How to use prancer to detect and fix the azure sql resources which uses tls version less than 1.2
•
0 likes•19 views
This document provides steps to use Prancer to detect and automatically remediate Azure SQL resources that use TLS versions less than 1.2. It involves creating configuration files, uploading them to Prancer, running a crawler to fetch Azure resources, running compliance tests to detect issues, viewing reports of failures, and using Prancer's remediation to fix vulnerabilities by updating TLS versions.
Report
Share
Report
Share
Download to read offline
Recommended
Detect and fix the azure sql resources which uses tls version less than 1.2

How to use Prancer to detect and fix the Azure SQL Resources which uses TLS Version less than 1.2
Solr Security: Tips and Tricks and Things You Really Ought to Know - Kevin Co...

Presented at Lucene/Solr Revolution 2017
SafePeak - How to manually configure SafePeak Cluster

This SafePeak guide describes how to configure a SafePeak cluster, by deploying two servers with SafePeak Standard / Stand-alone edition and then manually configure the NLB Cluster.
Hands-on Lab: re-Modernize - Updating and Consolidating MySQL

by Joyjeet Banerjee, Enterprise Solutions Architect, AWS
Database Week at the AWS Loft is an opportunity to learn about Amazon’s broad and deep family of managed database services. These services provide easy, scalable, reliable, and cost-effective ways to manage your data in the cloud. We explain the fundamentals and take a technical deep dive into Amazon RDS and Amazon Aurora relational databases, Amazon DynamoDB non-relational databases, Amazon Neptune graph databases, and Amazon ElastiCache managed Redis, along with options for database migration, caching, search and more. You'll will learn how to get started, how to support applications, and how to scale.
Optimize Is (Not) Bad For You - Rafał Kuć, Sematext Group, Inc.

Presented at Lucene/Solr Revolution 2017
Recommended
Detect and fix the azure sql resources which uses tls version less than 1.2

How to use Prancer to detect and fix the Azure SQL Resources which uses TLS Version less than 1.2
Solr Security: Tips and Tricks and Things You Really Ought to Know - Kevin Co...

Presented at Lucene/Solr Revolution 2017
SafePeak - How to manually configure SafePeak Cluster

This SafePeak guide describes how to configure a SafePeak cluster, by deploying two servers with SafePeak Standard / Stand-alone edition and then manually configure the NLB Cluster.
Hands-on Lab: re-Modernize - Updating and Consolidating MySQL

by Joyjeet Banerjee, Enterprise Solutions Architect, AWS
Database Week at the AWS Loft is an opportunity to learn about Amazon’s broad and deep family of managed database services. These services provide easy, scalable, reliable, and cost-effective ways to manage your data in the cloud. We explain the fundamentals and take a technical deep dive into Amazon RDS and Amazon Aurora relational databases, Amazon DynamoDB non-relational databases, Amazon Neptune graph databases, and Amazon ElastiCache managed Redis, along with options for database migration, caching, search and more. You'll will learn how to get started, how to support applications, and how to scale.
Optimize Is (Not) Bad For You - Rafał Kuć, Sematext Group, Inc.

Presented at Lucene/Solr Revolution 2017
State of Solr Security 2016: Presented by Ishan Chattopadhyaya, Lucidworks

Presented at Lucene/Solr Revolution 2016
patchVantage Cloud Starter Pack 

Quickly learn how to drive patchVantage and understand the benefits using the presentation in conjunction with the AWS Cloud Instance. This is a real-time actual Oracle Database Administration session
2018 Student360 - Beyond xp_cmdshell - Owning the Empire Through SQL Server

During this presentation, we’ll cover interesting techniques for executing operating system commands through SQL Server that can be used to avoid detection and maintain persistence during red team engagements. We’ll also talk about automating attacks through PowerShell Empire and PowerUpSQL. This will include a review of command execution through custom extended stored procedures, CLR assemblies, WMI providers, R scripts, python scripts, agent jobs, and custom ole objects. We’ll also dig into some new integrations with PowerShell Empire. All code and slide decks will be released during the presentation. This should be interesting to blue teamers looking for a faster way to test their detective control capabilities and red teamers looking for a practical way to avoid detection while trying to maintain access to their target environments.
How to Configure Amazon AWS EC2 Elastic IP Address

How To Configure Amazon AWS EE2 Elastic IP Address, Manage Elastic IP Address.
TROOPERS 20 - SQL Server Hacking Tips for Active Directory Environments

During this presentation, I’ll cover common ways to target, exploit, and escalate domain privileges through SQL Servers in Active Directory environments. I’ll also share a msbuild.exe project file that can be used as an offensive SQL Client during red team engagements when tools like PowerUpSQL are too overt.
Where there is Active Directory, there are SQL Servers. In dynamic enterprise environments it’s common to see both platforms suffer from misconfigurations that lead to unauthorized system and sensitive data access. During this presentation, I’ll cover common ways to target, exploit, and escalate domain privileges through SQL Servers in Active Directory environments. I’ll also share a msbuild.exe project file that can be used as an offensive SQL Client during red team engagements when tools like PowerUpSQL are too overt.
2017 Thotcon - Hacking SQL Servers on Scale with PowerShell

