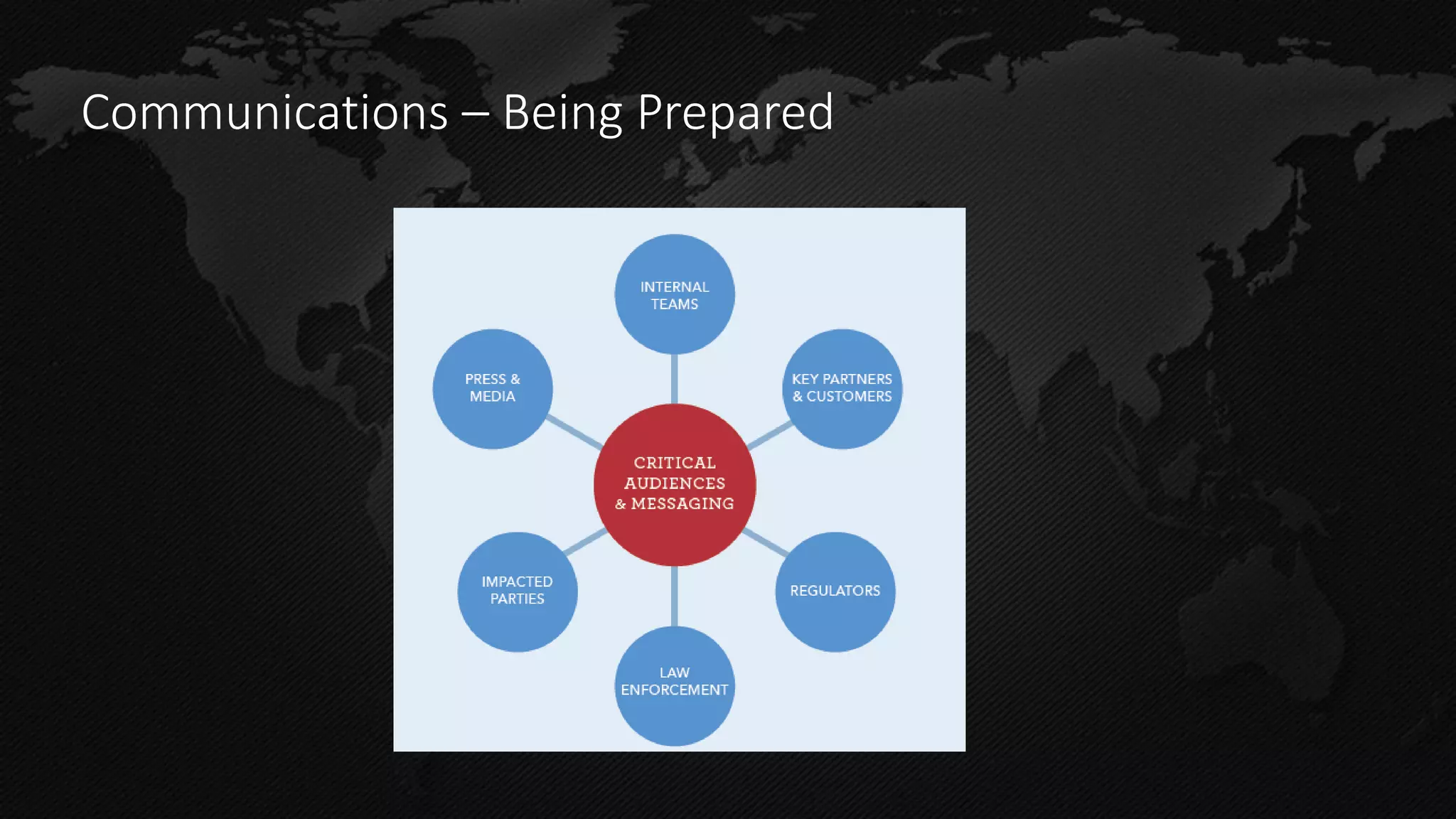
This document summarizes a presentation on trends in cyber crime and preparing for data breaches. It outlines that companies should develop a breach response plan to deal with incidents as all companies will experience a breach. It recommends contacting law enforcement within 72 hours of an incident and sharing threat information to help catch cyber criminals. It also discusses challenges around international jurisdiction and the need for a clear national standard for breach legislation in the US.