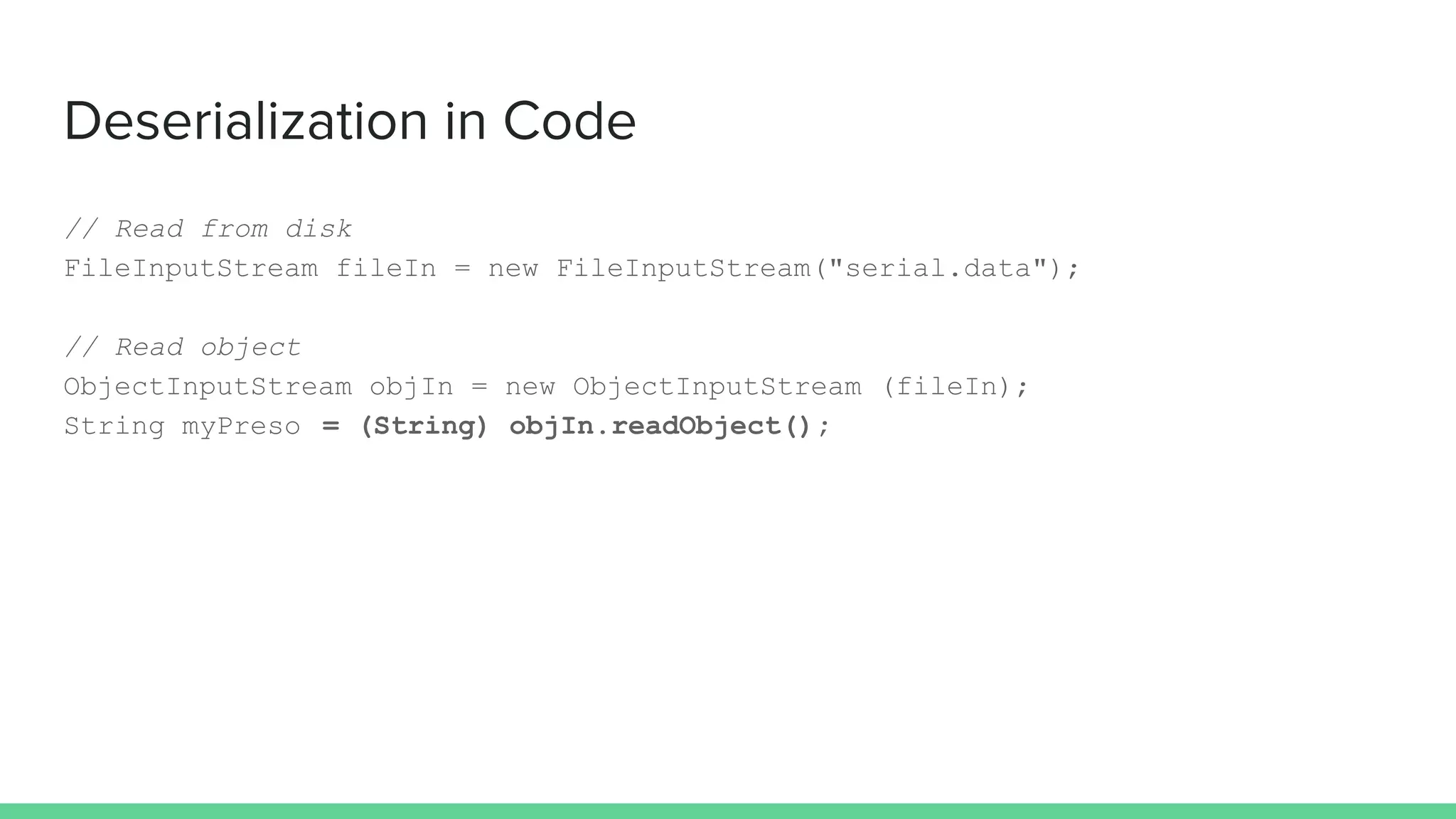
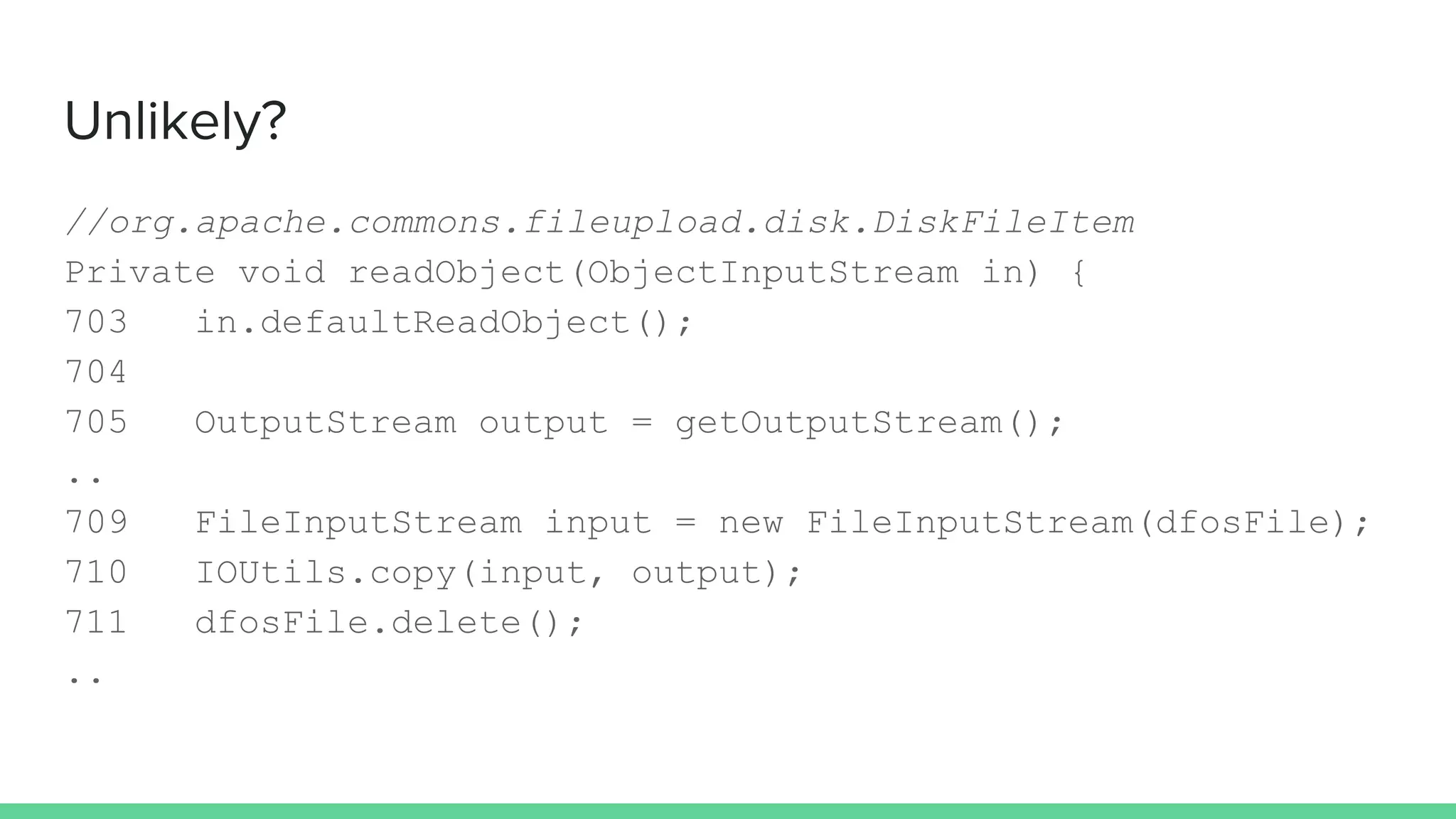
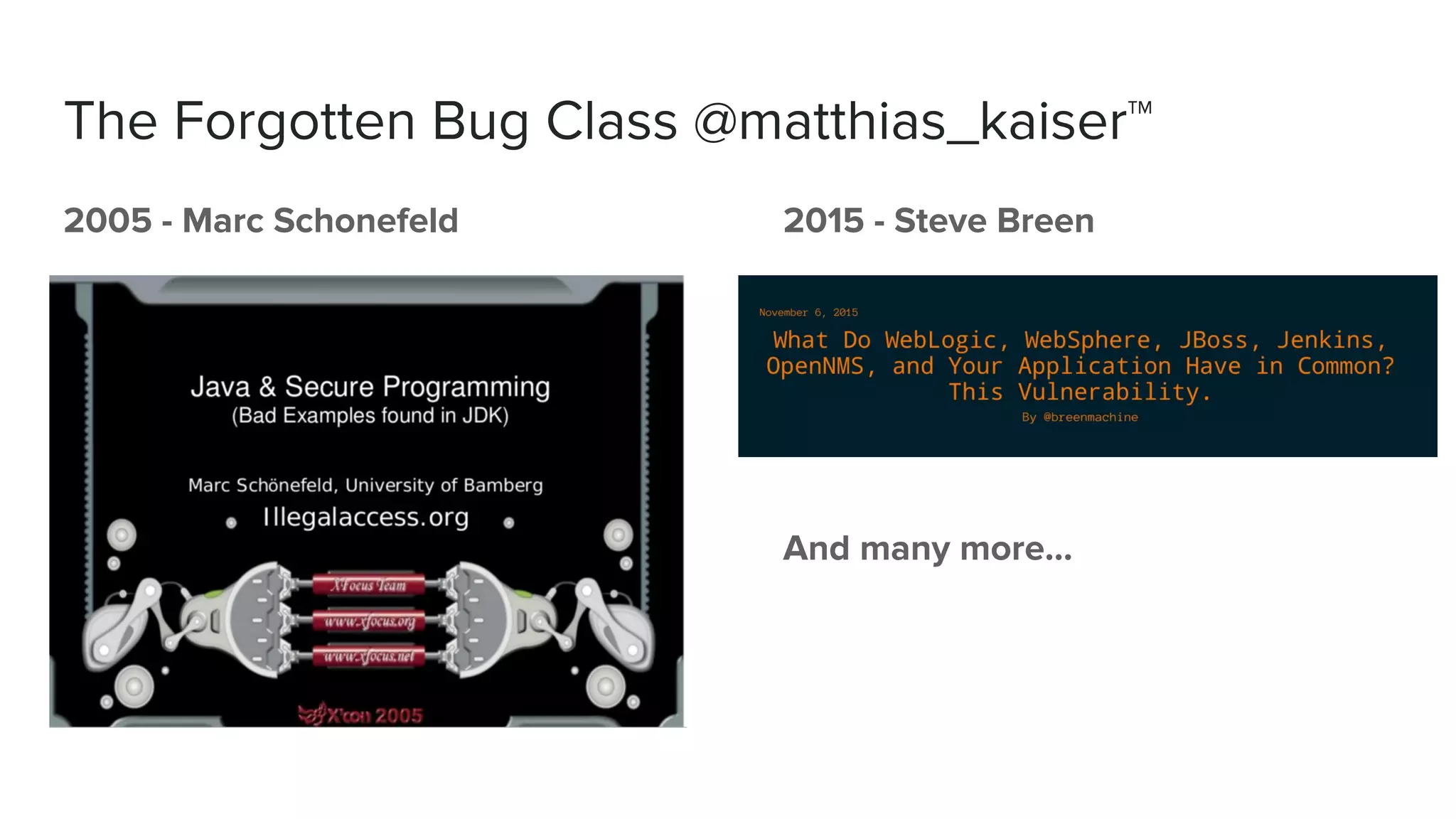
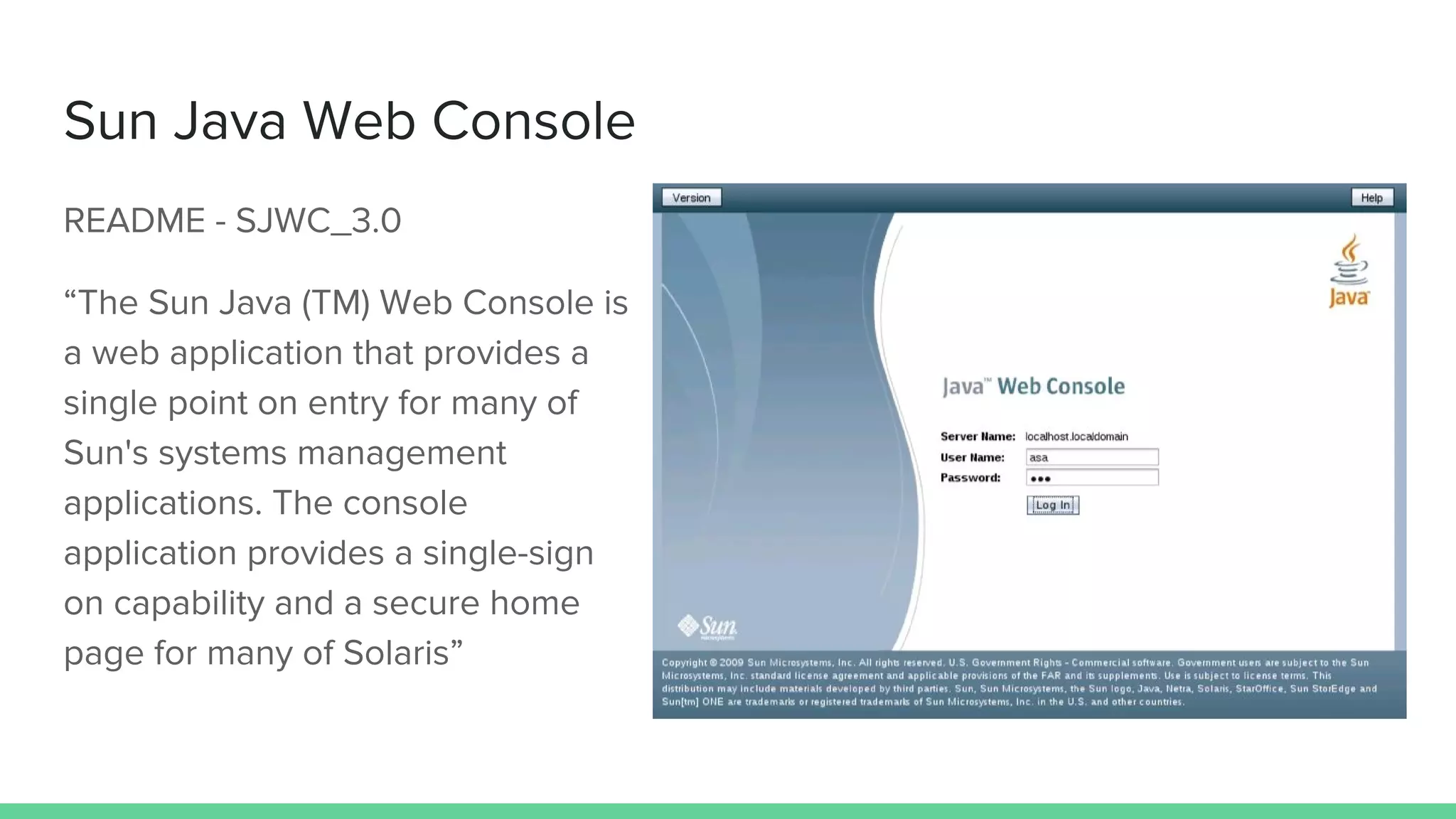
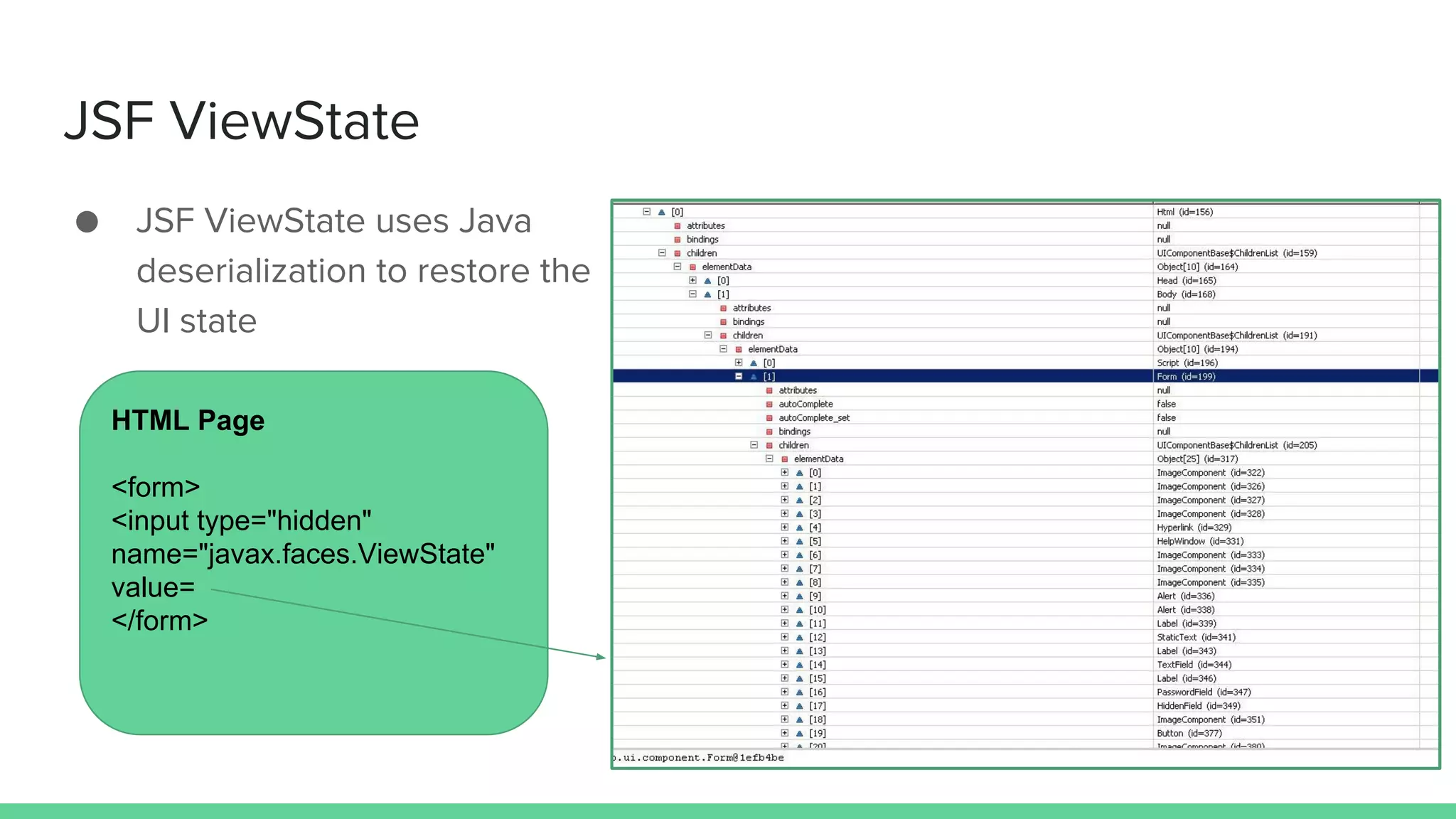
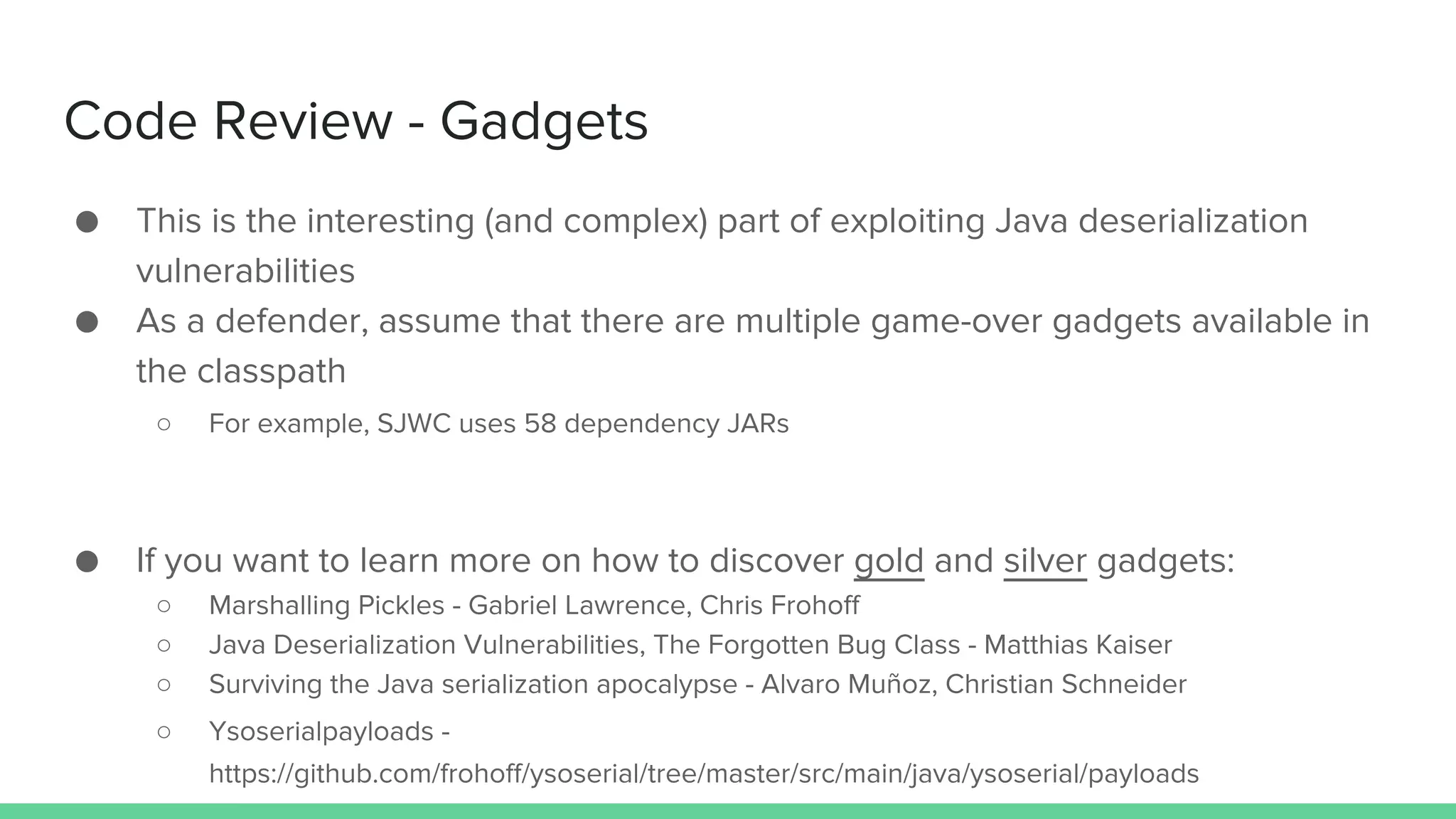
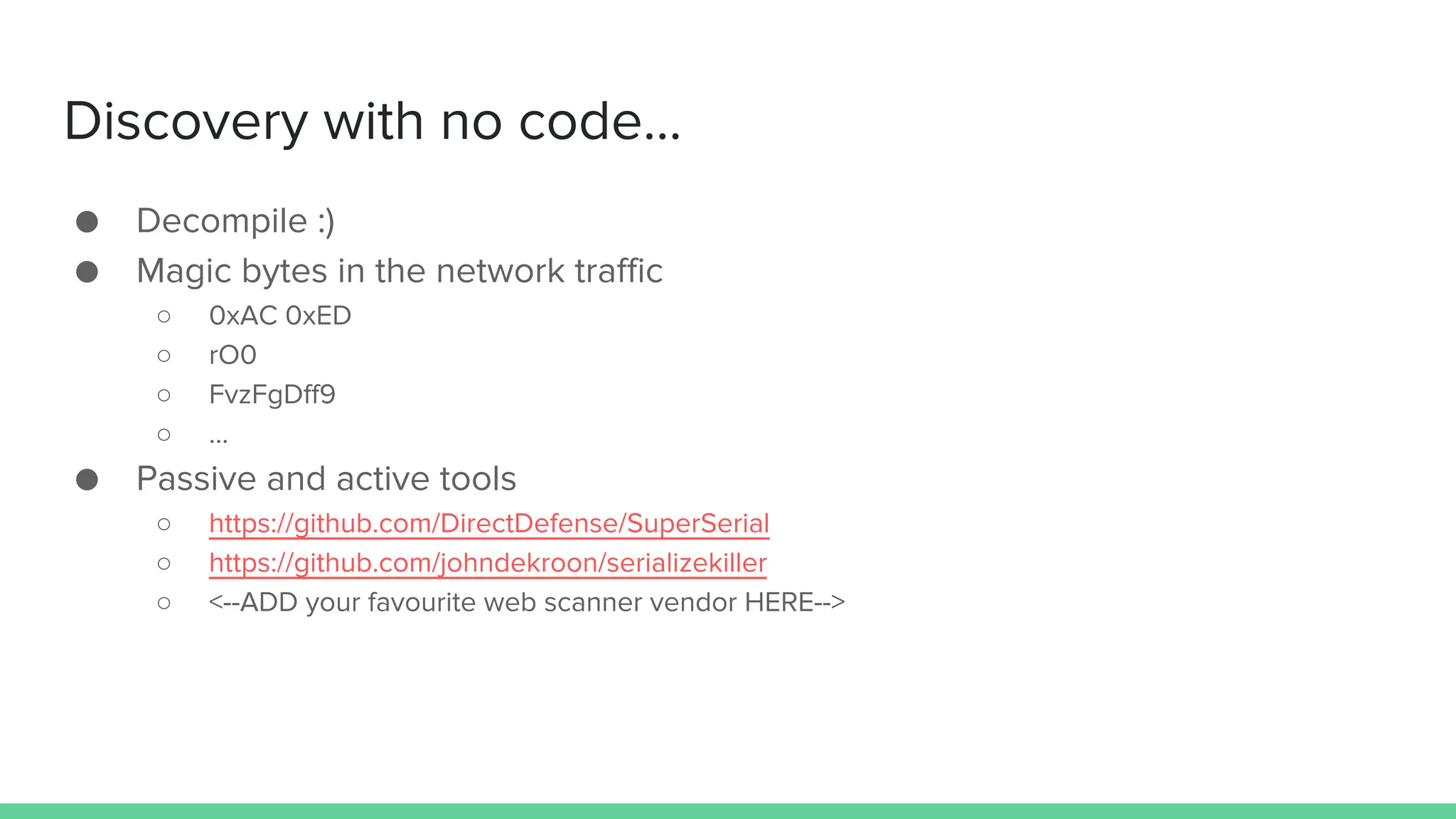
