Embed presentation

















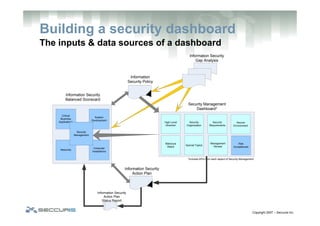



































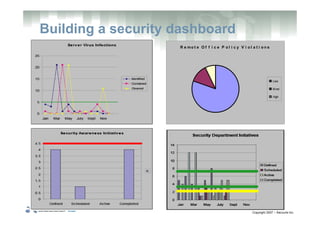






The document outlines the challenges faced by information security programs, including the need for effective monitoring and communication of security priorities. To address these challenges, it advocates for the creation of an information security program dashboard that visualizes key performance indicators (KPIs) and facilitates organizational awareness. The document details components necessary for building a dashboard, the advantages it provides, and steps for defining it within the context of strategic security management.


























































