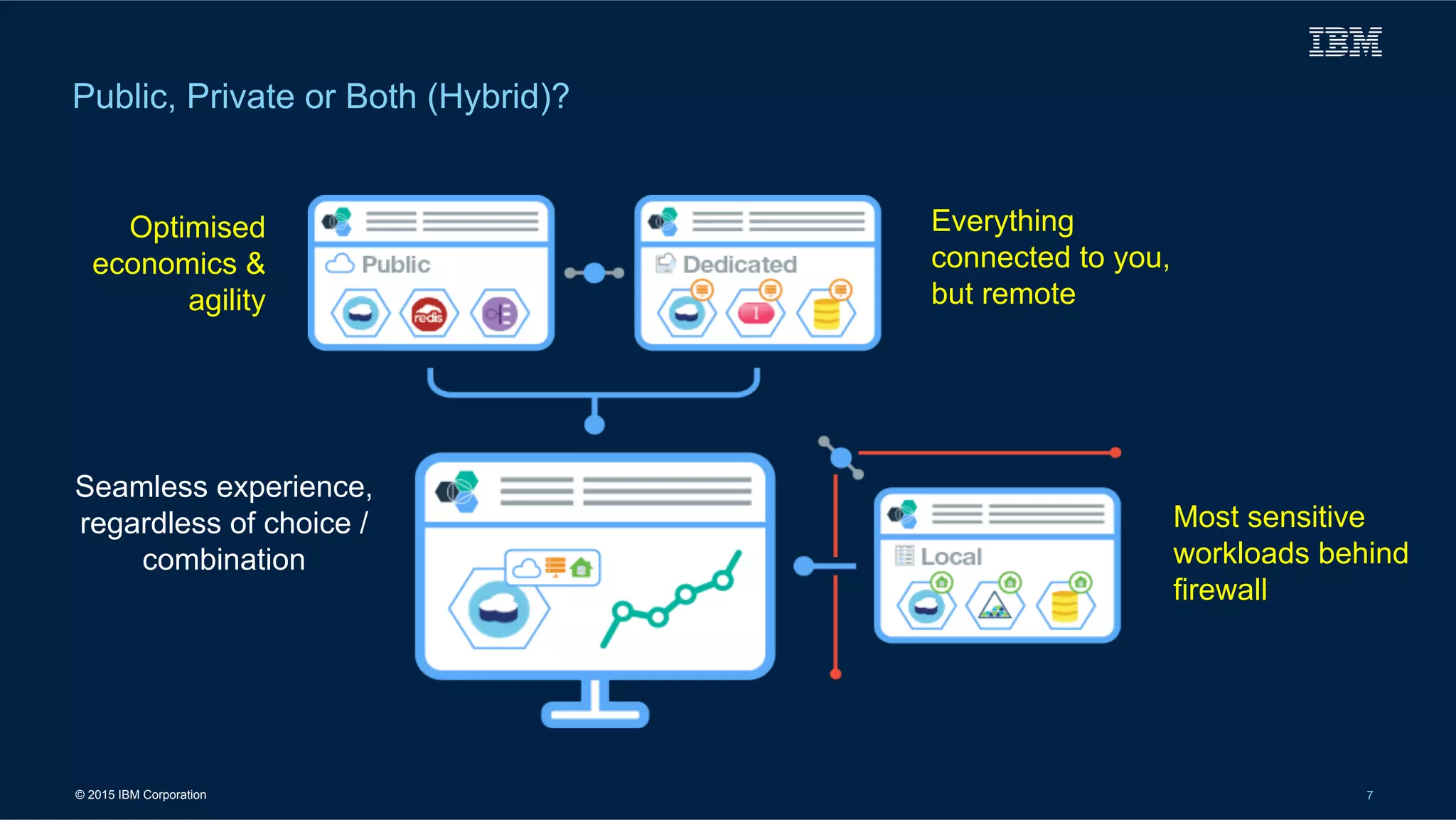
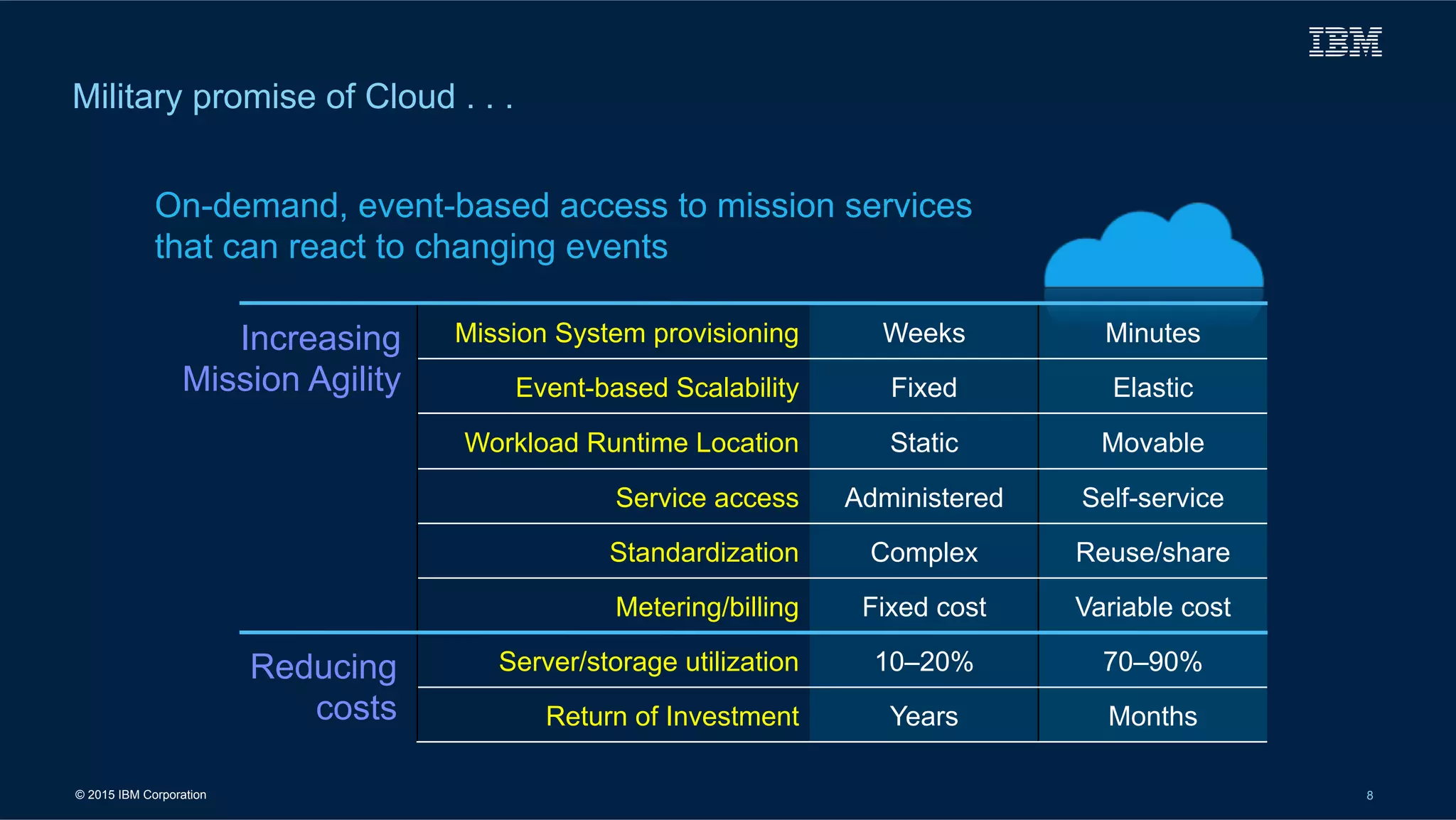
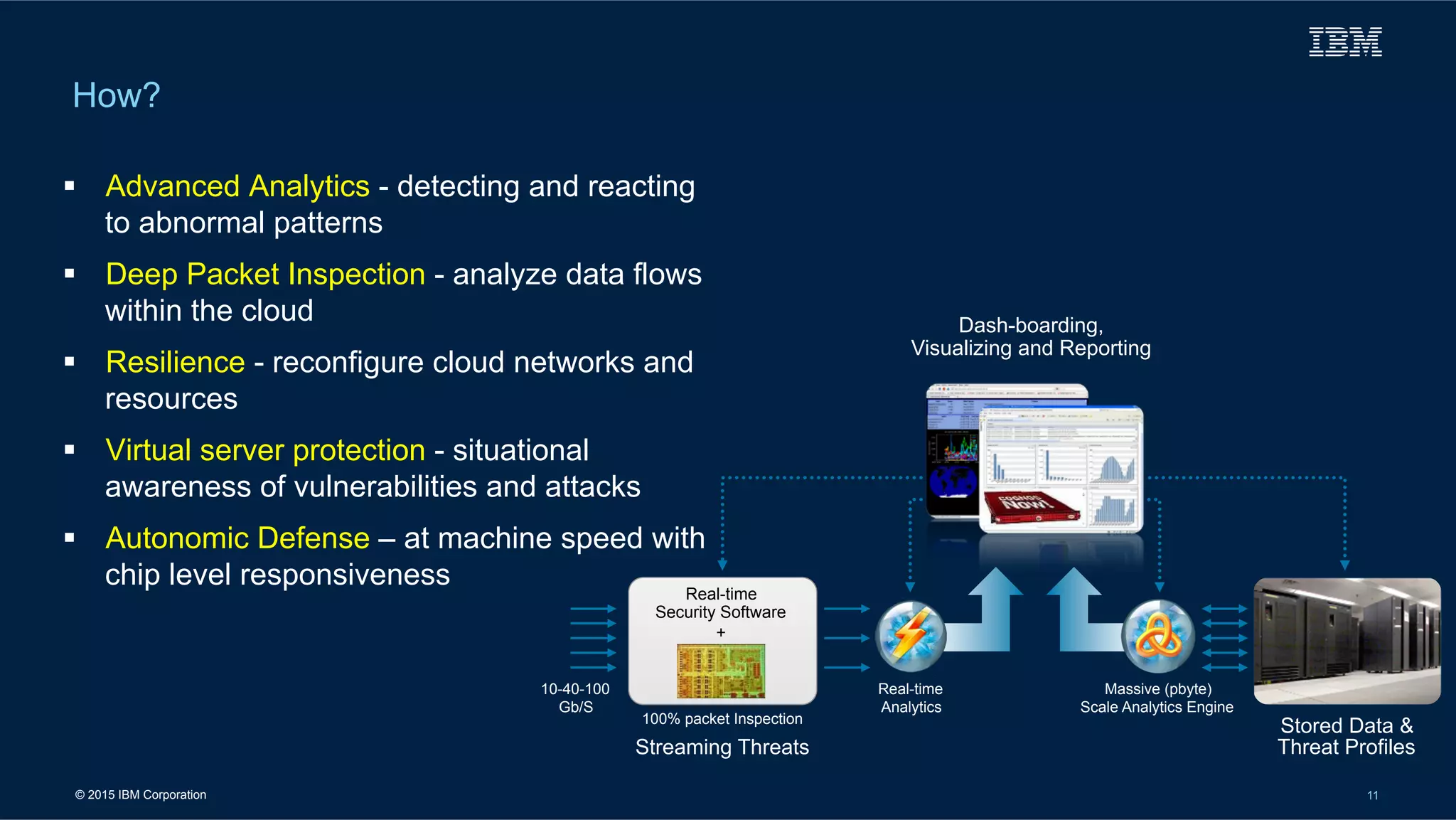
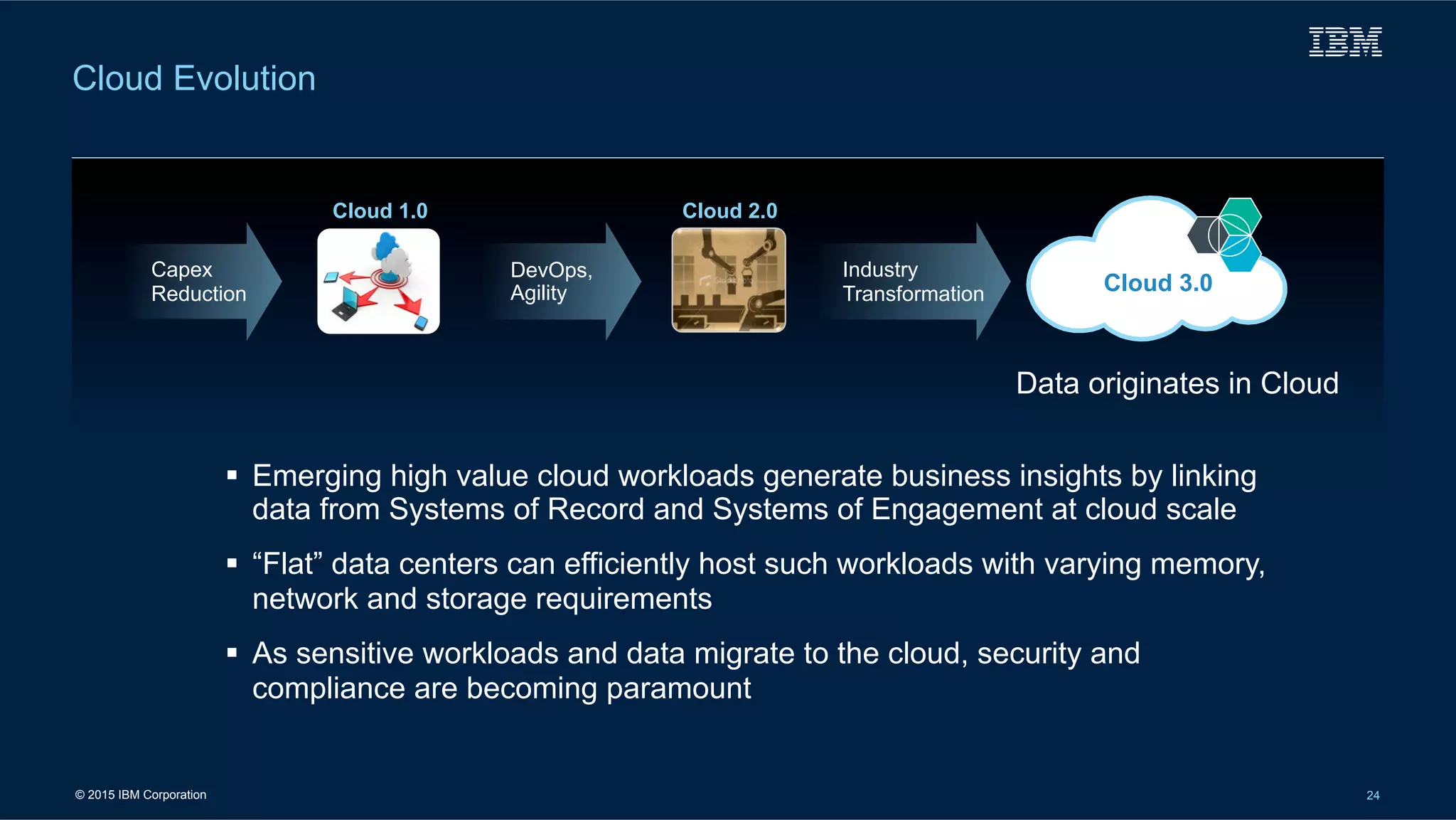
The document outlines IBM's cloud solutions tailored for military applications, emphasizing improved agility, cost efficiency, and security. It details specific use cases for the U.S. Air Force and Army logistics, showcasing advancements in data management