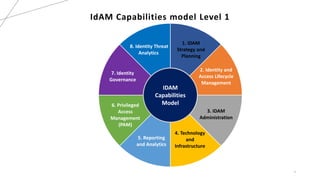
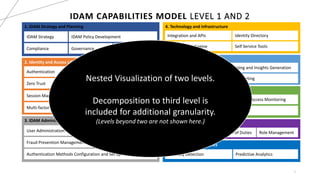
The document discusses the Identity and Access Management (IDAM) capabilities model, emphasizing its importance as a strategic technology enabler for organizations, particularly in the face of increasing cybercrimes. It outlines the key components of IDAM, including strategy and planning, lifecycle management, administration, and governance, while also providing details on various capabilities and their hierarchical structure. Additionally, it highlights the value of business capabilities in improving alignment between business and IT, optimizing processes, and providing useful insights through analytics.