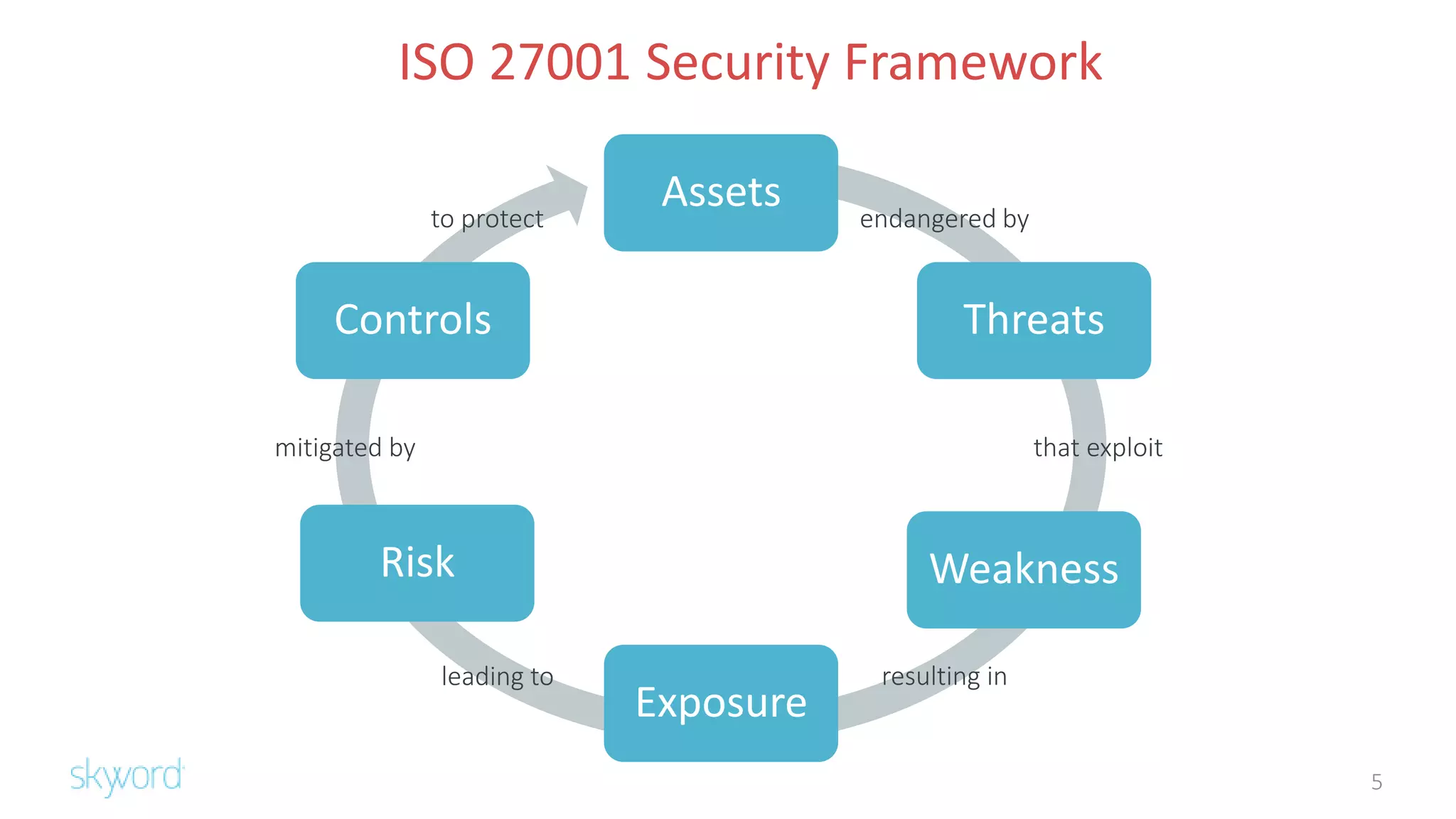
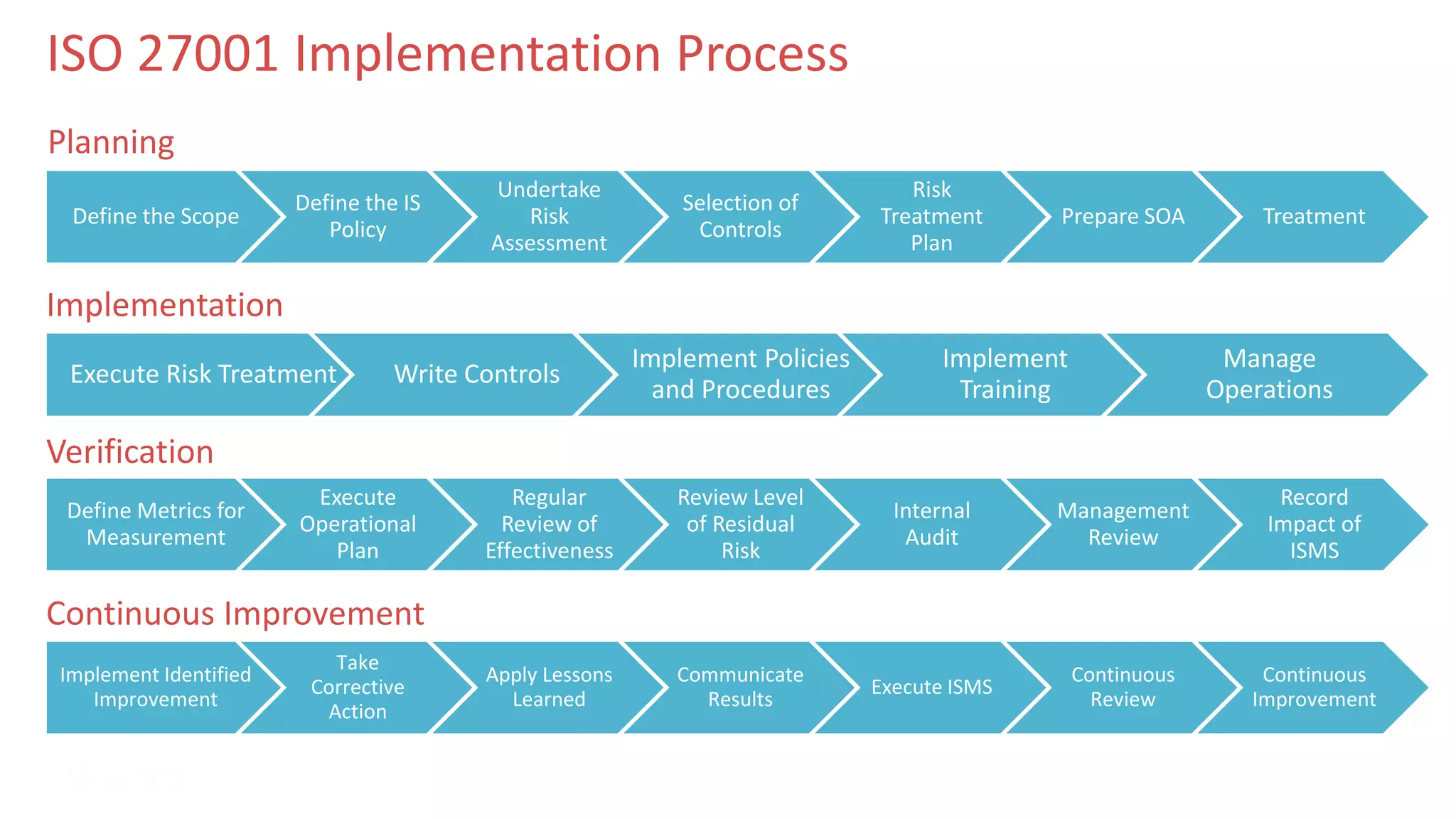
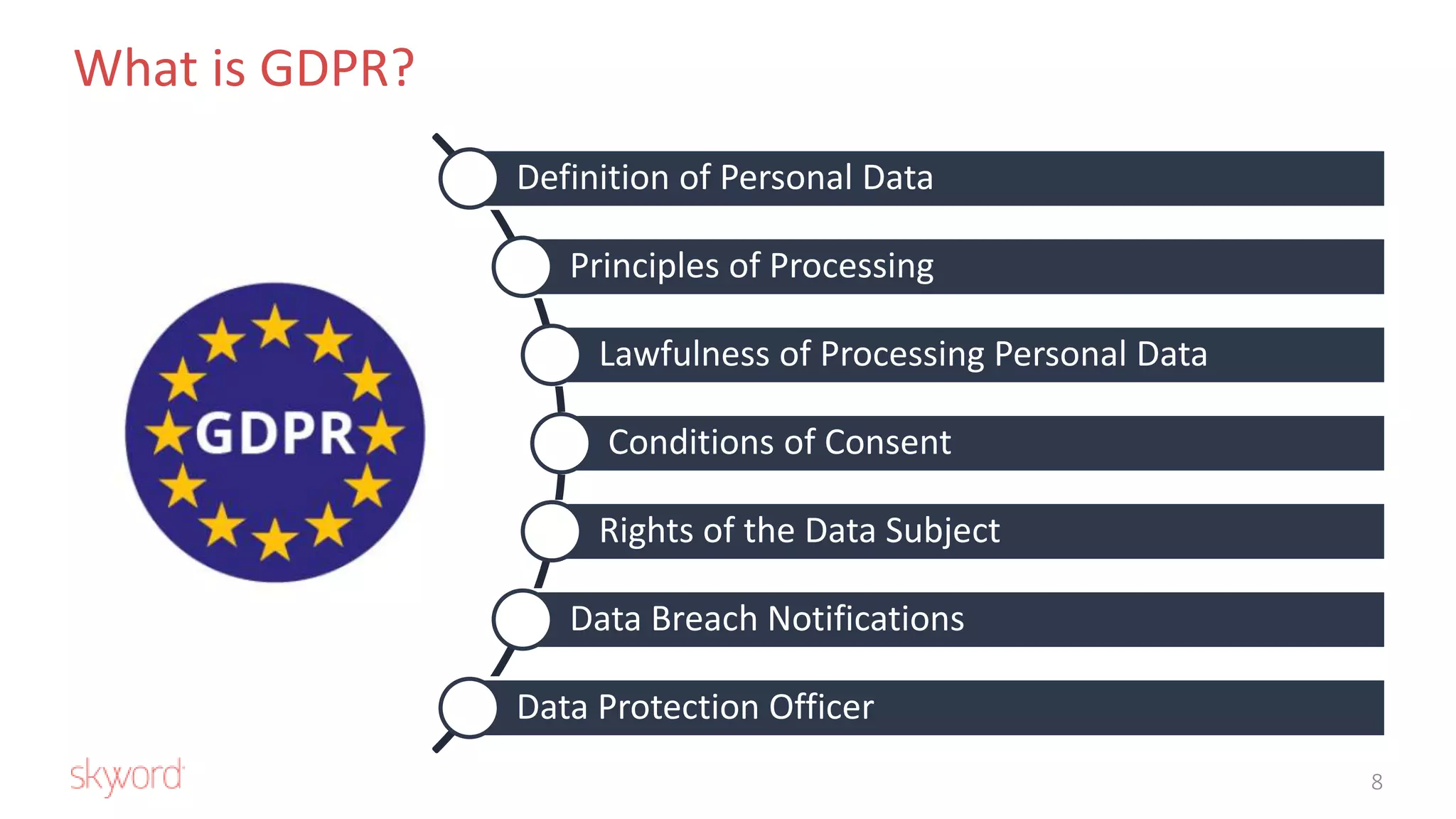
