Interoute Intelligent Monitoring
•Download as PPTX, PDF•
0 likes•548 views
This document provides an overview of Interoute Intelligent Monitoring (IIM), a monitoring platform that harnesses various best-of-breed tools. IIM provides complete monitoring of core infrastructure, network, security, applications, and databases. It features a customer portal for access to graphs, alerts, ticketing, and reports. IIM Logic performs event aggregation, filtering, and root cause analysis to reduce the time to fix issues. Interoute professional services can customize the monitoring checks and thresholds to provide full end-to-end monitoring. IIM supports hybrid cloud deployments and offers high availability through its resilient clustered architecture.
Report
Share
Report
Share
Recommended
WSO2Con EU 2016: WSO2 IoT Server: Your Foundation for the Internet of Things

WSO2 IoT Server encapsulates everything you need for implementing a server side Internet of things (IoT) architecture. It features an extensible framework for device manufacturers to write plugins, analytics and integration capabilities for devices they manufacture. It also has a strong analytics framework for performing batch, real time and predictive analytics on data streams from devices. Processed device data can be shared with other consumers allowing integration between devices or systems.
In this talk, Sumedha will introduce WSO2 IoT Server. He will focus on how device manufacturers and integration architects can make use of existing features of WSO2 IoT Server or extend them.
APIdays Paris 2019 - RASP for APIs and Microservices by Jean-Baptiste Aviat, ...

RASP for APIs and Microservices
Jean-Baptiste Aviat, Co-Founder & CTO of Sqreen.io
UNIFIED MESSAGE ARCHIVING – WHY IT IS IMPORTANT

Micro Focus Retain provides unified archiving of all
business communication, including email, social media,
and mobile communication data for case assessment,
search, and eDiscovery.
Use it in house or in the Cloud. So what does that
mean to you, and why do you need it? Check out the charts
and find out for yourself.
Scug 1803 modern device management

My presentation on Modern Device Management from SCUGDK 19 april 2018
Recommended
WSO2Con EU 2016: WSO2 IoT Server: Your Foundation for the Internet of Things

WSO2 IoT Server encapsulates everything you need for implementing a server side Internet of things (IoT) architecture. It features an extensible framework for device manufacturers to write plugins, analytics and integration capabilities for devices they manufacture. It also has a strong analytics framework for performing batch, real time and predictive analytics on data streams from devices. Processed device data can be shared with other consumers allowing integration between devices or systems.
In this talk, Sumedha will introduce WSO2 IoT Server. He will focus on how device manufacturers and integration architects can make use of existing features of WSO2 IoT Server or extend them.
APIdays Paris 2019 - RASP for APIs and Microservices by Jean-Baptiste Aviat, ...

RASP for APIs and Microservices
Jean-Baptiste Aviat, Co-Founder & CTO of Sqreen.io
UNIFIED MESSAGE ARCHIVING – WHY IT IS IMPORTANT

Micro Focus Retain provides unified archiving of all
business communication, including email, social media,
and mobile communication data for case assessment,
search, and eDiscovery.
Use it in house or in the Cloud. So what does that
mean to you, and why do you need it? Check out the charts
and find out for yourself.
Scug 1803 modern device management

My presentation on Modern Device Management from SCUGDK 19 april 2018
PROTECT AND SURVIVE – SAFEGUARDING YOUR INFORMATION ASSETS - #MFSummit2017

The cyber threats facing businesses today are
constantly evolving. They are being perpetrated
by highly skilled, well-organized and well-funded
groups.
In this session we’ll take a look at
some of these threats, and how you can
mitigate your risks.
BalaBit 2015: Control Your IT Staff

Privileged Activity Monitoring
Shell Control Box is an activity monitoring appliance that controls privileged access to remote IT systems, records activities in searchable, movie-like audit trails, and prevents malicious actions. SCB is a quickly deployable enterprise tool with the widest protocol coverage on the market. It is completely independent from clients and servers - integrating seamlessly into existing infrastructures.
Ewug 1802 secure your windows device in a modern way

My presentation on How to secure your Windows Devices with EMS, Conditional Access, Identity Protection and new Windows 10 1709 security features
Panda Security - Gatedefender