This presentation will provide an overview of common SQL Server discovery, privilege escalation, persistence, and data targeting techniques. Techniques will be shared for escalating privileges on SQL Server and associated Active Directory domains. Finally I’ll show how PowerShell automation can be used to execute the SQL Server attacks on scale with PowerUpSQL. All scripts demonstrated during the presentation are available on GitHub. This should be useful to penetration testers and system administrators trying to gain a better understanding of their SQL Server attack surface and how it can be exploited.
Hadoop sqoop2 server setup and application integration

Detail instructions about installing Sqoop2 server on Ubuntu ,integrating with Hadoop and java application.
Secure360 - Beyond xp cmdshell - Owning the Empire through SQL Server

During this presentation, we’ll cover interesting techniques for executing operating system commands through SQL Server that can be used to avoid detection and maintain persistence during red team engagements. We’ll also talk about automating attacks through PowerShell Empire and PowerUpSQL. This will include a review of command execution through custom extended stored procedures, CLR assemblies, WMI providers, R scripts, python scripts, agent jobs, and custom ole objects. We’ll also dig into some new integrations with PowerShell Empire. All code and slide decks will be released during the presentation. This should be interesting to blue teamers looking for a faster way to test their detective control capabilities and red teamers looking for a practical way to avoid detection while trying to maintain access to their target environments.
AWS essentials S3

The documents I obtain by joining a course about AWS in July 2013 in AWS Loft office in San Francisco.
PowerUpSQL - 2018 Blackhat USA Arsenal Presentation

This is the presentation we provided at the 2018 Blackhat USA Arsenal to introduce PowerUpSQL. PowerUpSQL includes functions that support SQL Server discovery, weak configuration auditing, privilege escalation on scale, and post exploitation actions such as OS command execution. It is intended to be used during internal penetration tests and red team engagements. However, PowerUpSQL also includes many functions that can be used by administrators to quickly inventory the SQL Servers in their ADS domain and perform common threat hunting tasks related to SQL Server. This should be interesting to red, blue, and purple teams interested in automating day to day tasks involving SQL Server.
More information can be found at:
https://github.com/NetSPI/PowerUpSQL/wiki
Beyond xp_cmdshell: Owning the Empire through SQL Server

During this presentation, we’ll cover interesting techniques for executing operating system commands through SQL Server that can be used to avoid detection and maintain persistence during red team engagements. We’ll also talk about automating attacks through PowerShell Empire and PowerUpSQL. This will include a review of command execution through custom extended stored procedures, CLR assemblies, WMI providers, R scripts, python scripts, agent jobs, and custom ole objects. We’ll also dig into some new integrations with PowerShell Empire. All code and slide decks will be released during the presentation.
This should be interesting to blue teamers looking for a faster way to test their detective control capabilities and red teamers looking for a practical way to avoid detection while trying to maintain access to their target environments.
Beyond XP_CMDSHELL: Owning the Empire Through SQL Server

Scott Sutherland and Alexander Leary present at Secure360 Twin Cities 2018 on Owning the Empire Through SQL Server.
Presentation includes five objectives:
- Get Access
- Hide from Audit Controls
- Execute OS Commands
- Use SQL Server as a breach head
- Detect OS Comment Execution
Questions? Contact @0xbadjuju or @_nullbind on Twitter.
2016 aRcTicCON - Hacking SQL Server on Scale with PowerShell (Slide Updates)

This is an updated version of the slides that I presented at DerbyCon 2016. It includes new slides related to some of the privilege escalation.
AWS essentials EC2

The documents I obtain by joining a course about AWS in July 2013 in AWS Loft office in San Francisco.
More Related Content
What's hot
State of Solr Security 2016: Presented by Ishan Chattopadhyaya, Lucidworks

Presented at Lucene/Solr Revolution 2016
patchVantage Cloud Starter Pack 

Quickly learn how to drive patchVantage and understand the benefits using the presentation in conjunction with the AWS Cloud Instance. This is a real-time actual Oracle Database Administration session
2018 Student360 - Beyond xp_cmdshell - Owning the Empire Through SQL Server

During this presentation, we’ll cover interesting techniques for executing operating system commands through SQL Server that can be used to avoid detection and maintain persistence during red team engagements. We’ll also talk about automating attacks through PowerShell Empire and PowerUpSQL. This will include a review of command execution through custom extended stored procedures, CLR assemblies, WMI providers, R scripts, python scripts, agent jobs, and custom ole objects. We’ll also dig into some new integrations with PowerShell Empire. All code and slide decks will be released during the presentation. This should be interesting to blue teamers looking for a faster way to test their detective control capabilities and red teamers looking for a practical way to avoid detection while trying to maintain access to their target environments.
How to Configure Amazon AWS EC2 Elastic IP Address

How To Configure Amazon AWS EE2 Elastic IP Address, Manage Elastic IP Address.
TROOPERS 20 - SQL Server Hacking Tips for Active Directory Environments

During this presentation, I’ll cover common ways to target, exploit, and escalate domain privileges through SQL Servers in Active Directory environments. I’ll also share a msbuild.exe project file that can be used as an offensive SQL Client during red team engagements when tools like PowerUpSQL are too overt.
Where there is Active Directory, there are SQL Servers. In dynamic enterprise environments it’s common to see both platforms suffer from misconfigurations that lead to unauthorized system and sensitive data access. During this presentation, I’ll cover common ways to target, exploit, and escalate domain privileges through SQL Servers in Active Directory environments. I’ll also share a msbuild.exe project file that can be used as an offensive SQL Client during red team engagements when tools like PowerUpSQL are too overt.
2017 Thotcon - Hacking SQL Servers on Scale with PowerShell

