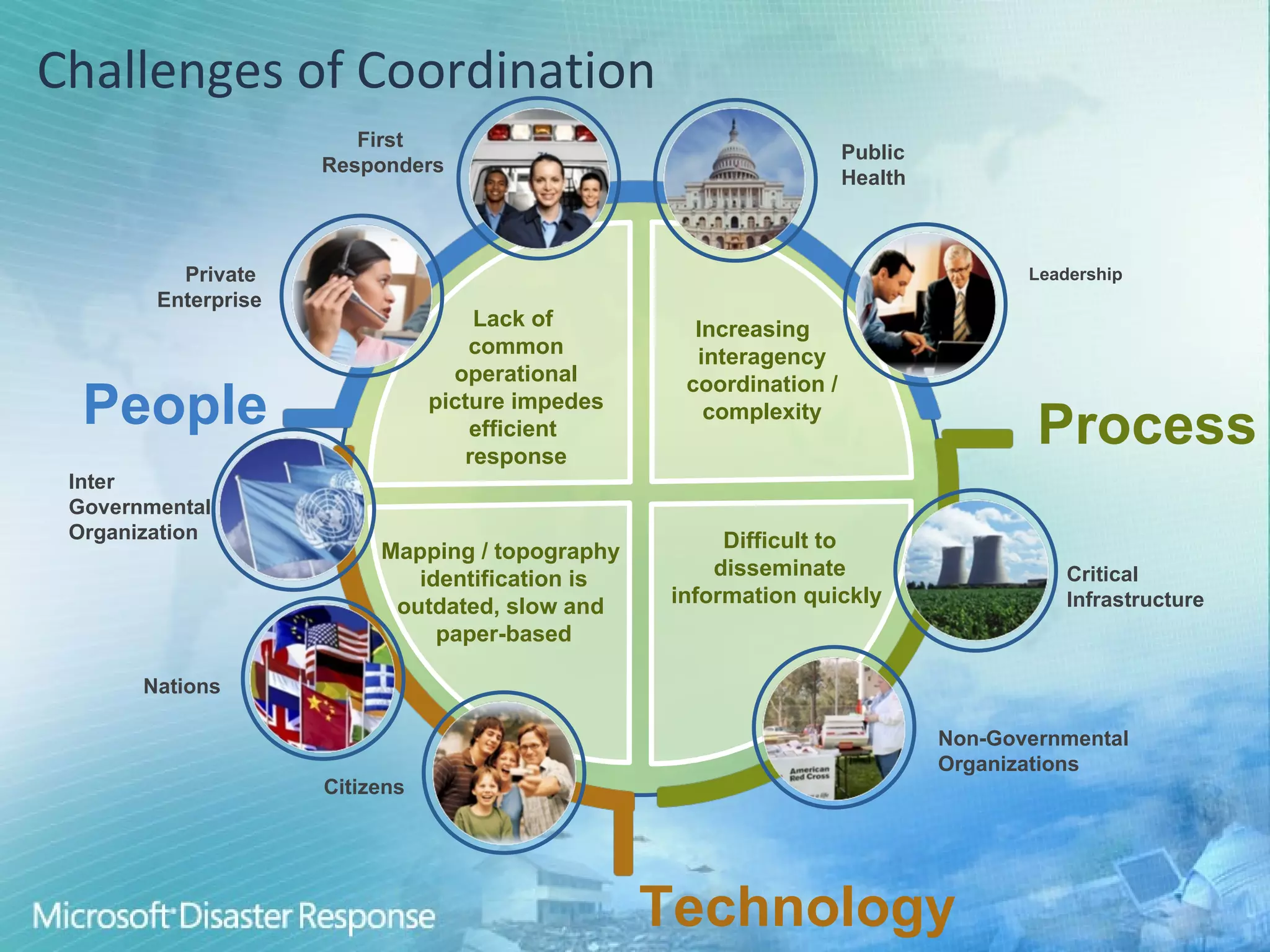
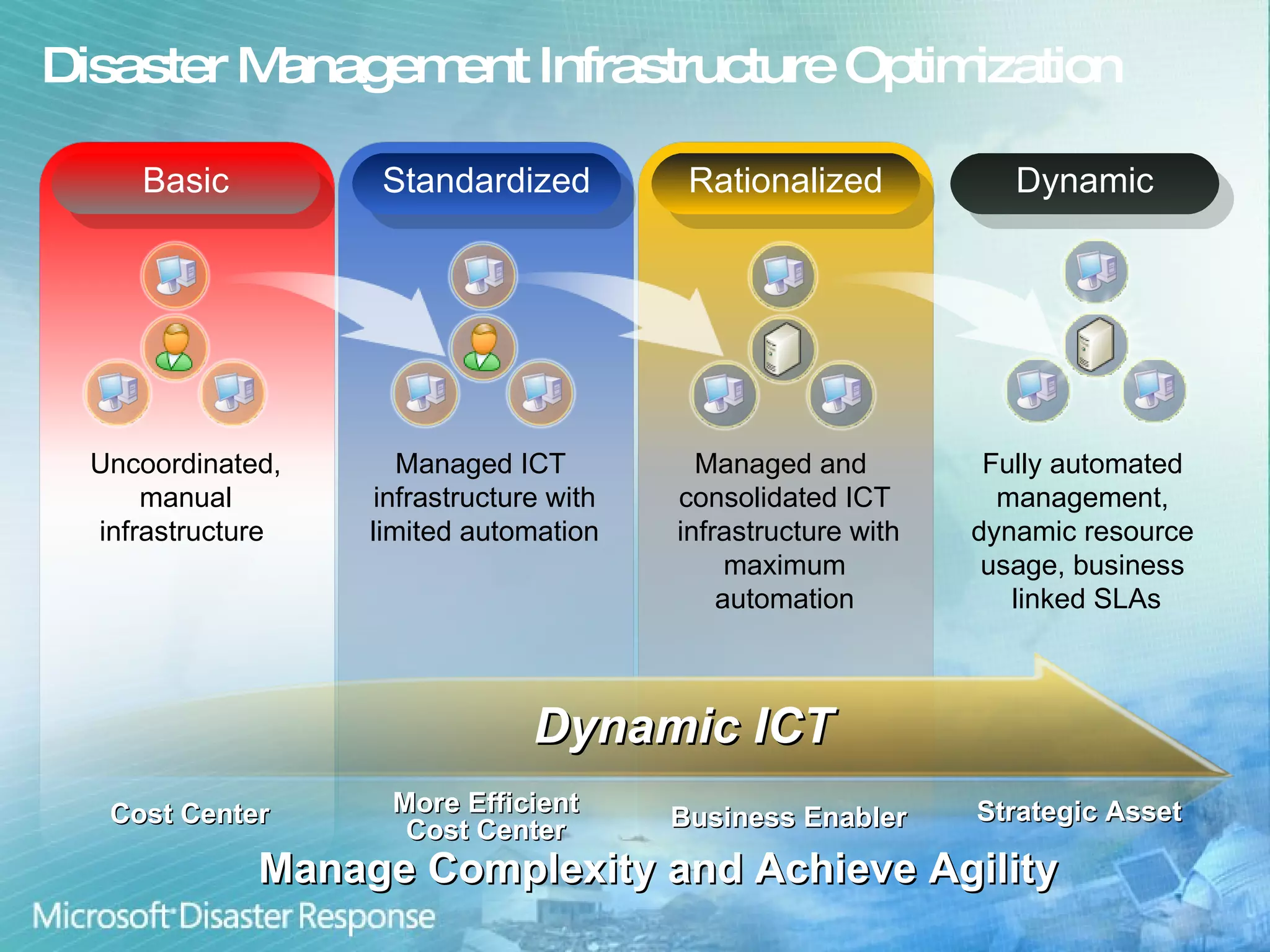
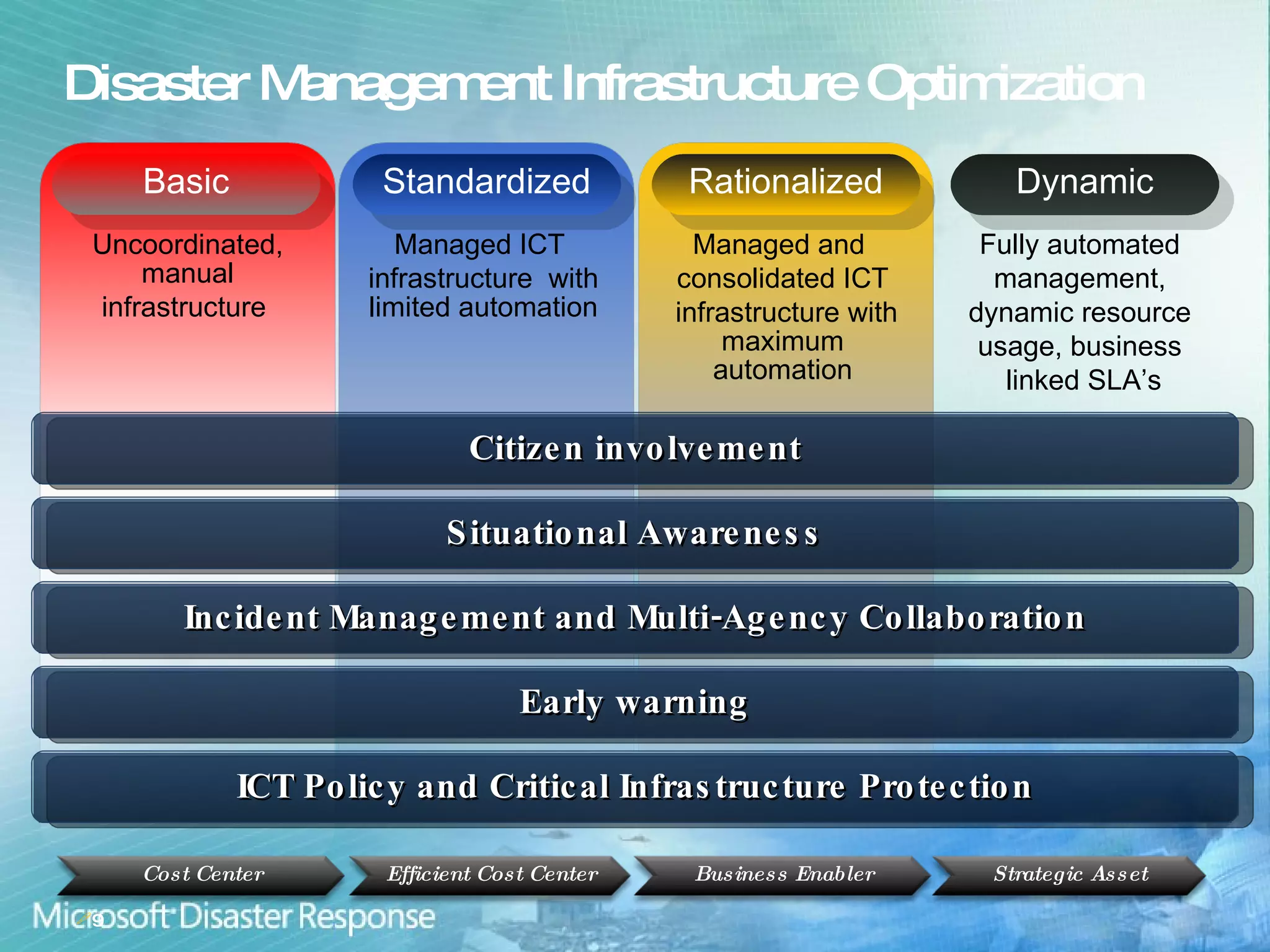
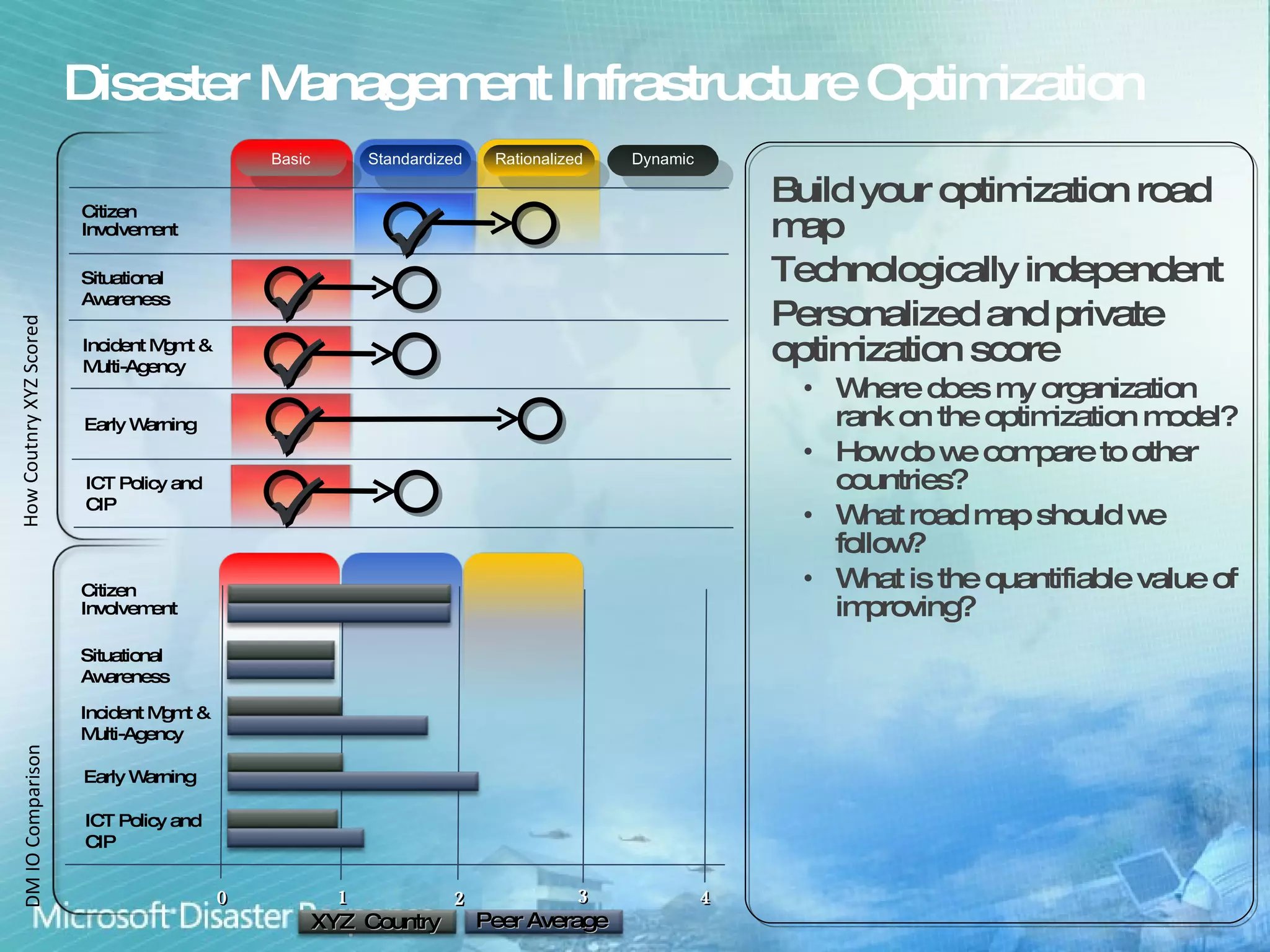
Microsoft aims to enhance international disaster risk reduction through technology and partnerships, focusing on building resilient communities and improving disaster management infrastructure. Initiatives like the OneResponse portal for inter-agency coordination and the Vine service for community engagement in emergencies showcase their commitment. The company provides ICT capacity assessments to strengthen disaster responses and streamline collaboration among various organizations.