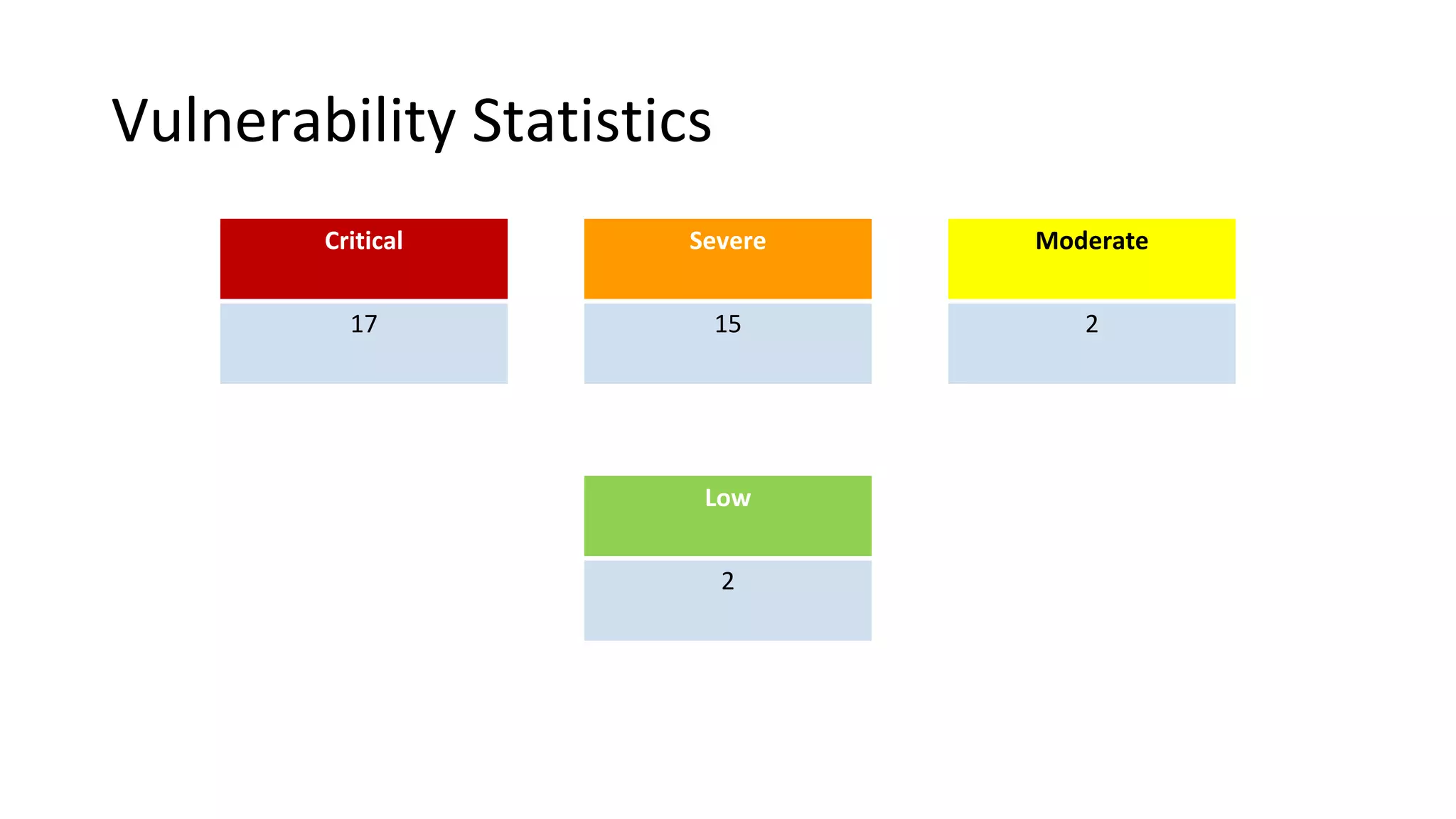