This presentation will provide an overview of common SQL Server discovery, privilege escalation, persistence, and data targeting techniques. Techniques will be shared for escalating privileges on SQL Server and associated Active Directory domains. Finally I’ll show how PowerShell automation can be used to execute the SQL Server attacks on scale with PowerUpSQL. All scripts demonstrated during the presentation are available on GitHub. This should be useful to penetration testers and system administrators trying to gain a better understanding of their SQL Server attack surface and how it can be exploited.
Hadoop sqoop2 server setup and application integration

Detail instructions about installing Sqoop2 server on Ubuntu ,integrating with Hadoop and java application.
Secure360 - Beyond xp cmdshell - Owning the Empire through SQL Server

During this presentation, we’ll cover interesting techniques for executing operating system commands through SQL Server that can be used to avoid detection and maintain persistence during red team engagements. We’ll also talk about automating attacks through PowerShell Empire and PowerUpSQL. This will include a review of command execution through custom extended stored procedures, CLR assemblies, WMI providers, R scripts, python scripts, agent jobs, and custom ole objects. We’ll also dig into some new integrations with PowerShell Empire. All code and slide decks will be released during the presentation. This should be interesting to blue teamers looking for a faster way to test their detective control capabilities and red teamers looking for a practical way to avoid detection while trying to maintain access to their target environments.
AWS essentials S3

The documents I obtain by joining a course about AWS in July 2013 in AWS Loft office in San Francisco.
PowerUpSQL - 2018 Blackhat USA Arsenal Presentation

This is the presentation we provided at the 2018 Blackhat USA Arsenal to introduce PowerUpSQL. PowerUpSQL includes functions that support SQL Server discovery, weak configuration auditing, privilege escalation on scale, and post exploitation actions such as OS command execution. It is intended to be used during internal penetration tests and red team engagements. However, PowerUpSQL also includes many functions that can be used by administrators to quickly inventory the SQL Servers in their ADS domain and perform common threat hunting tasks related to SQL Server. This should be interesting to red, blue, and purple teams interested in automating day to day tasks involving SQL Server.
More information can be found at:
https://github.com/NetSPI/PowerUpSQL/wiki
Beyond xp_cmdshell: Owning the Empire through SQL Server

During this presentation, we’ll cover interesting techniques for executing operating system commands through SQL Server that can be used to avoid detection and maintain persistence during red team engagements. We’ll also talk about automating attacks through PowerShell Empire and PowerUpSQL. This will include a review of command execution through custom extended stored procedures, CLR assemblies, WMI providers, R scripts, python scripts, agent jobs, and custom ole objects. We’ll also dig into some new integrations with PowerShell Empire. All code and slide decks will be released during the presentation.
This should be interesting to blue teamers looking for a faster way to test their detective control capabilities and red teamers looking for a practical way to avoid detection while trying to maintain access to their target environments.
Beyond XP_CMDSHELL: Owning the Empire Through SQL Server

Scott Sutherland and Alexander Leary present at Secure360 Twin Cities 2018 on Owning the Empire Through SQL Server.
Presentation includes five objectives:
- Get Access
- Hide from Audit Controls
- Execute OS Commands
- Use SQL Server as a breach head
- Detect OS Comment Execution
Questions? Contact @0xbadjuju or @_nullbind on Twitter.
2016 aRcTicCON - Hacking SQL Server on Scale with PowerShell (Slide Updates)

This is an updated version of the slides that I presented at DerbyCon 2016. It includes new slides related to some of the privilege escalation.
What's hot (19)
State of Solr Security 2016: Presented by Ishan Chattopadhyaya, Lucidworks

State of Solr Security 2016: Presented by Ishan Chattopadhyaya, Lucidworks
2018 Student360 - Beyond xp_cmdshell - Owning the Empire Through SQL Server

2018 Student360 - Beyond xp_cmdshell - Owning the Empire Through SQL Server
How to Configure Amazon AWS EC2 Elastic IP Address

How to Configure Amazon AWS EC2 Elastic IP Address
TROOPERS 20 - SQL Server Hacking Tips for Active Directory Environments

TROOPERS 20 - SQL Server Hacking Tips for Active Directory Environments
2017 Thotcon - Hacking SQL Servers on Scale with PowerShell

2017 Thotcon - Hacking SQL Servers on Scale with PowerShell
Hadoop sqoop2 server setup and application integration

Hadoop sqoop2 server setup and application integration
Secure360 - Beyond xp cmdshell - Owning the Empire through SQL Server

Secure360 - Beyond xp cmdshell - Owning the Empire through SQL Server
PowerUpSQL - 2018 Blackhat USA Arsenal Presentation

PowerUpSQL - 2018 Blackhat USA Arsenal Presentation
Beyond xp_cmdshell: Owning the Empire through SQL Server

Beyond xp_cmdshell: Owning the Empire through SQL Server
Beyond XP_CMDSHELL: Owning the Empire Through SQL Server

Beyond XP_CMDSHELL: Owning the Empire Through SQL Server
Oracle business intelligence enterprise edition 11g