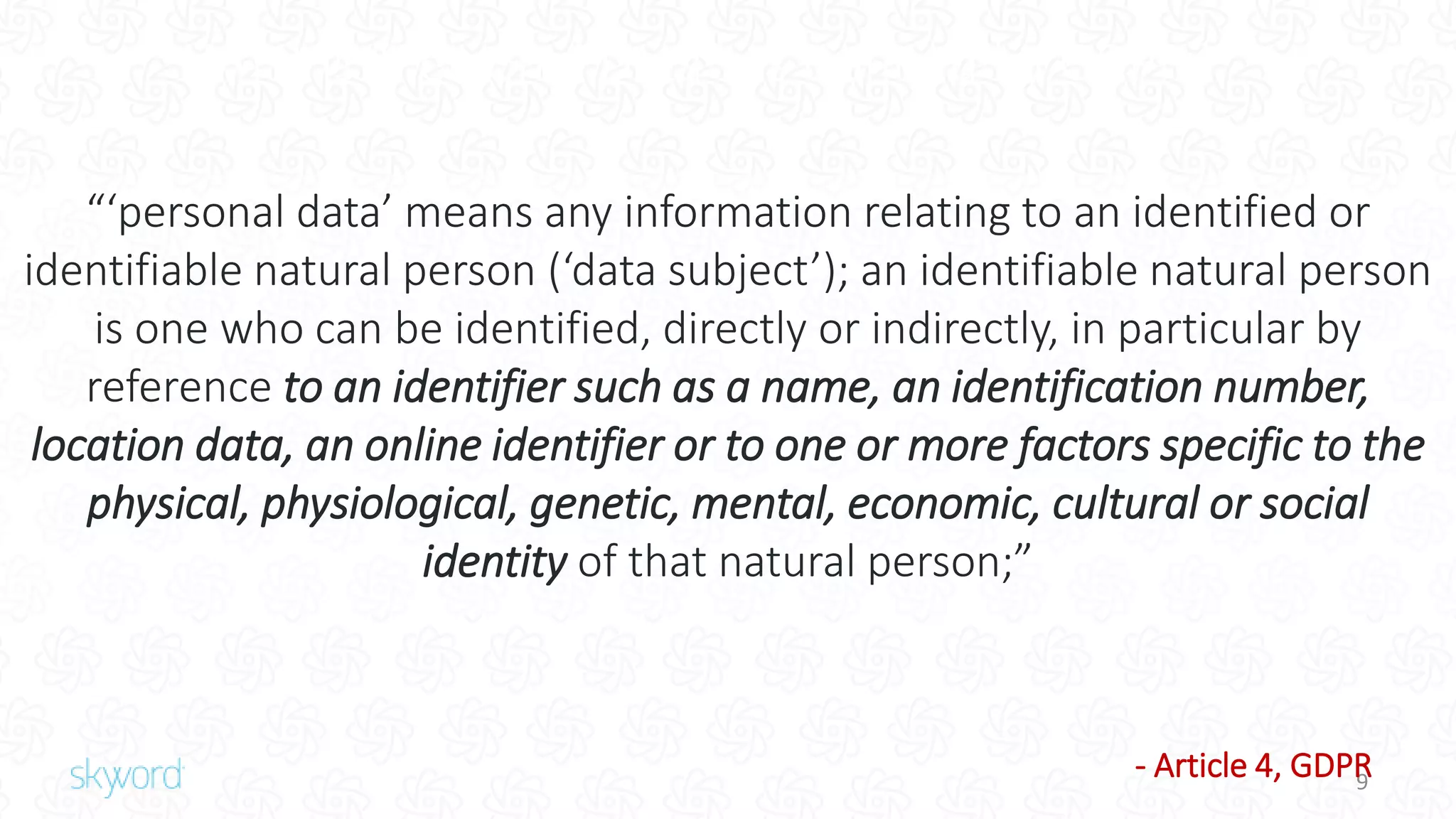
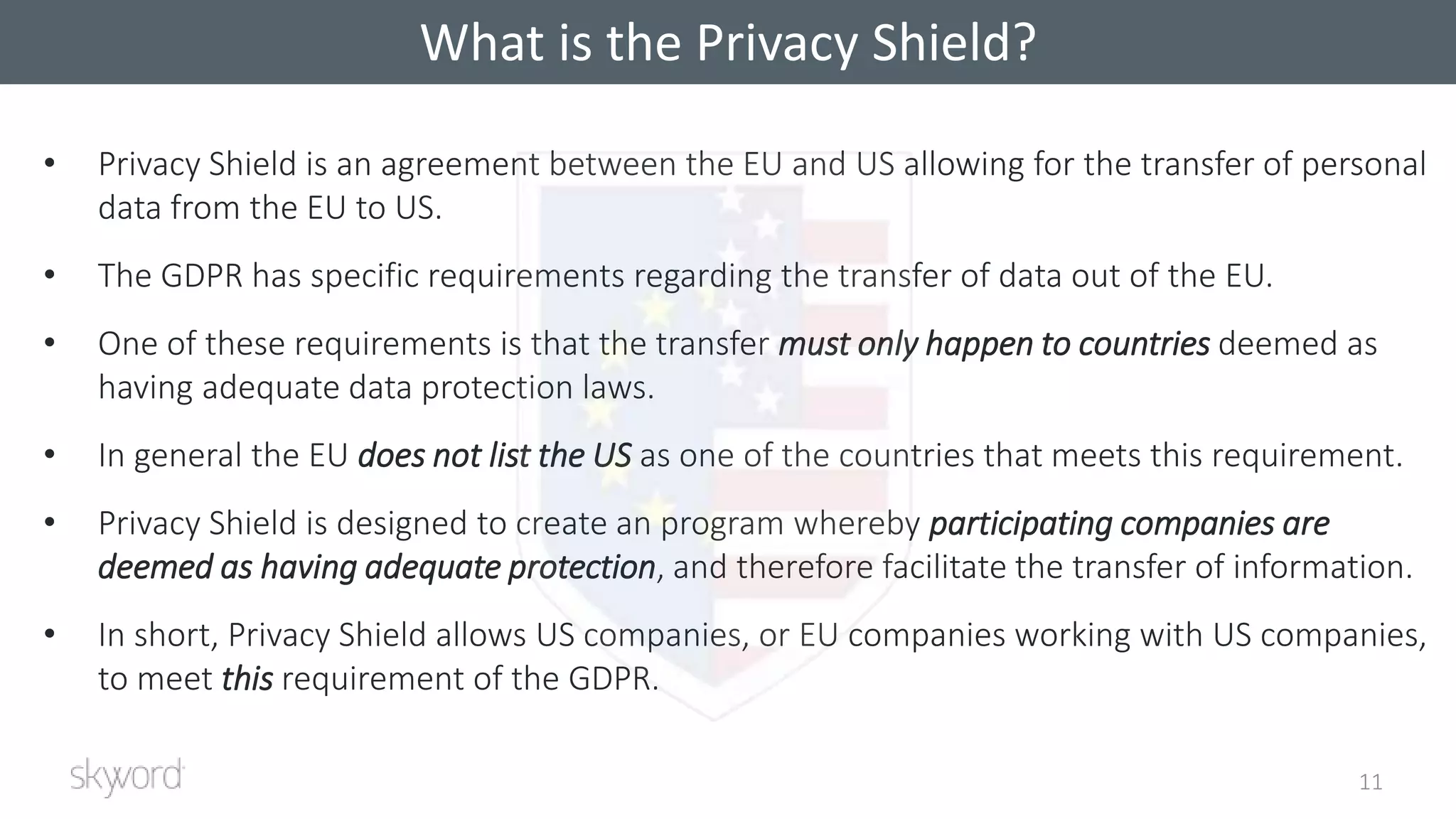