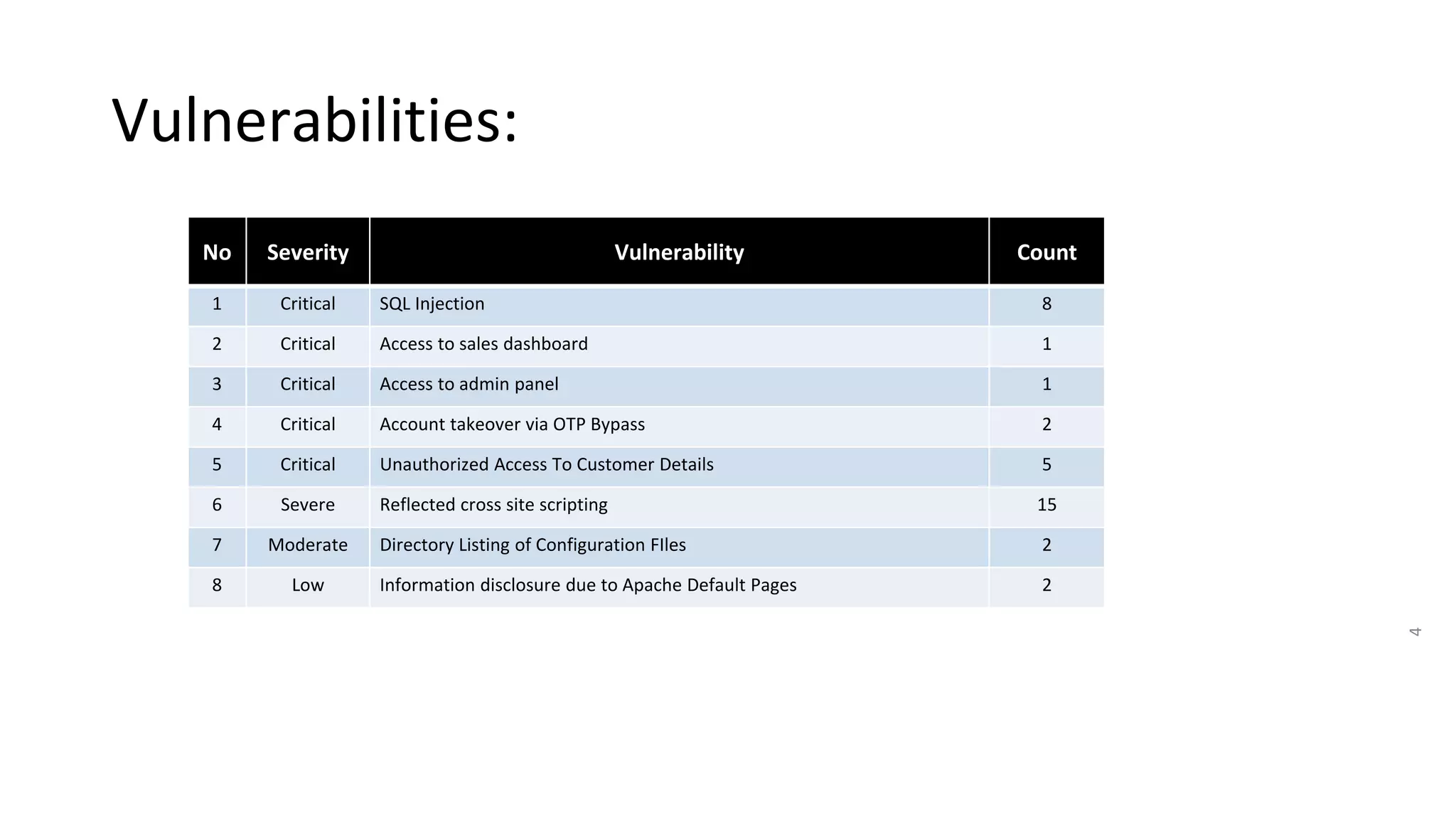
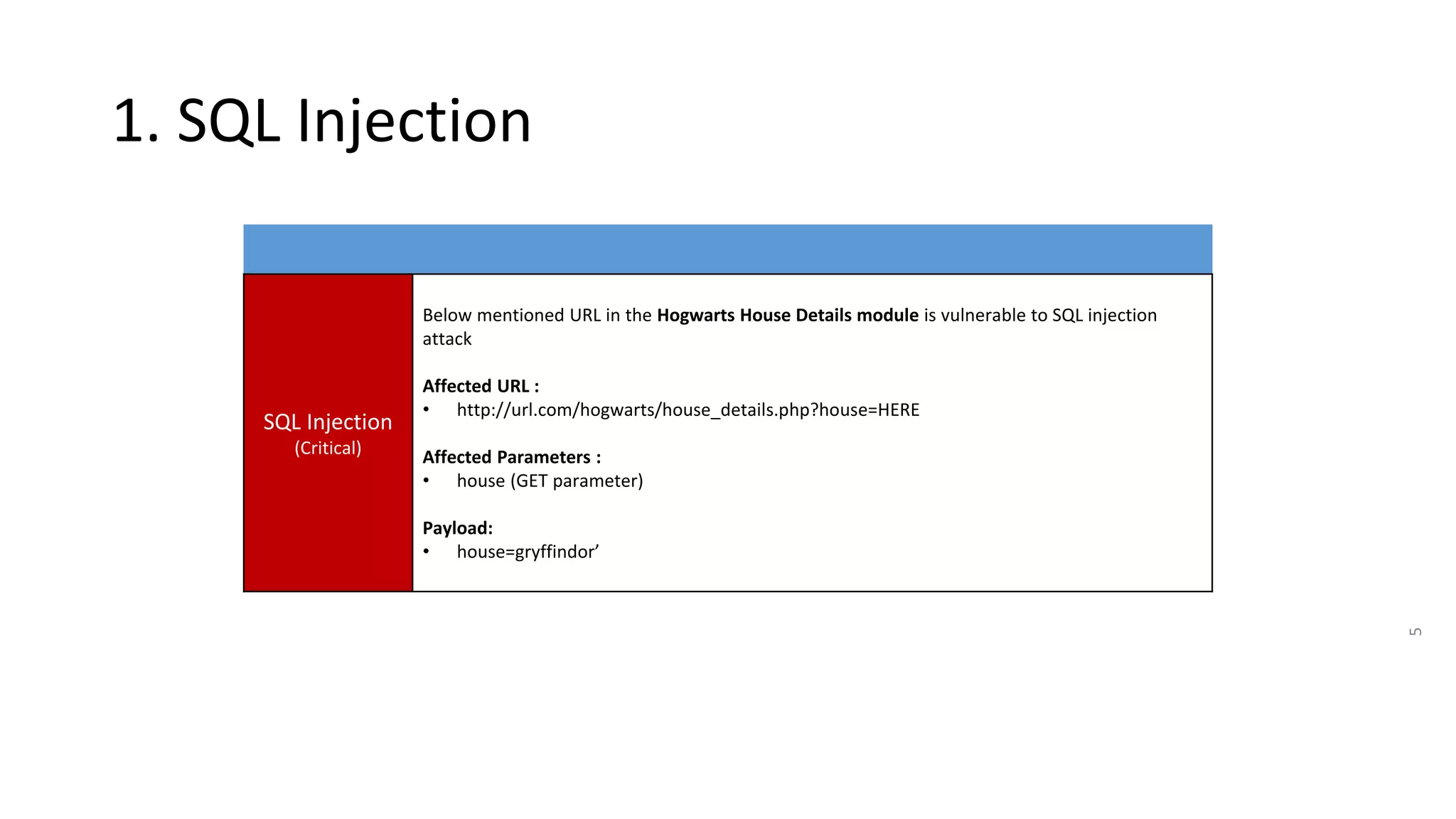