Oracle business intelligence enterprise edition 11g
2016 aRcTicCON - Hacking SQL Server on Scale with PowerShell (Slide Updates)

2016 aRcTicCON - Hacking SQL Server on Scale with PowerShell (Slide Updates)
Similar to How to use prancer to detect and fix the azure sql resources which uses tls version less than 1.2
AWS essentials EC2

The documents I obtain by joining a course about AWS in July 2013 in AWS Loft office in San Francisco.
sfdx continuous Integration with Jenkins on aws (Part I)

Sfdx is now an essential tool to set up in salesforce projects. It is used to ease the development of LWC and also to facilitate the continuous delivery of the code and its versioning.
With the experience gained on my latest projects in SFDX release management, I made a small guide for setting up a simple continuous delivery system in the frame of an sfdx project.
Oracle Database Backup

Backing up Oracle Databases with Handy Backup http://www.handybackup.net/oracle-backup-features.shtml
White Paper On ConCurrency For PCMS Application Architecture

White Paper On ConCurrency For PCMS Application Architecture
Asset Model Import FlexConnector Developer's Guide

Asset Model Import FlexConnector Developer's Guide
UPGRADING FROM ORACLE ENTERPRISE MANAGER 10G TO CLOUD CONTROL 12C WITH ZERO D...

A step-by-step description of using the 2-System Method to upgrade from Oracle Enterprise Manager 10g to Enterprise Manager Cloud Control 12c while upgrading database and migrating platforms with near zero downtime.
Hands-on Lab: Migrating Oracle to PostgreSQL 

by Ben Willett, Solutions Architect, AWS
Database Week at the AWS Loft is an opportunity to learn about Amazon’s broad and deep family of managed database services. These services provide easy, scalable, reliable, and cost-effective ways to manage your data in the cloud. We explain the fundamentals and take a technical deep dive into Amazon RDS and Amazon Aurora relational databases, Amazon DynamoDB non-relational databases, Amazon Neptune graph databases, and Amazon ElastiCache managed Redis, along with options for database migration, caching, search and more. You'll will learn how to get started, how to support applications, and how to scale.
[WSO2] Deployment Synchronizer for Deployment Artifact Synchronization Betwee...![[WSO2] Deployment Synchronizer for Deployment Artifact Synchronization Betwee...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[WSO2] Deployment Synchronizer for Deployment Artifact Synchronization Betwee...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Setting up a cluster is important when developing enterprise software and deploying them in production environments. Distributing deployment artifacts & related metadata to all nodes in a homogeneous cluster is a typical requirement for a clustered deployment of any middleware platform. In such a cluster, all nodes should contain the deployed artifacts as well as the related metadata.
The Deployment Synchronizer (DepSync) is the mechanism used in the WSO2 platform for distributing these artifacts and metadata across all nodes in the cluster. It provides the ability to synchronize data between the worker nodes of a product cluster. When used with the WSO2 Application Server, or the WSO2 ESB, you can synchronize your deployable artifacts like web services, and web applications etc. across the cluster nodes. In addition, with the latest WSO2 Carbon 4 release, WSO2 provides the ability to synchronize service metadata which includes service policies, transports, and service-type specific data. Now you only have to deploy and configure services in one node - called the manager. Then, DepSync will replicate those to other nodes - workers.
In this presentation, we present how this is done in the WSO2 Cloud-enabled middleware platform. Typical deployment artifacts will include webapps, JAXWS/JAXRS apps, data services, proxy services, and BPEL processes . The WSO2 platform also natively supports multi-tenancy. Tenants & tenant artifacts are loaded on demand. We will demonstrate how DepSync works efficiently with multi-tenancy.
Kasun Gajasinghe did the demonstration section of this webinar presentation while Pradeep Fernando provided technical aspects of Deployment Synchronizer
Database upgradation

Contents
Types of Upgrade
Compatability to upgrade 11g from 10g
Install 11g software
Preupgrade checkups
Upgrade
Post Upgrade Steps
Known Issues
ESM Asset Model FlexConnector Developer's Guide for ESM 6.8c

ESM Asset Model FlexConnector Developer's Guide for ESM 6.8c
Similar to How to use prancer to detect and fix the azure sql resources which uses tls version less than 1.2 (20)
sfdx continuous Integration with Jenkins on aws (Part I)

sfdx continuous Integration with Jenkins on aws (Part I)
White Paper On ConCurrency For PCMS Application Architecture

White Paper On ConCurrency For PCMS Application Architecture
Asset Model Import FlexConnector Developer's Guide

Asset Model Import FlexConnector Developer's Guide
UPGRADING FROM ORACLE ENTERPRISE MANAGER 10G TO CLOUD CONTROL 12C WITH ZERO D...

UPGRADING FROM ORACLE ENTERPRISE MANAGER 10G TO CLOUD CONTROL 12C WITH ZERO D...
WSO2 Dep Sync for Artifact Synchronization of Cluster Nodes

WSO2 Dep Sync for Artifact Synchronization of Cluster Nodes
[WSO2] Deployment Synchronizer for Deployment Artifact Synchronization Betwee...![[WSO2] Deployment Synchronizer for Deployment Artifact Synchronization Betwee...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[WSO2] Deployment Synchronizer for Deployment Artifact Synchronization Betwee...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[WSO2] Deployment Synchronizer for Deployment Artifact Synchronization Betwee...
ESM Asset Model FlexConnector Developer's Guide for ESM 6.8c

ESM Asset Model FlexConnector Developer's Guide for ESM 6.8c
More from Prancer Io
Prancer Enterprise has achieved SOC 2 Type I compliance in accordance with Am...

