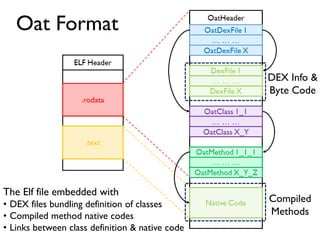
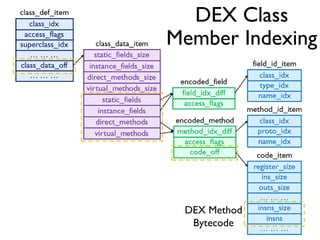
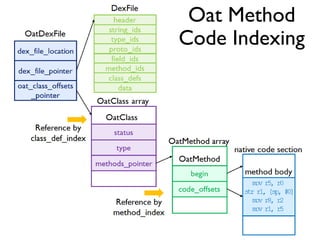
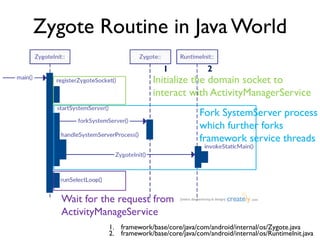
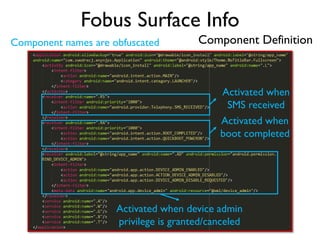
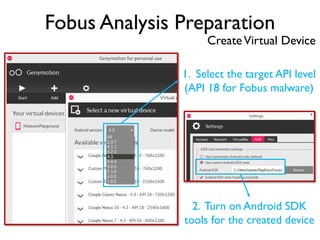
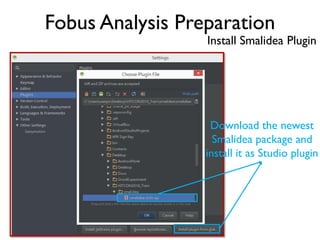
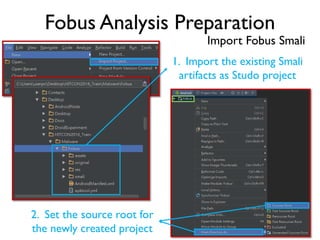
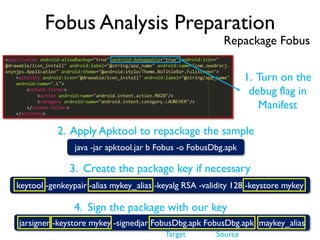
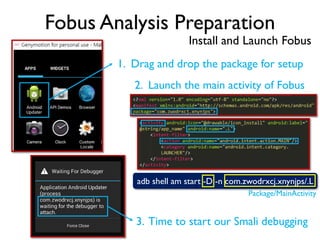
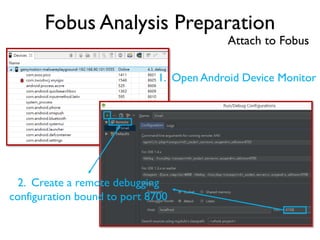
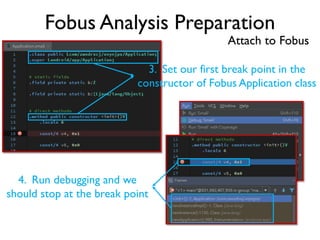
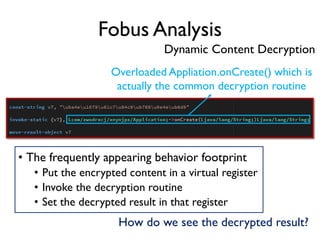
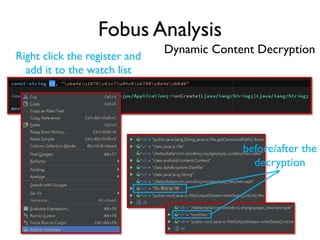
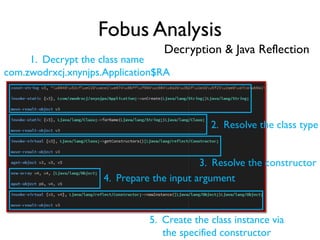
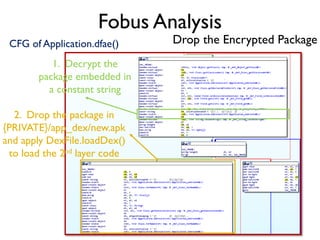
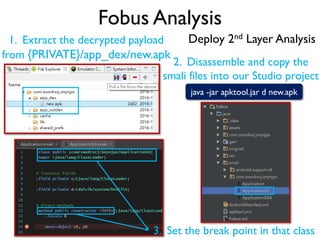
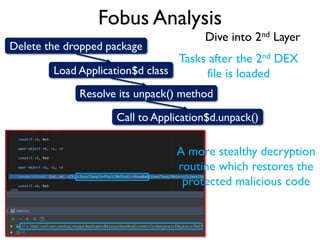
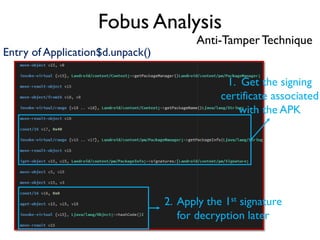