Panda Gatedefender is a network security appliance, which protects the company from external threats.
More info: http://www.pandasecurity.com/enterprise/solutions/gatedefender-eSeries/
The Biggest Mistake you can make with your Data Center Licenses

IT is spending more on software than ever before. This most likely leaves you looking for ways to make the most of the software licenses you already have. On top of that, increasingly complex data center environments compound spending on software assets. Limited visibility into those assets could expose your most valuable business-critical applications to significant risk and additional cost.
See how data center discovery ninja Matt Reardon, takes an aggressive approach to gain visibility on complex software licenses so you can start making the most of your IT investments.
How Endpoint Security works ?

Endpoint security will helps in enhancing protection to corporate networks. It prevents from threats, virus and monitor potential entry in the network. Would you like to know more about the endpoint security working mechanism, then click here https://www.comodo.com/business-enterprise/endpoint-protection/endpoint-security-manager.php
CyberArk Cleveland Defend Non-Human ID Exploitations

We had an amazing event in Cleveland. Customers have been asking for the slides for the event. This is the CyberArk Cleveland Defend Non-Human ID Exploitation slide deck. Thank you for all who attended.
How Cloud-Based Service Providers Can Integrate Strong Identity and Security

Our Chief Product Officer, Lila Kee spoke at Cloud Computing Expo in New York.
The talk is about how cloud-based service providers must build security and trust into their offerings. It is imperative that as these cloud-based service providers make identity, security, and privacy easy for their customers as customers become more reliant on these offerings. The slides include the best practices for cloud-based service providers and how a superior user experience that is backed by security features will enable business growth and reduce customer churn.
You can find out more in our webinar: https://www.globalsign.com/en/lp/webinar-the-business-advantages-of-ssl-as-a-service/
DNSFilter Webinar: Decentralized Security

Decentralized Security! In this webinar, we discuss the current state of IT security and why we should be taking the decentralized approach for the new year.
AccessIT in 5 easy steps

How to enhance your IT efficiency in 5 steps
Minicom announces the launch of a new, open platform access management solution targeted at organizations with a minimum number of IT staff that maintain and operate up to 250 IT assets
[2.3] Large enterprise SIEM: get ready for oversize - Svetlana (Mona) Arkhipova![[2.3] Large enterprise SIEM: get ready for oversize - Svetlana (Mona) Arkhipova](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2.3] Large enterprise SIEM: get ready for oversize - Svetlana (Mona) Arkhipova](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Logs are NOT YET SIEM! :)
Enterprise firewalls feature and benefits

Cyberoam network security appliances offer next generation security features and deliver future-ready security to highly complex enterprise networks. The unique Layer 8 identity-based security gives enterprises complete visibility and control over user activity.
Mark Lomas | Zero-Trust Trust No One, Trust Nothing

Mark Lomas speaking about Zero-Trust Trust No One, Trust Nothing. Managing and Mitigating Risk in a Post-GDPR World at Midlands Cyber Security Expo 2019 #midscybersecurity19
Norton Zone File-Sharing Service

Norton Zone lets you deploy a safe and easy file-sharing service with the security expertise, visibility, and administrative controls you can only get from Symantec. With patented key encryption, Active Directory for SSO, automated two-factor authentication, and more, your employees can share files any time from any device—smartphone, computer or tablet.
Securing serverless system

by Mr. Vincent Lau, CTO, Voyager Innovations Singapore, at NUS-ISS SkillsFuture Series Seminar: Secured IoTs and Secured Cloud – Partners in ensuring a Secured Smart Nation Seminar (3 Oct)
Securing Serverless Systems

Wondering what is serverless (or FaaS) and how it impacts security risk? We will start with understanding how serverless is being used, the serverless architecture for IoT & AI, and examples of serverless applications. After which, we will go through the security impact of going serverless, then conclude with the top 10 serverless security risks and measures to mitigate them.
Best practices of mobile technology leaders: Airwatch Connect 2013

Presentation from Chris Pepin at Airwatch Connect in Atlanta, GA in September, 2013
Quantix virtualisation case study