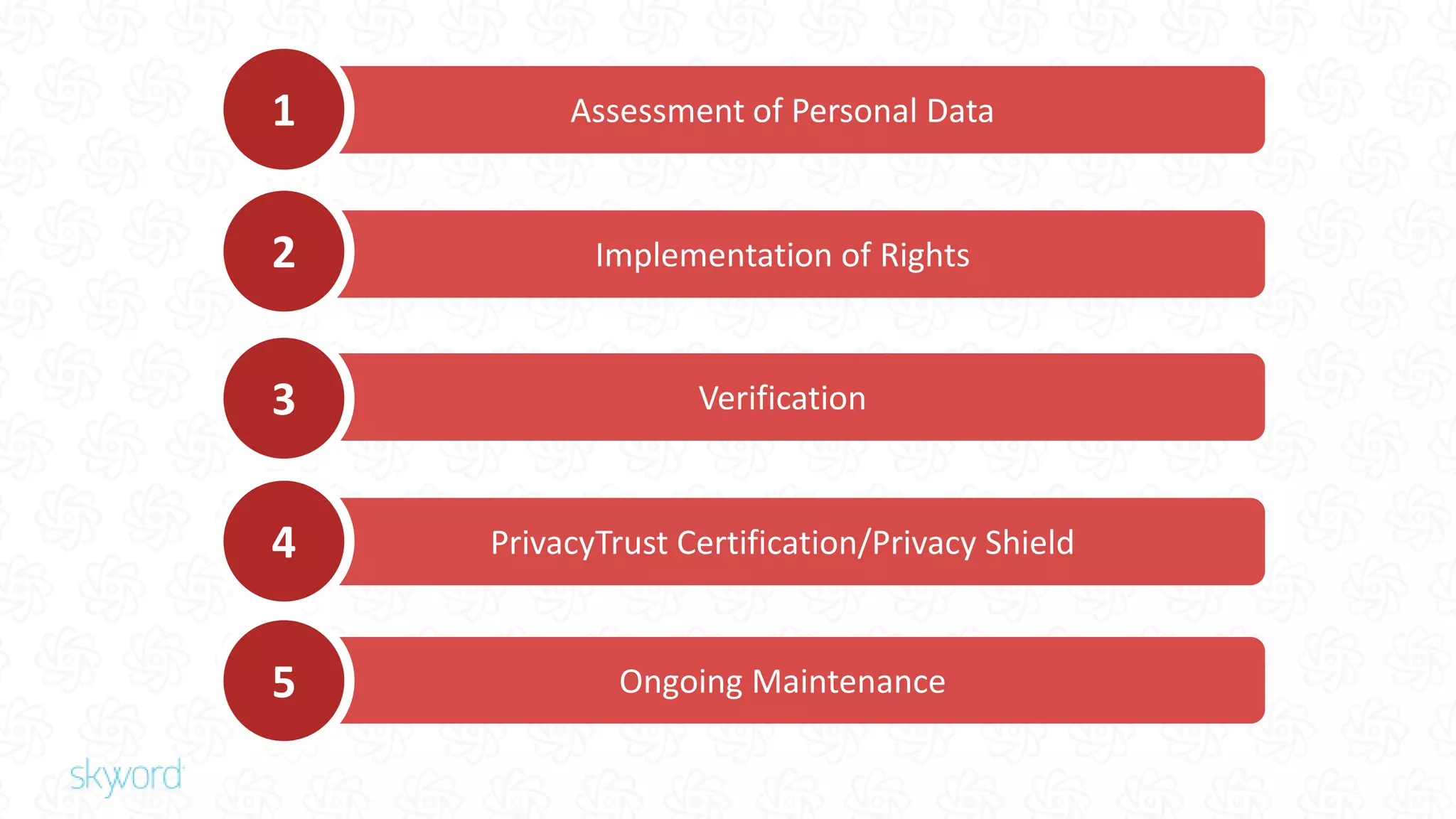
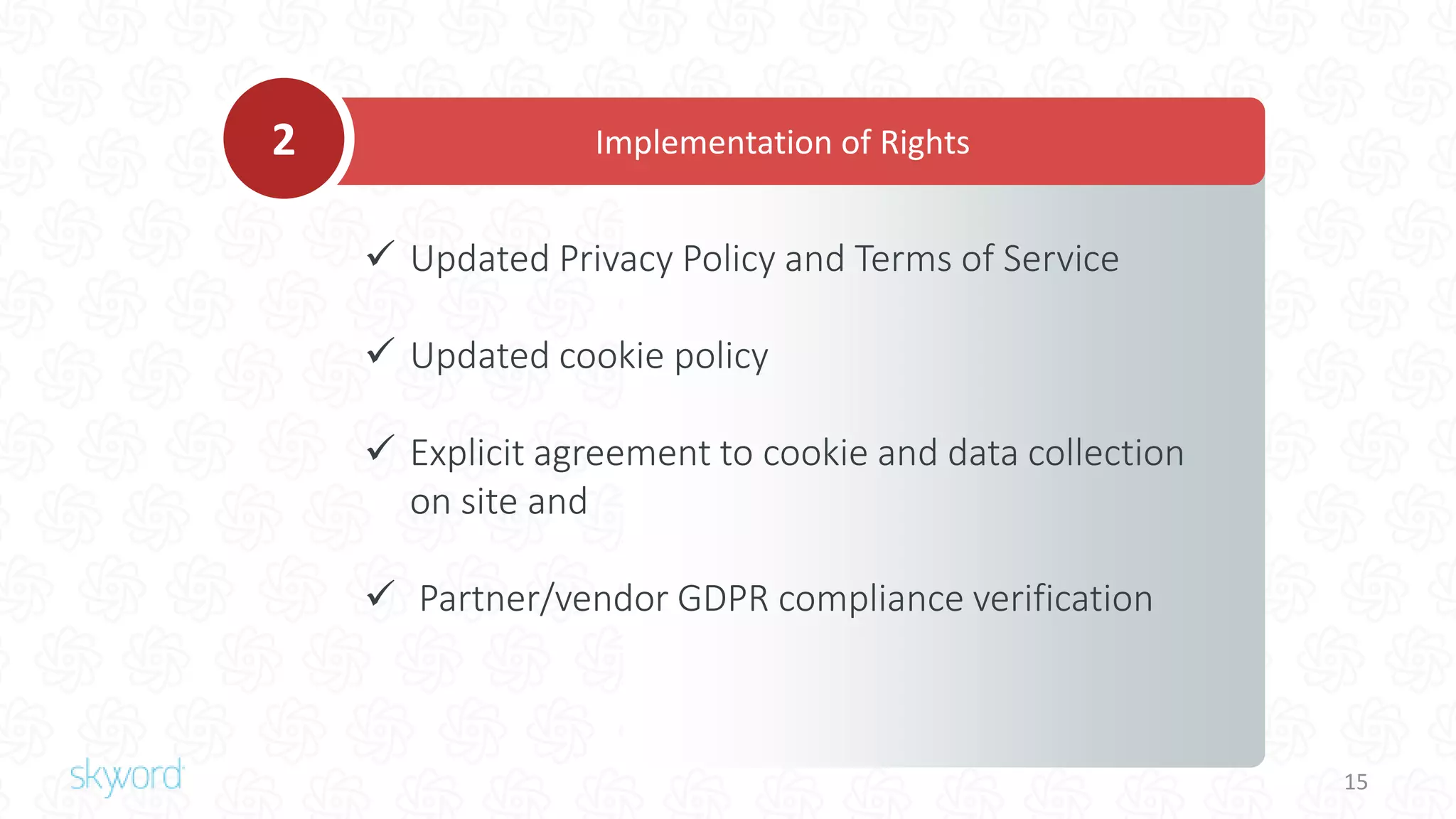
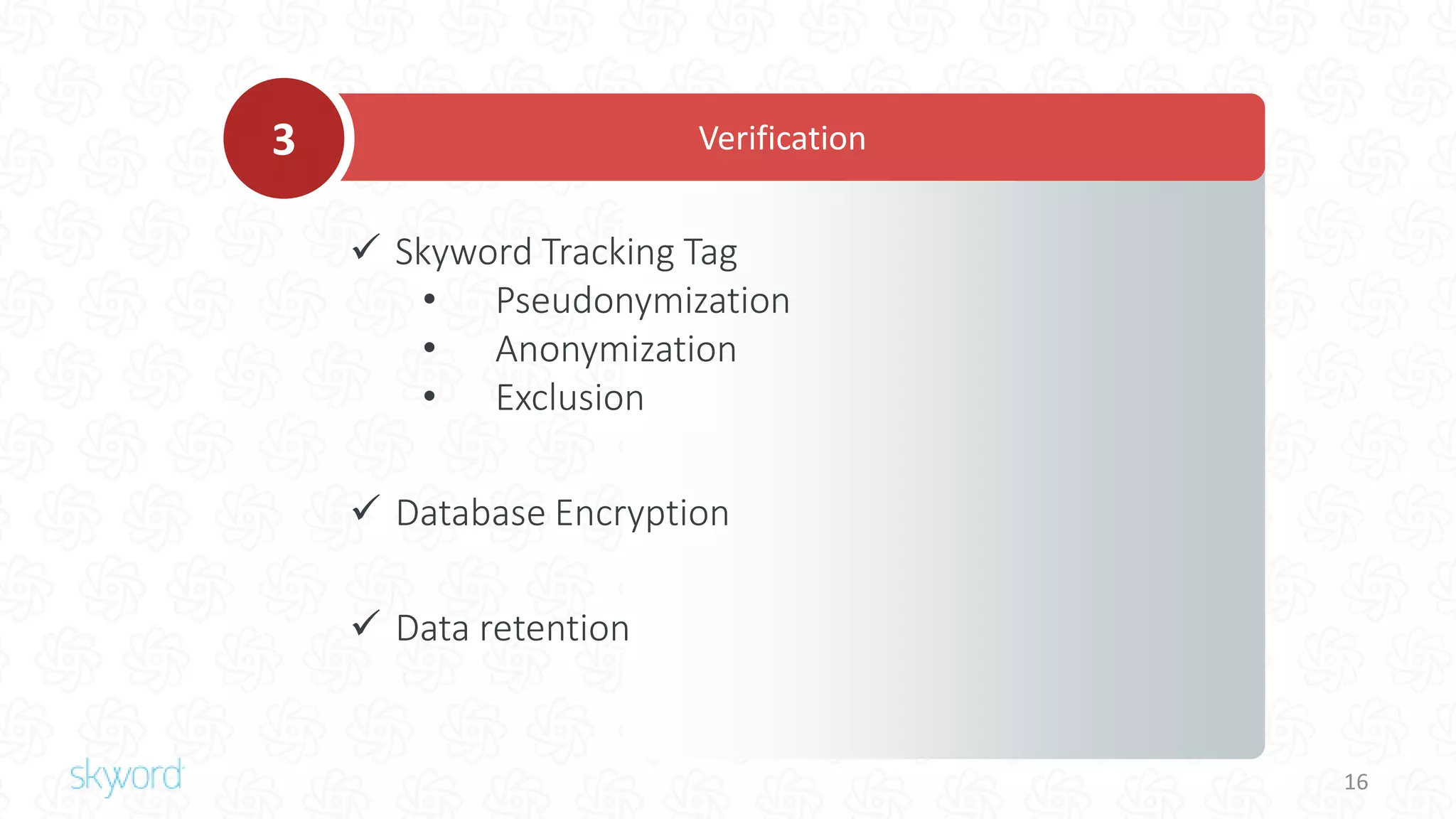
