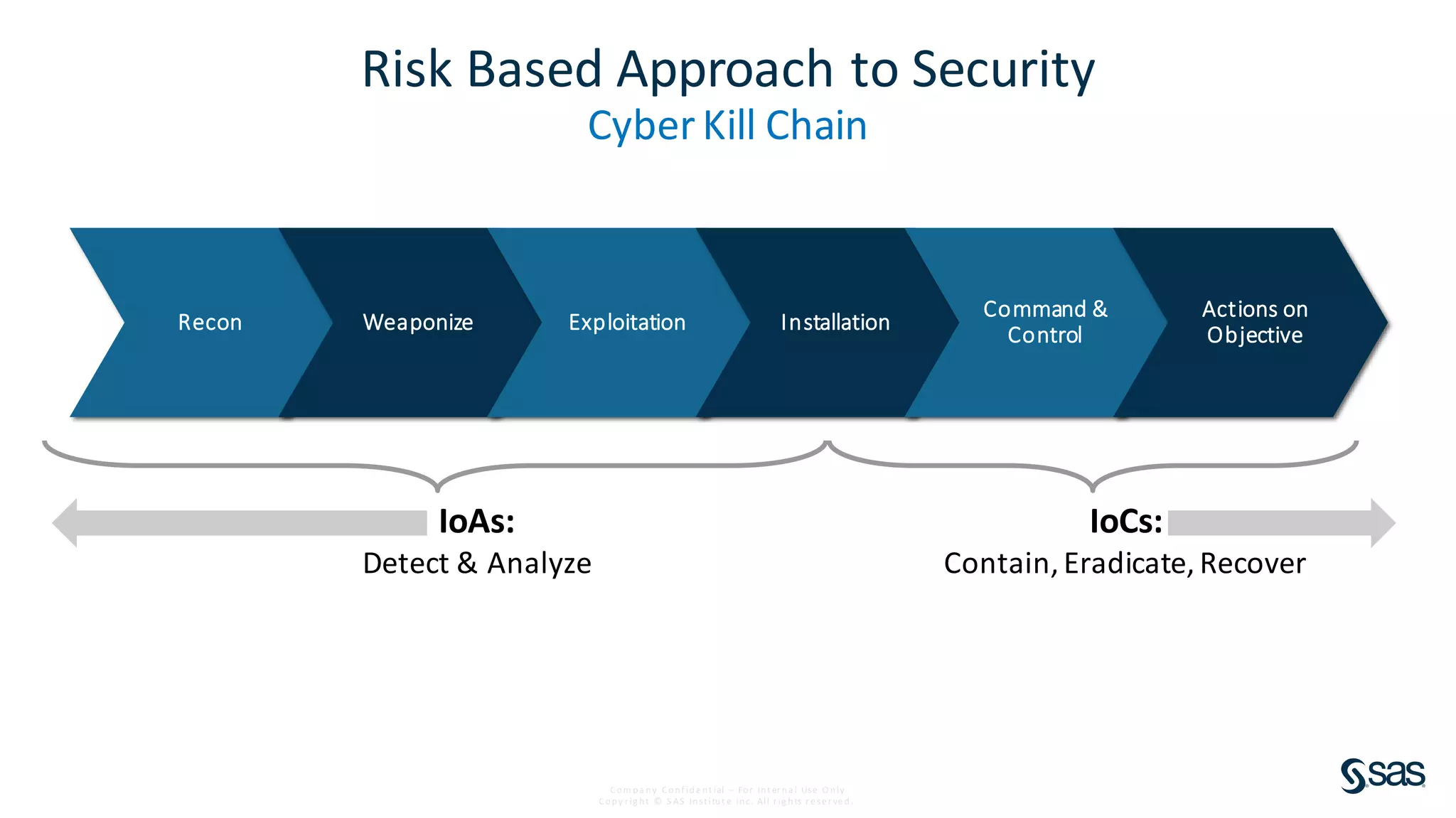
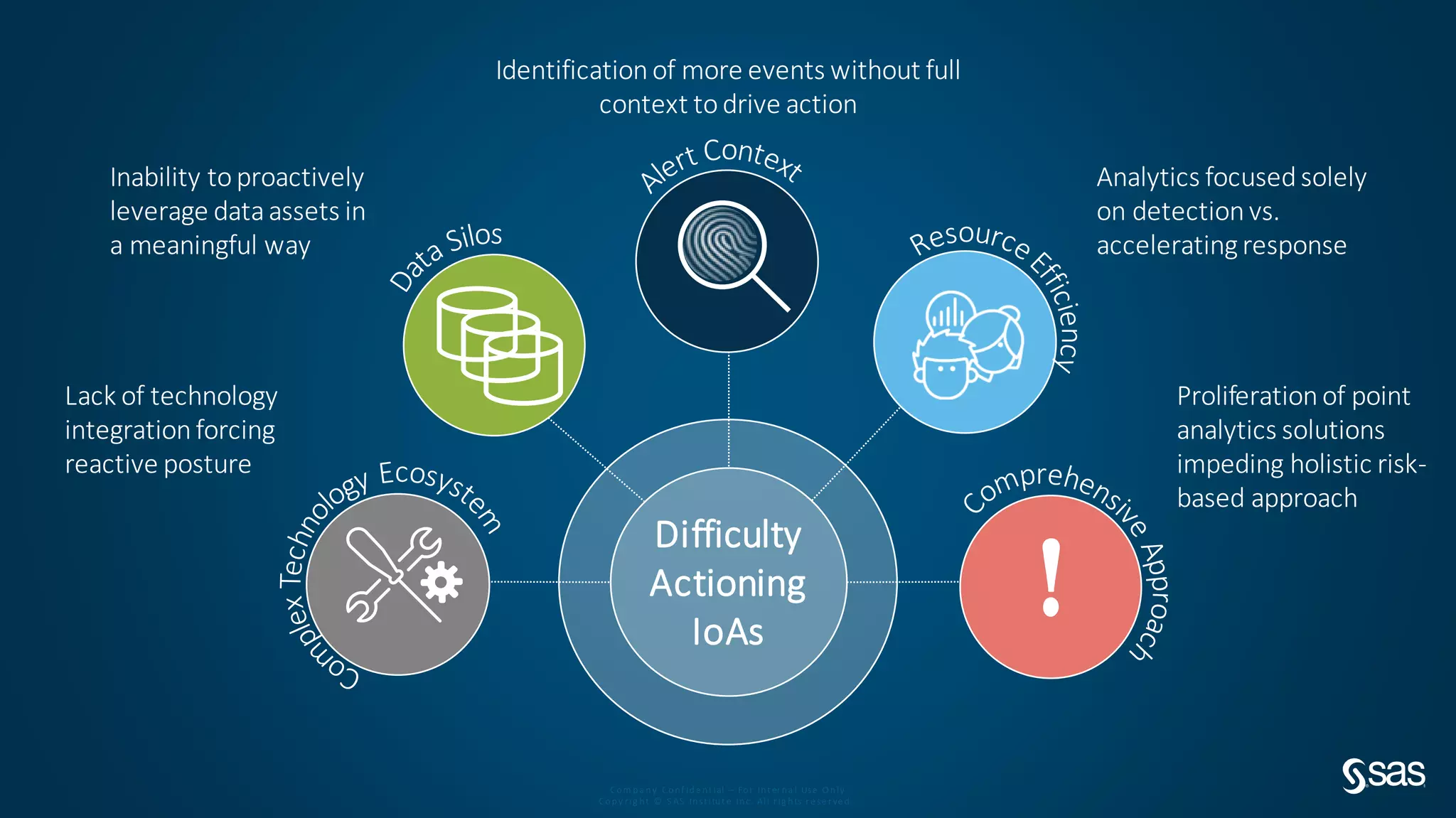
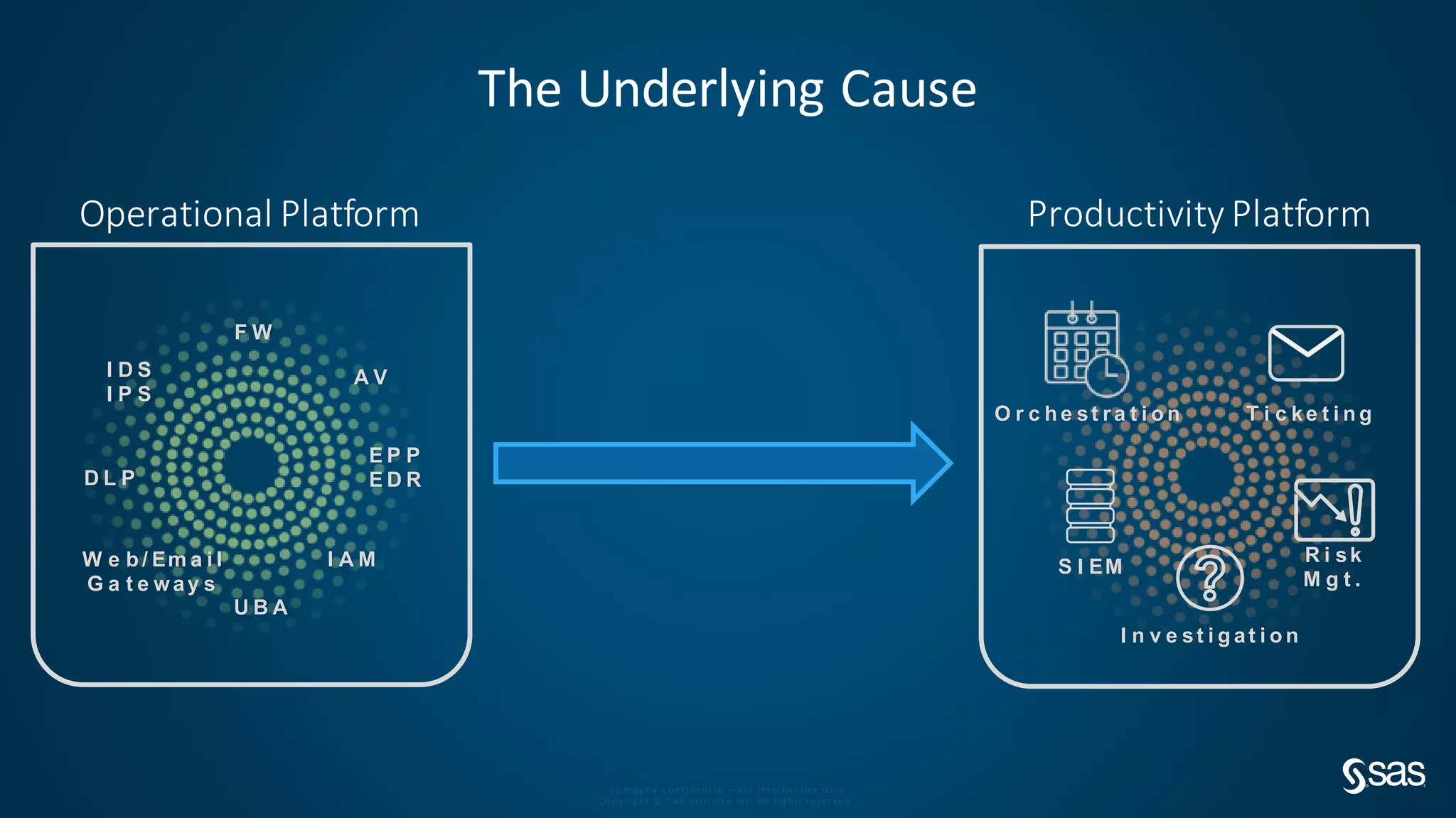