A Quantix case study currently showcased on microsoft.com. This use case features a virtualisation project at Smith Flow Controls.
More Related Content
What's hot
PROTECT AND SURVIVE – SAFEGUARDING YOUR INFORMATION ASSETS - #MFSummit2017

The cyber threats facing businesses today are
constantly evolving. They are being perpetrated
by highly skilled, well-organized and well-funded
groups.
In this session we’ll take a look at
some of these threats, and how you can
mitigate your risks.
BalaBit 2015: Control Your IT Staff

Privileged Activity Monitoring
Shell Control Box is an activity monitoring appliance that controls privileged access to remote IT systems, records activities in searchable, movie-like audit trails, and prevents malicious actions. SCB is a quickly deployable enterprise tool with the widest protocol coverage on the market. It is completely independent from clients and servers - integrating seamlessly into existing infrastructures.
Ewug 1802 secure your windows device in a modern way

My presentation on How to secure your Windows Devices with EMS, Conditional Access, Identity Protection and new Windows 10 1709 security features
Panda Security - Gatedefender

Panda Gatedefender is a network security appliance, which protects the company from external threats.
More info: http://www.pandasecurity.com/enterprise/solutions/gatedefender-eSeries/
The Biggest Mistake you can make with your Data Center Licenses

IT is spending more on software than ever before. This most likely leaves you looking for ways to make the most of the software licenses you already have. On top of that, increasingly complex data center environments compound spending on software assets. Limited visibility into those assets could expose your most valuable business-critical applications to significant risk and additional cost.
See how data center discovery ninja Matt Reardon, takes an aggressive approach to gain visibility on complex software licenses so you can start making the most of your IT investments.
How Endpoint Security works ?

Endpoint security will helps in enhancing protection to corporate networks. It prevents from threats, virus and monitor potential entry in the network. Would you like to know more about the endpoint security working mechanism, then click here https://www.comodo.com/business-enterprise/endpoint-protection/endpoint-security-manager.php
CyberArk Cleveland Defend Non-Human ID Exploitations

We had an amazing event in Cleveland. Customers have been asking for the slides for the event. This is the CyberArk Cleveland Defend Non-Human ID Exploitation slide deck. Thank you for all who attended.
How Cloud-Based Service Providers Can Integrate Strong Identity and Security

Our Chief Product Officer, Lila Kee spoke at Cloud Computing Expo in New York.
The talk is about how cloud-based service providers must build security and trust into their offerings. It is imperative that as these cloud-based service providers make identity, security, and privacy easy for their customers as customers become more reliant on these offerings. The slides include the best practices for cloud-based service providers and how a superior user experience that is backed by security features will enable business growth and reduce customer churn.
You can find out more in our webinar: https://www.globalsign.com/en/lp/webinar-the-business-advantages-of-ssl-as-a-service/
DNSFilter Webinar: Decentralized Security

Decentralized Security! In this webinar, we discuss the current state of IT security and why we should be taking the decentralized approach for the new year.
AccessIT in 5 easy steps

How to enhance your IT efficiency in 5 steps
Minicom announces the launch of a new, open platform access management solution targeted at organizations with a minimum number of IT staff that maintain and operate up to 250 IT assets
[2.3] Large enterprise SIEM: get ready for oversize - Svetlana (Mona) Arkhipova![[2.3] Large enterprise SIEM: get ready for oversize - Svetlana (Mona) Arkhipova](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2.3] Large enterprise SIEM: get ready for oversize - Svetlana (Mona) Arkhipova](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Logs are NOT YET SIEM! :)
Enterprise firewalls feature and benefits

Cyberoam network security appliances offer next generation security features and deliver future-ready security to highly complex enterprise networks. The unique Layer 8 identity-based security gives enterprises complete visibility and control over user activity.
Mark Lomas | Zero-Trust Trust No One, Trust Nothing

Mark Lomas speaking about Zero-Trust Trust No One, Trust Nothing. Managing and Mitigating Risk in a Post-GDPR World at Midlands Cyber Security Expo 2019 #midscybersecurity19
Norton Zone File-Sharing Service

