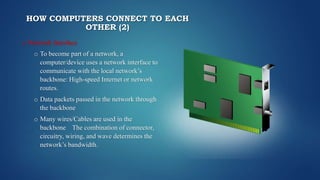
The document discusses various types of computer networks, including LAN, WAN, PAN, and MAN, and their components like servers, clients, routers, and switches. It explains how devices connect through different mediums such as twisted-pair wiring, coaxial cable, and fiber optic cable, as well as wireless connections. Additionally, it covers the functioning of data packets in transmission, Bluetooth connectivity, and NFC (Near Field Communication) technology for short-range data exchange.