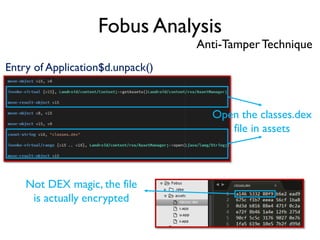
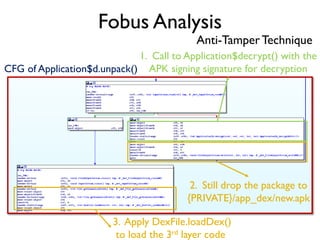
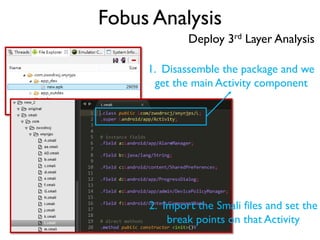
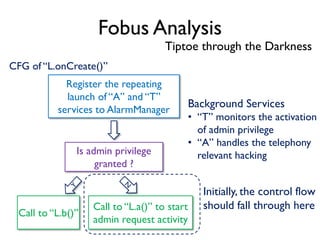
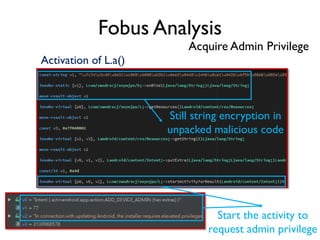
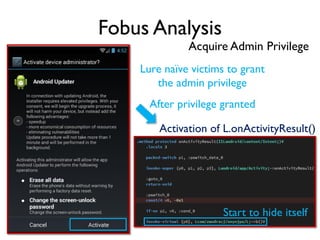
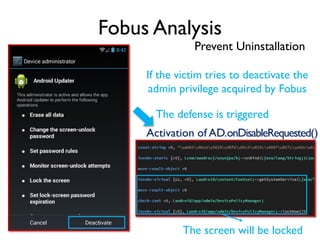
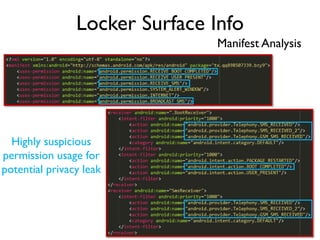
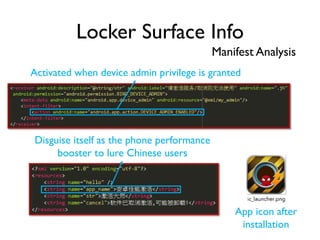
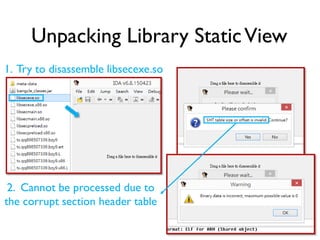
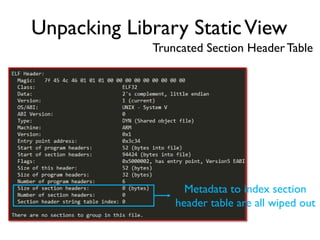
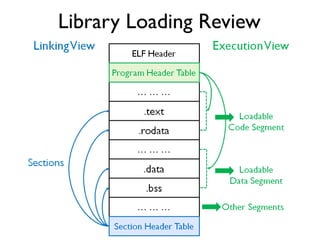
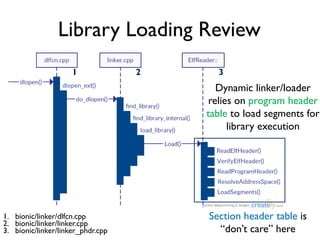
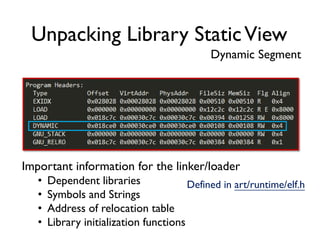
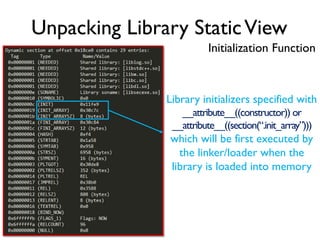
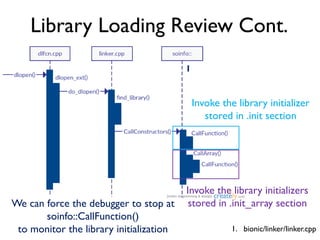
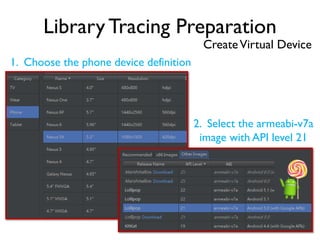
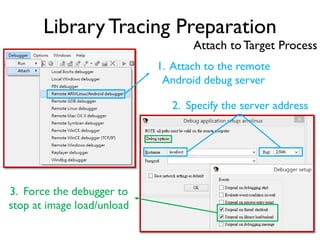
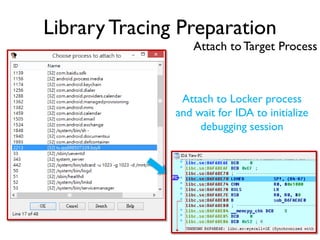
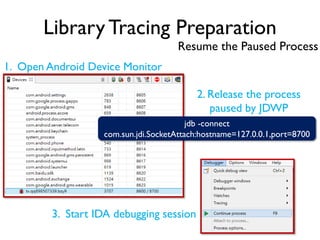
