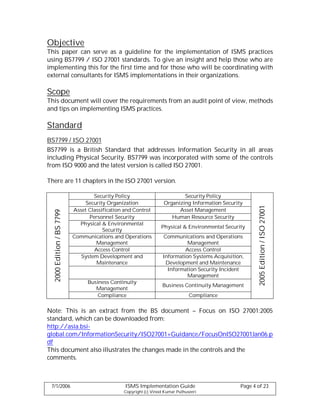
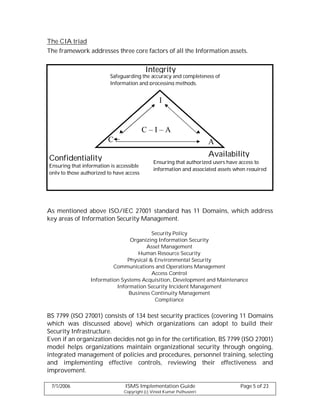
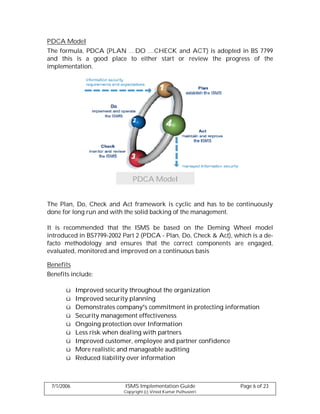
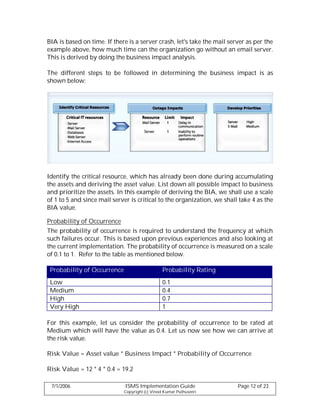
This document provides guidelines for implementing an Information Security Management System (ISMS) according to the BS7799 and ISO 27001 standards. It discusses forming an implementation team, defining the implementation scope, conducting a risk assessment including asset inventory and valuation, risk identification and management, and audit processes. The implementation process is broken down into stages of planning, executing, checking, and acting in line with the PDCA model. User awareness training and obtaining management commitment are also covered as important aspects of a successful ISMS implementation.