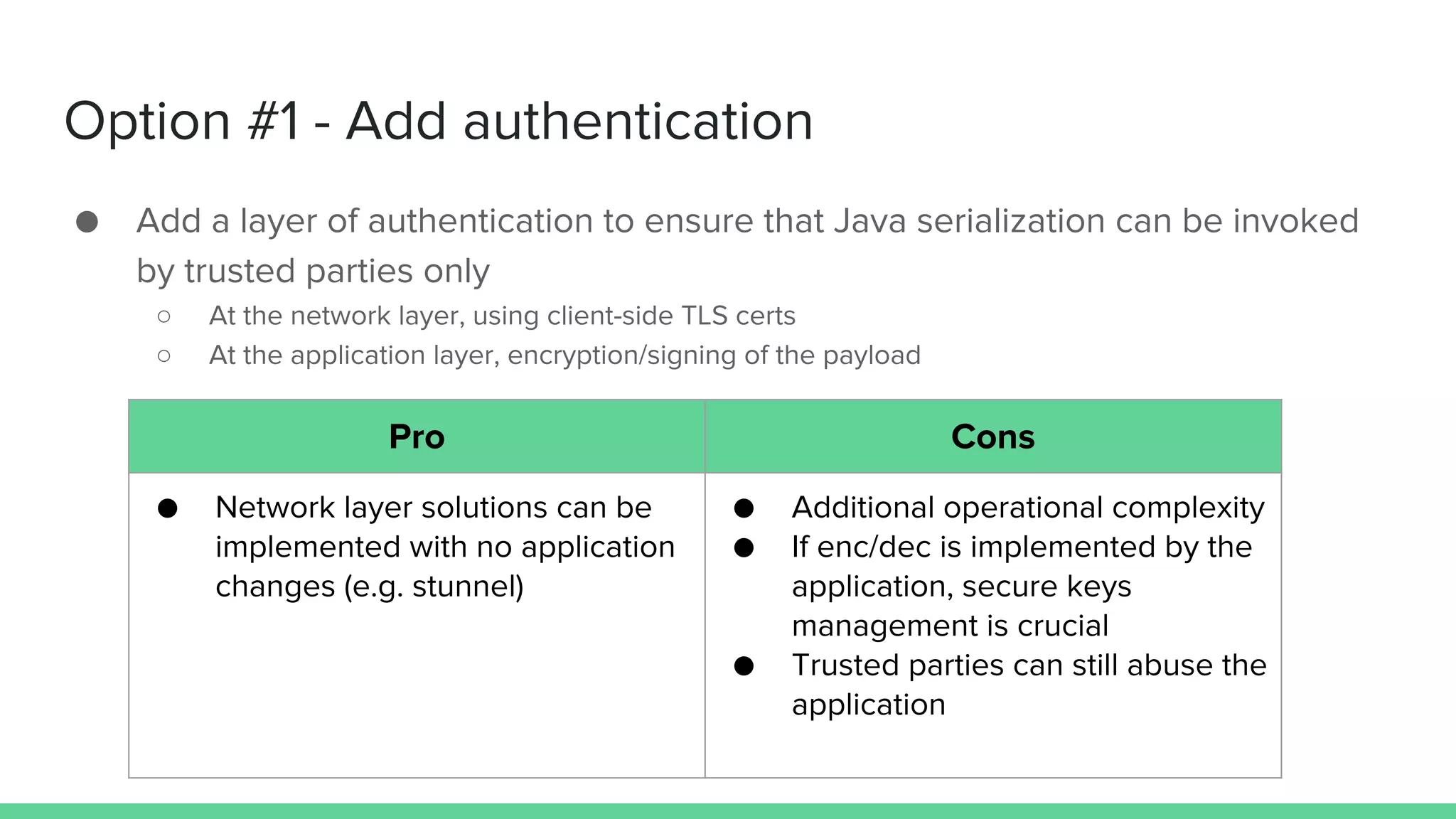
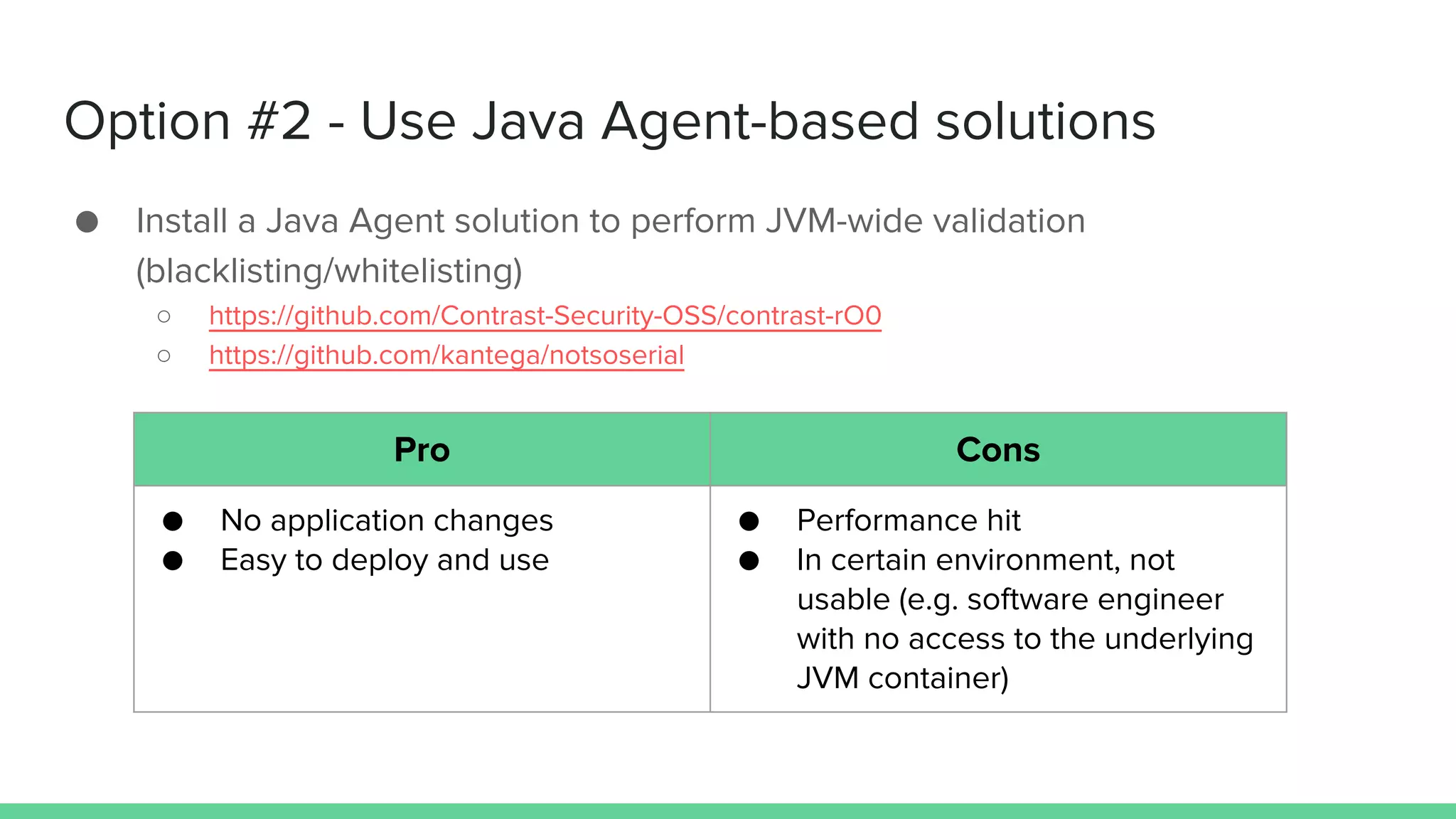
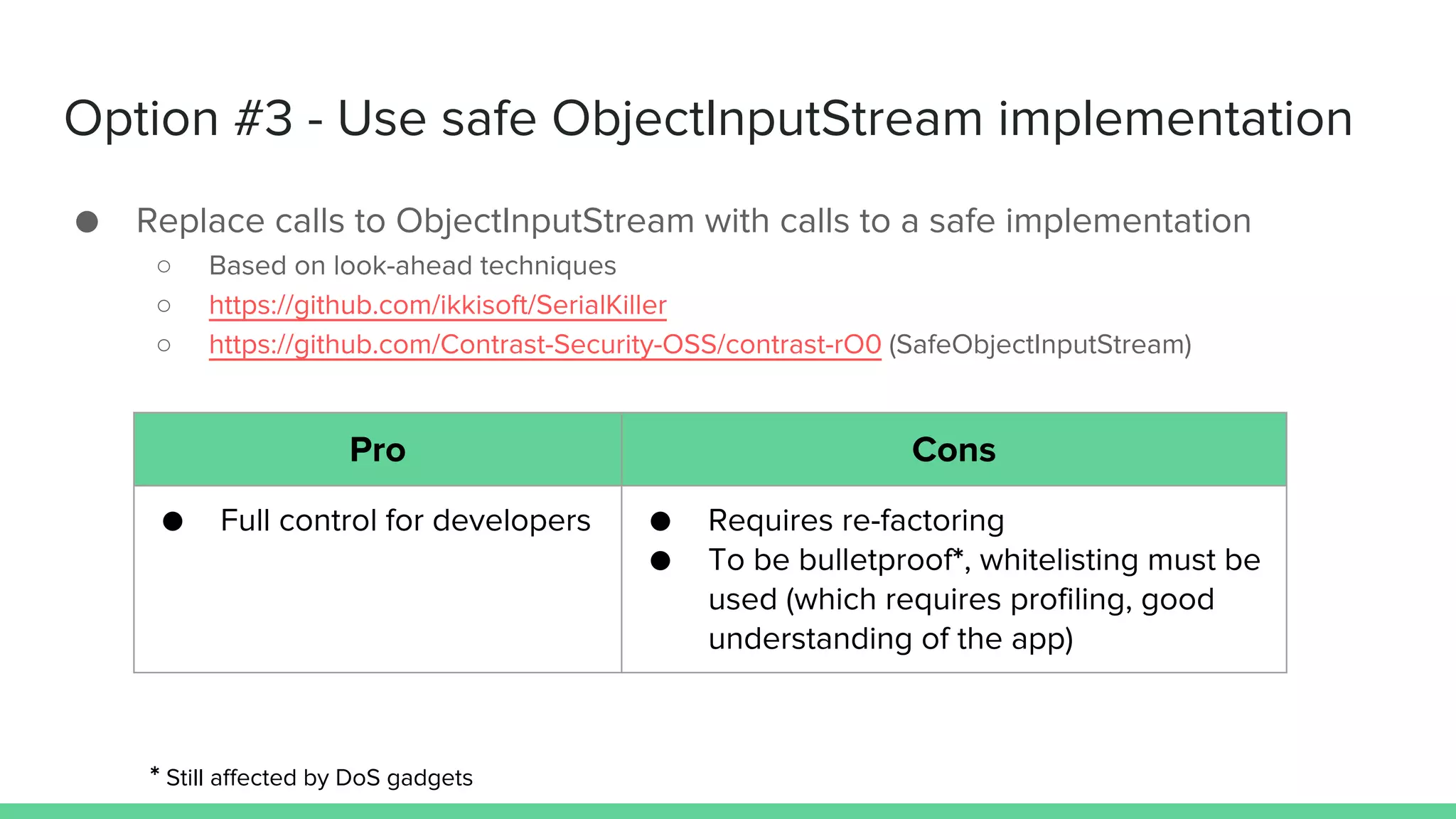
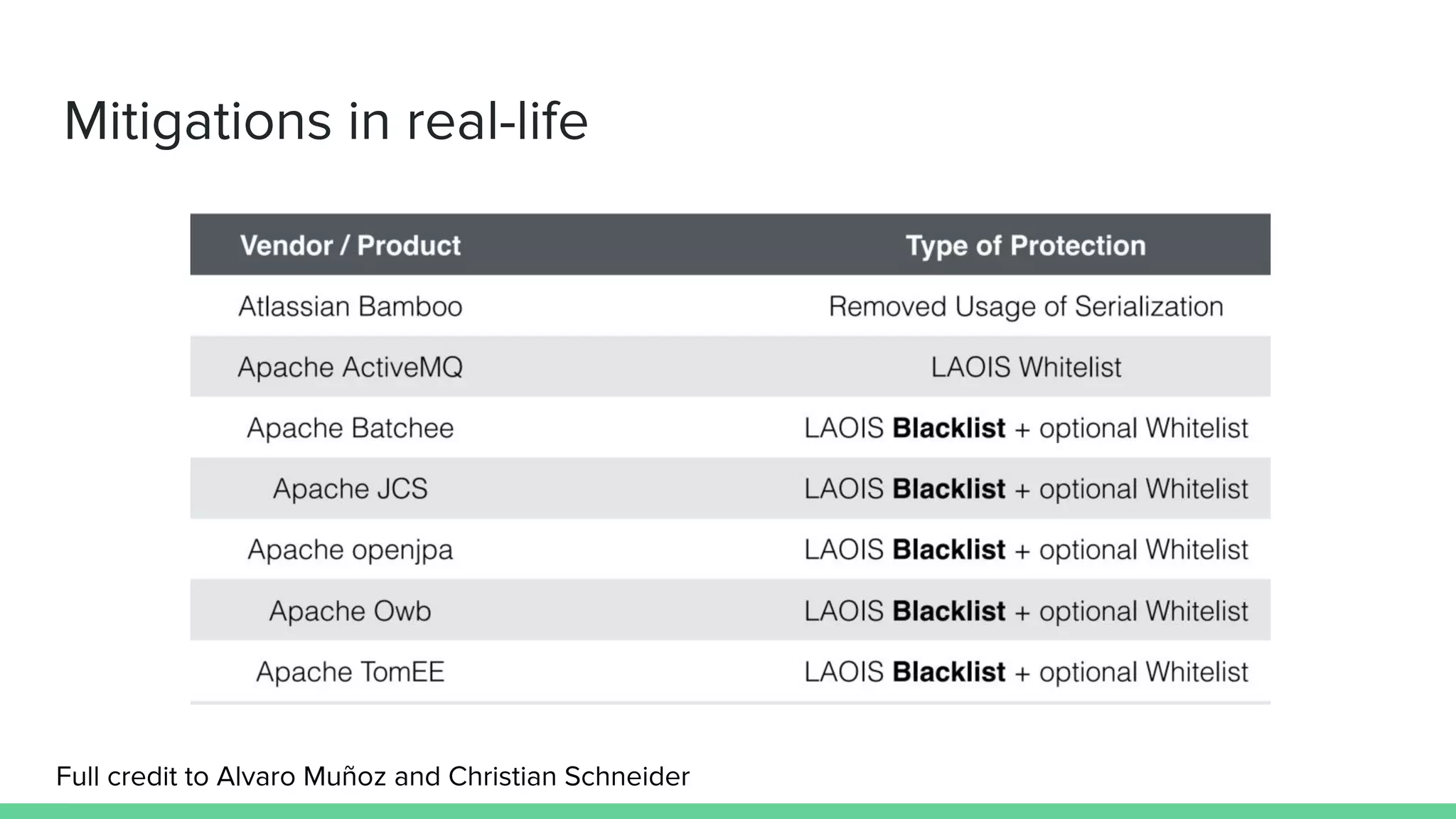
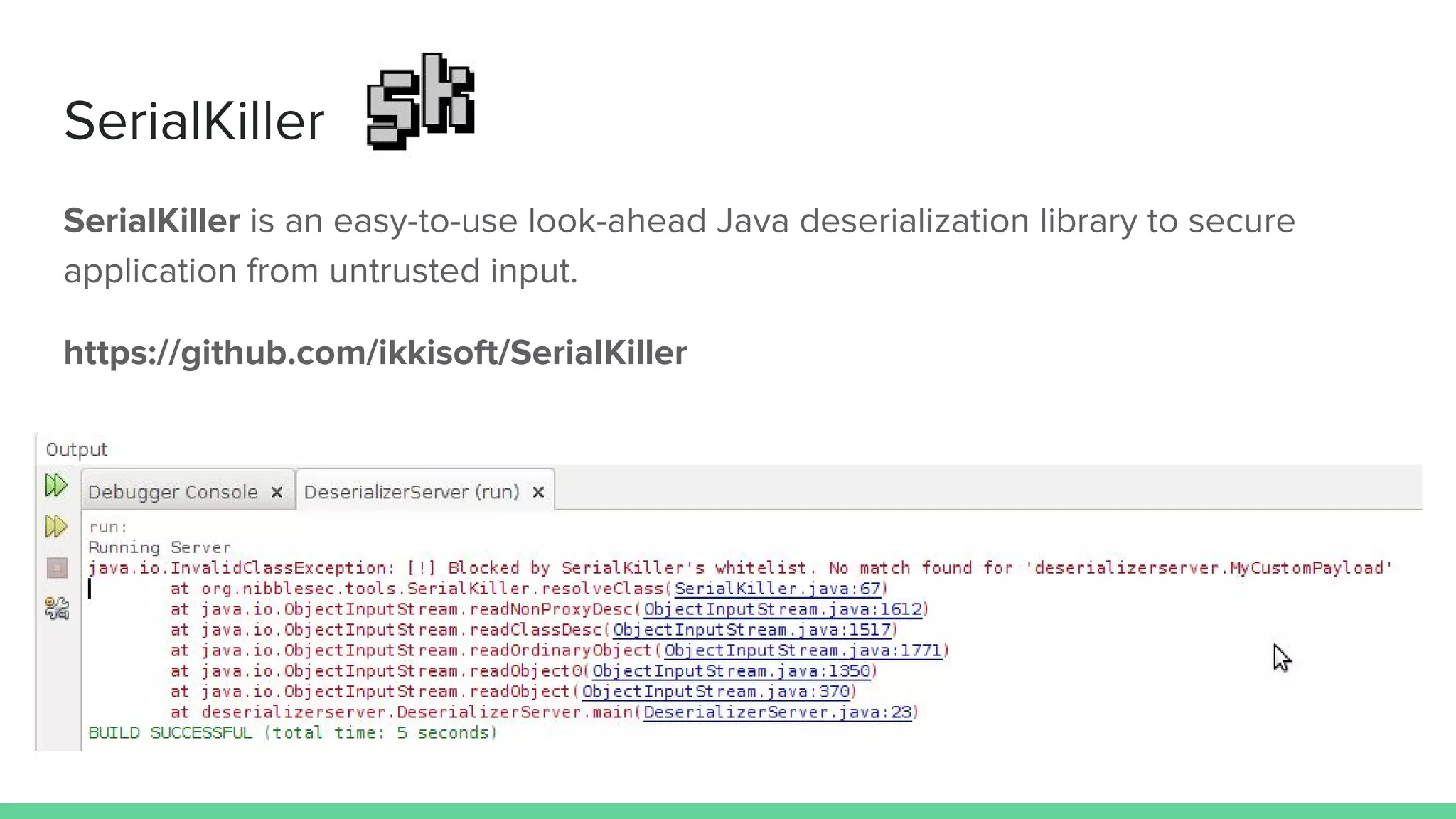
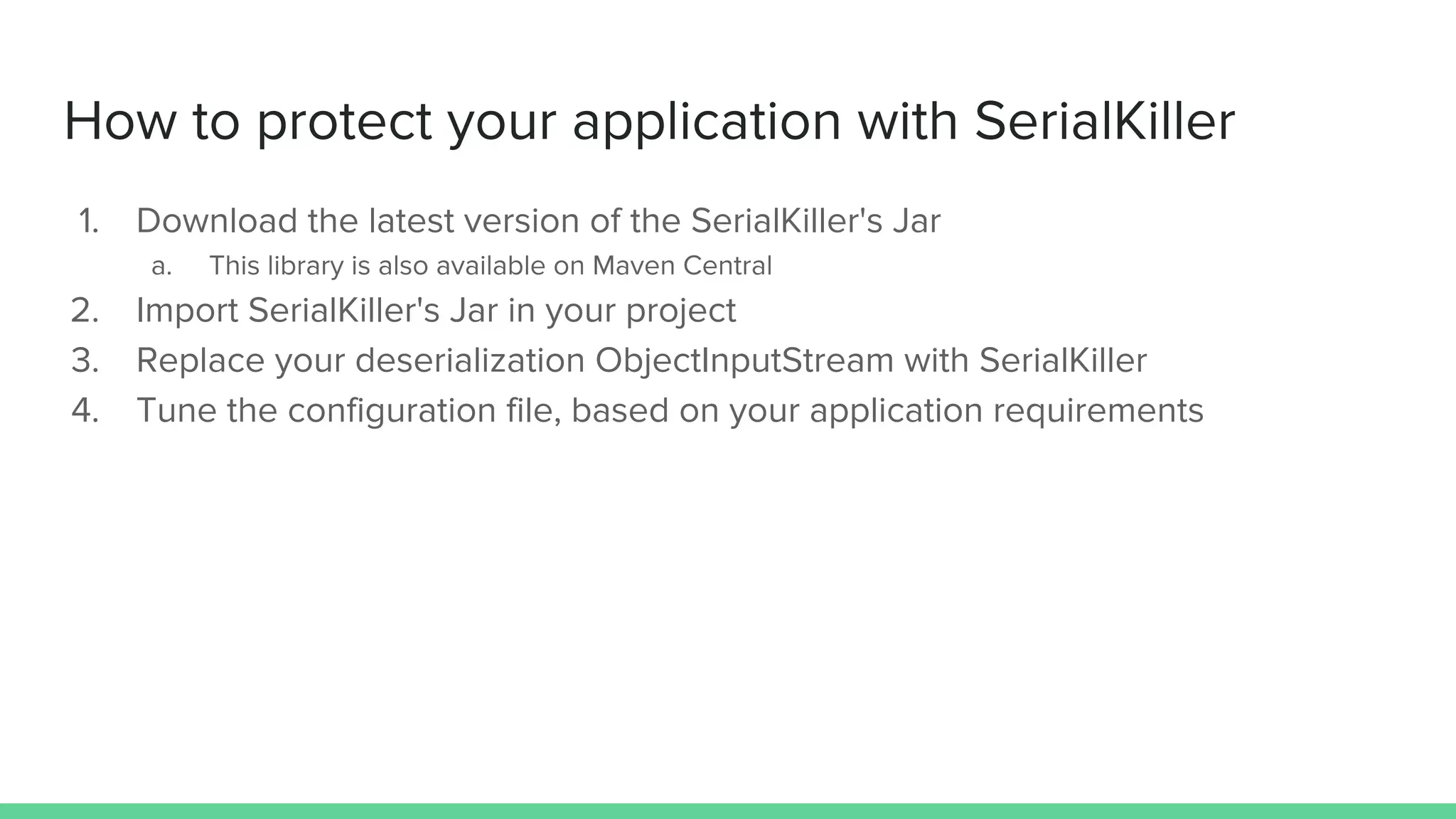