Prancer provides a comprehensive suite of Code security and penetration testing as code (PAC) solutions to enable shift-left approaches to implement preventative controls and offensive security testing mechanisms.
Prancer Enterprise announces today the release of the Zero Trust Security Val...

Prancer Enterprise, a visionary cloud security startup specializing in offensive and defensive security tools, announced today the release of the Zero Trust Security Validation Service technology.
Prancer for Offensive Security Testing

Whether you’re a pentester or a developer, there are several advantages to employing automated offensive security tools like Prancer for cloud environments.
Why do Next-generation snapshot scanning security solutions raise security co...

Agent-based scanning is getting less relevant because modern cloud-native elastic workloads are too fast-moving and dynamic for agents to keep up.
Announcing the launch of Red and Blue Cyber Security Show

Prancer provides a comprehensive suite of Infrastructure As Code (IAC) security and penetration testing as code (PAC) solutions to enable shift-left approaches.
9 tips for assessing your modern cloud security toolsets.pdf

Cloud specific security tooling is essential for protecting your cloud application and data. Today, organizations in the cloud use multiple open source tools to secure their cloud ecosystem across several domains. This includes workload protection, infrastructure protection, application protection, static code analysis and security incident management. How are you evaluating your cloud security toolsets? Here are 9 tips used in the industry to evaluate whether your system is effective…or not!
Infrastructure as Code

If you would like to learn more about cloud technology and security, IaC, compliance, Azure, and much more, be sure to contact the experts at prancer.
IAC Compliance.pdf

Prancer provides a cloud validation framework that can effectively test for compliance and offer solutions in an ever-changing environment. Contact us today to learn more and get started.
IaC Security and Continuous Compliance

Prancer Enterprise (https://www.prancer.io) provides a pre-deployment and post-deployment multi-cloud security platform for Infrastructure as Code (IaC) and live cloud environments.
IaC Security and Continuous Compliance

Prancer Enterprise (https://www.prancer.io) provides a pre-deployment and post-deployment multi-cloud security platform for Infrastructure as Code (IaC) and live cloud environments.
Security Validation as Code

If you’re interested in implementing Security Validation as Code for your cloud applications, sign up for Prancer Platform!
Automated Pentesting vs Dynamic Application Security Testing

Dynamic application security testing (DAST) is a form of security testing that involves the manual or automated testing of applications while they are in use.
Security Validation

Security Validation as Code enables validation of cloud applications and infrastructure in a more automated and API-driven way. If you’re interested in implementing Security Validation as Code for your cloud applications, sign up for Prancer Platform!
Cloud Security Validation at Scale

Shift Security to the left by Prancer's end-to-end cloud security platform. Pentesting as Code (PAC) codifies and validates the company's cloud resources against the zero-day vulnerabilities and latest cyber security threats in real-time to build an attack-ready cloud. Infrastructure as Code (IaC) Static Code Analysis (SCA) ensures the secure code hits the cloud and the Prancer's CSPM engine gathers information from cloud live resources to support these initiatives.
Security Validation as Code.pdf

Cloud applications demand security validation to guarantee that the software is safe and compliant with security standards. It also aids in the prevention of data breaches and other threats prevalent to the public cloud.
Prancer web interface for the ease of use

Only available in the Enterprise and Premium versions of the product, companies can use the web interface to fully customize and monitor their experience with Prancer.
What are the configuration files in the prancer framework

There are different configuration items and files available in the Prancer framework. The Prancer framework is at the heart of the Prancer Platform. The different configuration files available in the Prancer framework are as follows:
Automated pentesting vs dynamic application security testing (dast) (2)

Dynamic application security testing (DAST) is a form of security testing that involves the manual or automated testing of applications while they are in use. This type of security testing is used to identify vulnerabilities that could be exploited by attackers. DAST is often used in conjunction with static application security testing (SAST) to have a more comprehensive view of web application vulnerabilities.
Is iac scanning scalable in the git ops era

Gitops is breaking down boundaries between the CI and CD processes for infrastructure projects, ensuring that your cloud resources are always in sync with your coding base. The injection of IAC scans after code commit in CD phase causes disruption.
Prancer web interface for the ease of use

Prancer platform provides full API access for enterprise customers. Only available in the Enterprise and Premium versions of the product, you can interact with the prancer platform with the REST API calls. You can integrate the prancer platform to your current CI/CD pipeline in your DevSecOps process. Also, Enterprise CLI is available to fully customize the platform from a command-line interface
More from Prancer Io (20)
Prancer Enterprise has achieved SOC 2 Type I compliance in accordance with Am...

Prancer Enterprise has achieved SOC 2 Type I compliance in accordance with Am...
Prancer Enterprise announces today the release of the Zero Trust Security Val...

Prancer Enterprise announces today the release of the Zero Trust Security Val...
Why do Next-generation snapshot scanning security solutions raise security co...