Norton Zone lets you deploy a safe and easy file-sharing service with the security expertise, visibility, and administrative controls you can only get from Symantec. With patented key encryption, Active Directory for SSO, automated two-factor authentication, and more, your employees can share files any time from any device—smartphone, computer or tablet.
Securing serverless system

by Mr. Vincent Lau, CTO, Voyager Innovations Singapore, at NUS-ISS SkillsFuture Series Seminar: Secured IoTs and Secured Cloud – Partners in ensuring a Secured Smart Nation Seminar (3 Oct)
Securing Serverless Systems

Wondering what is serverless (or FaaS) and how it impacts security risk? We will start with understanding how serverless is being used, the serverless architecture for IoT & AI, and examples of serverless applications. After which, we will go through the security impact of going serverless, then conclude with the top 10 serverless security risks and measures to mitigate them.
Best practices of mobile technology leaders: Airwatch Connect 2013

Presentation from Chris Pepin at Airwatch Connect in Atlanta, GA in September, 2013
What's hot (20)
PROTECT AND SURVIVE – SAFEGUARDING YOUR INFORMATION ASSETS - #MFSummit2017

PROTECT AND SURVIVE – SAFEGUARDING YOUR INFORMATION ASSETS - #MFSummit2017
Ewug 1802 secure your windows device in a modern way

Ewug 1802 secure your windows device in a modern way
The Biggest Mistake you can make with your Data Center Licenses

The Biggest Mistake you can make with your Data Center Licenses
CyberArk Cleveland Defend Non-Human ID Exploitations

CyberArk Cleveland Defend Non-Human ID Exploitations
How Cloud-Based Service Providers Can Integrate Strong Identity and Security

How Cloud-Based Service Providers Can Integrate Strong Identity and Security
[2.3] Large enterprise SIEM: get ready for oversize - Svetlana (Mona) Arkhipova![[2.3] Large enterprise SIEM: get ready for oversize - Svetlana (Mona) Arkhipova](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2.3] Large enterprise SIEM: get ready for oversize - Svetlana (Mona) Arkhipova](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2.3] Large enterprise SIEM: get ready for oversize - Svetlana (Mona) Arkhipova
Mark Lomas | Zero-Trust Trust No One, Trust Nothing

Mark Lomas | Zero-Trust Trust No One, Trust Nothing
Best practices of mobile technology leaders: Airwatch Connect 2013

Best practices of mobile technology leaders: Airwatch Connect 2013
Viewers also liked
Quantix virtualisation case study

A Quantix case study currently showcased on microsoft.com. This use case features a virtualisation project at Smith Flow Controls.
Navigating Social Media in the Automotive Industry

A helpful whitepaper by DMEautomotive, aimed at providing a brief description of social media, its importance and insights on how dealerships can integrate social media into their marketing strategies.
Viewers also liked (7)
Navigating Social Media in the Automotive Industry

Navigating Social Media in the Automotive Industry
Similar to Interoute Intelligent Monitoring
Presentation cloud security the grand challenge

Download & Share Technology
Presentations http://goo.gl/k80oY0
Student Guide & Best http://goo.gl/6OkI77
Extend Your Market Reach with IBM Security QRadar for MSPs

View on-demand recording: http://securityintelligence.com/events/ibm-security-qradar-for-msps/
As the number of security events grow in complexity and frequency, your clients are likely looking for ways to deploy leading security capabilities to gain more comprehensive security visibility across their operations. With the next release of IBM Security QRadar, you have an enhanced opportunity to deliver a best-in-class security intelligence solution to your broad base of customers.
Join us for a webcast presented by Vijay Dheap, IBM Security Global Solutions Manager, to learn about the new features of IBM Security QRadar designed especially for Managed Service Providers. He will cover:
- Centralized views and incident management with extensive APIs
- Flexible MSP pricing options
- Horizontal, snap-on scalability that is cloud ready
Cloud Security: What you need to know about IBM SmartCloud Security

Safeguarding the cloud with IBM Security solutions - Maintain visibility and control with proven security solutions for public, private and hybrid clouds.
IBM Softlayer Bluemix Marketplace

IBM Softlayer Bluemix Marketplace
API Economy
Infrastructure as a Service
Platform as a Service
Software as a Service
IaaS PaaS SaaS
Register for Bluemix at http://ibm.biz/BluemixSBSS
See Softlayer at http://ibm.biz/SBSlideShareSL
Join the Marketplace at http://ibm.biz/SBSlideShareMP
BT Cloud Enterprise Service Store - Rob Rowlingson