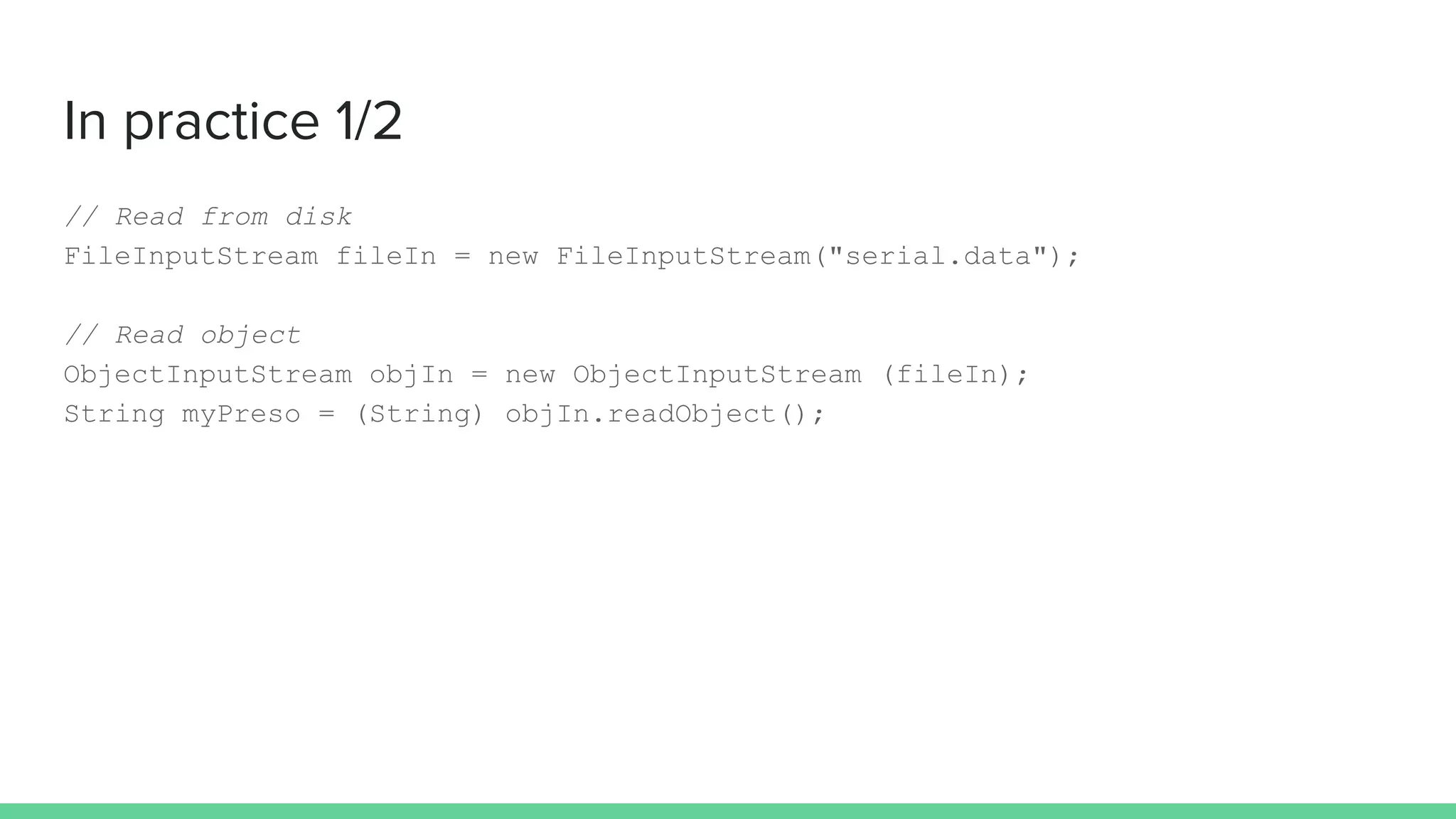
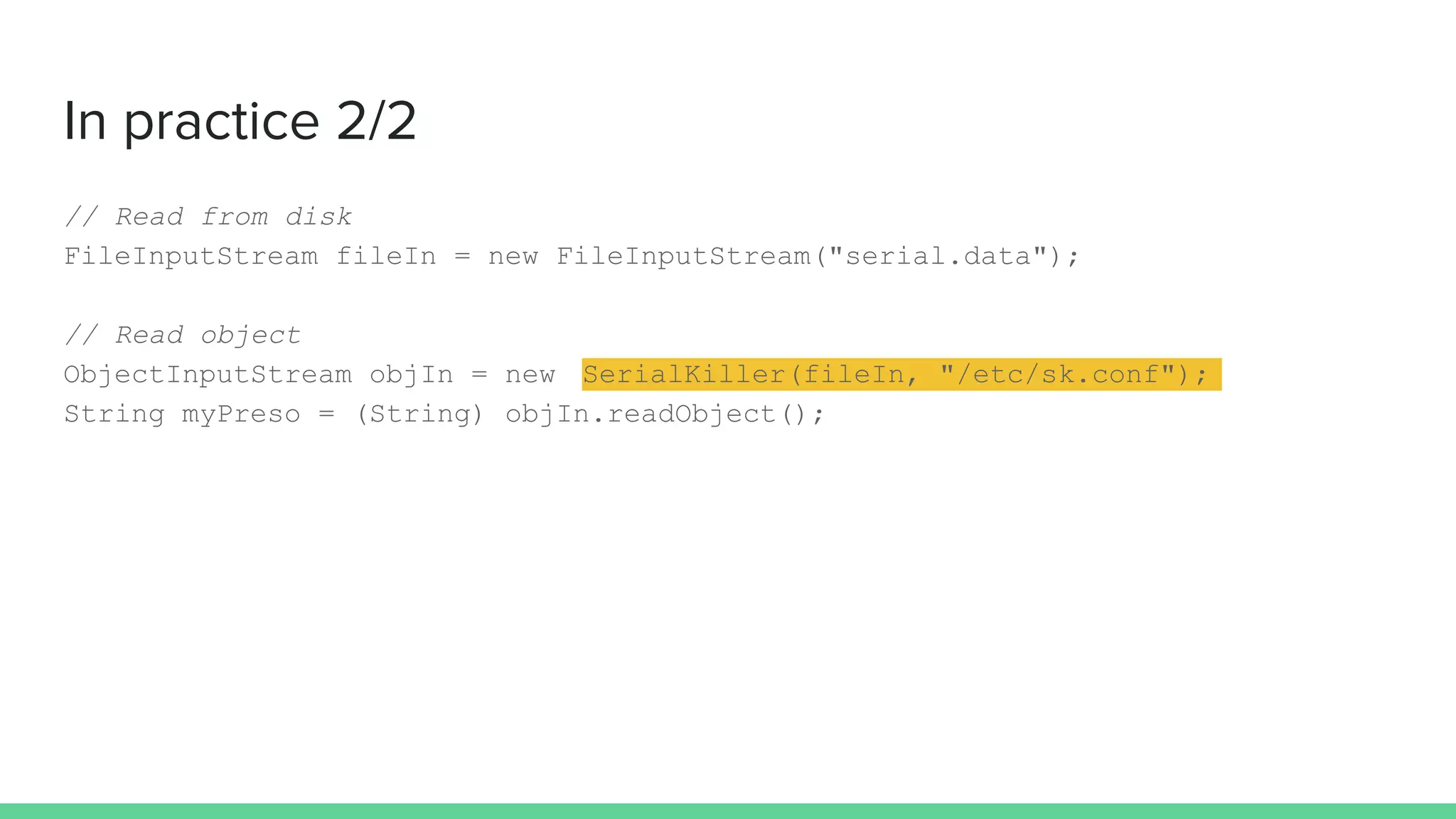
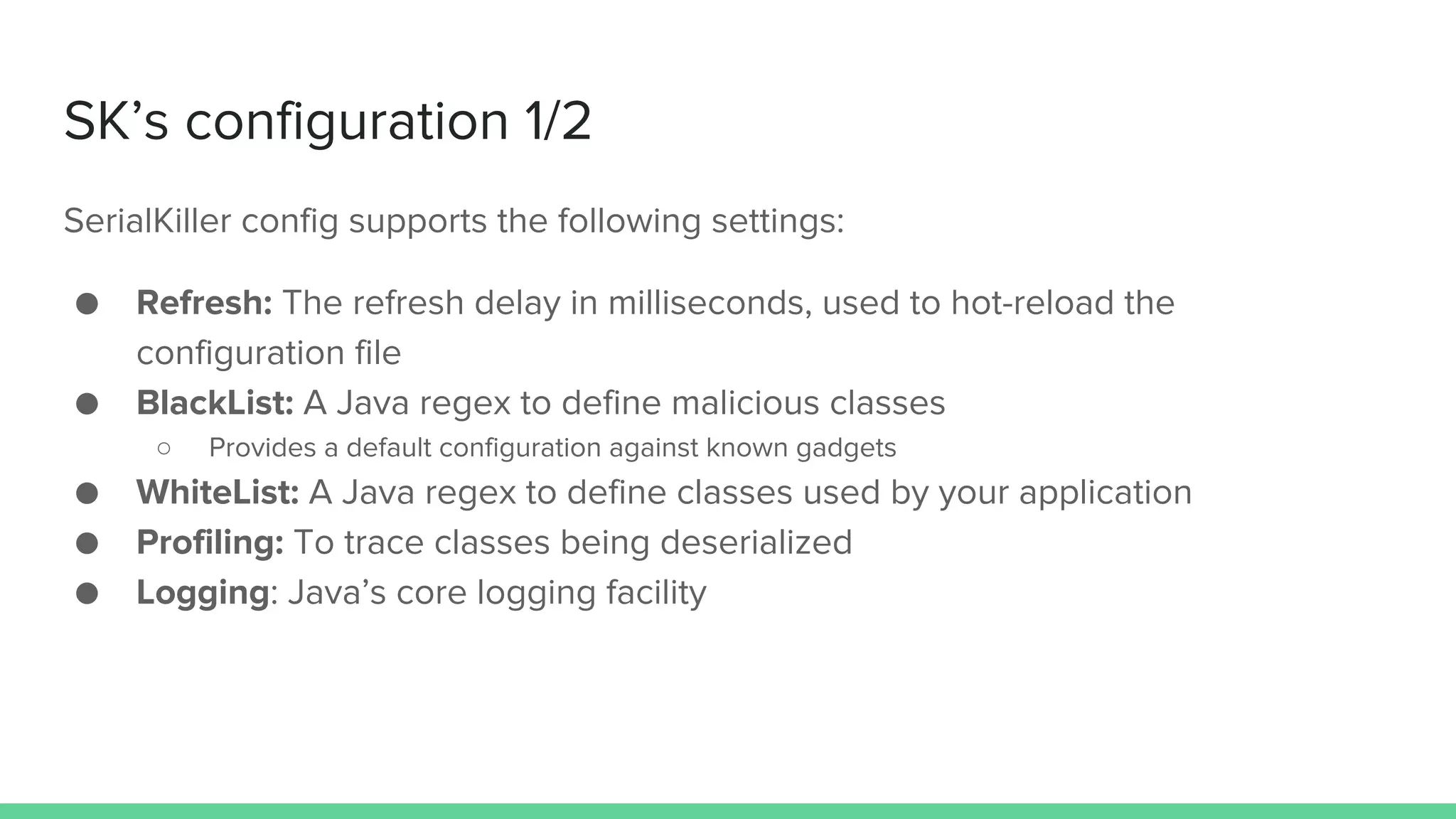
The document discusses defending against Java deserialization vulnerabilities, detailing both the nature of these vulnerabilities and methods for protection. It