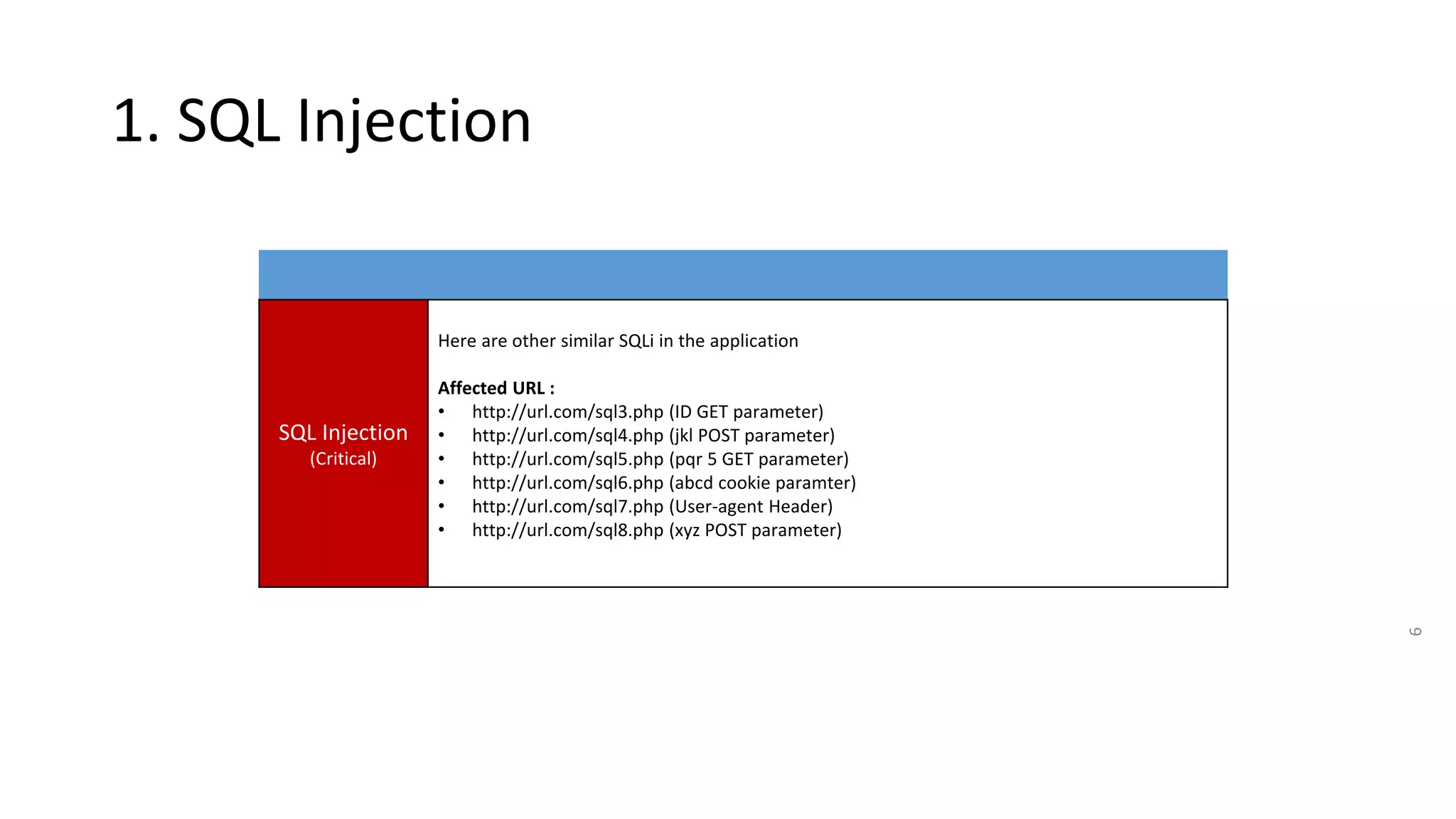