Rob Rowlingson, Principal Security Researcher at BT Research and Technology, gave this presentation at the EIT ICT Labs Interactive Cloud Clinic event.
FIWARE Global Summit - Building Production Grade IoT Platform Leveraging FIWARE

Presentation by Parwinder Singh (Technical Specialist, NEC Technologies India Pvt Ltd.) and Satinder Jeet Singh (Group Project Manager, NEC Technologies India Pvt Ltd.)
FIWARE Global Summit
23-24 October 2019 - Berlin, Germany
Revolutionizing IoT Testing - A Sneak Peek of HiveMQ Swarm

Load testing and reliability testing of MQTT systems are imperative for any business-critical IoT solution. HiveMQ Swarm provides the distributed simulation environment to successfully test millions of MQTT clients, millions of MQTT messages, and hundreds of thousands of MQTT topic names. The tool can check the performance, scalability, and reliability of your IoT solution before it is deployed into production.
In this webinar, Dominik Obermaier, CTO and co-founder at HiveMQ, and Georg Held, engineering manager at HiveMQ, introduce this new testing tool and give a demo to showcase its capabilities, such as:
- Complete end-to-end testing
- A Distributed platform
- Simulation of millions of devices, messages and MQTT topics
- Develop reusable scenarios
- Create custom data generators
About the Speakers.
Dominik Obermaier is CTO and co-founder of HiveMQ. He is a member of the OASIS Technical Committee and is part of the standardization committee for MQTT 3.1.1 and MQTT 5. He is the co-author of the book 'The Technical Foundations of IoT' and a frequent speaker on IoT, MQTT, and messaging.
Georg Held is Engineering Manager at HiveMQ.
To watch the webinar recording: https://www.hivemq.com/webinars/revolutionizing-iot-testing-a-sneak-peak-of-hivemq-swarm/
IBM Softlayer ile bulutta 3. Boyut Bora Taşer IBM

IBM Softlayer ile bulutta 3. Boyut Bora Taşer IBM - Webrazzi Summit 2015
Securing your IoT Implementations

As the Internet of Things is deployed across a wide range of industrial, consumer, and business environments, of special interest and concern is the need to implement IoT solutions with careful attention to security. While many of the challenges in IoT security are similar to the challenges of securing information technology (IT) computing environments, there are special considerations due to the scale, operating conditions, system capabilities, and wide range of device types which are used in IoT solutions. Further, these systems, by connecting the electronic and physical worlds, must address both operations technology (OT) security and information technology (IT) security.
In this session we will discuss the existing and emerging capabilities from IBM which we are both building into our IoT platform as well as the solutions built on top of that platform. Security features address the full spectrum of designing, building, deploying, and operating IoT solutions and are being built to enable a risk-based approach to applying these security capabilities. Both well-established and new technologies such as blockchain-based collaboration are part of these security capabilities. We consider device, network, application, and user security, with consideration for confidentiality, integrity, and availability of the systems and information. Considerations for safety and privacy also factor into the capabilities which IBM is building to secure IoT environments.
Cloud for the Military - Projects, Promise

Cloud computing offers much promise to the military by addressing the fundamentals of increasing mission agility / complexity in a climate of economic constraint. This presentation - given to the NATO IST-125 panel in Ankara, Turkey on the 11th Jun 2015 - analyses cloud usage in three project case studies then specifically considers the SECURITY challenge and how this can be addressed as cloud evolves in future.
Cloud Computing: Its Applications and Security Issues (A Major Challenge in C...

https://www.irjet.net/archives/V4/i12/IRJET-V4I12131.pdf
IBM Endpoint Manager for Mobile Devices (Overview)

Manage all devices - smartphones, tablets, laptops, desktops, and servers - from a single console. IBM Endpoint Manager also integrates Enterproid Divide secure container and NitroDesk TouchDown secure email technologies for separation of organizational content on BYOD and contractor devices.
Effective Security Monitoring for IBM i: What You Need to Know