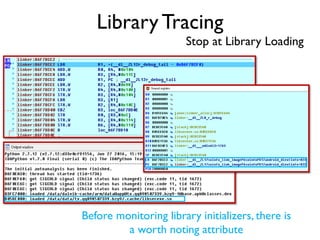
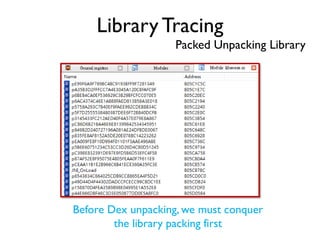
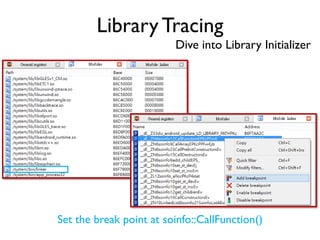
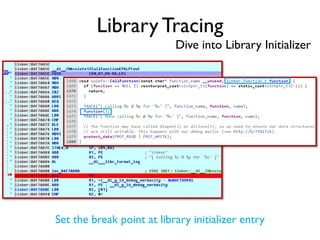
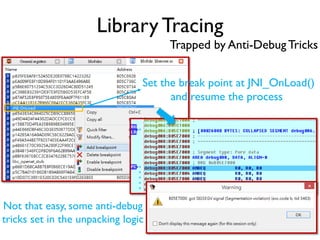
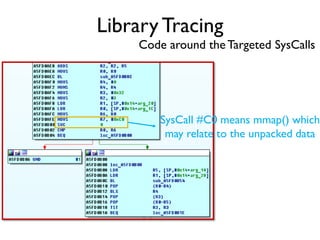
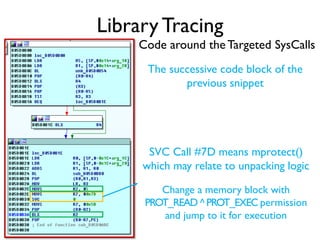
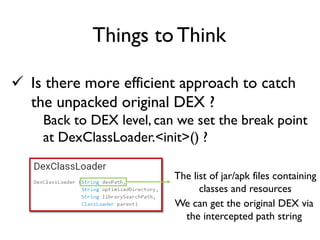
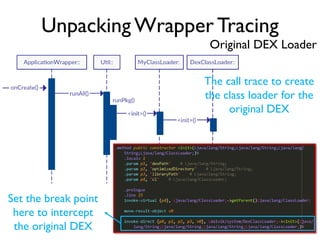
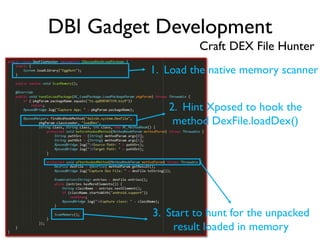
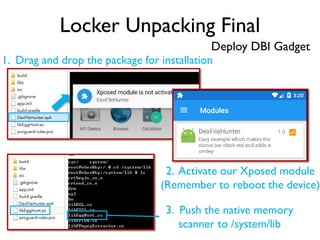
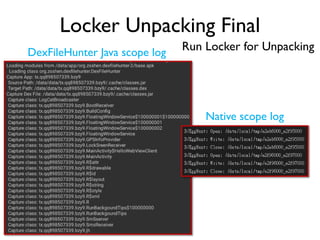
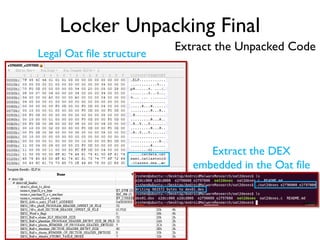
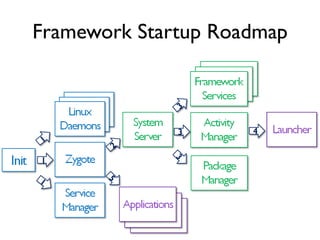
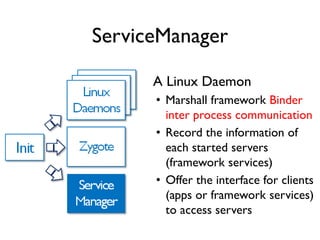
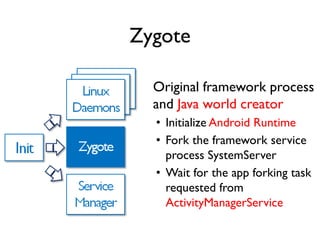
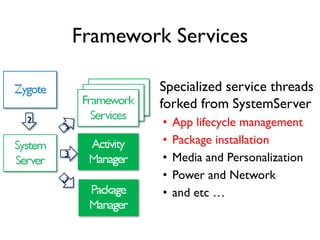
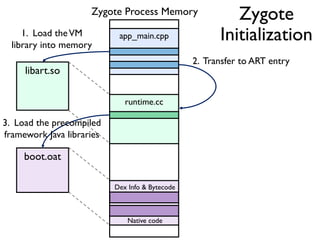
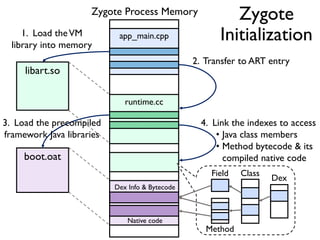
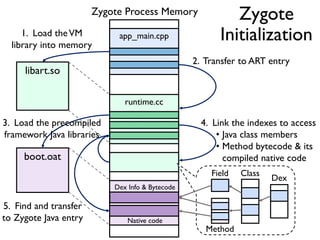
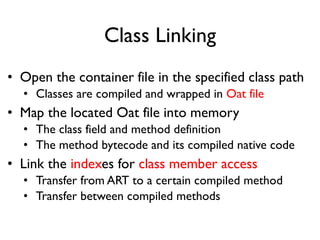
The document provides an overview of analyzing obfuscated Android malware. It begins with a quick review of the Android runtime and framework startup process. It then discusses dynamic analysis techniques for fighting encrypted DEX code and native protectors. For encrypted DEX code, it describes preparing an emulator, debugging tools, and tracing plugins to analyze a sample that uses encryption. It explores the sample's decryption and loading logic, class decryption through reflection, and an anti-tampering technique. For native protectors, it discusses unpacking the library through static and dynamic analysis, reviewing the library loading process, and preparing to trace library initialization for monitoring decryption.