and cybersecurity. Additionally, it highlights the National Oceanic and Atmospheric Administration's use of cloud technology to enhance weather data accessibility and analysis.









![© 2015 IBM Corporation 16
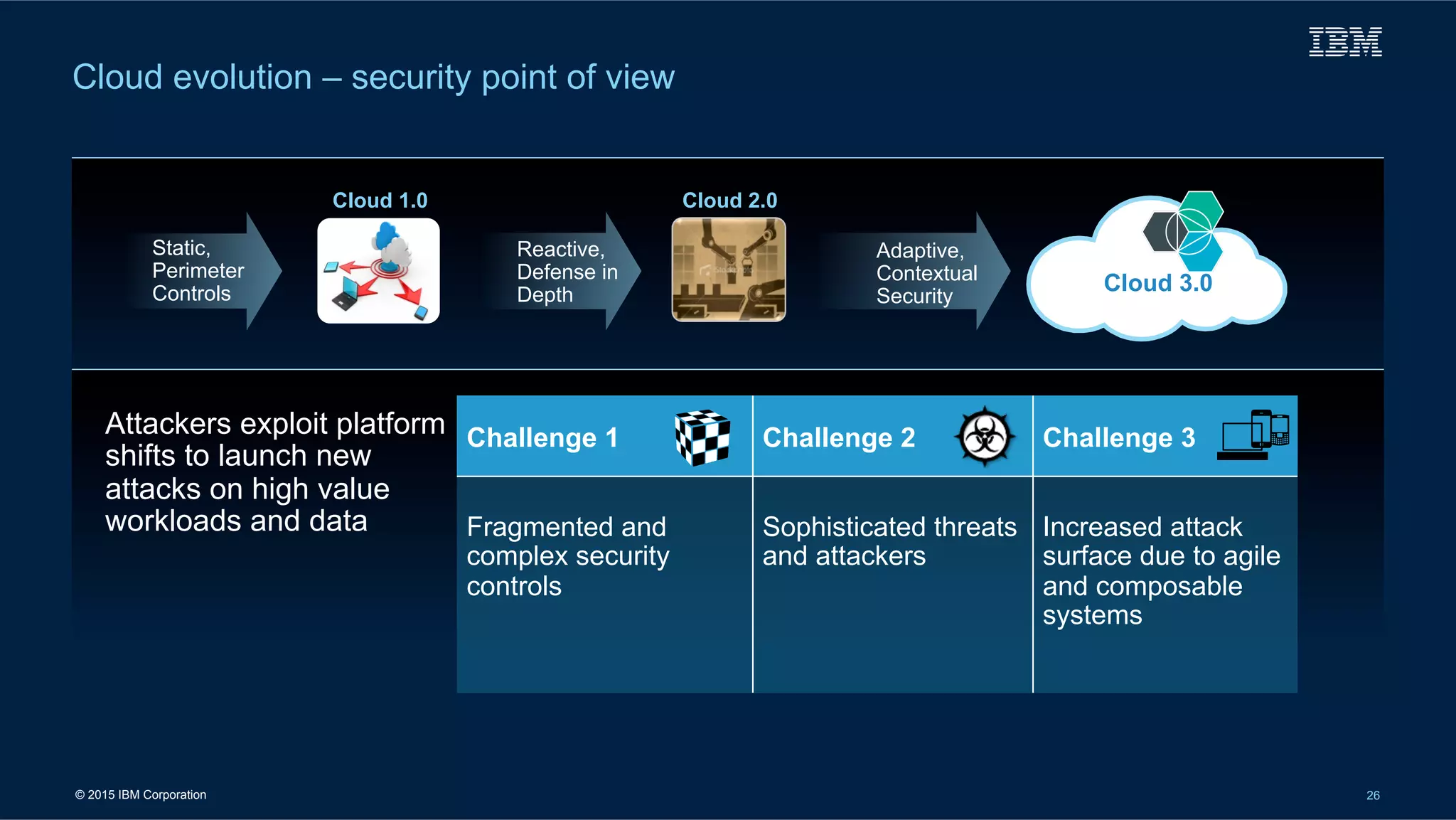
[1] Discovering “Real” As-Is
Firewall
Solaris
Servers
Trusted
User
EMC SAN
Other LOGSA
Customers
IETM
Customers
Basic
Services
IETM
Servers
Fiber Channel
Network