Defending against the increasing sophistication and complexity of today’s security threats requires a comprehensive, multi-layered approach. The key is to maximize the strength of each layer of your defenses, and then ask yourself “If this layer is breached, what do I have in place to prevent further damage?”
Even if you have implemented the proper layers of protection, effective security still requires a thoughtful and comprehensive approach to monitoring and reporting. Monitoring plays a critical role in any effective IT security strategy. It's like having a security guard constantly patrolling your digital infrastructure, vigilantly watching for suspicious activity and potential threats. Security monitoring allows you to detect threats as soon as possible, giving you a better chance of responding quickly and effectively.
Join us for this webinar we will cover:
• The best practices for monitoring your IBM i environment.
• The benefits of combining your IBM i monitoring with other IT systems
• A demonstration of a new Assure Security Monitoring and Reporting interface
Securing Your Cloud Applications

The cloud offers simplified application development and delivery by providing infrastructure, platform and software services that are ready to use immediately. However, the major inhibitor for businesses has been concerns around security. IBM has simplified the typical method for approaching this problem. Whether you’re looking to employ infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS) or software-as-a-service (SaaS), use the framework below when designing your solution. Each platform comes with certain built-in security qualities and lets you use add-ons on top of the platform to secure each workload.
Security Information and Event Management (SIEM)

Leo TechnoSoft SIEM products help's every enterprise with all security threats. Security information and event management software provides real-time visibility.
IBM Endpoint Manager for Lifecycle Management (Overview)

Complete visibility and management over all endpoints - physical or virtual, on- or off-network across Windows, Max, Unix, and Linux servers, desktops, laptops, and specialty devices. Includes network discovery, deep hardware and software inventory of managed devices, software distribution and patch management, OS deployment and bare-metal provisioning, and remote control.
Similar to Interoute Intelligent Monitoring (20)
Extend Your Market Reach with IBM Security QRadar for MSPs

Extend Your Market Reach with IBM Security QRadar for MSPs
Cloud Security: What you need to know about IBM SmartCloud Security

Cloud Security: What you need to know about IBM SmartCloud Security
BT Cloud Enterprise Service Store - Rob Rowlingson

BT Cloud Enterprise Service Store - Rob Rowlingson
FIWARE Global Summit - Building Production Grade IoT Platform Leveraging FIWARE

FIWARE Global Summit - Building Production Grade IoT Platform Leveraging FIWARE
Revolutionizing IoT Testing - A Sneak Peek of HiveMQ Swarm

Revolutionizing IoT Testing - A Sneak Peek of HiveMQ Swarm
Cloud Computing: Its Applications and Security Issues (A Major Challenge in C...

Cloud Computing: Its Applications and Security Issues (A Major Challenge in C...
IBM Endpoint Manager for Mobile Devices (Overview)

IBM Endpoint Manager for Mobile Devices (Overview)
Effective Security Monitoring for IBM i: What You Need to Know

Effective Security Monitoring for IBM i: What You Need to Know
IBM Endpoint Manager for Lifecycle Management (Overview)

IBM Endpoint Manager for Lifecycle Management (Overview)
More from Onomi
Oracle ISV Cloud Presentation

Presentation delivered by Quantix at the Oracle Financial Services ISV event (12/9)
Exchange server 2010 archiving and retention

Our ExchangeCloud service offers a dedicated Exchange 2010 server. This presentation outlines the archiving and retention features in the latest release
9 Steps to Cloud Security Heaven

A useful presentation slide which details the 9 policy enforcement points aligned to users accessing the Quantix Cloud infrastructure
TechMarketView article - Quantix Growth

A great review on the rise of Quantix's Cloud Services from a well respected source.
Quantix cloud case study

This hit the press this week and demonstrates how Shire Pharmaceuticals have leveraged the Quantix Cloud. They have been able to use our technology to convert a client/server app (IDBS E-Workbook) into a flexible SaaS model.
Quantix - Cloud Computing Congress (15/10)

Updated version of the Cloudstorm presentation. Delivered at the Cloud Computing Congress at Olympia (15th March 2010)
Cloud Business Continuity White Paper

White paper covering the business case for Cloud Disaster Recovery. www.cloud-dr.com
More from Onomi (17)
Recently uploaded
A tale of scale & speed: How the US Navy is enabling software delivery from l...