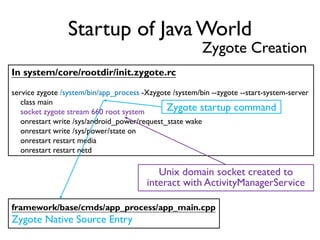
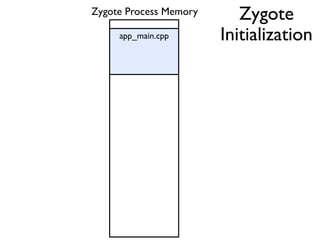
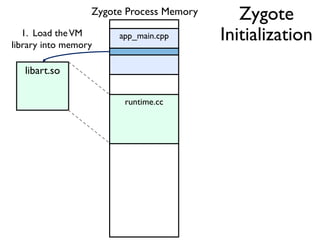
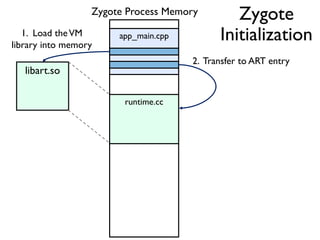
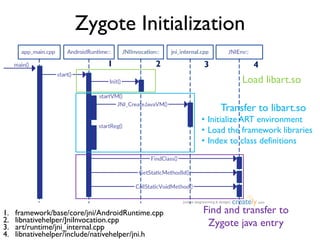

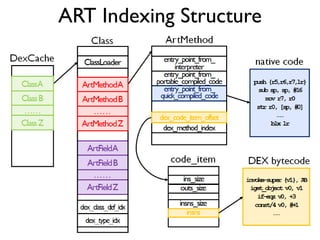
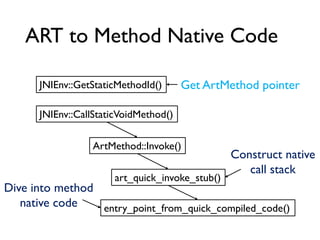
![Between Method Native Code
0x00: sget-object v0, Ljava/util/ArrayList; org.dsns.cleango.CleanGo.gRecord
0x02: invoke-virtual {v3}, java.lang.String java.lang.Object.toString()
0x05: move-result-object v1
0x06: invoke-virtual {v0, v1}, boolean java.util.ArrayList.add(java.lang.Object)
……
dex PC: 0x00
……
ldr.w r6, [r0, #432]
mov r1, r8
ldr r0, [r1, #0]
dex PC: 0x02
ldr.w r0, [r0, #396]
ldr.w lr, [r0, #40]
blx lr
……
Native Code Get Object object
Get toString() ArtMethod pointer
Get entry to compiled native code
Branch and link to the callee
Dex Bytecode](https://image.slidesharecdn.com/towarddynamicanalysisofobfuscatedandroidmalware-161126103554/85/Toward-dynamic-analysis-of-obfuscated-android-malware-21-320.jpg)