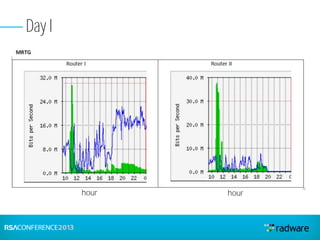
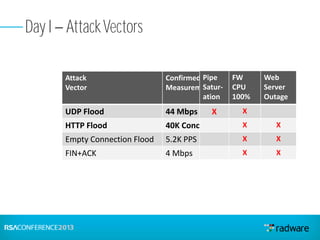
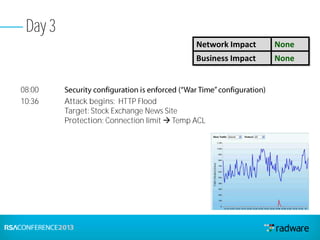
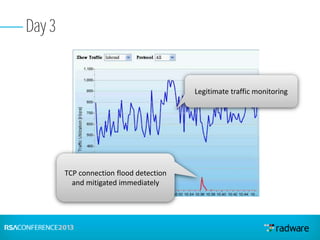
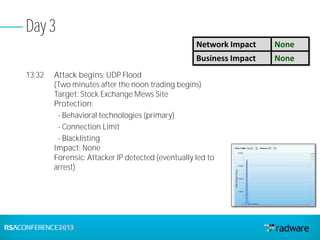
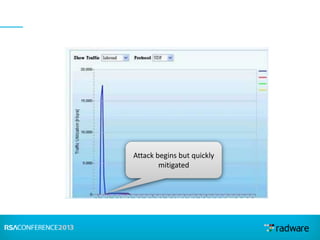
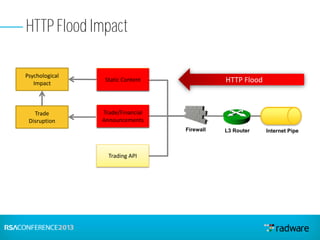
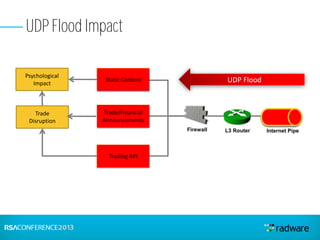
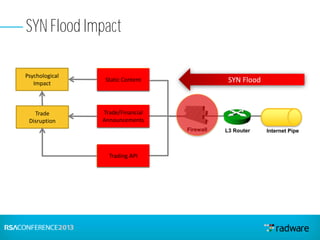
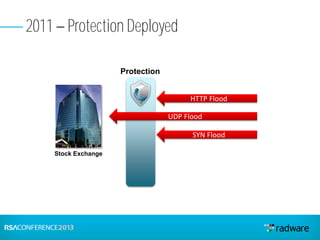
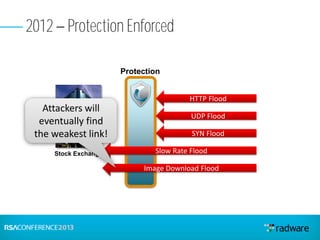
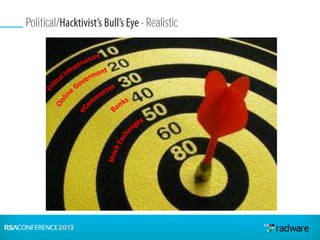
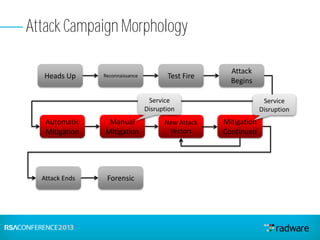
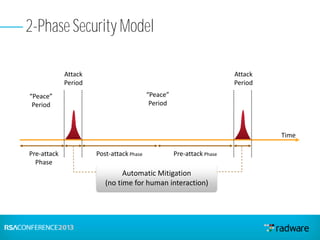
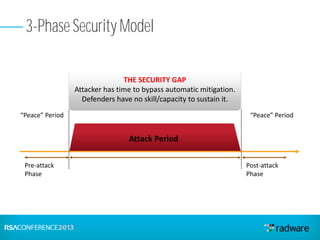
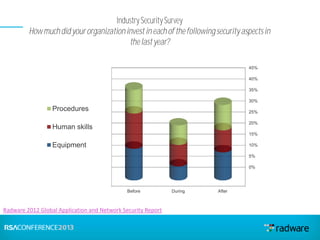
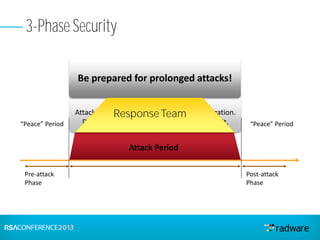
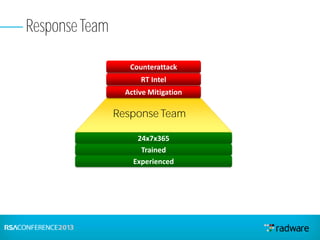
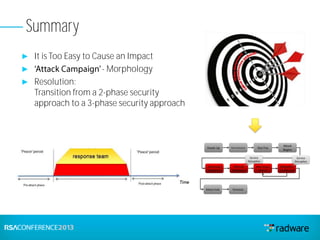
This document discusses cyberattacks against stock exchanges and provides two case studies. The first case study describes a three-day attack against a stock exchange news site, beginning with a UDP flood that caused a four hour outage. On subsequent days, additional mitigation measures were implemented and the attacks were less effective. The second case study examines a 2012 attack against Israeli stock exchanges and banks. It identifies weaknesses in a two-phase security approach and argues for a three-phase approach with an active response team to sustain defense during attacks.

![► NYSE Euronext[1]
► NASDAQ OMX Group[2]
► Hong Kong Stock Exchange[3]
► TMX Group[4]
► BATS Global Markets[5]
► Chicago Board Options Exchange[6]
► Bursa Malaysia[7]
► Tel Aviv Stock Exchange[8]
► Tadawul (Saudi Arabia)[9]
Publicly Known Attacks on Stock Exchanges
Top 10
Downtime](https://image.slidesharecdn.com/ht-r33-150420135443-conversion-gate01/85/Ht-r33-2-320.jpg)