USPV
SAN
Tape NASNon-VM
Servers
Network
V-Block
Incomplete
ETL
Fiber Channel
Non-ERP
Databases
Non-ERP
Files
ERP
Databases
• Poor VM processes & mgmt
• Data Warehouse in disarray
• Excessive applications
• Disjointed SAN architecture
• Maxed-out SAN frames
• Thousands of patches not
applied over previous decadePortal
Databases
OldOSVMs
Active
Directory
• Numerous access mechanisms
• Badly outdated
equipment
SFTP &
Custom
Interfaces
Multiple
DB
Interfaces
Web Portal SSO, E-mail
Server Minimal SOA
Multiple
Client
Interfaces](https://image.slidesharecdn.com/milcloudist-150615102658-lva1-app6892/75/Cloud-for-the-Military-Projects-Promise-16-2048.jpg)
![© 2015 IBM Corporation 17
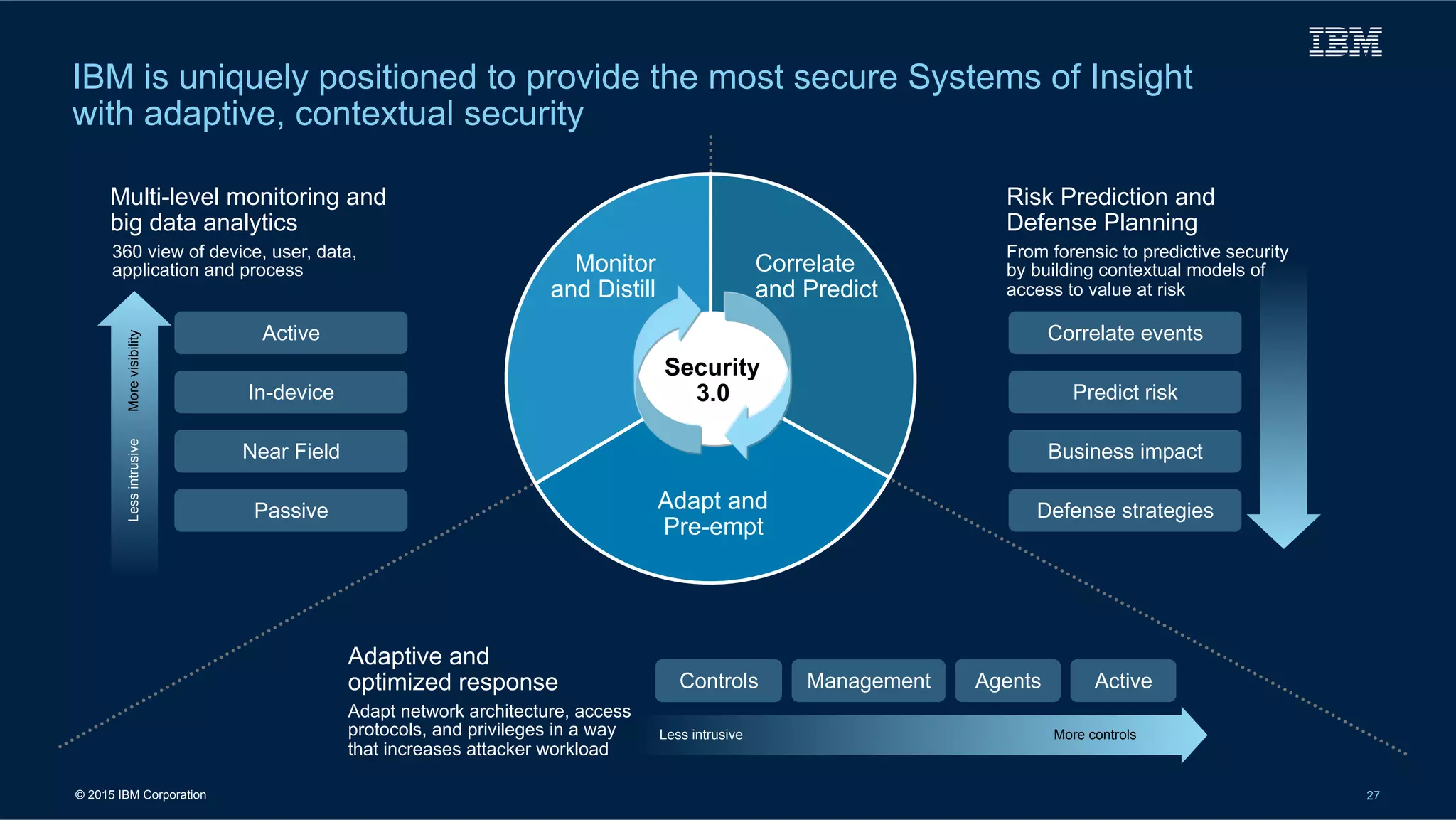
[2] . . . to Managed Services
• Migrate to Unified SAN
• Massive upgrade/patch fix
• Modernize equipment• Improve VM processes/mgmt