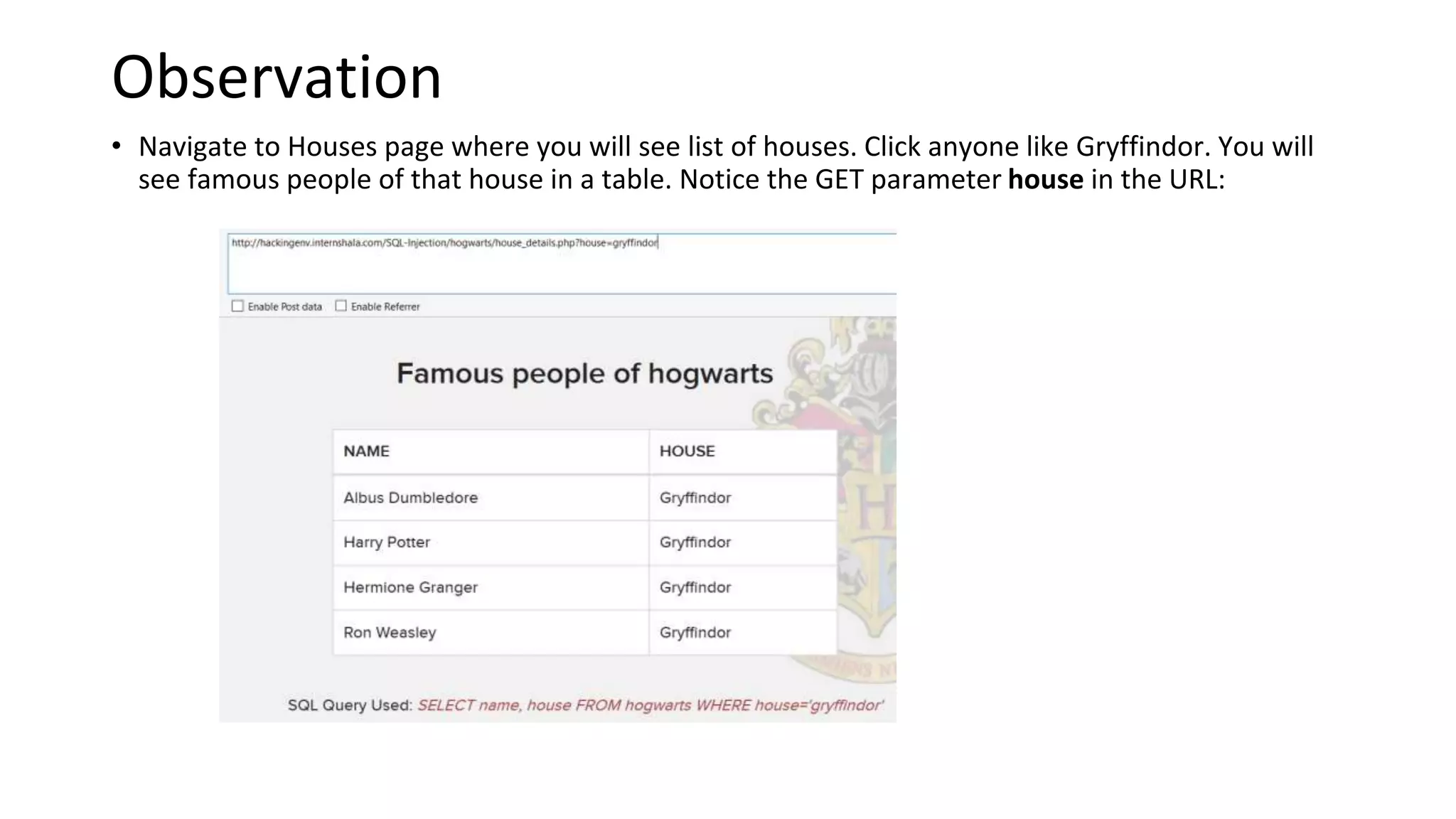
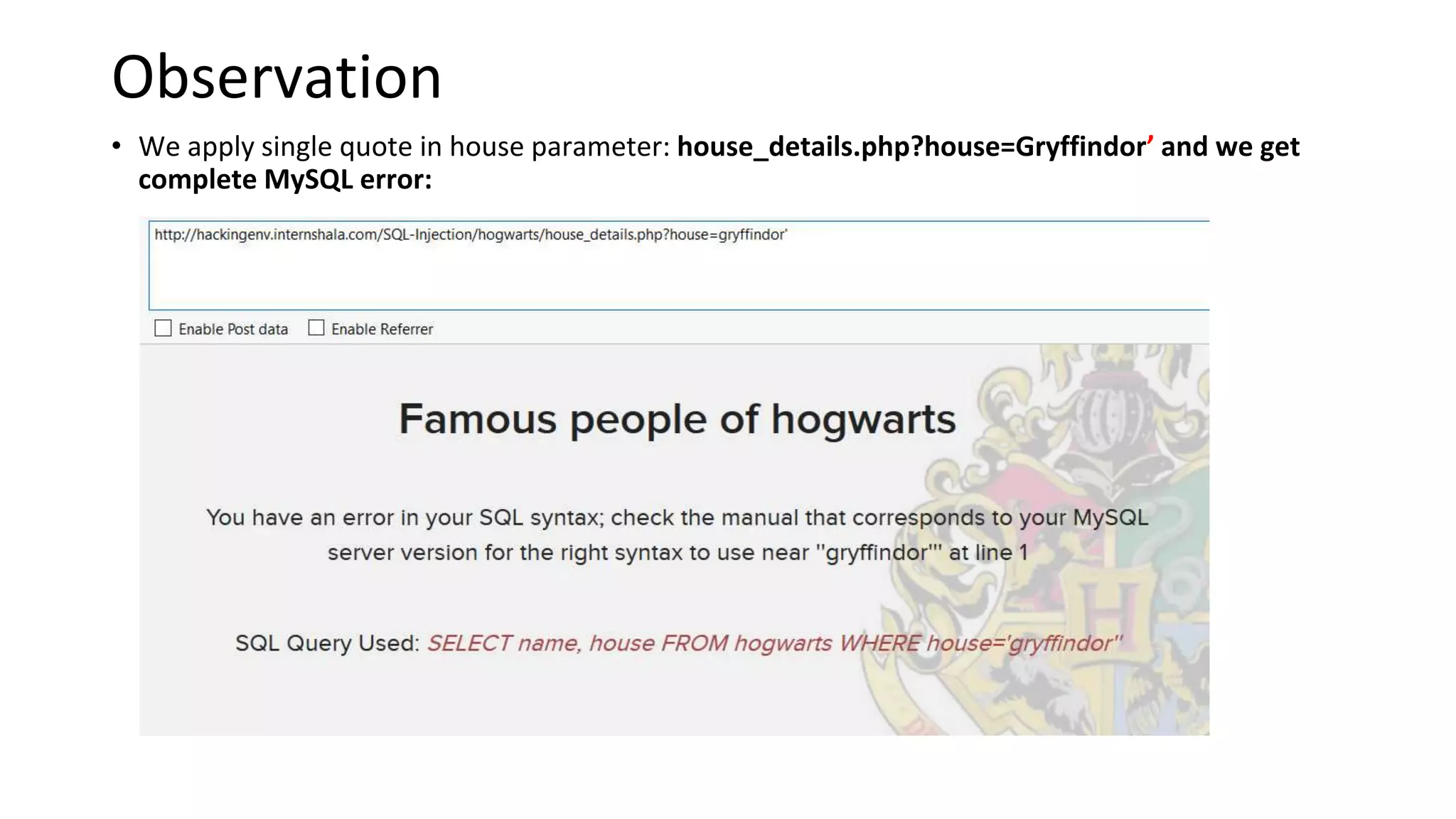
