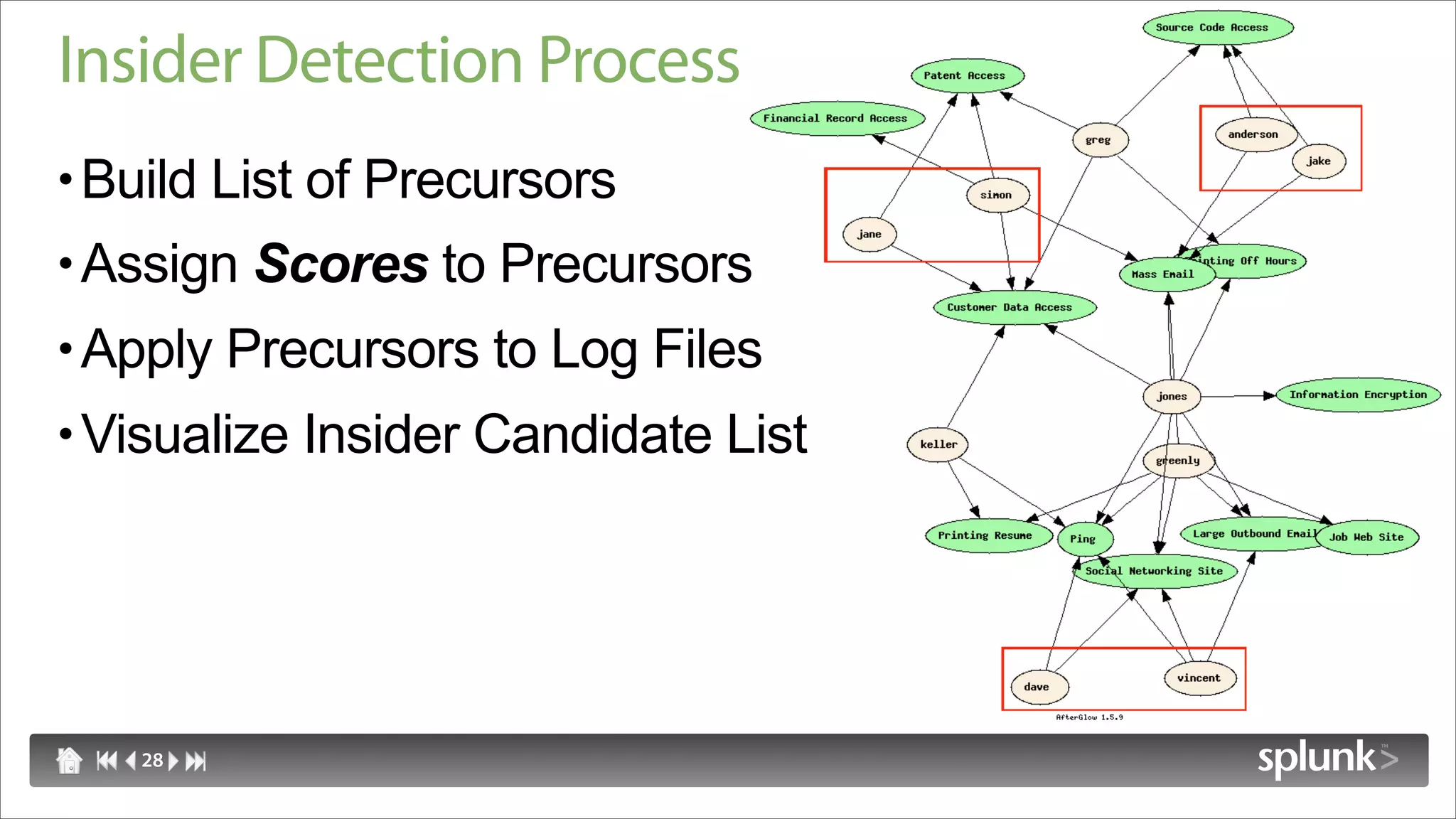
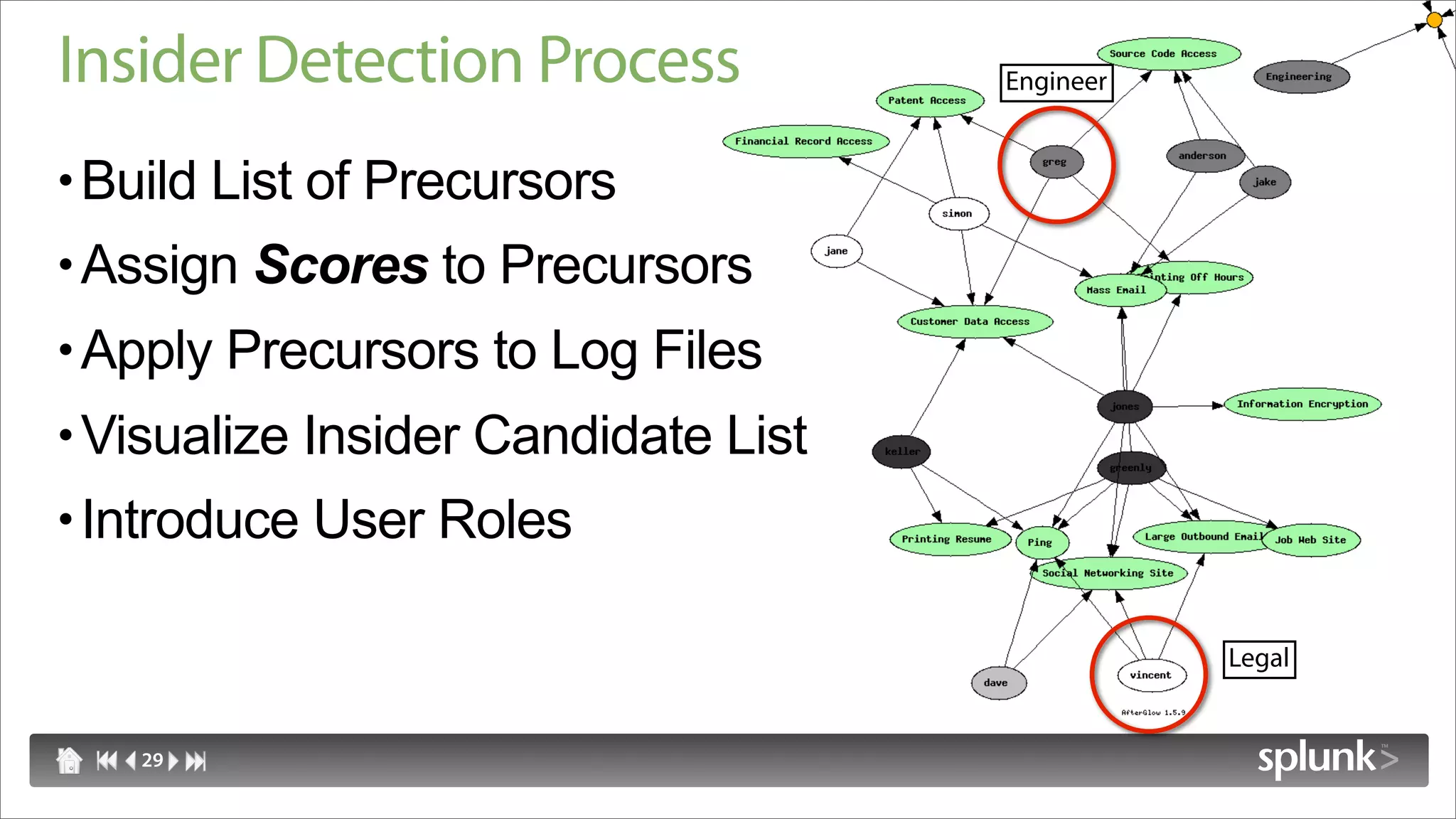
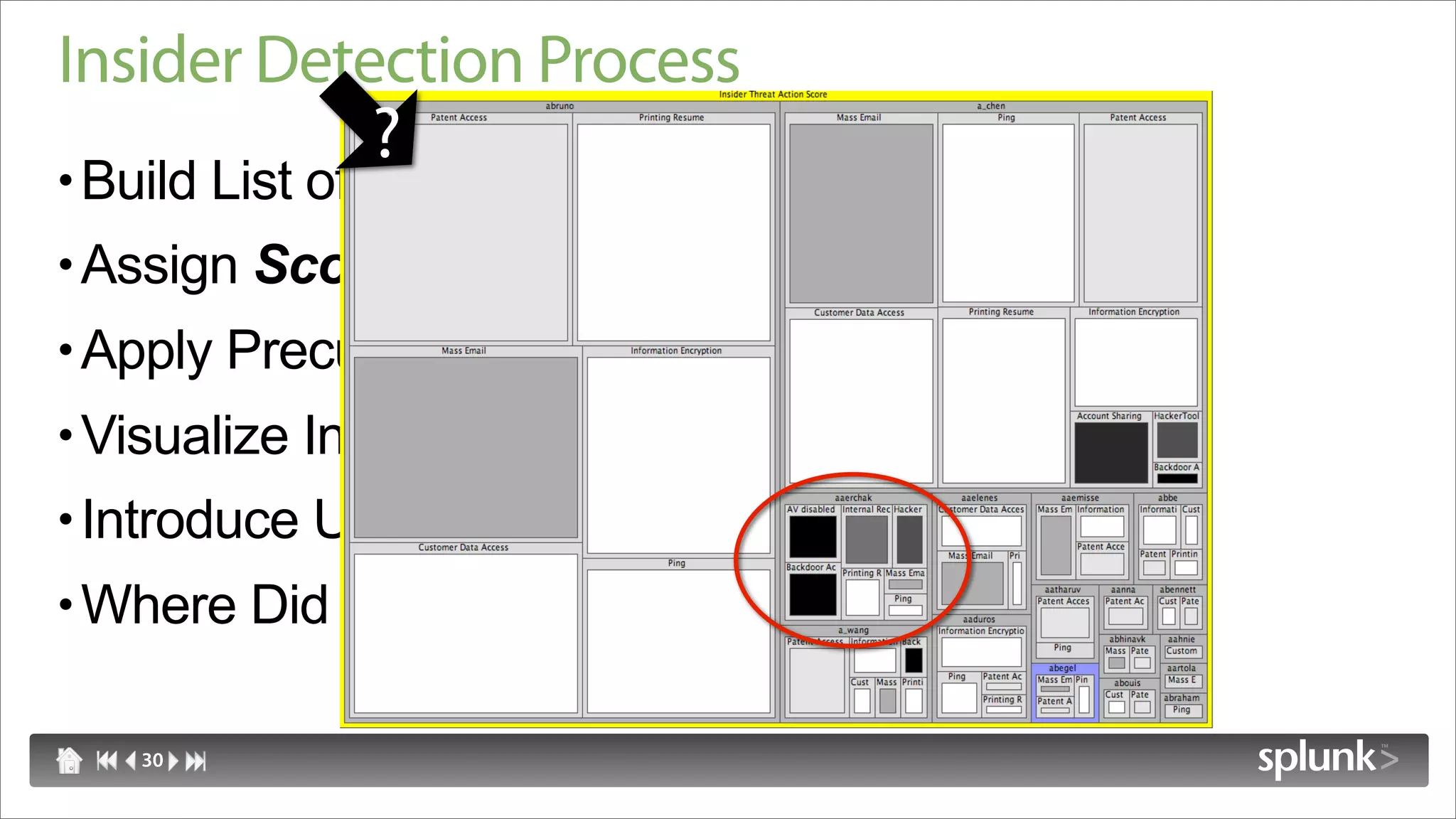
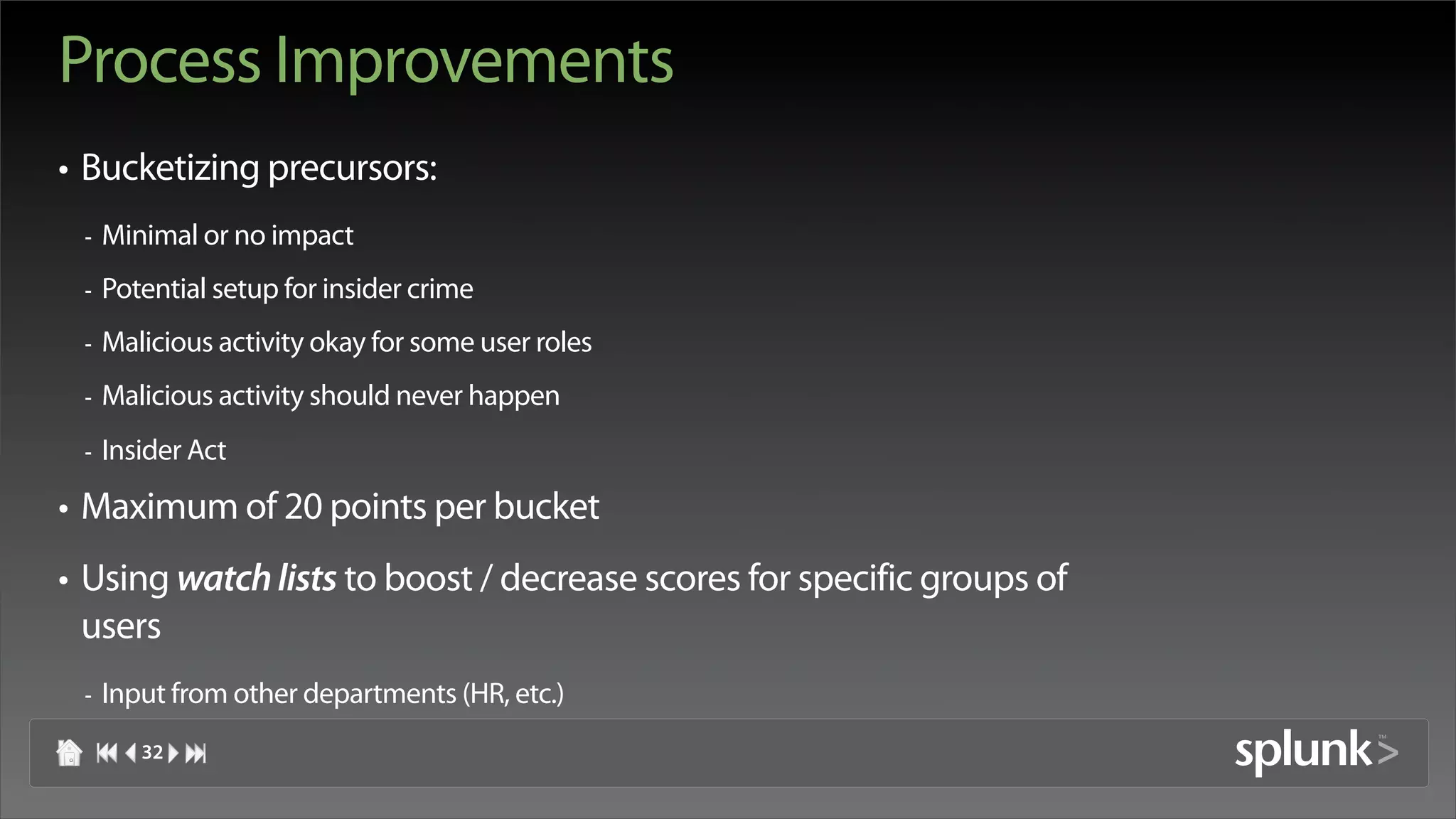
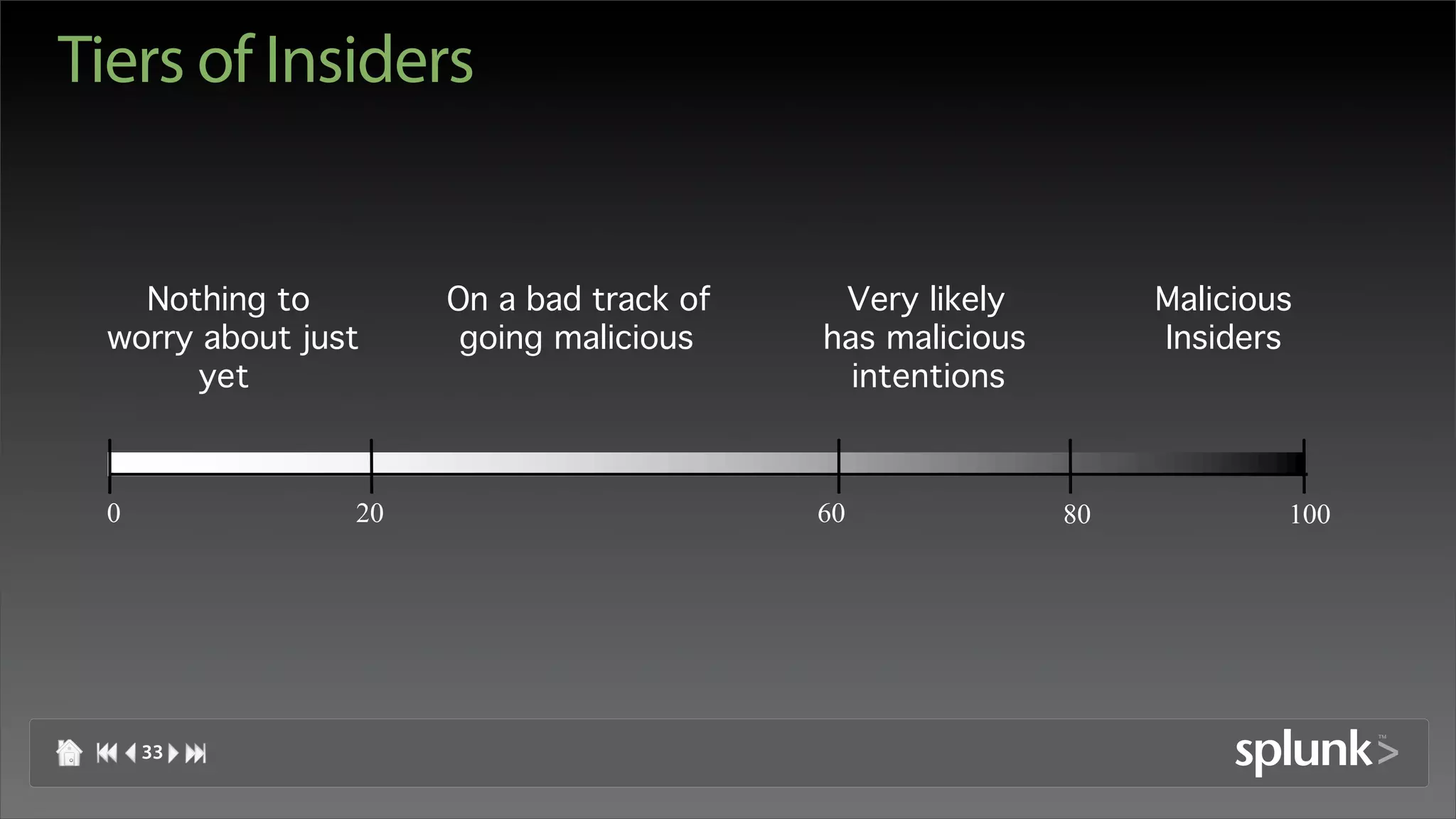
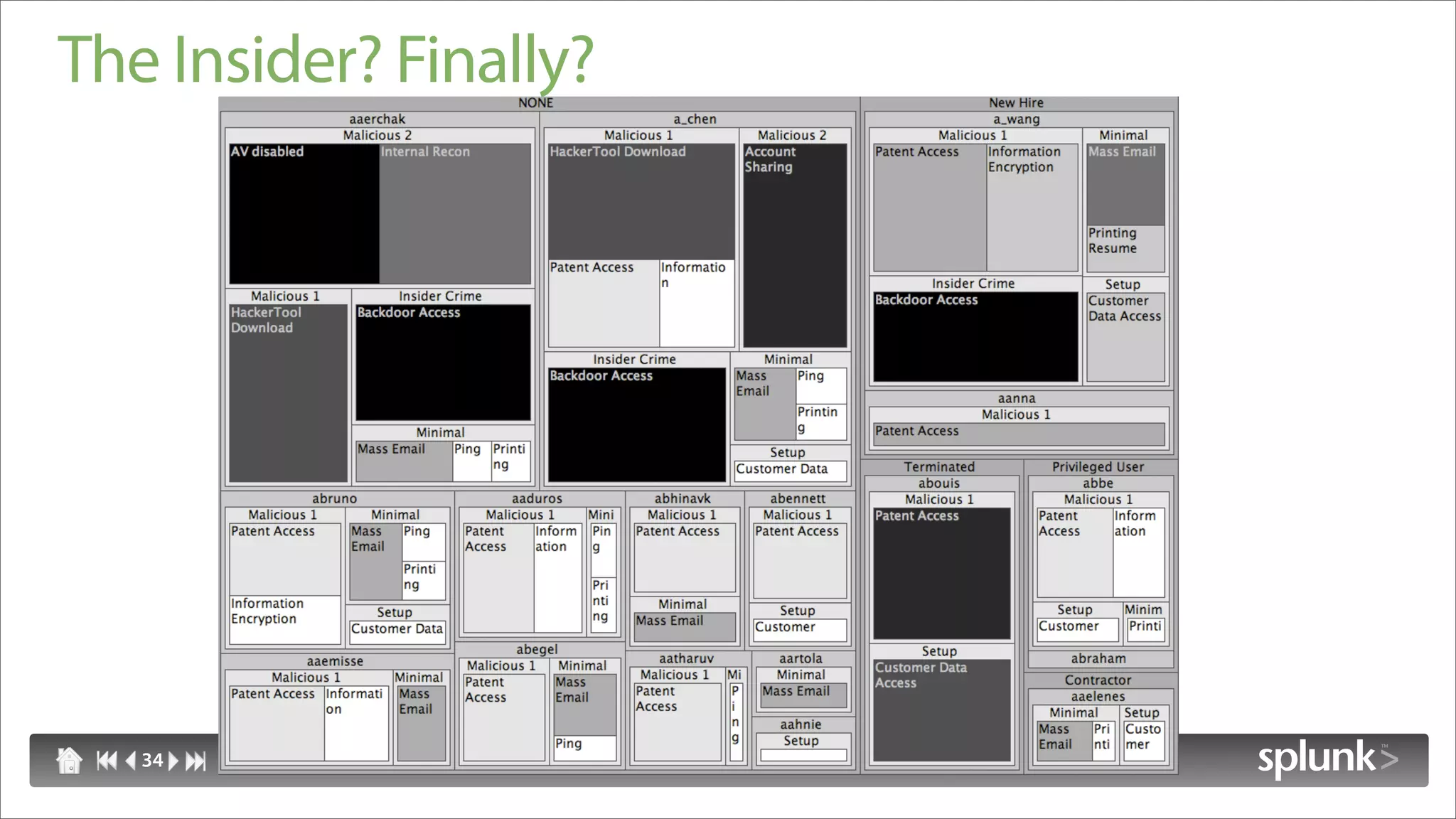
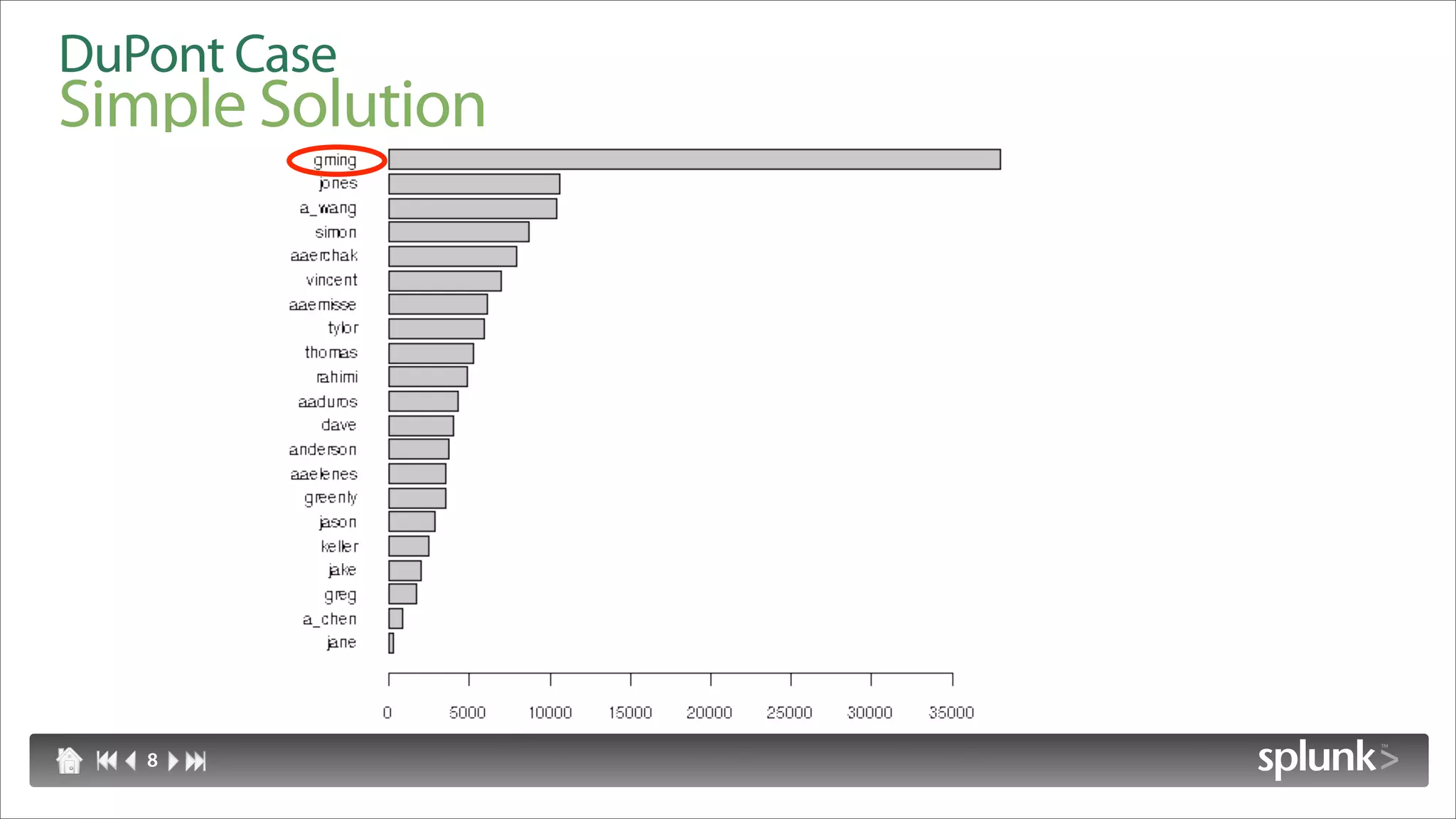
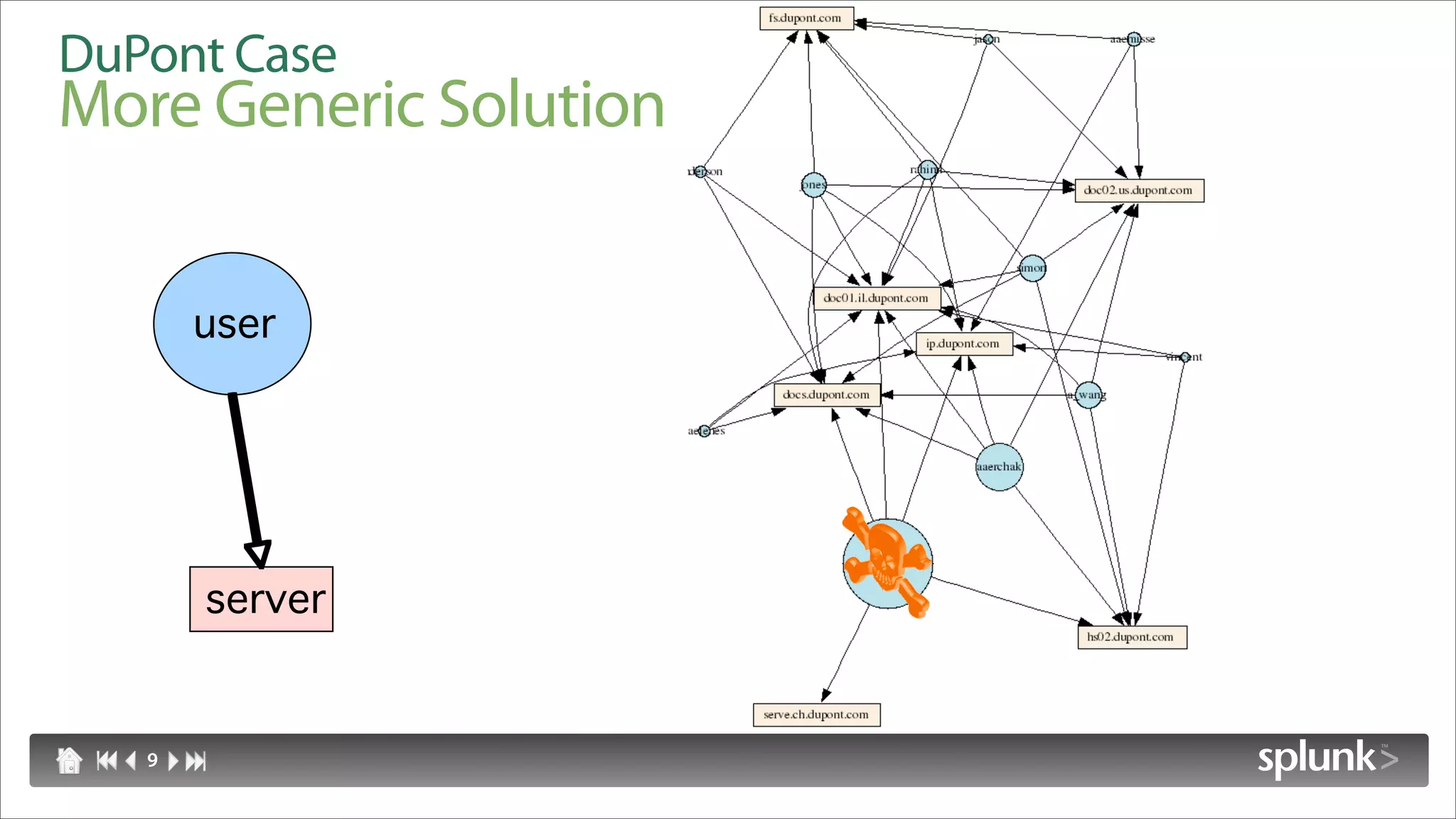
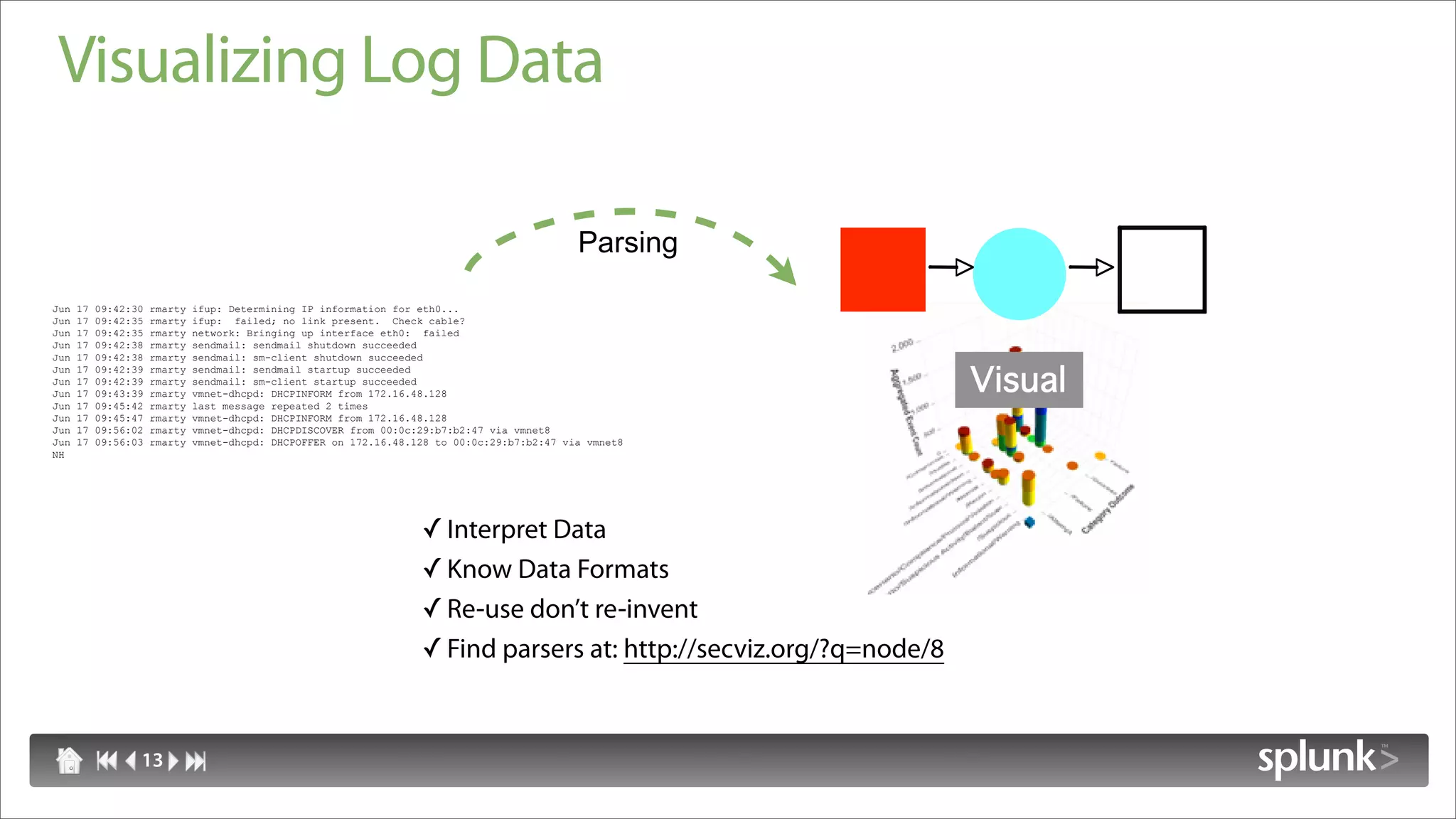