• Resolve License/Lease issues
• Reduce number of databases
• Modeled, doctrine-aligned Business Processes
Firewall
Solaris
Servers
Trusted
User
EMC SAN
LOGSA
Customers
IETM
Customers
SVCIETM
Servers
Fiber Channel
USPV
Non-VM
Servers
ILDP
Server
Network
V-Block
InfoSphere
ETL&ISD
Fiber Channel
Non-ERP
Databases
Non-ERP
Files
ERP
Databases
Portal
Unify
Databases
Solaris
VMS
LinuxVMs
SFTP /
LOGFERS
LOGTRANS,
LOGETL,
ILAP, LIW-F
Web
Portal,
E-mail
Server
Client SOA
Interfaces
Tape
Network
Active
Directory
XIV SAN
Substantial repairs
New/major updates
LIW-1
Forward
ALEG
Business
Glossary
NAS](https://image.slidesharecdn.com/milcloudist-150615102658-lva1-app6892/75/Cloud-for-the-Military-Projects-Promise-17-2048.jpg)






![© 2015 IBM Corporation 25
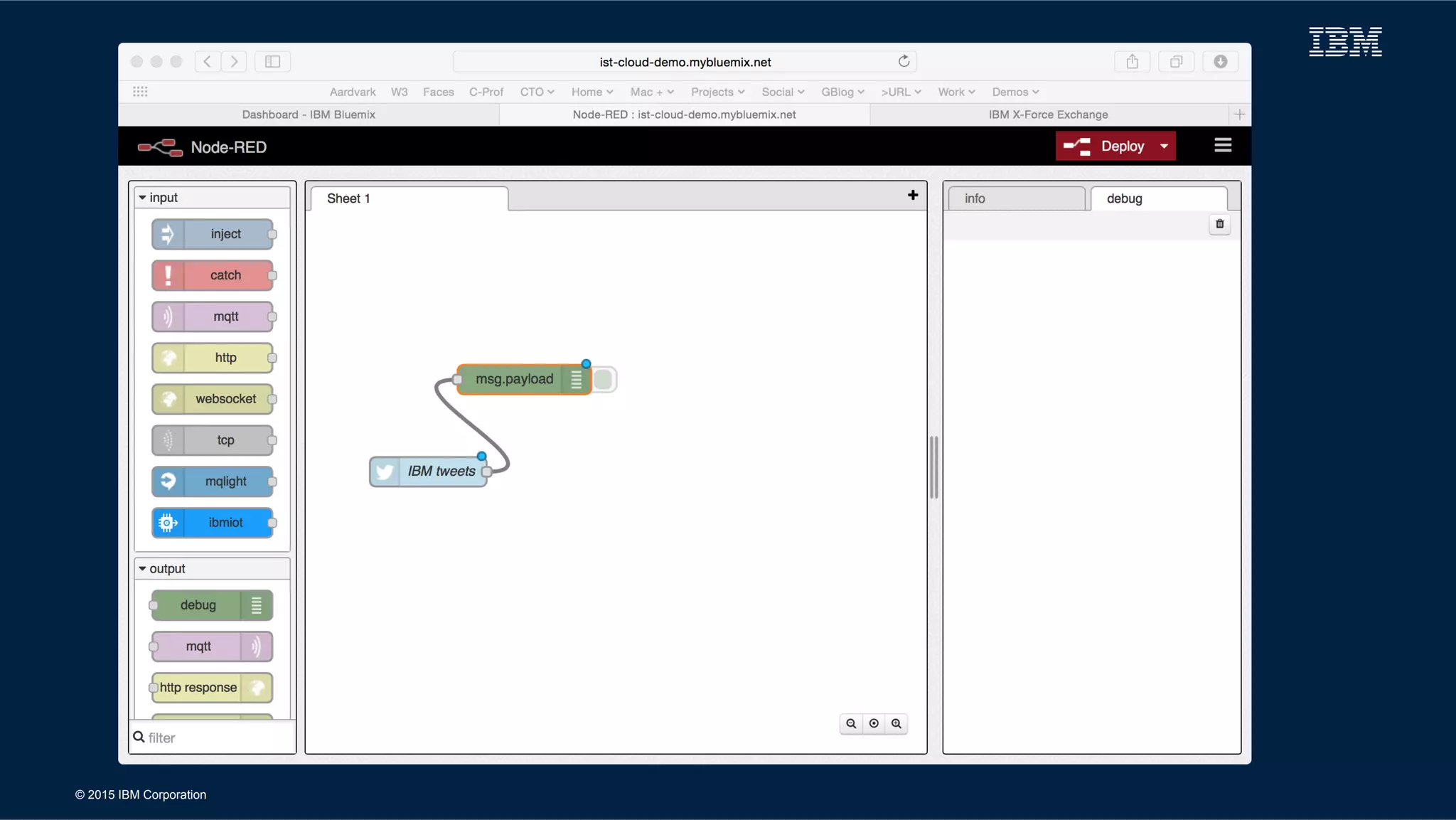
IBM BlueMix Overview
! Open Standards based Cloud Platform
! Mobile & application developers access to software [1]
– Integration
– Security
– Business functions
– Advanced, exploratory elements
! EASE of application development
! Immediate use of Web Service
! Ideal vehicle for Open Innovation
[1] from IBM & partners](https://image.slidesharecdn.com/milcloudist-150615102658-lva1-app6892/75/Cloud-for-the-Military-Projects-Promise-25-2048.jpg)