Why do Next-generation snapshot scanning security solutions raise security co...
Announcing the launch of Red and Blue Cyber Security Show

Announcing the launch of Red and Blue Cyber Security Show
9 tips for assessing your modern cloud security toolsets.pdf

9 tips for assessing your modern cloud security toolsets.pdf
Automated Pentesting vs Dynamic Application Security Testing

Automated Pentesting vs Dynamic Application Security Testing
What are the configuration files in the prancer framework

What are the configuration files in the prancer framework
Automated pentesting vs dynamic application security testing (dast) (2)

Automated pentesting vs dynamic application security testing (dast) (2)
Recently uploaded
Essentials of Automations: The Art of Triggers and Actions in FME

In this second installment of our Essentials of Automations webinar series, we’ll explore the landscape of triggers and actions, guiding you through the nuances of authoring and adapting workspaces for seamless automations. Gain an understanding of the full spectrum of triggers and actions available in FME, empowering you to enhance your workspaces for efficient automation.
We’ll kick things off by showcasing the most commonly used event-based triggers, introducing you to various automation workflows like manual triggers, schedules, directory watchers, and more. Plus, see how these elements play out in real scenarios.
Whether you’re tweaking your current setup or building from the ground up, this session will arm you with the tools and insights needed to transform your FME usage into a powerhouse of productivity. Join us to discover effective strategies that simplify complex processes, enhancing your productivity and transforming your data management practices with FME. Let’s turn complexity into clarity and make your workspaces work wonders!
Microsoft - Power Platform_G.Aspiotis.pdf

Revolutionizing Application Development
with AI-powered low-code, presentation by George Aspiotis, Sr. Partner Development Manager, Microsoft
UiPath Test Automation using UiPath Test Suite series, part 5

Welcome to UiPath Test Automation using UiPath Test Suite series part 5. In this session, we will cover CI/CD with devops.
Topics covered:
CI/CD with in UiPath
End-to-end overview of CI/CD pipeline with Azure devops
Speaker:
Lyndsey Byblow, Test Suite Sales Engineer @ UiPath, Inc.
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

The choice of an operating system plays a pivotal role in shaping our computing experience. For decades, Microsoft's Windows has dominated the market, offering a familiar and widely adopted platform for personal and professional use. However, as technological advancements continue to push the boundaries of innovation, alternative operating systems have emerged, challenging the status quo and offering users a fresh perspective on computing.
One such alternative that has garnered significant attention and acclaim is Nitrux Linux 3.5.0, a sleek, powerful, and user-friendly Linux distribution that promises to redefine the way we interact with our devices. With its focus on performance, security, and customization, Nitrux Linux presents a compelling case for those seeking to break free from the constraints of proprietary software and embrace the freedom and flexibility of open-source computing.
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
20240609 QFM020 Irresponsible AI Reading List May 2024

Everything I found interesting about the irresponsible use of machine intelligence in May 2024
GridMate - End to end testing is a critical piece to ensure quality and avoid...

End to end testing is a critical piece to ensure quality and avoid regressions. In this session, we share our journey building an E2E testing pipeline for GridMate components (LWC and Aura) using Cypress, JSForce, FakerJS…
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
UiPath Test Automation using UiPath Test Suite series, part 6

Welcome to UiPath Test Automation using UiPath Test Suite series part 6. In this session, we will cover Test Automation with generative AI and Open AI.
UiPath Test Automation with generative AI and Open AI webinar offers an in-depth exploration of leveraging cutting-edge technologies for test automation within the UiPath platform. Attendees will delve into the integration of generative AI, a test automation solution, with Open AI advanced natural language processing capabilities.
Throughout the session, participants will discover how this synergy empowers testers to automate repetitive tasks, enhance testing accuracy, and expedite the software testing life cycle. Topics covered include the seamless integration process, practical use cases, and the benefits of harnessing AI-driven automation for UiPath testing initiatives. By attending this webinar, testers, and automation professionals can gain valuable insights into harnessing the power of AI to optimize their test automation workflows within the UiPath ecosystem, ultimately driving efficiency and quality in software development processes.
What will you get from this session?
1. Insights into integrating generative AI.
2. Understanding how this integration enhances test automation within the UiPath platform
3. Practical demonstrations
4. Exploration of real-world use cases illustrating the benefits of AI-driven test automation for UiPath
Topics covered:
What is generative AI
Test Automation with generative AI and Open AI.
UiPath integration with generative AI
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

Leonard Jayamohan, Partner & Generative AI Lead, Deloitte
This keynote will reveal how Deloitte leverages Neo4j’s graph power for groundbreaking digital twin solutions, achieving a staggering 100x performance boost. Discover the essential role knowledge graphs play in successful generative AI implementations. Plus, get an exclusive look at an innovative Neo4j + Generative AI solution Deloitte is developing in-house.
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
Uni Systems Copilot event_05062024_C.Vlachos.pdf

Unlocking Productivity: Leveraging the Potential of Copilot in Microsoft 365, a presentation by Christoforos Vlachos, Senior Solutions Manager – Modern Workplace, Uni Systems
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

As the digital landscape continually evolves, operating systems play a critical role in shaping user experiences and productivity. The launch of Nitrux Linux 3.5.0 marks a significant milestone, offering a robust alternative to traditional systems such as Windows 11. This article delves into the essence of Nitrux Linux 3.5.0, exploring its unique features, advantages, and how it stands as a compelling choice for both casual users and tech enthusiasts.
GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024

Maruthi Prithivirajan, Head of ASEAN & IN Solution Architecture, Neo4j
Get an inside look at the latest Neo4j innovations that enable relationship-driven intelligence at scale. Learn more about the newest cloud integrations and product enhancements that make Neo4j an essential choice for developers building apps with interconnected data and generative AI.
A tale of scale & speed: How the US Navy is enabling software delivery from l...

