Embed presentation
Downloaded 15 times




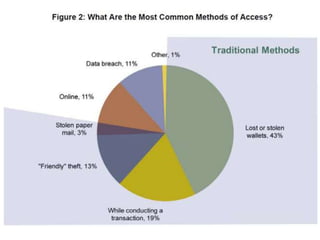







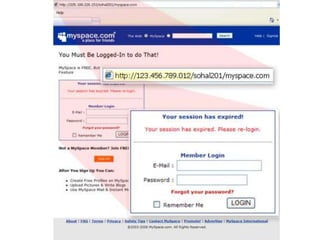
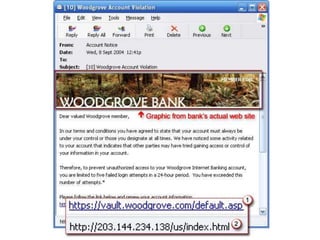
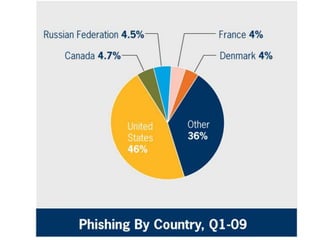
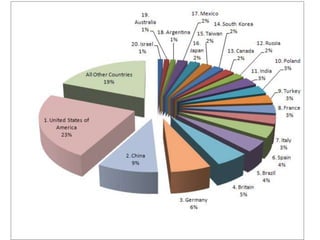

ID theft occurs when personal information is used without authorization to commit fraud, affecting over 10 million people annually in the US. Personal information can be obtained through phishing scams, lost or stolen wallets, mail theft, or hacking of online transactions. To prevent ID theft, one should shred mail, update contact information, avoid sharing personal details, and monitor credit reports. If a victim, one should file a police report, place fraud alerts on credit files, and keep records of recovery efforts. Phishing involves deceiving people into sharing private credentials through electronic messages, and has evolved from early financial scams to targeting social networks and specific individuals.
