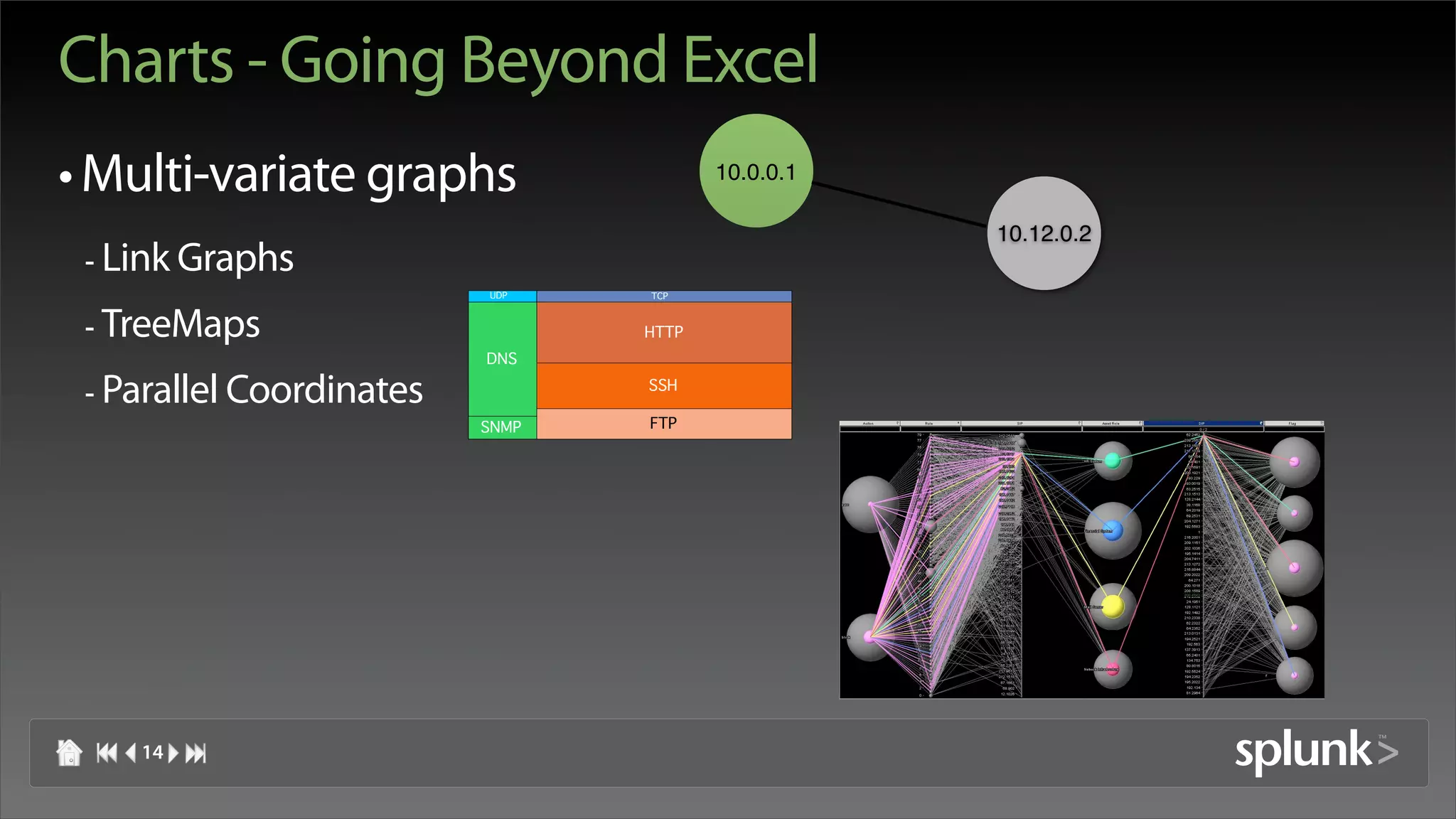
Raffael Marty discusses using log visualization to detect insider threats. He outlines an insider detection process that involves building a list of precursor activities, assigning them scores, applying the precursors to log files, and visualizing results to surface insider candidates. Visualization helps analyze data