Rapid and secure feature delivery is a goal across every application team and every branch of the DoD. The Navy’s DevSecOps platform, Party Barge, has achieved:
- Reduction in onboarding time from 5 weeks to 1 day
- Improved developer experience and productivity through actionable findings and reduction of false positives
- Maintenance of superior security standards and inherent policy enforcement with Authorization to Operate (ATO)
Development teams can ship efficiently and ensure applications are cyber ready for Navy Authorizing Officials (AOs). In this webinar, Sigma Defense and Anchore will give attendees a look behind the scenes and demo secure pipeline automation and security artifacts that speed up application ATO and time to production.
We will cover:
- How to remove silos in DevSecOps
- How to build efficient development pipeline roles and component templates
- How to deliver security artifacts that matter for ATO’s (SBOMs, vulnerability reports, and policy evidence)
- How to streamline operations with automated policy checks on container images
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI)
UiPath Test Automation using UiPath Test Suite series, part 3

Welcome to UiPath Test Automation using UiPath Test Suite series part 3. In this session, we will cover desktop automation along with UI automation.
Topics covered:
UI automation Introduction,
UI automation Sample
Desktop automation flow
Pradeep Chinnala, Senior Consultant Automation Developer @WonderBotz and UiPath MVP
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
When stars align: studies in data quality, knowledge graphs, and machine lear...

Keynote at DQMLKG workshop at the 21st European Semantic Web Conference 2024
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

“AGI should be open source and in the public domain at the service of humanity and the planet.”
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovation With Your Product by VP of Product Design, Warner Music Group
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

💥 Speed, accuracy, and scaling – discover the superpowers of GenAI in action with UiPath Document Understanding and Communications Mining™:
See how to accelerate model training and optimize model performance with active learning
Learn about the latest enhancements to out-of-the-box document processing – with little to no training required
Get an exclusive demo of the new family of UiPath LLMs – GenAI models specialized for processing different types of documents and messages
This is a hands-on session specifically designed for automation developers and AI enthusiasts seeking to enhance their knowledge in leveraging the latest intelligent document processing capabilities offered by UiPath.
Speakers:
👨🏫 Andras Palfi, Senior Product Manager, UiPath
👩🏫 Lenka Dulovicova, Product Program Manager, UiPath
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, Product School
Essentials of Automations: Optimizing FME Workflows with Parameters

Are you looking to streamline your workflows and boost your projects’ efficiency? Do you find yourself searching for ways to add flexibility and control over your FME workflows? If so, you’re in the right place.
Join us for an insightful dive into the world of FME parameters, a critical element in optimizing workflow efficiency. This webinar marks the beginning of our three-part “Essentials of Automation” series. This first webinar is designed to equip you with the knowledge and skills to utilize parameters effectively: enhancing the flexibility, maintainability, and user control of your FME projects.
Here’s what you’ll gain:
- Essentials of FME Parameters: Understand the pivotal role of parameters, including Reader/Writer, Transformer, User, and FME Flow categories. Discover how they are the key to unlocking automation and optimization within your workflows.
- Practical Applications in FME Form: Delve into key user parameter types including choice, connections, and file URLs. Allow users to control how a workflow runs, making your workflows more reusable. Learn to import values and deliver the best user experience for your workflows while enhancing accuracy.
- Optimization Strategies in FME Flow: Explore the creation and strategic deployment of parameters in FME Flow, including the use of deployment and geometry parameters, to maximize workflow efficiency.
- Pro Tips for Success: Gain insights on parameterizing connections and leveraging new features like Conditional Visibility for clarity and simplicity.
We’ll wrap up with a glimpse into future webinars, followed by a Q&A session to address your specific questions surrounding this topic.
Don’t miss this opportunity to elevate your FME expertise and drive your projects to new heights of efficiency.
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
By Design, not by Accident - Agile Venture Bolzano 2024

As presented at the Agile Venture Bolzano, 4.06.2024
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
Recently uploaded (20)
A tale of scale & speed: How the US Navy is enabling software delivery from l...