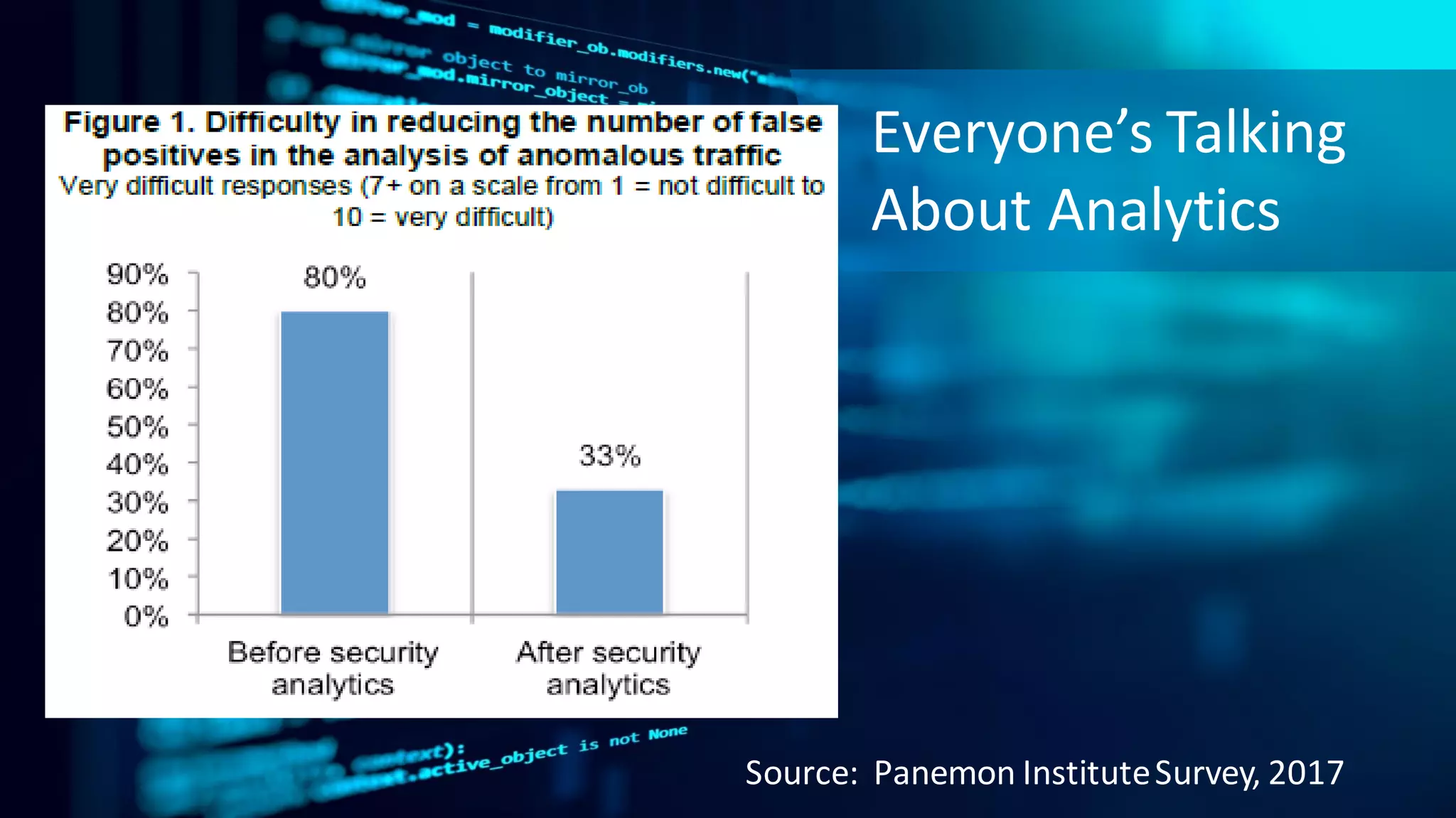
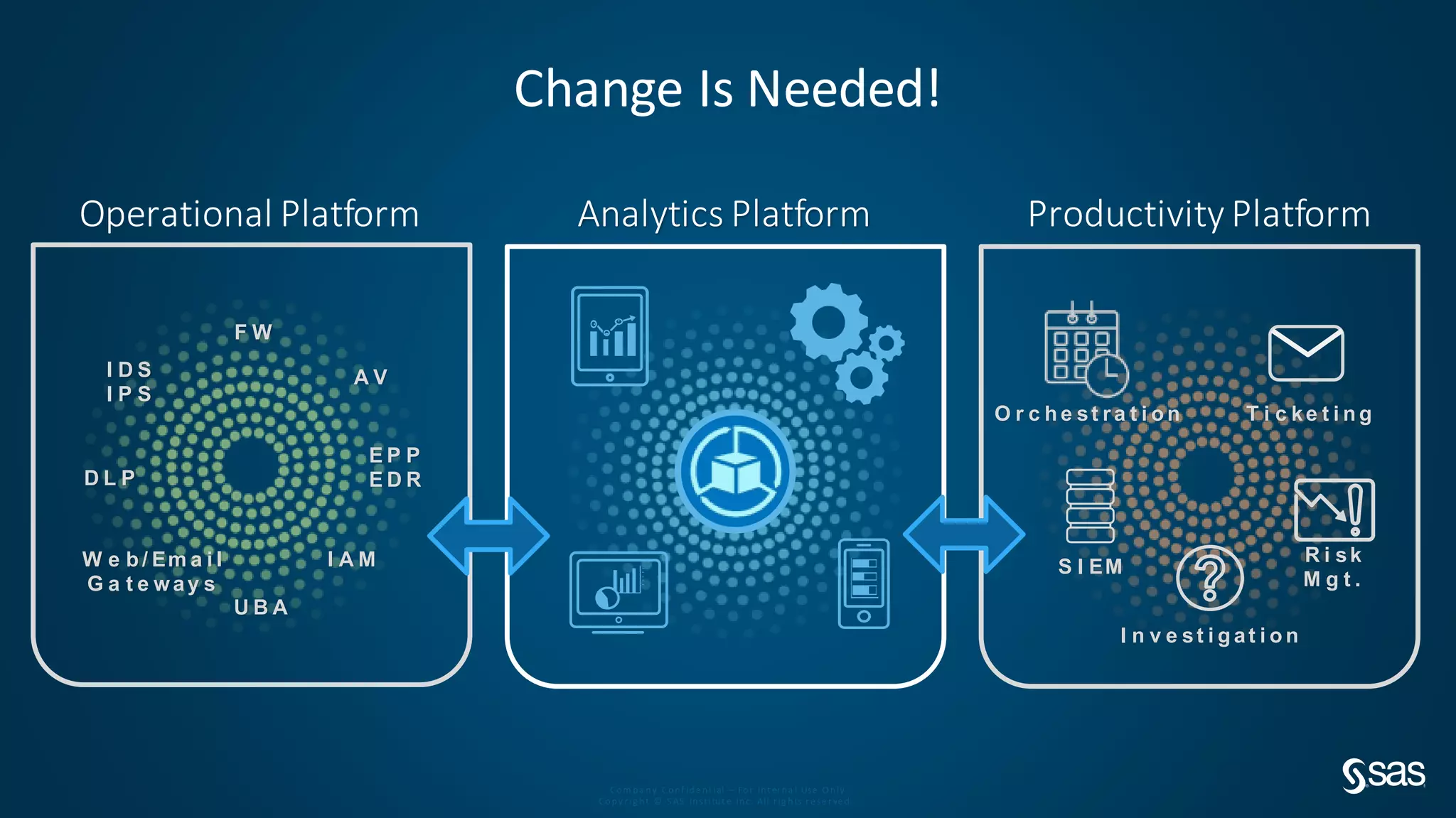
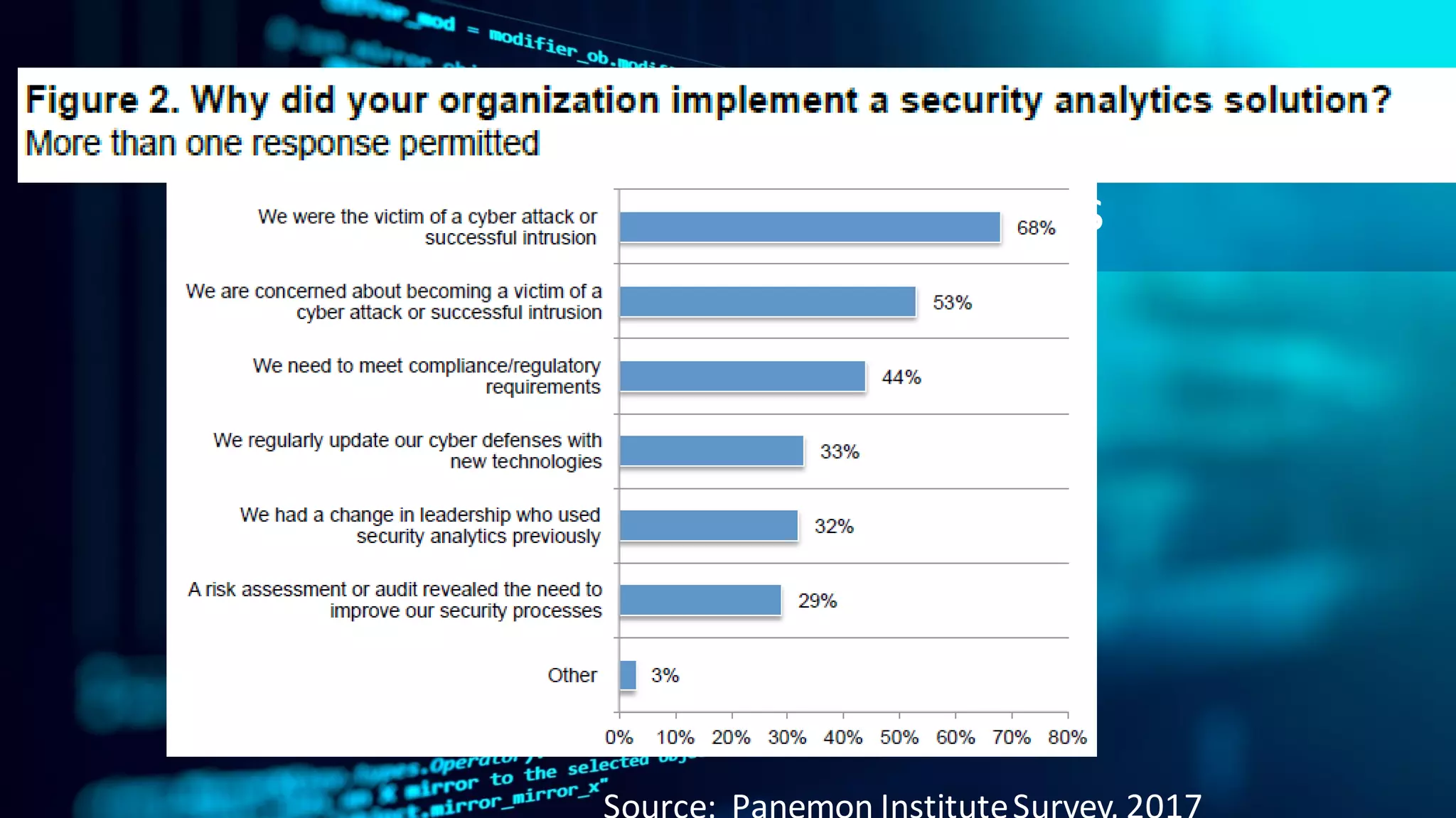
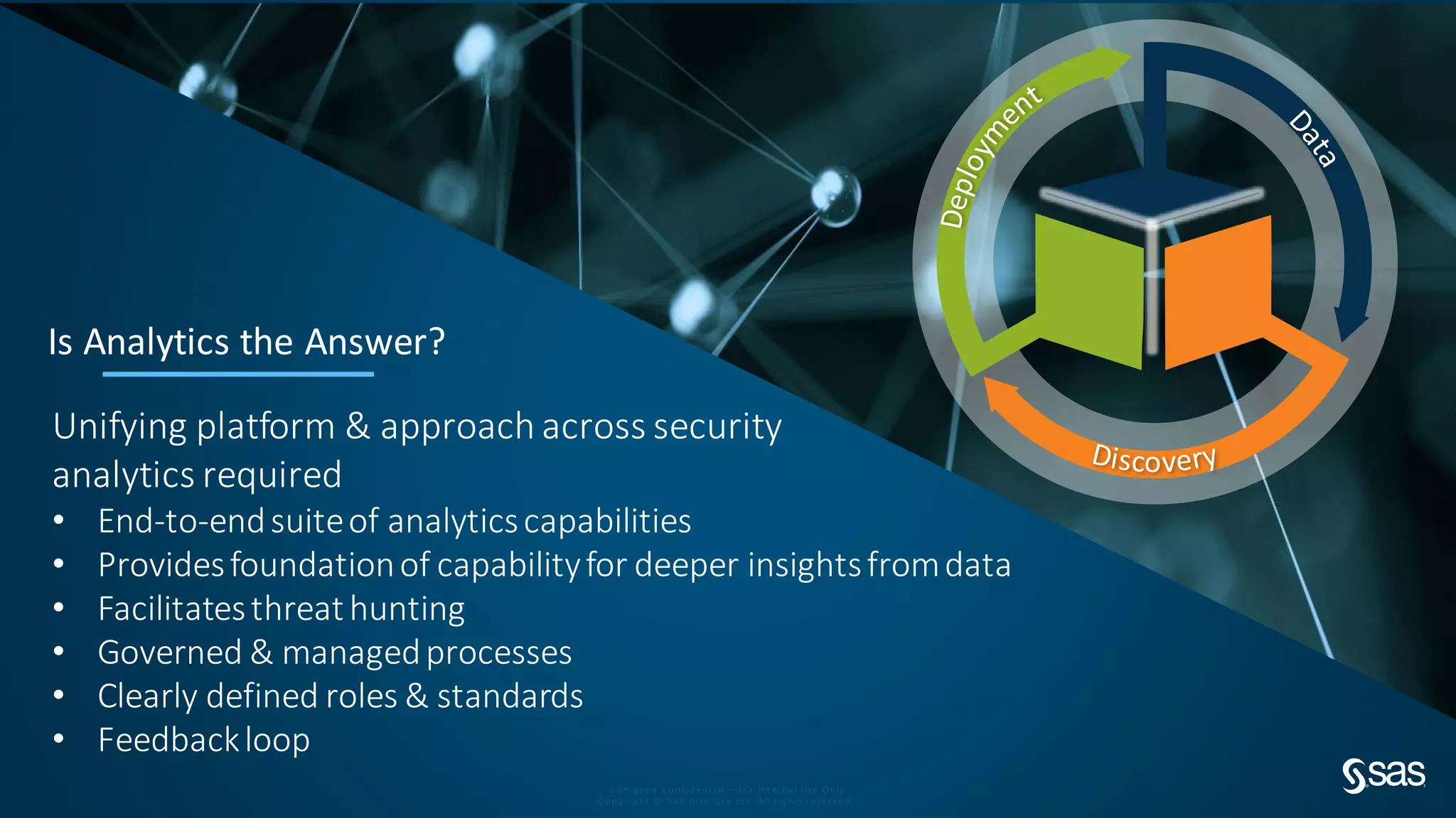