access patterns, financial transactions, and tune the detection process by grouping similar user behaviors. Improvements include bucketizing precursors and using watch lists to adjust user scores.






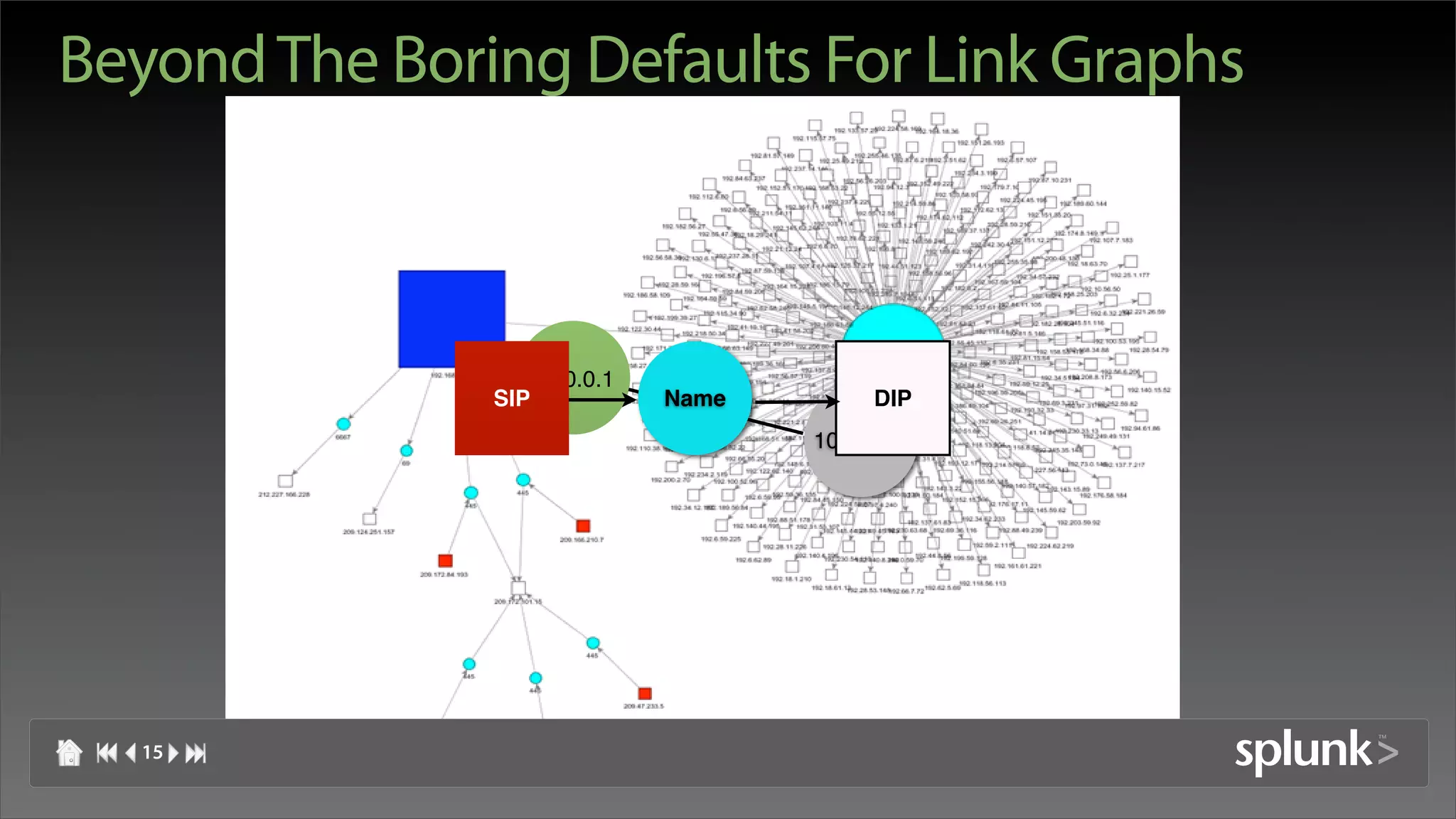
![Link Graph Shake Up
[**] [1:1923:2] RPC portmap UDP proxy attempt [**]
[Classification: Decode of an RPC Query] [Priority: 2]
