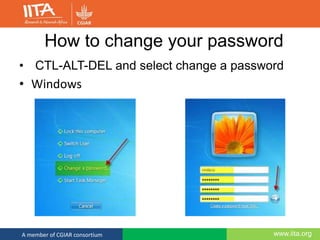
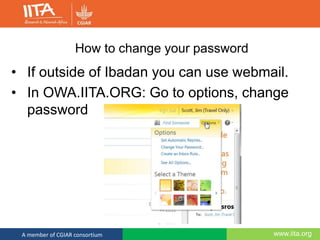
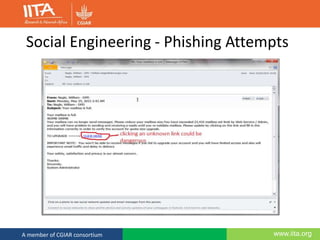
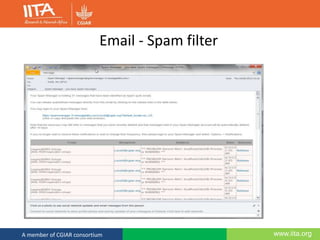
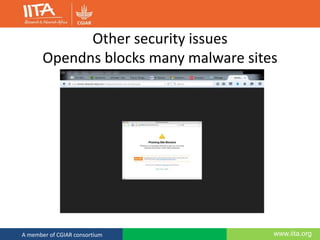
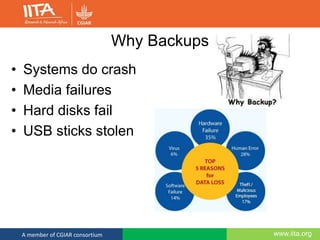
This document discusses computer security and outlines best practices for protecting systems and data. It defines computer security as protecting computing systems and data through ensuring confidentiality, integrity and availability. It then identifies common security risks like hacking, phishing, and social engineering. The document provides recommendations for strong passwords, backups, and awareness of suspicious emails or links. The overall message is that computer security is a shared responsibility and following basic practices can help prevent the majority of security breaches.














![www.iita.orgA member of CGIAR consortium
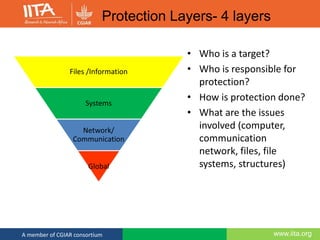
Password Policy
• Change every 180 days.
• Must be at least 8 characters from at least three of
the following sets:
• Lower case letters a-z
• UPPER CASE LETTERS A-Z
• Numerics 0-9
• Special characters (!"# $%& ' *+, -./ : ;<=>?@ []^_` {|}~ )
• If you feel your password has been compromised
change it immediately.](https://image.slidesharecdn.com/ictsecurity-july-161117075710/85/ICT-Security-is-Everyone-s-Business-20-320.jpg)