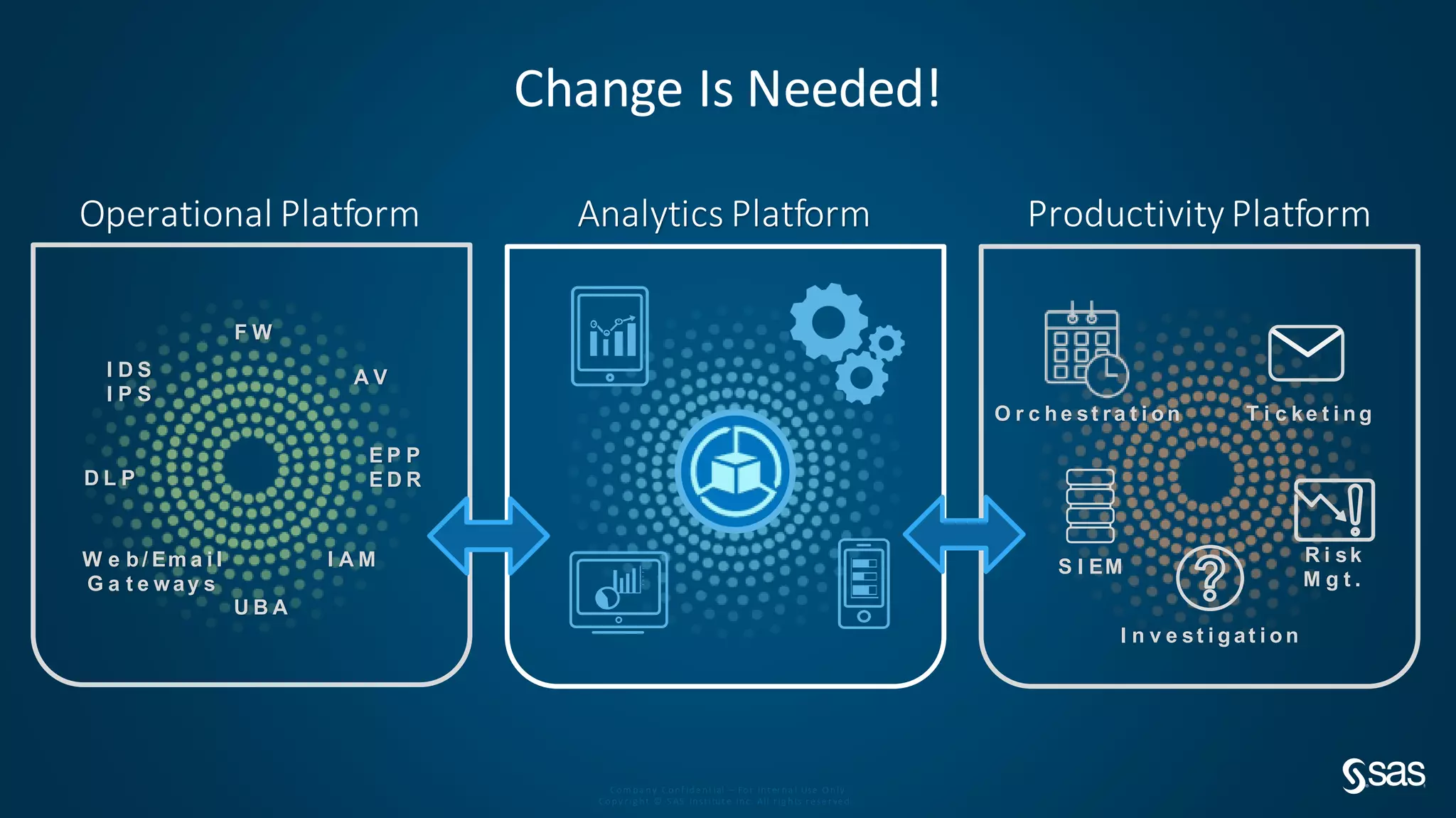
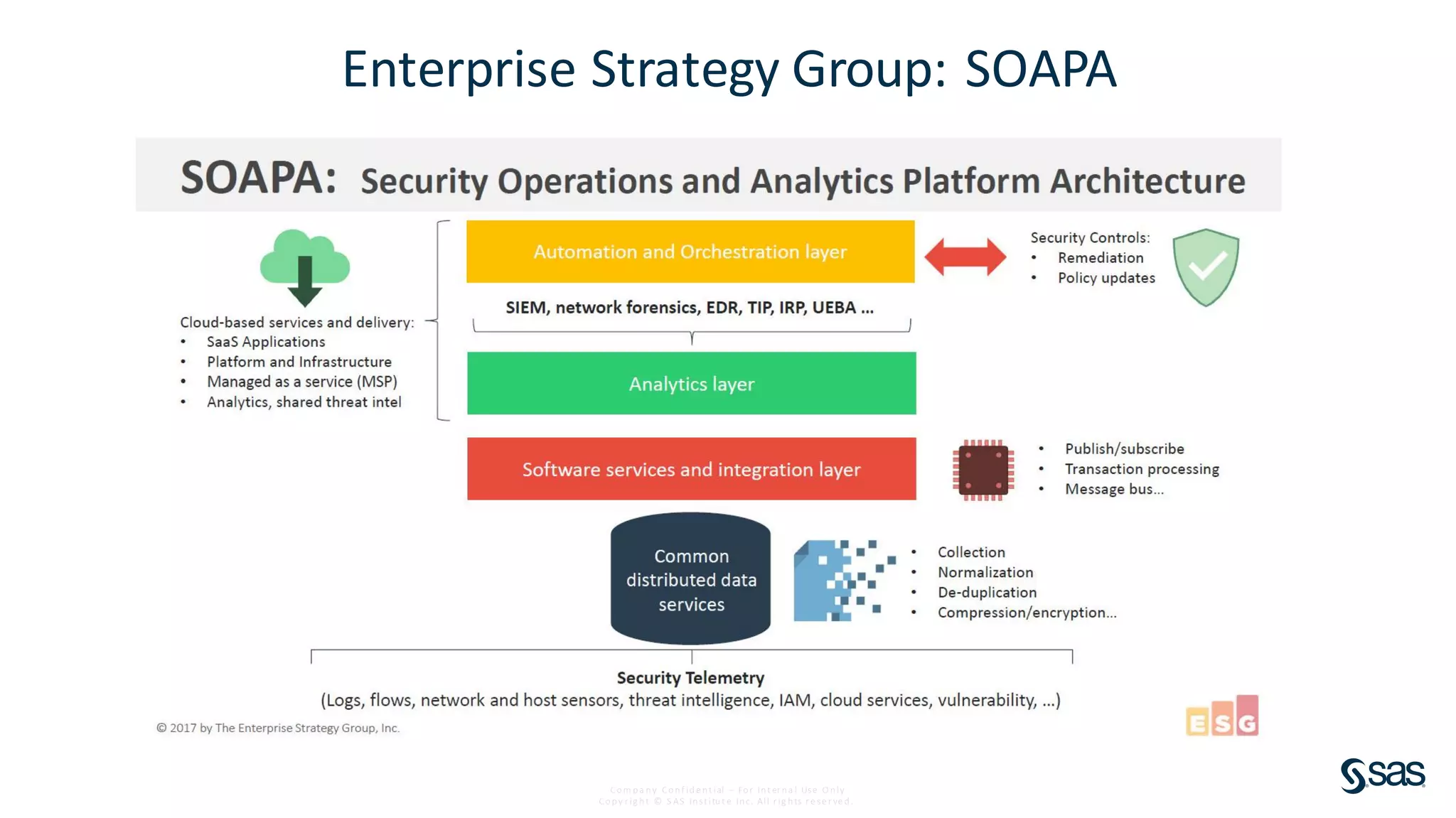
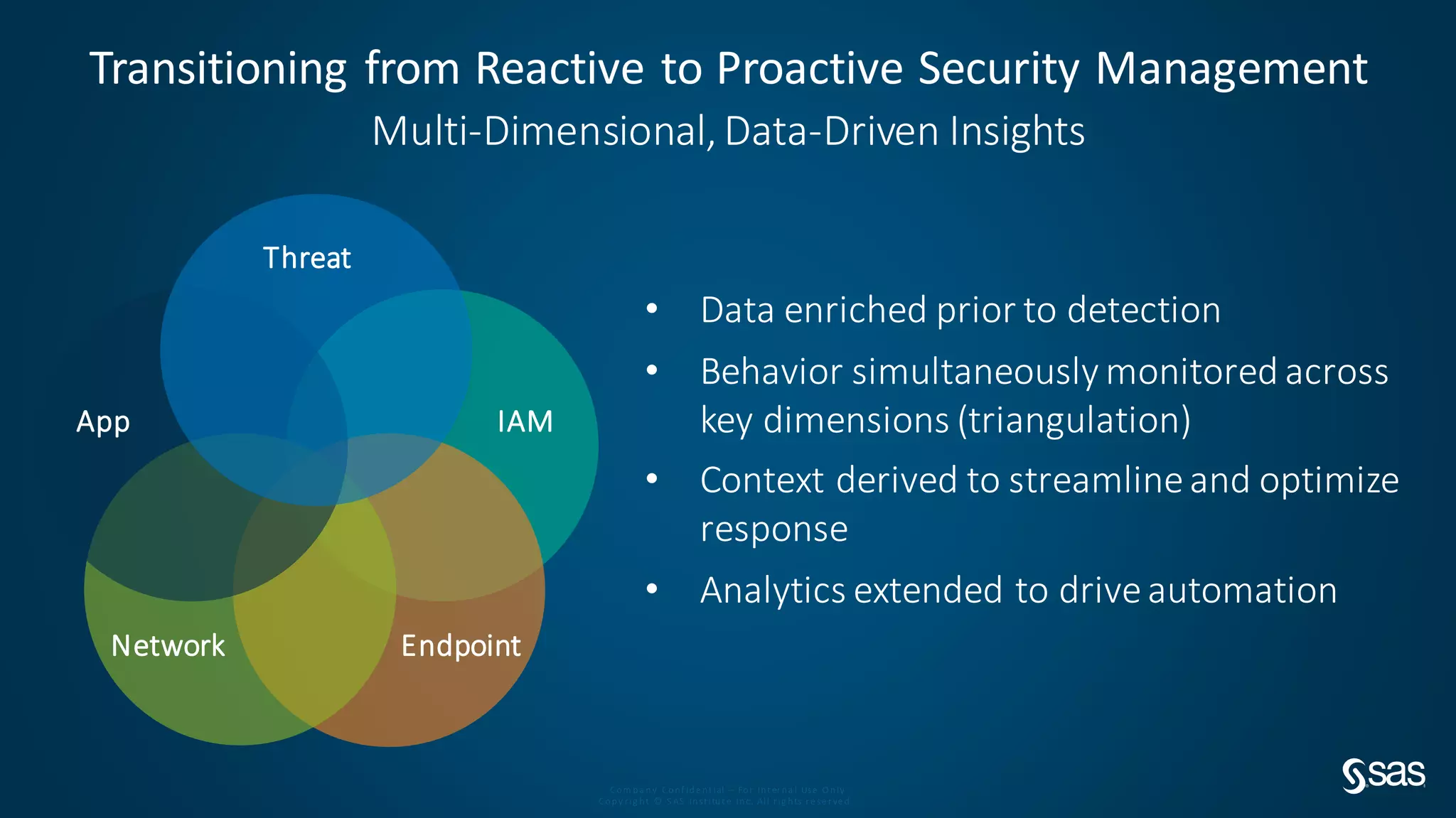