06/04-15:56:28.219753 192.168.10.90:32859 -> 192.168.10.255:111
UDP TTL:64 TOS:0x0 ID:0 IpLen:20 DgmLen:148 DF
Len: 120
SIP Name DIP SIP DIP DPort
192.168.10.90 portmap 192.168.10.255 192.168.10.90 192.168.10.255 111
SIP SPort DPort Name SIP DIP
192.168.10.90 32859 111 RPC portmap 192.168.10.90 192.168.10.255
16](https://image.slidesharecdn.com/martyvisualizationhitb07-120811210922-phpapp02/75/Insider-Threat-Visualization-HackInTheBox-2007-16-2048.jpg)
![AfterGlow http://afterglow.sourceforge.net
Parser AfterGlow Grapher
Graph
CSV File LanguageFile
digraph structs {
graph [label="AfterGlow 1.5.8", fontsize=8];
node [shape=ellipse, style=filled,
fontsize=10, width=1, height=1,
aaelenes,Printing Resume fixedsize=true];
abbe,Information Encrytion edge [len=1.6];
aanna,Patent Access
aatharuy,Ping "aaelenes" -> "Printing Resume" ;
"abbe" -> "Information Encryption" ;
"aanna" -> "Patent Access" ;
"aatharuv" -> "Ping" ;
}
20](https://image.slidesharecdn.com/martyvisualizationhitb07-120811210922-phpapp02/75/Insider-Threat-Visualization-HackInTheBox-2007-20-2048.jpg)
![Why AfterGlow?
