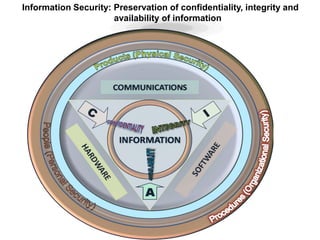
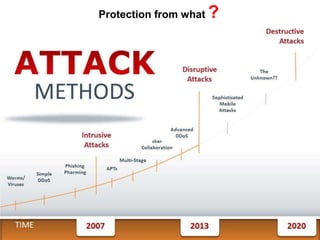
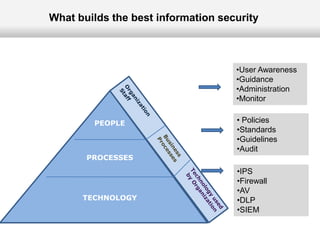
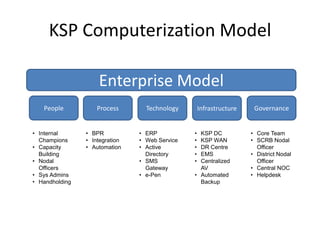
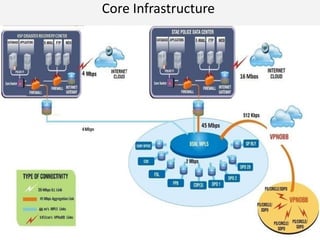
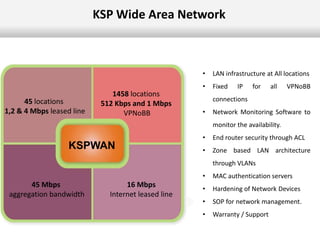
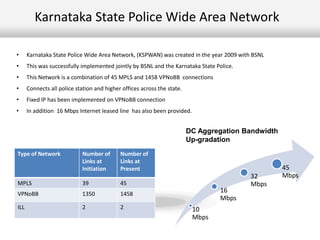
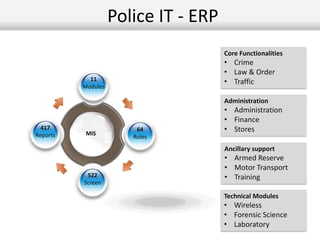
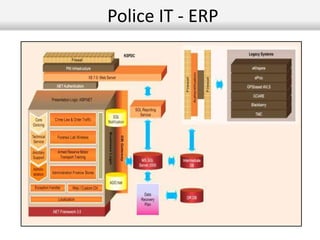
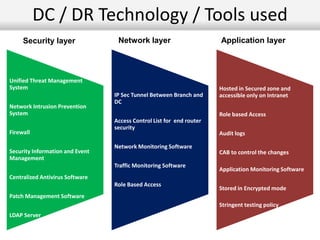
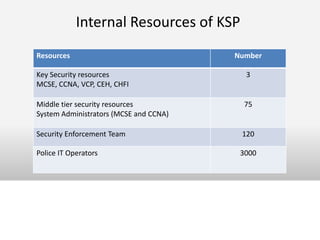
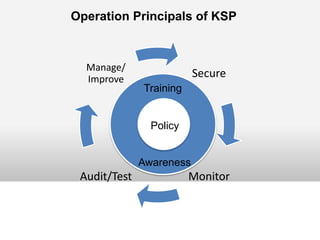
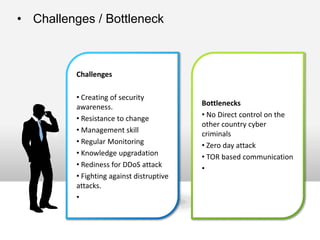
This document outlines the information security model and infrastructure of the Karnataka State Police (KSP). It discusses the people, processes, and technology that comprise the KSP security operations. The key aspects of the KSP security model include user awareness training, security policies and guidelines, centralized antivirus and firewall protection, network monitoring tools, and role-based access controls. The document also provides an overview of the KSP computer network and data centers, and discusses some ongoing challenges and areas for further improvement.