The document proposes a Technological Framework for Safe and Secure Cities (TFSSC) to address homeland security threats. The framework includes:
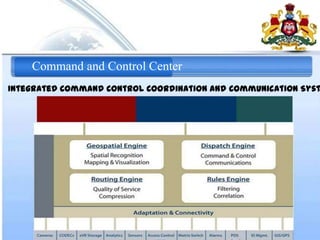
1. Command and control centers to integrate different data feeds and coordinate emergency response.
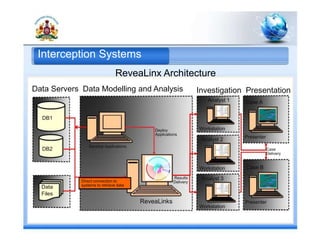
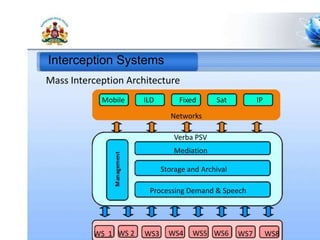
2. Interception systems to monitor communications and gather intelligence.
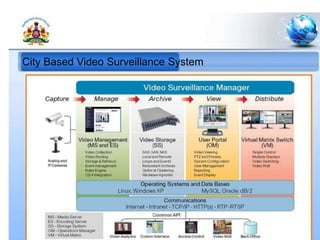
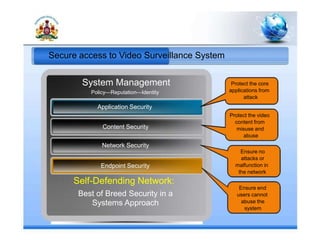
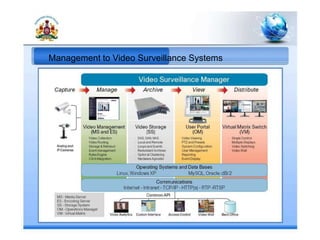
3. A city-based video surveillance system to provide video evidence.
4. A TETRA radio network for secure digital police communication.
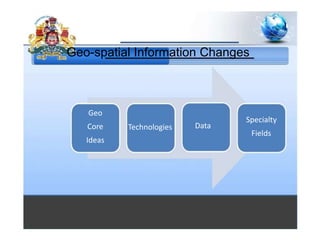
5. Geospatial technology to provide mapping and situational awareness.
6. An ERP system and database integration to share information across departments.
7. Training programs to improve managerial response to security threats.