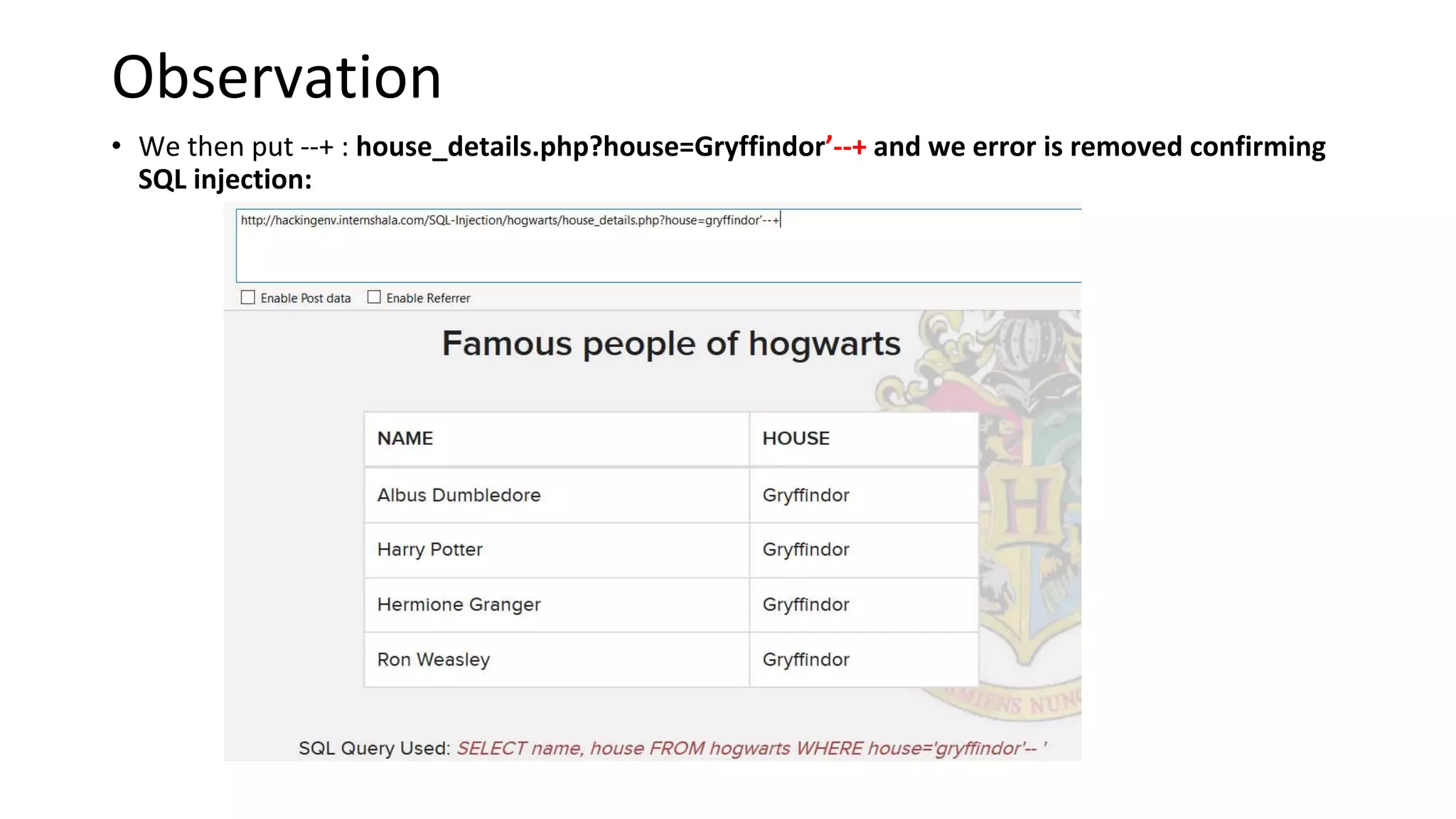
