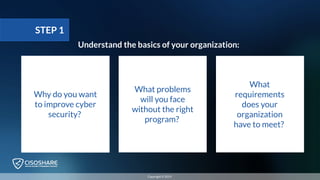
The document outlines the key considerations for choosing a virtual Chief Information Security Officer (vCISO), an outsourced security role pivotal for leading cyber security programs. It emphasizes five steps: educating oneself about the organization's needs, assessing the current security state, exploring options for the vCISO role, communicating findings to stakeholders, and making an informed decision. Additionally, it describes various service providers and stresses the importance of understanding budgetary constraints and different outsourcing models.