A tale of scale & speed: How the US Navy is enabling software delivery from l...
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
Assure Contact Center Experiences for Your Customers With ThousandEyes

Assure Contact Center Experiences for Your Customers With ThousandEyes
UiPath Test Automation using UiPath Test Suite series, part 3

UiPath Test Automation using UiPath Test Suite series, part 3
When stars align: studies in data quality, knowledge graphs, and machine lear...

When stars align: studies in data quality, knowledge graphs, and machine lear...
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

Transcript: Selling digital books in 2024: Insights from industry leaders - T...
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...
Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx

Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, P...
Essentials of Automations: Optimizing FME Workflows with Parameters

Essentials of Automations: Optimizing FME Workflows with Parameters
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
By Design, not by Accident - Agile Venture Bolzano 2024

By Design, not by Accident - Agile Venture Bolzano 2024
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
Interoute Intelligent Monitoring
- 1. MAY 2013
- 2. The core infrastructure module reports on key hosting services such as storage, servers, operating systems, and virtual platforms. Success of backup jobs and other maintenance routines are all reported to clients via the web portal. Our extensive capability provides complete monitoring of security events to full IP performance management. The diverse tool set will proactively monitor everything from firewalls to MPLS connectivity. Interoute professional services can personalise the IIM monitoring checks and thresholds to provide full end to end monitoring. IIM Interoute Intelligent Monitoring (IIM) Overview Our mature tool set developed over the last 15 years provides critical monitoring for a range of database, application and web server technologies.
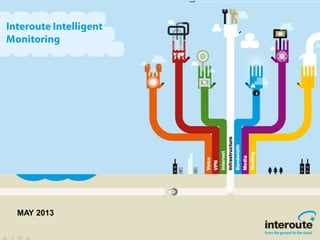
- 3. One monitoring platform, harnessing best of breed tools 3 The Hub • Customer portal • Graphs • Alert ticketing • Reporting IIM Logic • Event aggregation • Filtering • Root cause analysis • Custom thresholds Best of Breed Tools Core Infrastructure Network & Security Applications & Databases Custom monitoring checks
- 4. IIM Logic reduces the time to fix through root cause analysis
- 5. IIM Logic reduces the time to fix through root cause analysis The environment suffers a firewall outage All the devices generate alerts as they cannot deliver service
- 6. IIM Logic reduces the time to fix through root cause analysis IIM then delivers real time root cause analysis as the firewall “down” events are weighted above server service checks.
- 7. IIM Logic reduces the time to fix through root cause analysis Engineers can rapidly restore service by fixing the isolated root cause This is only possible due to IIM’s industry leading architecture, applying logic to ALL alerts, from every source.
- 8. Next Generation Monitoring for Hybrid Cloud Deployments Interoute Cloud Monitor your services on the Interoute cloud. Ensure that cloud services maintain the same visibility as dedicated servers. Customer On-PremiseDedicated Hosting IIM Complete monitoring of your environment available in all our datacentres. Track success of backups and gain in depth application monitoring. Monitor services running between the customer site and Interoute DC’s. On-premise “agentless” option for applications.
- 9. IIM Case Study: Hybrid Cloud IIM Currency Trading Application Firewalls Load Balancers Intrusion Prevention System Anti Virus IIS 7.0 Server Farm SQL Server 2012 AlwaysOn Cluster Node Windows 2008 r2 Backups Internet Access Custom Checks SQL Server 2012 Always On Cluster Node SQL Server data replication SSRS Windows 2008 r2 Site to Site VPN Connection Interoute Cloud Customer On-Premise SQL Server 2012 AlwaysOn Replication Customer Web Internal App & Reporting
- 10. What makes IIM stand out in the market? 10 1. Hybrid Cloud Support IIM offers Interoute the ability to support hybrid cloud solutions, which could utilise computing resources from different locations including customers own internal systems. 2. IIM Logic IIM logic provides the intelligence to conduct root cause analysis, combining all the monitoring sources from one of the most comprehensive tool sets, from network to application. 3. High Availability IIM is based on a highly resilient clustered architecture , which includes a business continuity provision to a second datacentre. 4. Custom Monitoring and Personalisation Interoute professional services are able to customise monitoring checks to provide an end to end personalised service.