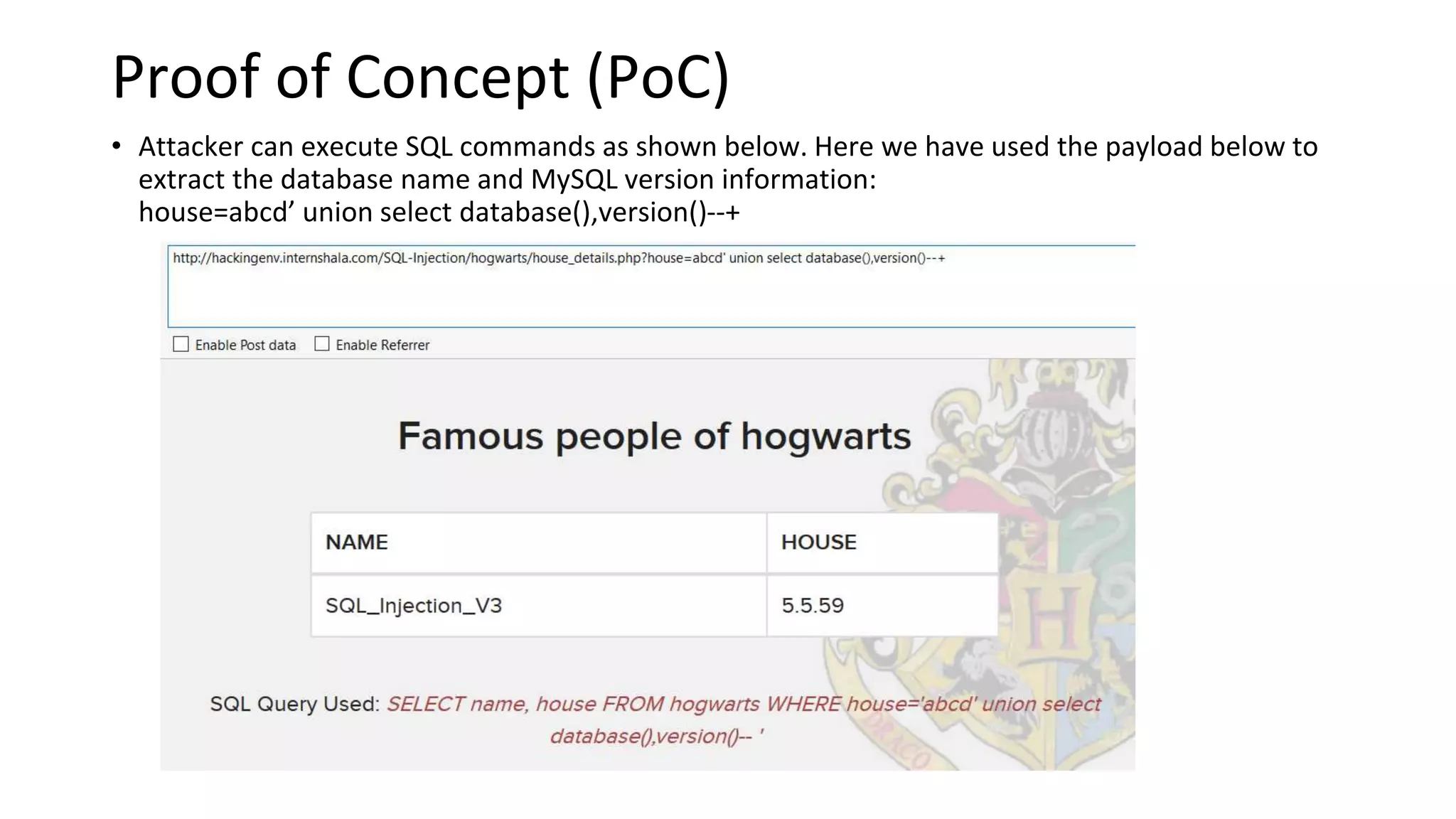
