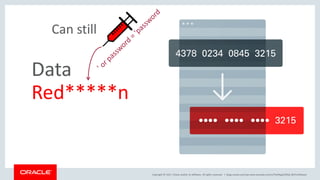
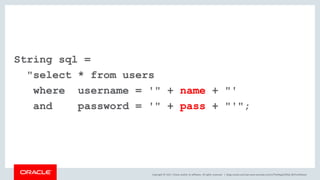
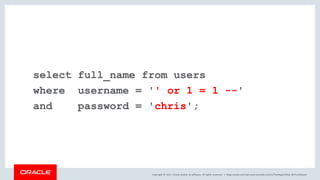
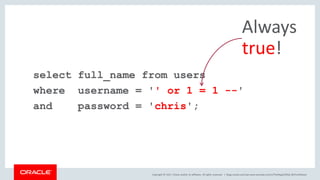
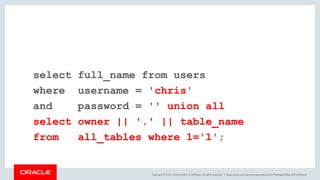
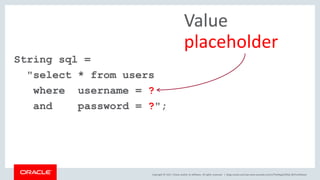
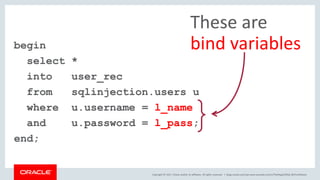
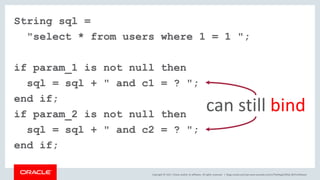
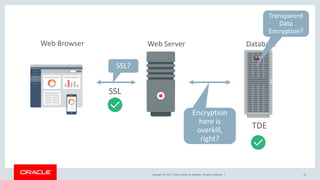
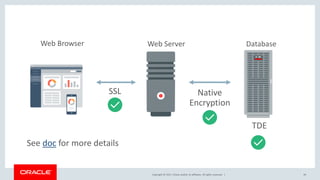
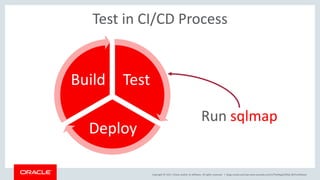
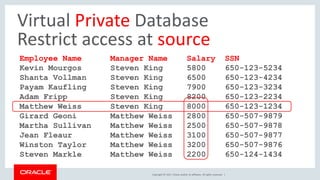
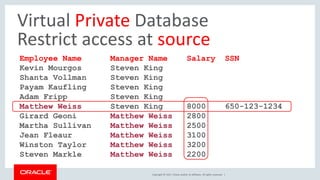
The document discusses SQL vulnerabilities and security practices, emphasizing the importance of sanitizing inputs and using bind variables to prevent SQL injections. It highlights various real-world hacking incidents and suggests employing a layered security approach. Overall, the document serves as a tutorial for developers on securing their applications against SQL-related attacks.