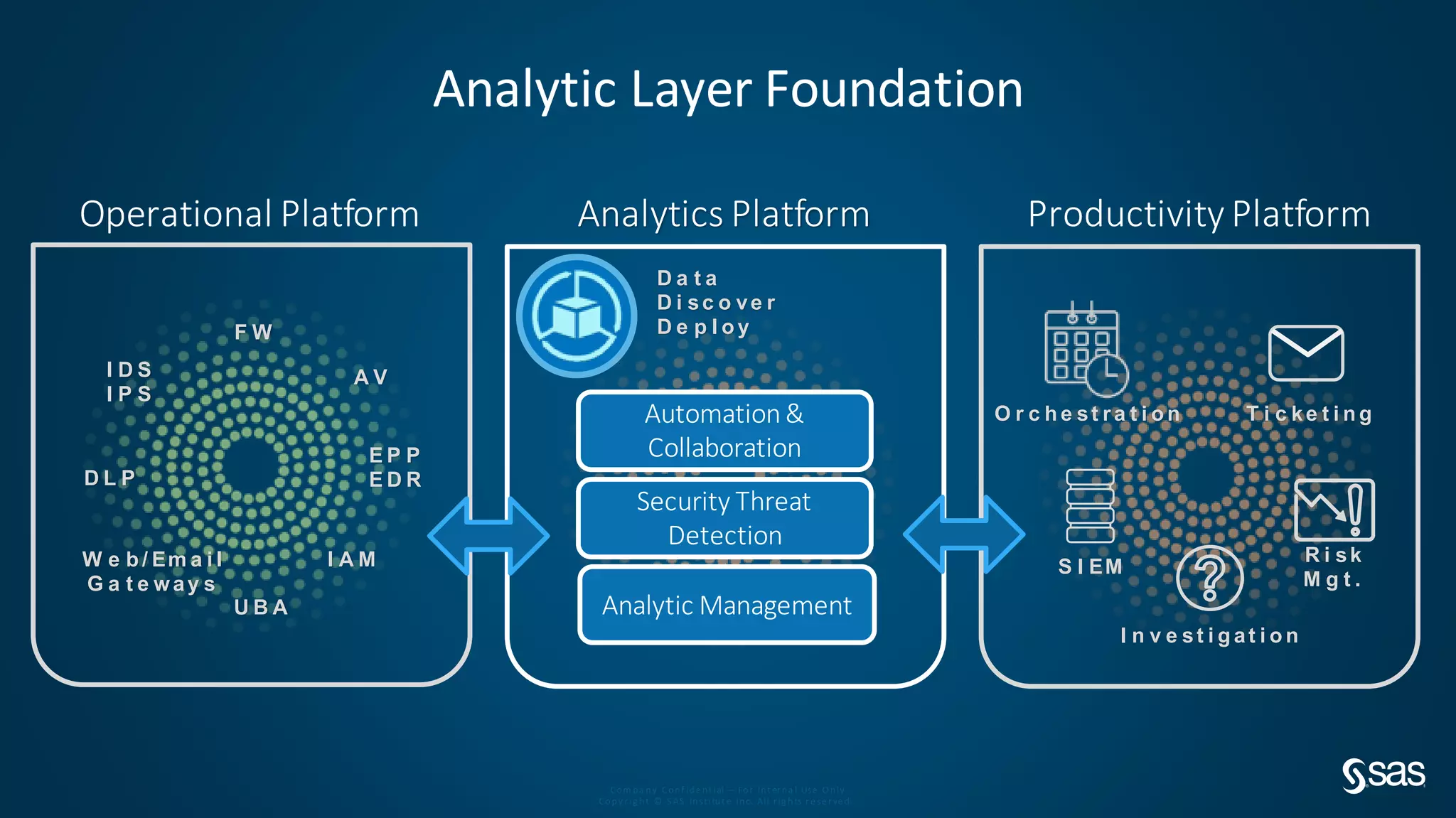
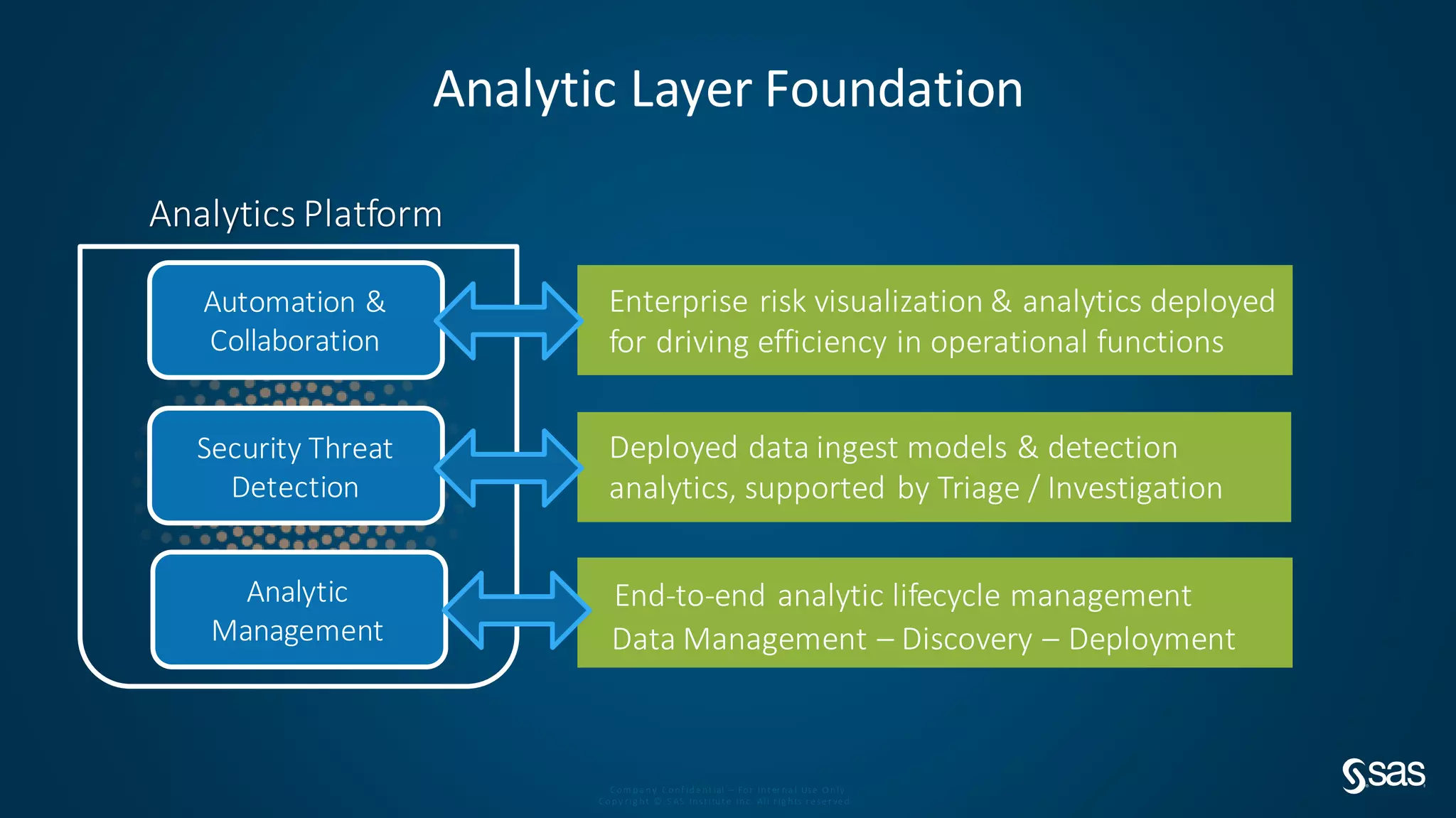
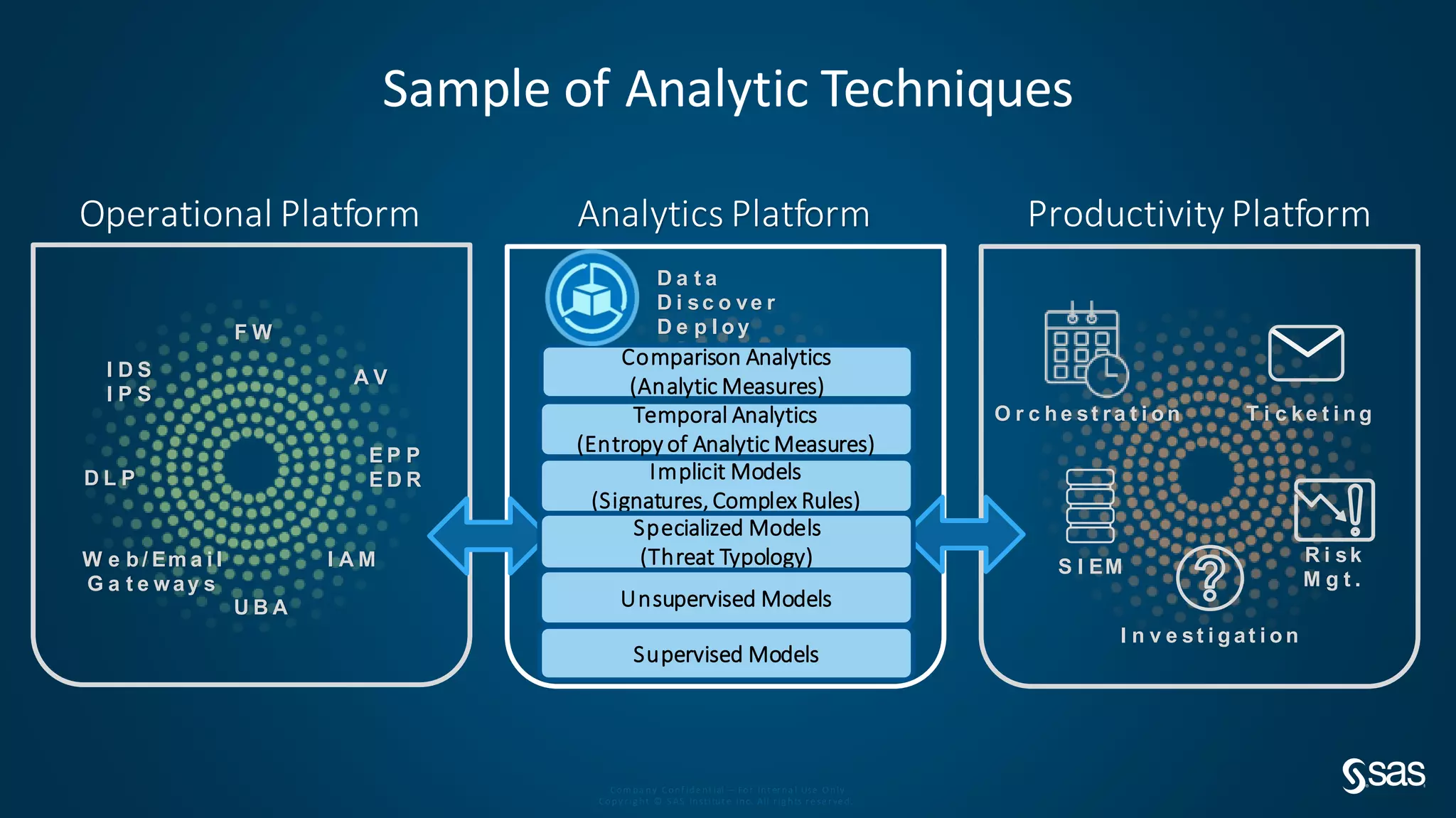
The document discusses implementing a security analytics platform to enable a proactive, risk-based approach to cybersecurity. It notes challenges with current point solutions that make holistic risk management difficult. The presentation argues that a unified analytics platform is needed to integrate data from multiple security tools and facilitate deeper insights through techniques like threat hunting. It presents SAS Institute's security analytics platform as a solution to transition organizations from reactive to proactive security management through multi-dimensional, data-driven insights.