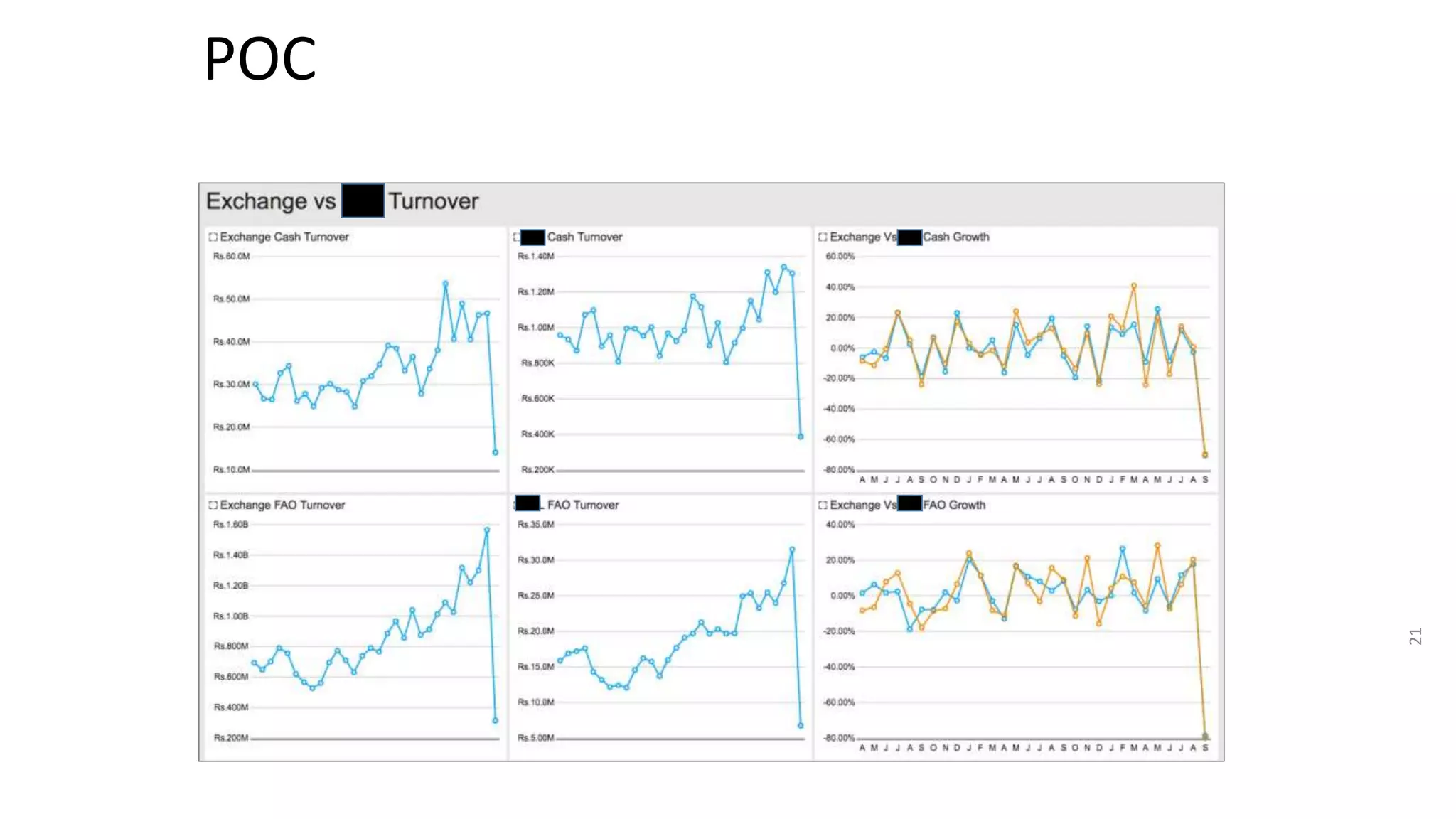
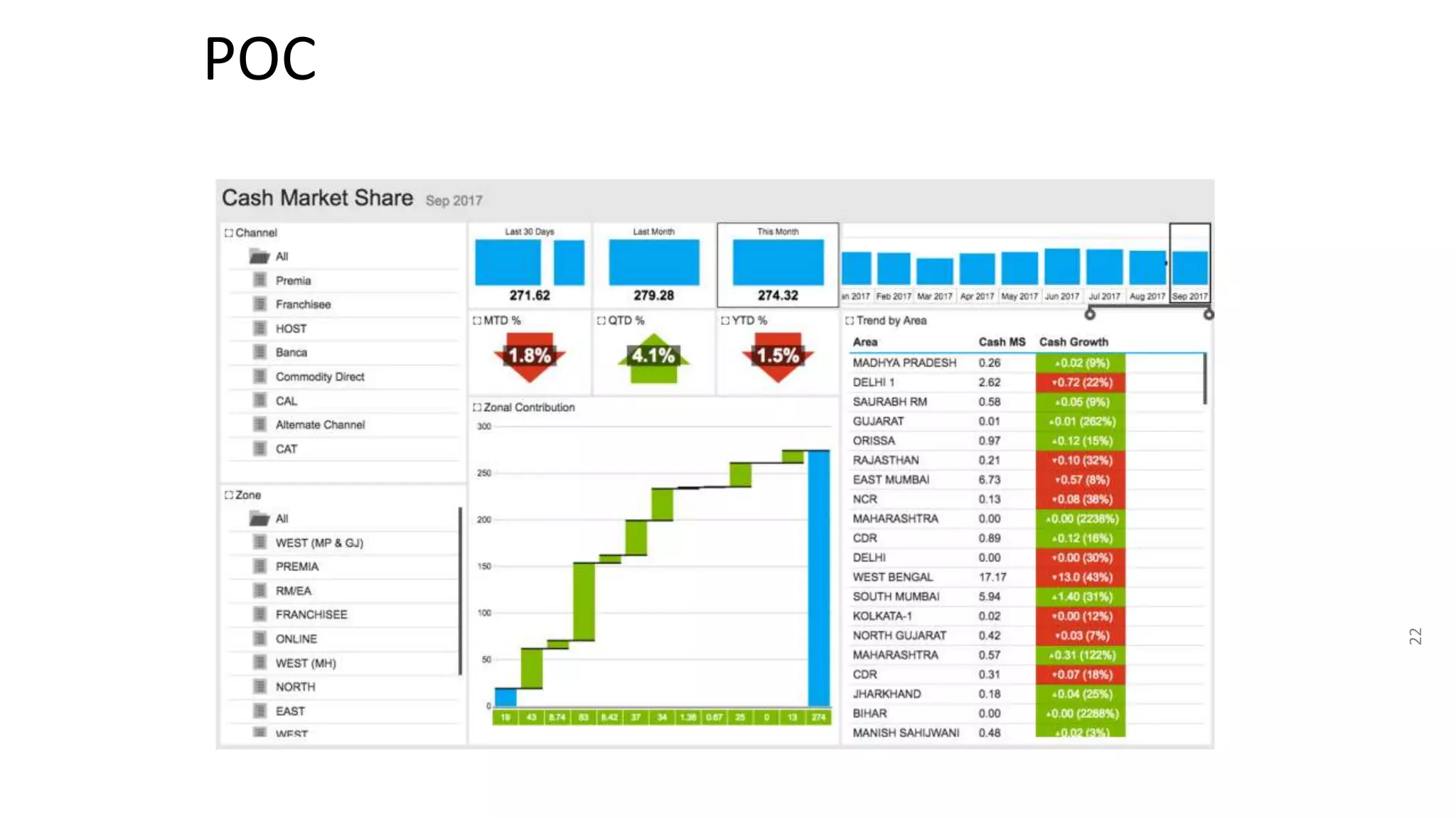