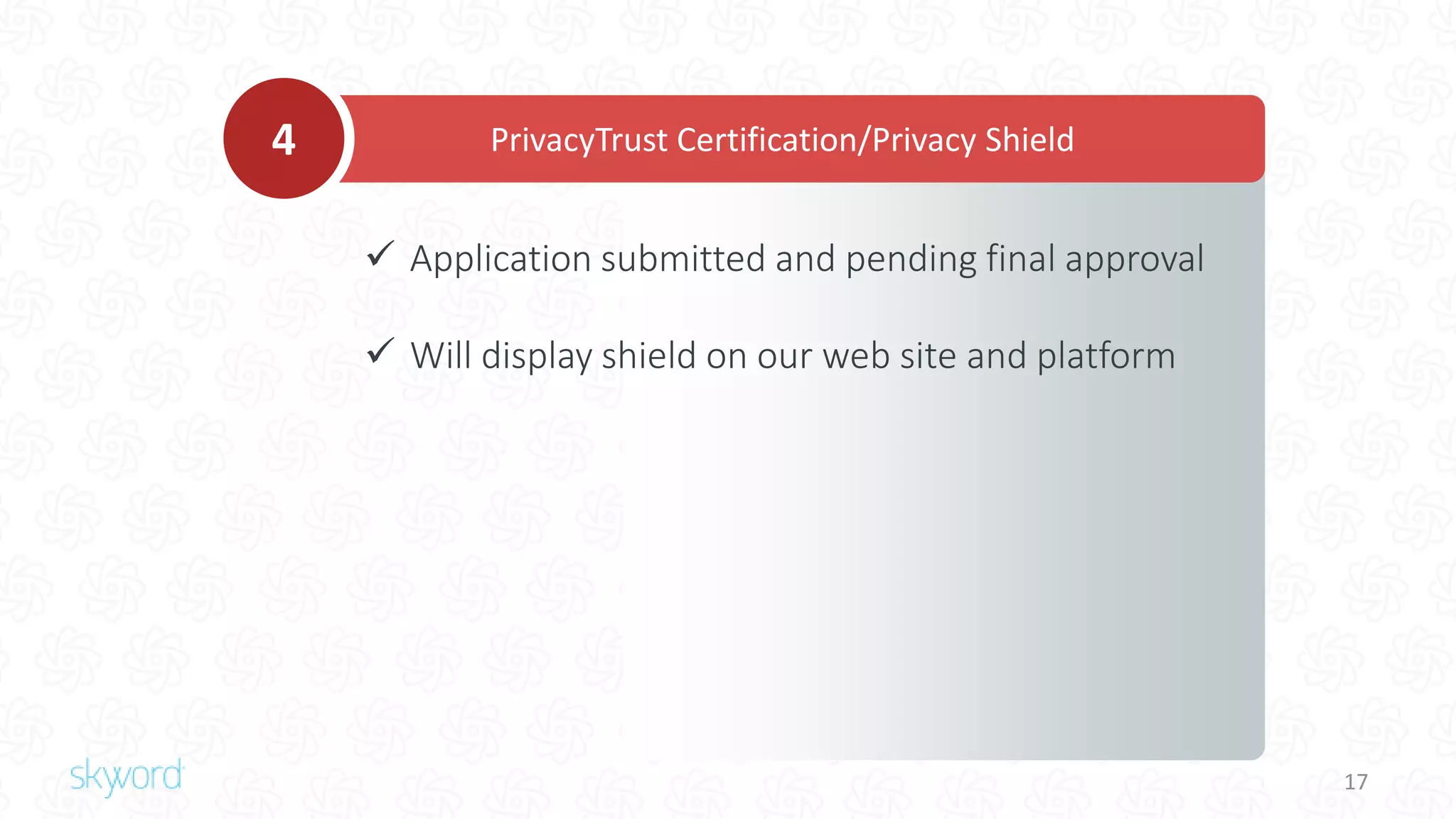
The document outlines Skyword's commitment to security and GDPR compliance, emphasizing ISO 27001 standards and the importance of protecting personal data. It details Skyword's action plan, which includes a comprehensive data audit, policy updates, and processes for handling data subject rights and inquiries. Additionally, the document describes the Privacy Shield agreement, which facilitates the transfer of personal data between the EU and US while ensuring adequate protection measures are in place.