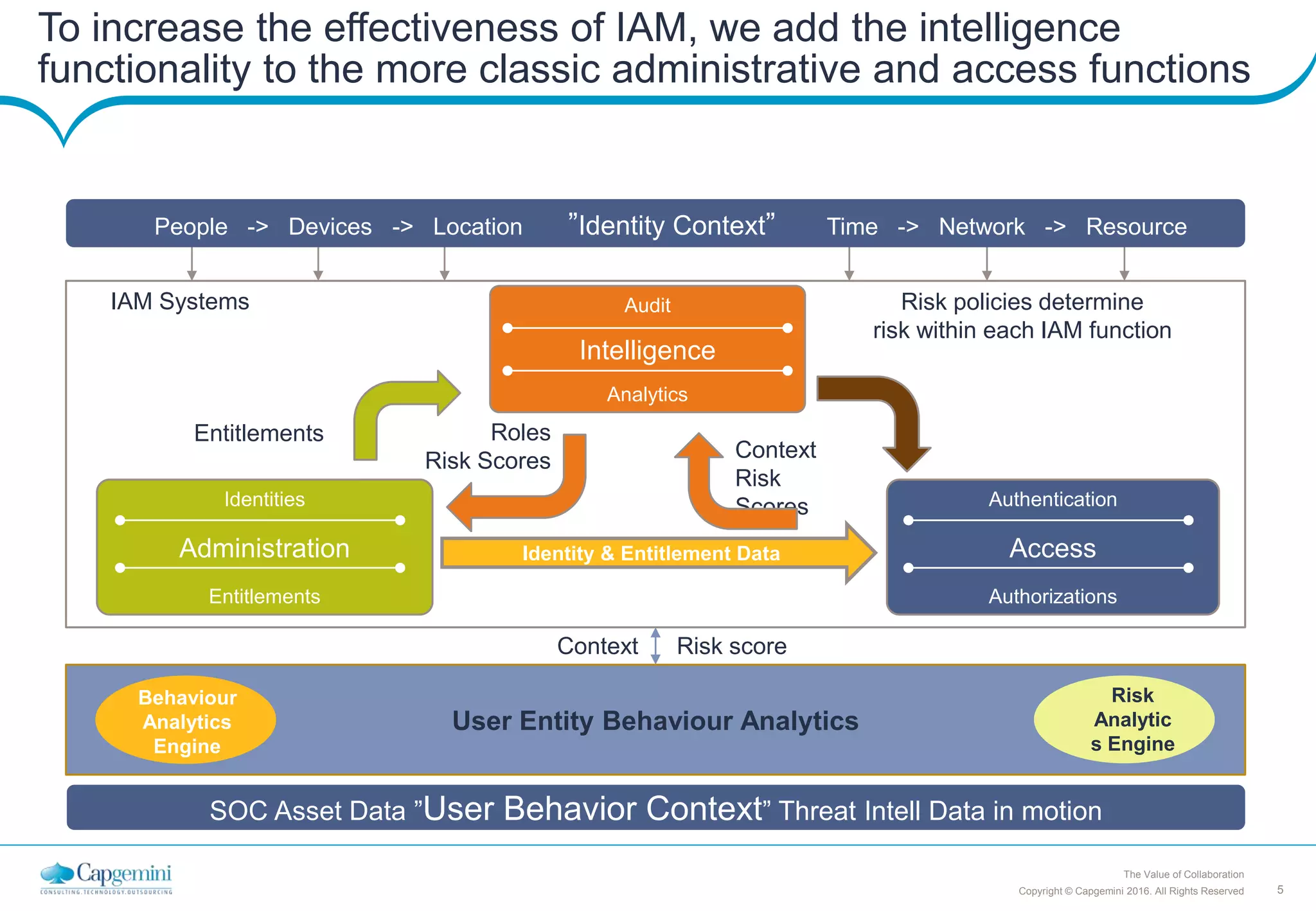
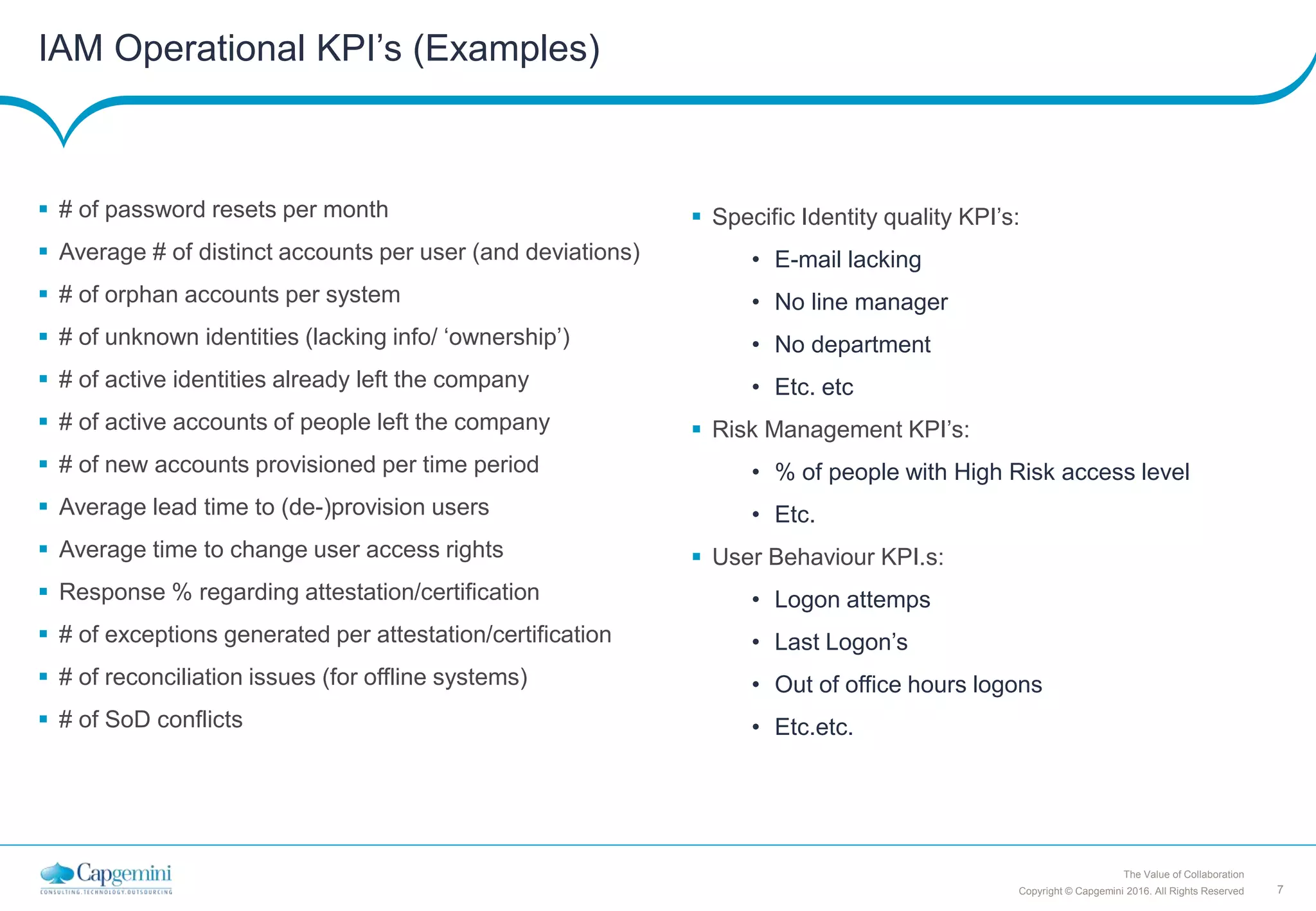
Capgemini's vision for cybersecurity is to reduce risks from IT use by making prudent choices. Their mission is to deliver convenient, cost-effective cybersecurity services that adapt to clients' changing needs. They focus on identity and access management, which is the cornerstone of effective security. Capgemini uses a strategic approach to balance security, costs, and business needs. Their Identity and Access Management strategy aims to make security processes largely automated and risk-based.