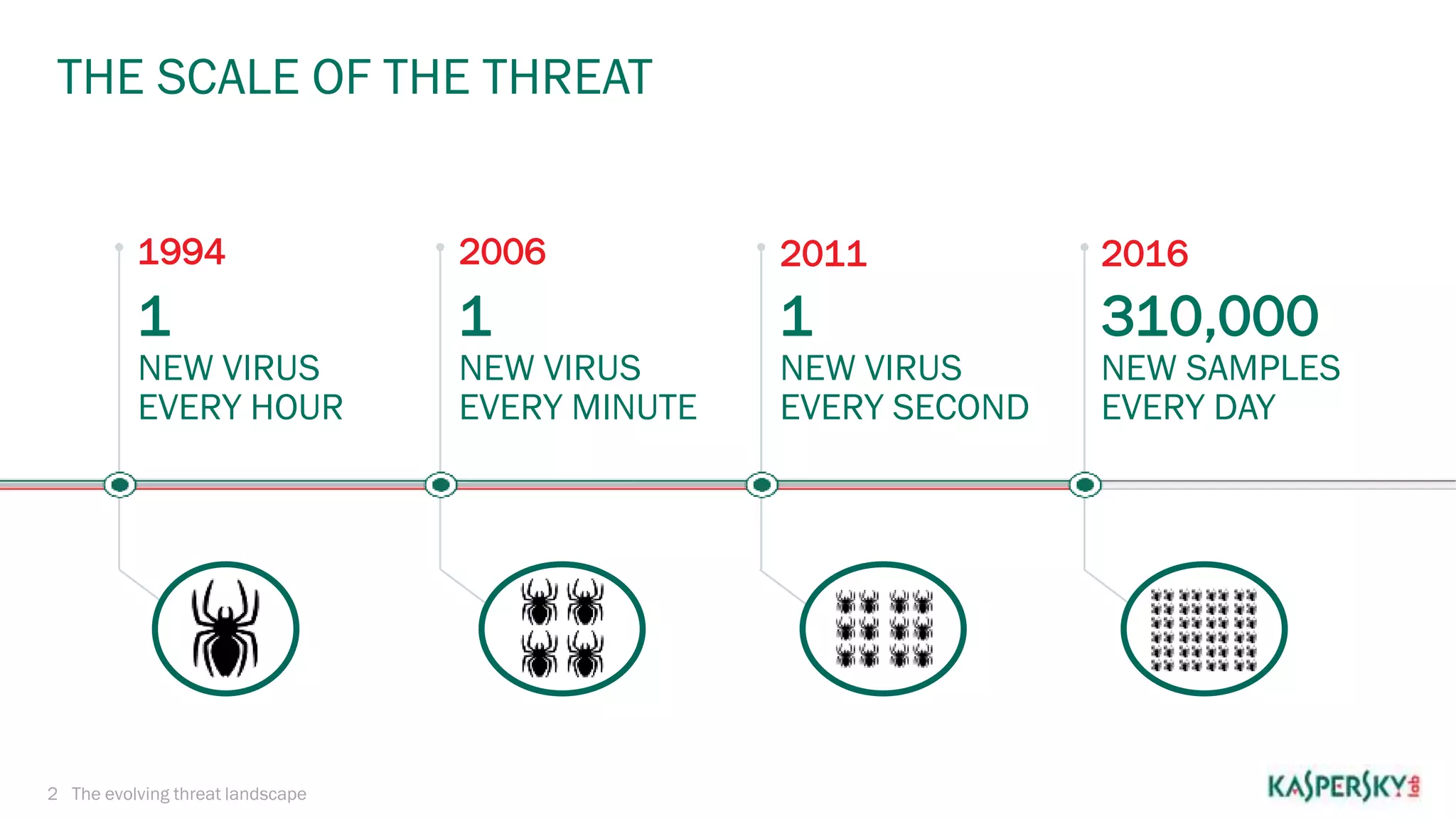
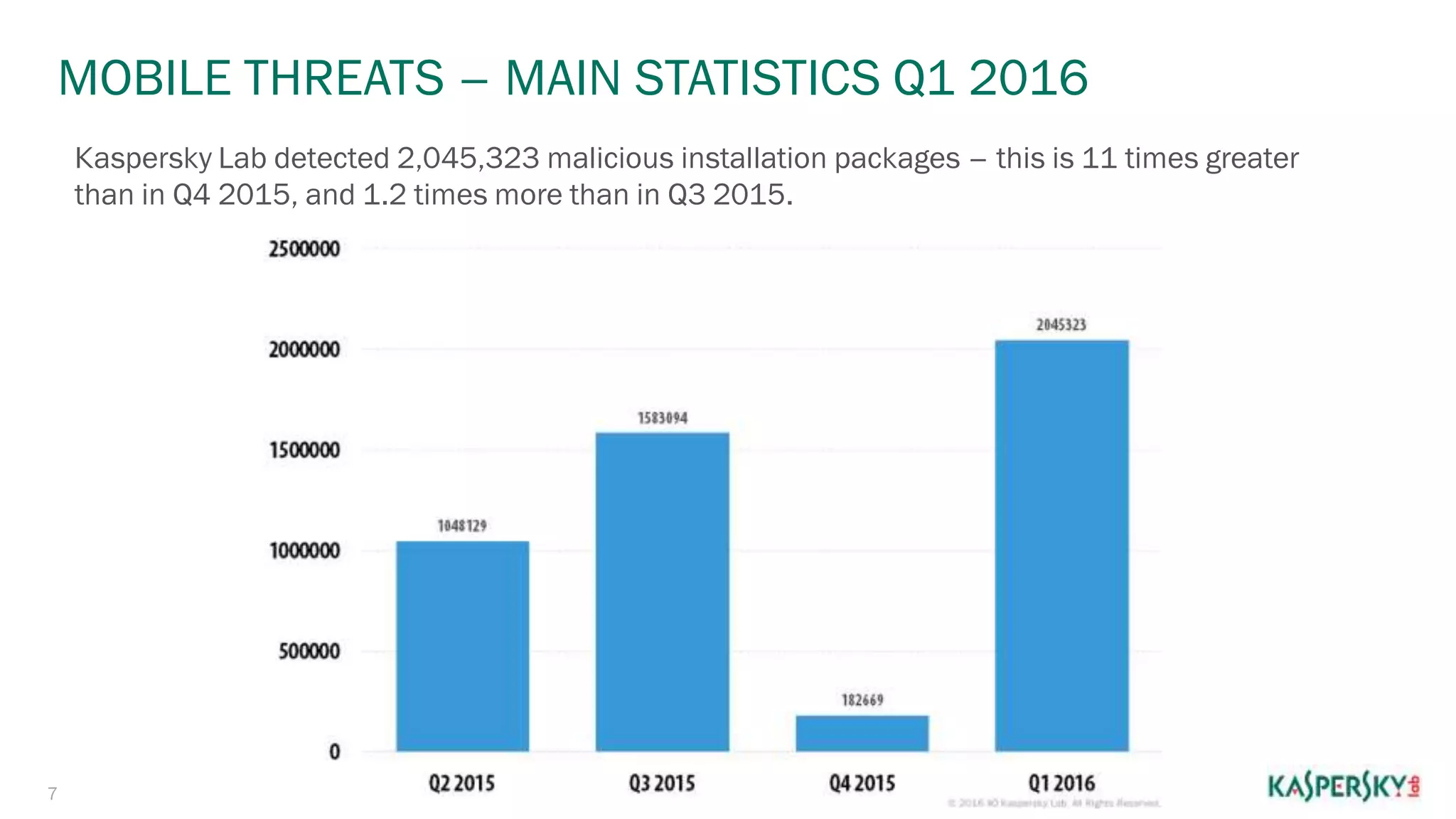
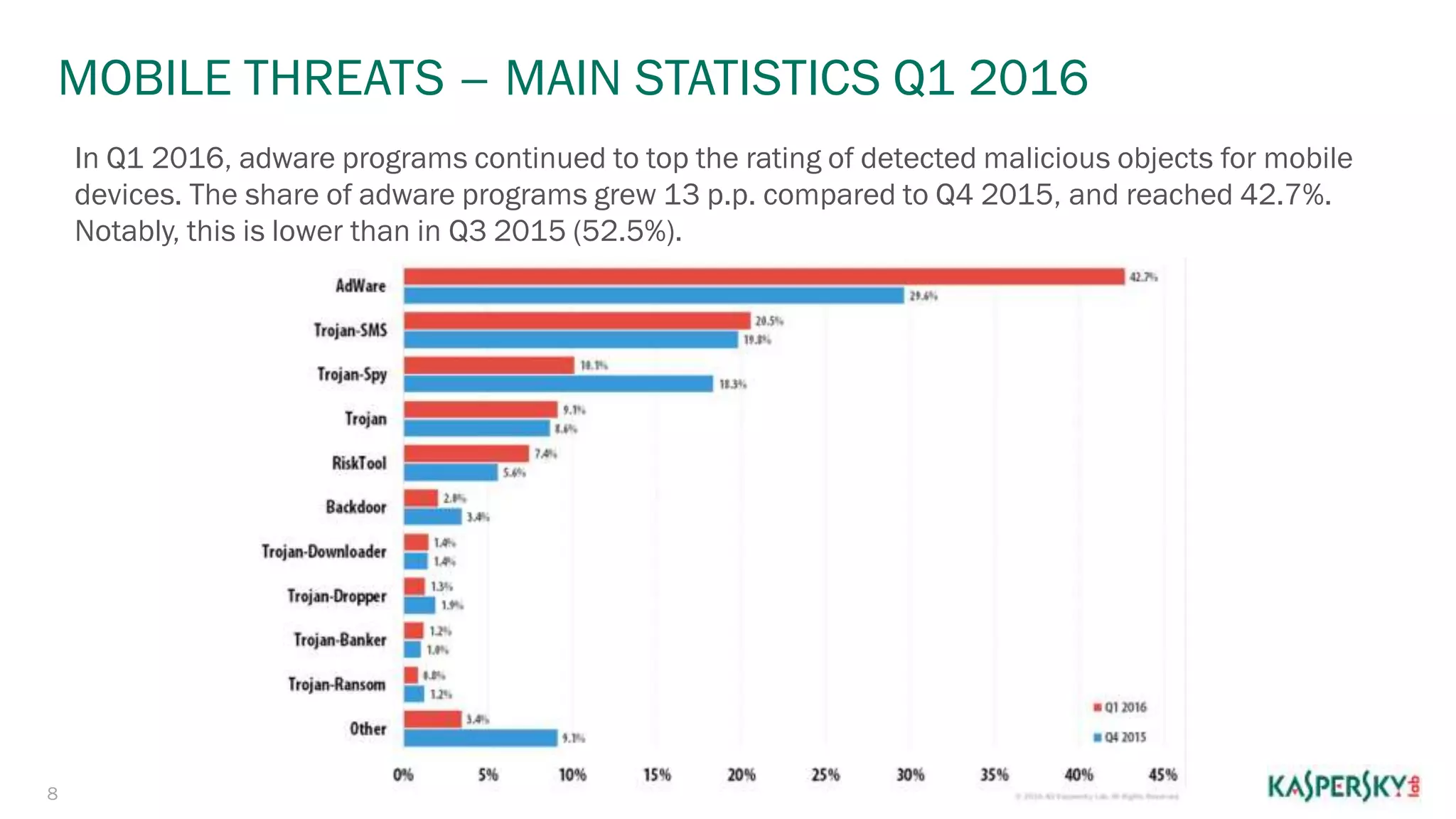
The document summarizes malware evolution over 20 years from 1994 to 2016. It notes that in 1994 there was a new virus every hour, rising to a new virus every second by 2011. By 2016 there were 310,000 new malware samples detected every day. It also provides statistics on attacks repelled and malware detected by Kaspersky Lab in the first quarter of 2016, including ransomware attacks blocked and mobile threats detected.