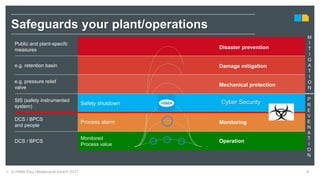
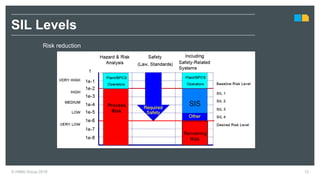
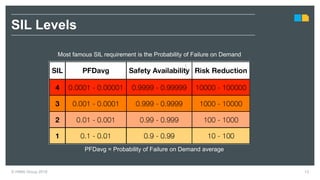
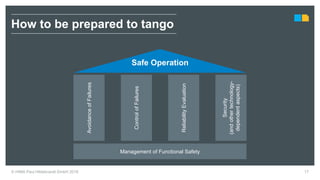
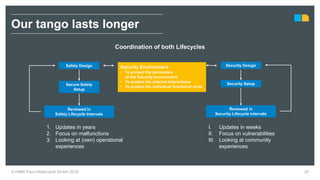
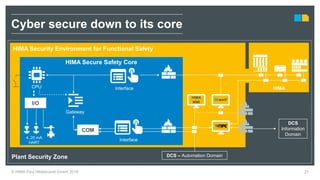
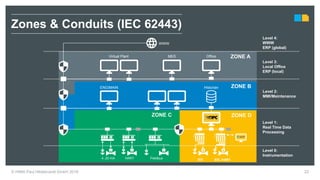
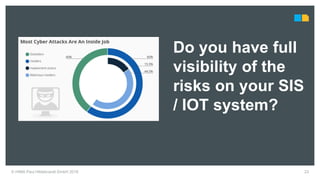
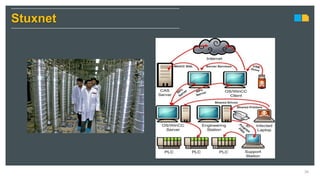
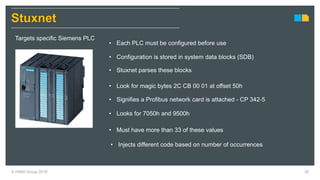
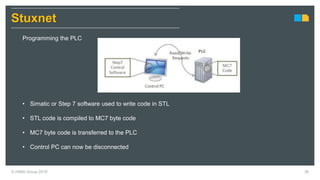
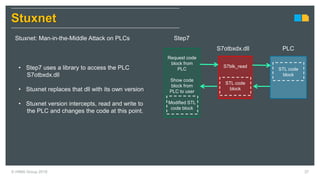
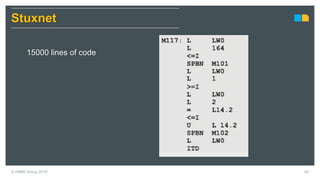
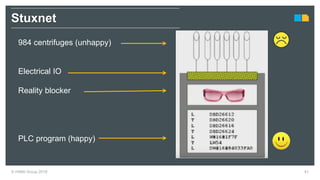
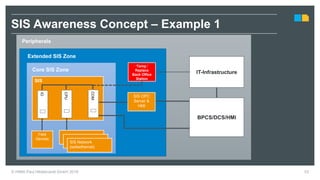
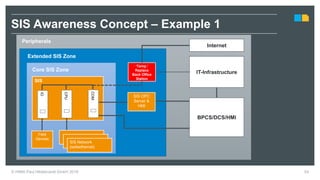
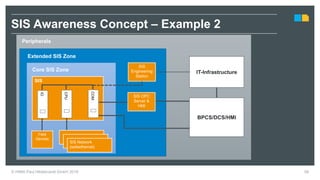
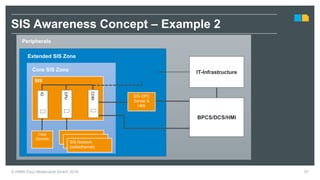
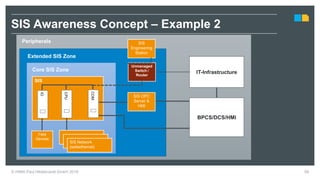
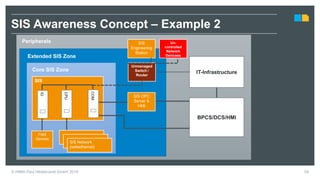
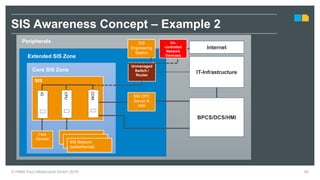
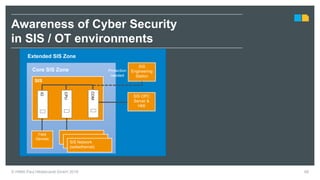
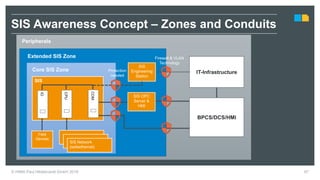
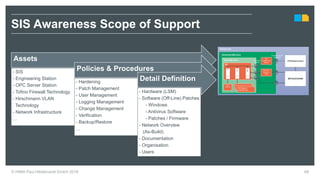
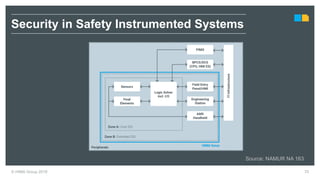
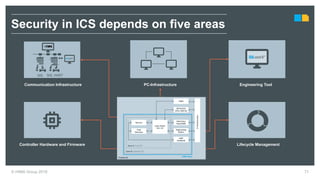
HIMA specializes in safety solutions, contributing to plant safety and operational availability through innovative safety systems and life cycle services. The document highlights the importance of functional safety and cybersecurity in industrial control systems, outlining the need for robust safety measures to mitigate risks associated with cyber threats. It emphasizes the integration of safety and security strategies to ensure the protection of industrial processes and assets.