includes a real-life case study of a vulnerability in the Sun Java Web Console and suggests several defense strategies, such as using authentication, Java agent-based solutions, and safe ObjectInputStream implementations. The presentation emphasizes the importance of avoiding serialization for untrusted data and introduces the Serialkiller library as a tool for enhancing application security against these threats.




![Deserialization in Bytecode
[...]
aload ois
invokevirtual Object ObjectInputStream.readObject()
checkcast String
[...]
Any Serializable class will
work until this point.
No type safety](https://image.slidesharecdn.com/defendingagainstjavadeserializationvulnerabilities-160925041930/75/Defending-against-Java-Deserialization-Vulnerabilities-7-2048.jpg)





![SK’s configuration 2/2
<?xml version="1.0" encoding="UTF-8"?>
<config>
<refresh>6000</refresh>
<mode>
<profiling>true</profiling>
</mode>
<logging>
<enabled>true</enabled>
<logfile>/tmp/serialkiller.log</logfile>
</logging>
<blacklist>
[...]
<!-- ysoserial's Spring1 payload -->
<regexp>org.springframework.beans.factory.ObjectFactory$</regexp>
</blacklist>
<whitelist>
<regexp>.*</regexp>
</whitelist>
</config>](https://image.slidesharecdn.com/defendingagainstjavadeserializationvulnerabilities-160925041930/75/Defending-against-Java-Deserialization-Vulnerabilities-34-2048.jpg)