# Variable and Color
• Translates CSV into graph description
variable=@violation=("Backdoor Access", "HackerTool
Download”);
color.target="orange" if (grep(/$fields[1]/,@violation));
• Define node and edge attributes color.target="palegreen"
- color # Node Size and Threshold
- size maxnodesize=1;
size.source=$fields[2]
- shape size=0.5
sum.target=0;
• Filter and process data entries threshold.source=14;
- threshold filter Fan Out: 3 # Color and Cluster
color.source="palegreen" if ($fields[0] =~ /^111/)
- fan-out filter color.source="red"
color.target="palegreen"
- clustering cluster.source=regex_replace("(d+).d+")."/8"
21](https://image.slidesharecdn.com/martyvisualizationhitb07-120811210922-phpapp02/75/Insider-Threat-Visualization-HackInTheBox-2007-21-2048.jpg)
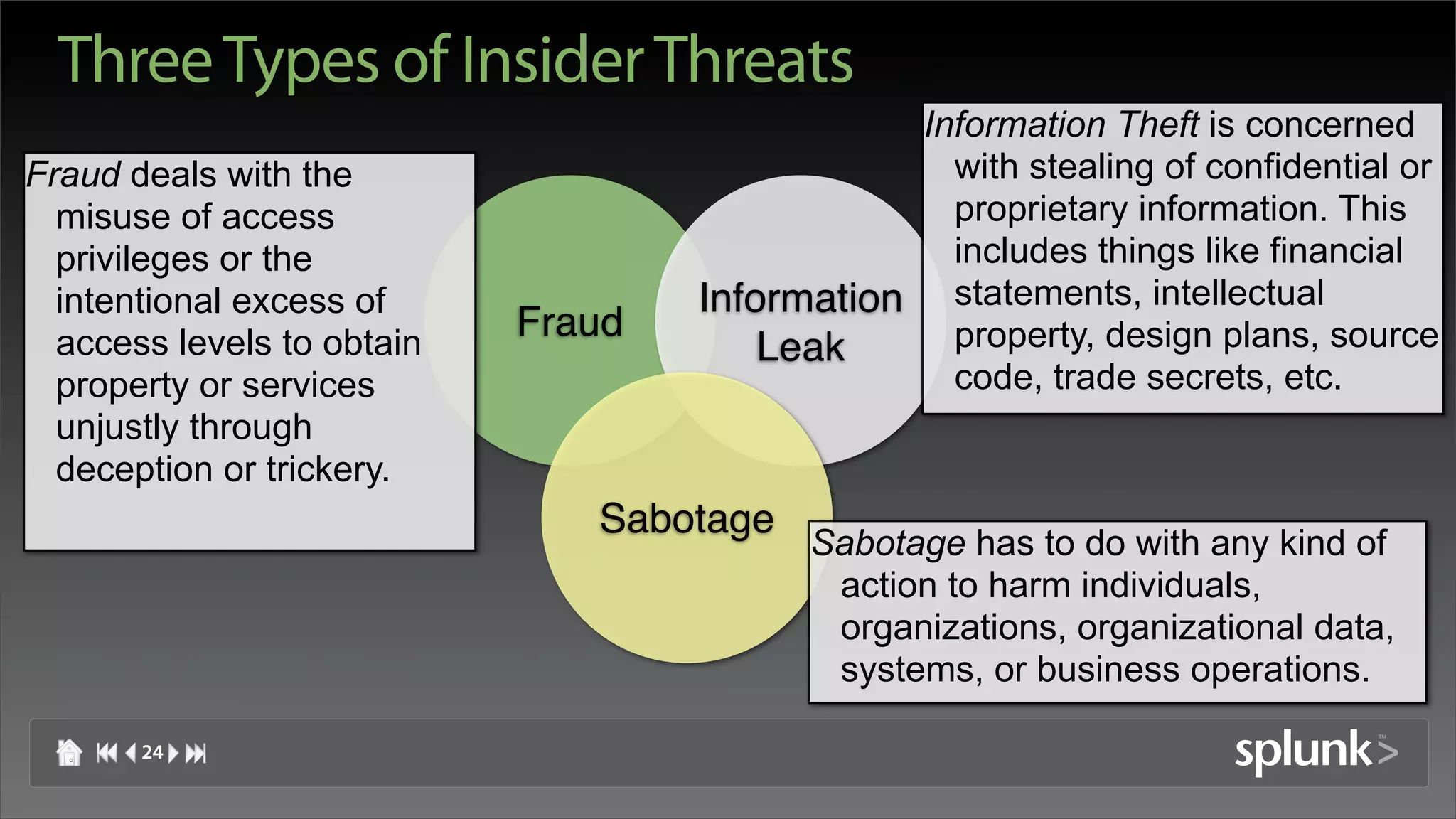
![Insider Threat Definition
"Current or former employee or contractor who
• intentionally exceeded or misused an authorized level of
access to networks, systems or data in a manner that
• targeted a specific individual or affected the security of
the organization’s data, systems and/or daily business
operations"