Rapid and secure feature delivery is a goal across every application team and every branch of the DoD. The Navy’s DevSecOps platform, Party Barge, has achieved:
- Reduction in onboarding time from 5 weeks to 1 day
- Improved developer experience and productivity through actionable findings and reduction of false positives
- Maintenance of superior security standards and inherent policy enforcement with Authorization to Operate (ATO)
Development teams can ship efficiently and ensure applications are cyber ready for Navy Authorizing Officials (AOs). In this webinar, Sigma Defense and Anchore will give attendees a look behind the scenes and demo secure pipeline automation and security artifacts that speed up application ATO and time to production.
We will cover:
- How to remove silos in DevSecOps
- How to build efficient development pipeline roles and component templates
- How to deliver security artifacts that matter for ATO’s (SBOMs, vulnerability reports, and policy evidence)
- How to streamline operations with automated policy checks on container images
Recently uploaded (20)
Essentials of Automations: The Art of Triggers and Actions in FME

Essentials of Automations: The Art of Triggers and Actions in FME
UiPath Test Automation using UiPath Test Suite series, part 5

UiPath Test Automation using UiPath Test Suite series, part 5
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
20240609 QFM020 Irresponsible AI Reading List May 2024

20240609 QFM020 Irresponsible AI Reading List May 2024
GridMate - End to end testing is a critical piece to ensure quality and avoid...

GridMate - End to end testing is a critical piece to ensure quality and avoid...
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
Monitoring Java Application Security with JDK Tools and JFR Events

Monitoring Java Application Security with JDK Tools and JFR Events
UiPath Test Automation using UiPath Test Suite series, part 6

UiPath Test Automation using UiPath Test Suite series, part 6
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!
GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024

GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024
A tale of scale & speed: How the US Navy is enabling software delivery from l...