[CERT: http://www.cert.org/insider_threat Definition of an Insider]
23](https://image.slidesharecdn.com/martyvisualizationhitb07-120811210922-phpapp02/75/Insider-Threat-Visualization-HackInTheBox-2007-23-2048.jpg)
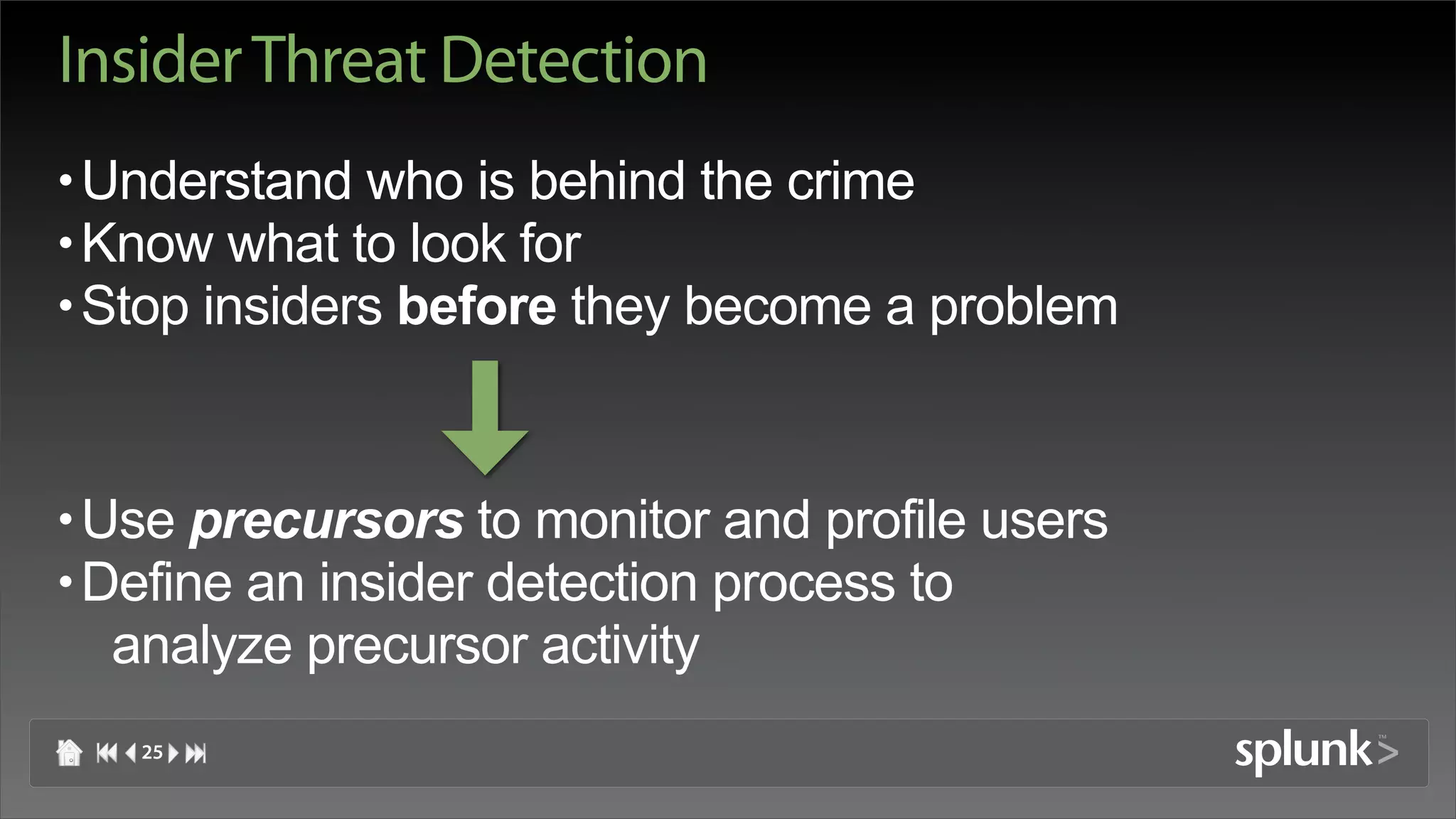
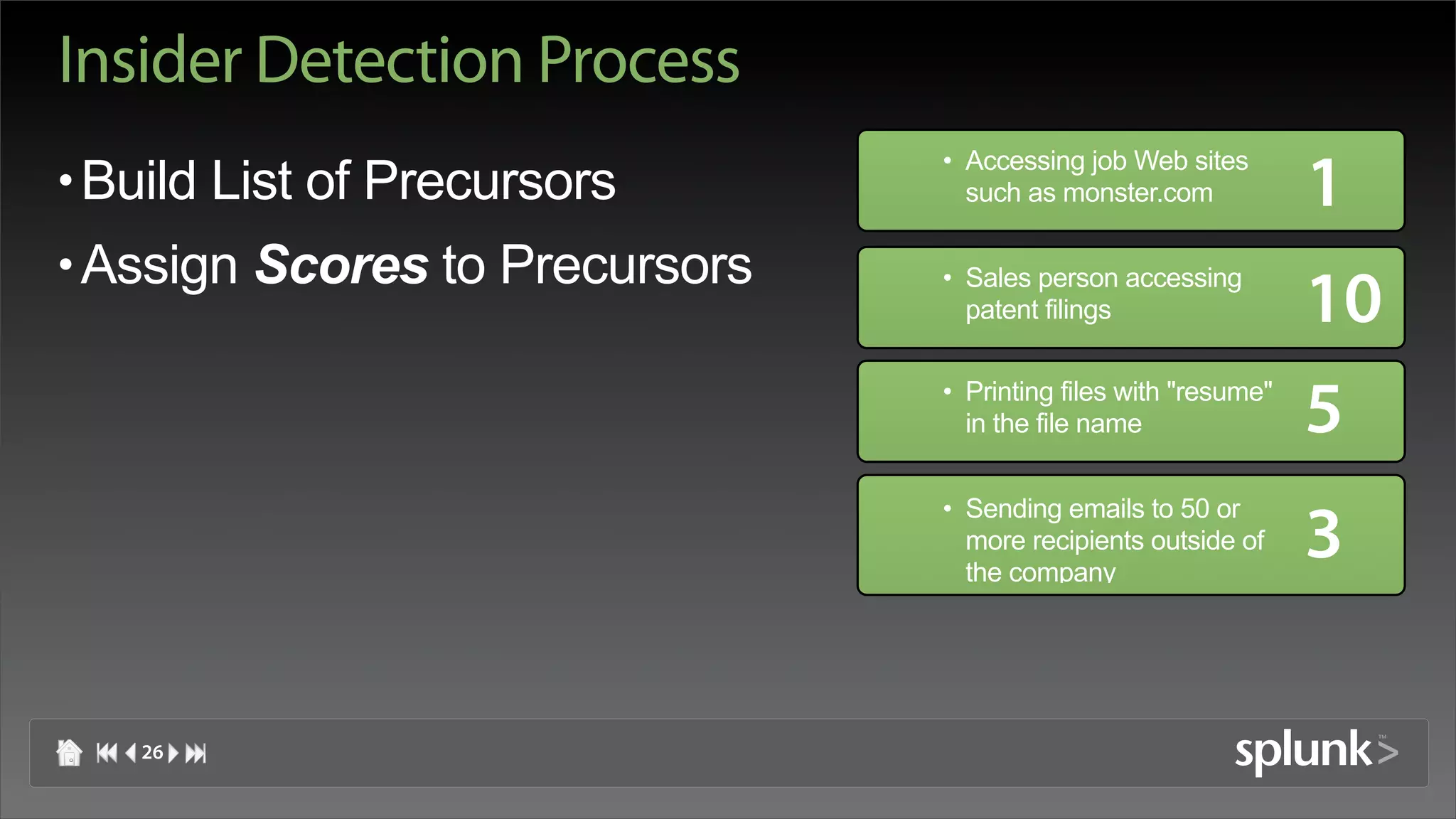
![Insider Detection Process
Aug 31 15:57:23 [68] ram kCGErrorIllegalArgument:
• Build List of Precursors CGXGetWindowDepth: Invalid window -1
Aug 31 15:58:06 [68] cmd "loginwindow" (0x5c07)
set hot key operating mode to all disabled
• Assign Scores to Precursors Aug 31 15:58:06 [68] Hot key operating mode is now
all disabled
• Apply Precursors to Log Files Aug 27 10:21:39 ram com.apple.SecurityServer:
authinternal failed to authenticate user
raffaelmarty.
Aug 27 10:21:39 ram com.apple.SecurityServer:
Failed to authorize right system.login.tty by process /
usr/bin/su
do for authorization created by /usr/bin/sudo.
Apr 04 19:45:29 rmarty Privoxy(b65ddba0)
Request: www.google.com/search?q=password
+cracker
27](https://image.slidesharecdn.com/martyvisualizationhitb07-120811210922-phpapp02/75/Insider-Threat-Visualization-HackInTheBox-2007-27-2048.jpg)