A tale of scale & speed: How the US Navy is enabling software delivery from l...
How to use prancer to detect and fix the azure sql resources which uses tls version less than 1.2
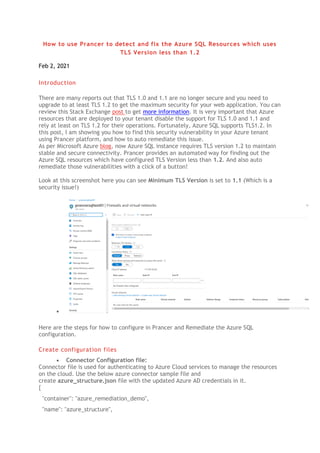
- 1. How to use Prancer to detect and fix the Azure SQL Resources which uses TLS Version less than 1.2 Feb 2, 2021 Introduction There are many reports out that TLS 1.0 and 1.1 are no longer secure and you need to upgrade to at least TLS 1.2 to get the maximum security for your web application. You can review this Stack Exchange post to get more information. It is very important that Azure resources that are deployed to your tenant disable the support for TLS 1.0 and 1.1 and rely at least on TLS 1.2 for their operations. Fortunately, Azure SQL supports TLS1.2. In this post, I am showing you how to find this security vulnerability in your Azure tenant using Prancer platform, and how to auto remediate this issue. As per Microsoft Azure blog, now Azure SQL instance requires TLS version 1.2 to maintain stable and secure connectivity. Prancer provides an automated way for finding out the Azure SQL resources which have configured TLS Version less than 1.2. And also auto remediate those vulnerabilities with a click of a button! Look at this screenshot here you can see Minimum TLS Version is set to 1.1 (Which is a security issue!) • Here are the steps for how to configure in Prancer and Remediate the Azure SQL configuration. Create configuration files • Connector Configuration file: Connector file is used for authenticating to Azure Cloud services to manage the resources on the cloud. Use the below azure connector sample file and create azure_structure.json file with the updated Azure AD credentials in it. { "container": "azure_remediation_demo", "name": "azure_structure",
- 2. "json": { "type": "azure", "fileType": "structure", "companyName": "Prancer", // replace your tenant id "tenant_id": "f997f2f9-a48f-****-****-************", "autoRemediate": true, "accounts": [ { "department": "Network Security", "subscription": [ { "subscription_name": "whitekite", "subscription_description": "whitekite", // replace your subscription id "subscription_id": "d34d6141-7a19-****-****-************", "users": [ { // subscription user name. "name": "abc*****@gmail.com", // replace your client id "client_id": "db57053a-7bce-****-****-************" } ] } ] } ] } } • Master Snapshot Configuration file: Master Snapshot configuration file is used to define resource type details which you want to execute the compliance test on. Create azure_snapshot.json file, based on the below sample configuration json file. { "container": "azure_remediation_demo",
- 3. "name": "azure_snapshot", "json": { "contentVersion": "1.0.0.0", "fileType": "masterSnapshot", "snapshots": [ { "source": "azure_structure", "type": "azure", // subscription user name, should be same as used in connector file "testUser": "abc*****@gmail.com", // subscription id, should be same as used in connector file "subscription_id": "d34d6141-7a19-****-****-************", "nodes": [ { "masterSnapshotId": "AZURE_SQL", "type": "Microsoft.Sql/servers", "collection": "Microsoft.Servers" } ] } ] } } • Master Compliance Configuration file: Master Compliance configuration file contains the list of testcases that will be run on fetched cloud resource json files. Create azure_test.json file, based on the below configuration json file. { "container": "azure_remediation_demo", "name": "azure_test", "json": { "contentVersion": "1.0.0.0", "fileType": "mastertest", "masterSnapshot": "azure_snapshot", "testSet": [ {
- 4. "masterTestName": "AZURE_TEST", "version": "0.1", "cases": [ { "masterTestId": "AZURE_SQL_TEST", "type": "rego", "rule": "file(azure_sql.rego)", "tags": [ { "cloud": "Azure", "compliance": [], "service": [ "Databases" ] } ], "evals": [ { "id": "sql_tls_version", "eval": "data.rule.tls_version", "message": "data.rule.tls_version_err", "remediationDescription": "Mannual Steps: n 1) Open Azure Portal. n 2) Open SQL Servers list n 3) Select the SQL Server for which you want to modify the Mimimal TLS Version. n 4) Click on `Firewalls and virtual networks` option under `Security` section. n 5) Update the Minimum TLS Version to `1.2` and click on save button.", "remediationFunction": "remediate_security_rule.py" } ], "title": "Azure SQL Database check minumum TLS version", "description": "This policy will find the Azure SQL Databases which are set the minumum TLS version lower then 1.2", "masterSnapshotId": [ "AZURE_SQL" ], "status": "enable" }
- 5. ] } ], "notification": [] } } • Rego file: Create the azure_sql.rego file which contains the rule checks which will be perform against cloud resource. Create azure_sql.rego file as below. package rule sql_database_issue["invalid_minimal_tls_version"] { lower(input.type) == "microsoft.sql/servers" input.properties.minimalTlsVersion != "1.2" } default tls_version = null tls_version = true { not sql_database_issue["invalid_minimal_tls_version"] } tls_version = false { sql_database_issue["invalid_minimal_tls_version"] } tls_version_err = "Azure SQL Database has set minumum TLS version lower then 1.2" { sql_database_issue["invalid_minimal_tls_version"] } Upload configuration files on Prancer • Create Collection: All the configuration files Connector configuration file, Snapshot configuration file, Compliance Configuration file, Rego files should be store in a collection. The name of the collection should be same as one which we defined in all configuration json files. Here we have set azure_remediation_demo value as container_name in all configuration json files. To create a new collection on Prancer:
- 6. 1. Open the collection screen from left side menu items. 2. Click on Add Collection button. 3. Enter the collection name and click on save button. • Upload Rego file Once collection is created, you can see the created collection in the collection list. Now we can upload the Rego file to that collection. To upload the Rego file, 1. Click on upload button 2. Drag and drop the azure_sql.rego file in file upload area. 3. Click on Upload button.
- 7. • Upload Connector file For upload a Connector Configuration file, 1. Open connector upload screen. 2. Drag and drop the azure_structure.json file in file upload area. 3. Click on Upload Connector button. • Upload Master Snapshot Configuration file For upload a Master Snapshot configuration file, 1. Open screen for upload new snapshot. 2. Drag and drop the azure_snapshot.json file in file upload area. 3. Select Master Resource Snapshot option as a Snapshot Type.
- 8. 4. Click on Submit button. • Upload Compliance Configuration file For upload a compliance file, 1. Open screen for upload new compliance. 2. Drag and drop the azure_test.json file in file upload area. 3. Select Master Compliance option as a Compliance Type. 4. Click on Submit button. Set client secret value in vault
- 9. • For security purpose we are storing the confidential data in azure vault. • In azure_structure.json file, we have set the Client Id db57053a-7bce-****-****- ************. Now require to add the Client Secret value of that client id into the vault. Run Crawler • Crawler is the process in which Prancer will connect to Azure cloud with your provided credentials and will get the list of cloud resources. It generates the Snapshot Configuration file which contains the list of cloud resources. To crawl the resources: 1. Open the Run Crawler screen. 2. Select the collection name azure_remediation_demo. 3. Click on Run Crawler button.
- 10. Verify generated snapshot files: Once the crawler is done then verify that the cloud resources are fetched correctly or not. • Open All Resource Configuration screen. • Select the Resource Configuration Tab • Search for your collection name. • It should show the generated snapshot in the list. ’ Click on the generated snapshot list item to verify that resources are fetched correctly.
- 11. Run compliance Once you verify that all the resources are fetched correctly, we can run the compliance on it. • Open the Run Compliance screen. • Select the collection name azure_remediation_demo • Click on Run Test button. Check Report Once the compliance process is completed then we can see the pass/fail reports in report page.
- 12. • Open the Report screen. • It will show the latest compliance report by default. • It takes sometime to show the latest report based on number of resources available. so if you did not see the report then after few seconds click on filter button for see the latest report. • In report you can see the list of resources and it’s status (pass/fail) • Click on the failed resource for view detail information of it. • You can see the path of the cloud resource and manual steps for fix the issue. • Click on Remediation button for fix the problem. It will run the process for fix the problem on cloud and will give the success message about Remediation done.
- 13. Verify Azure SQL on Portal