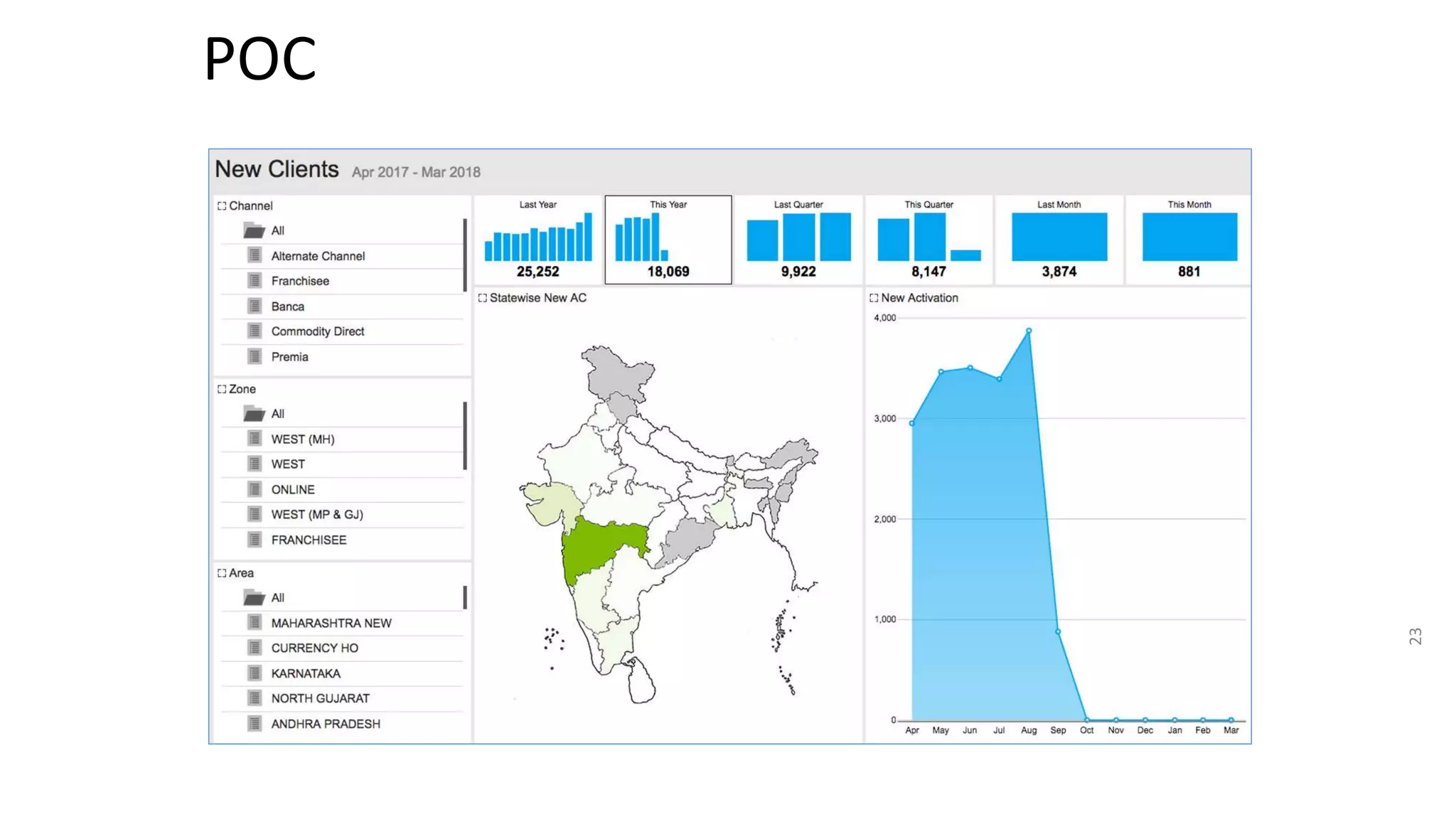
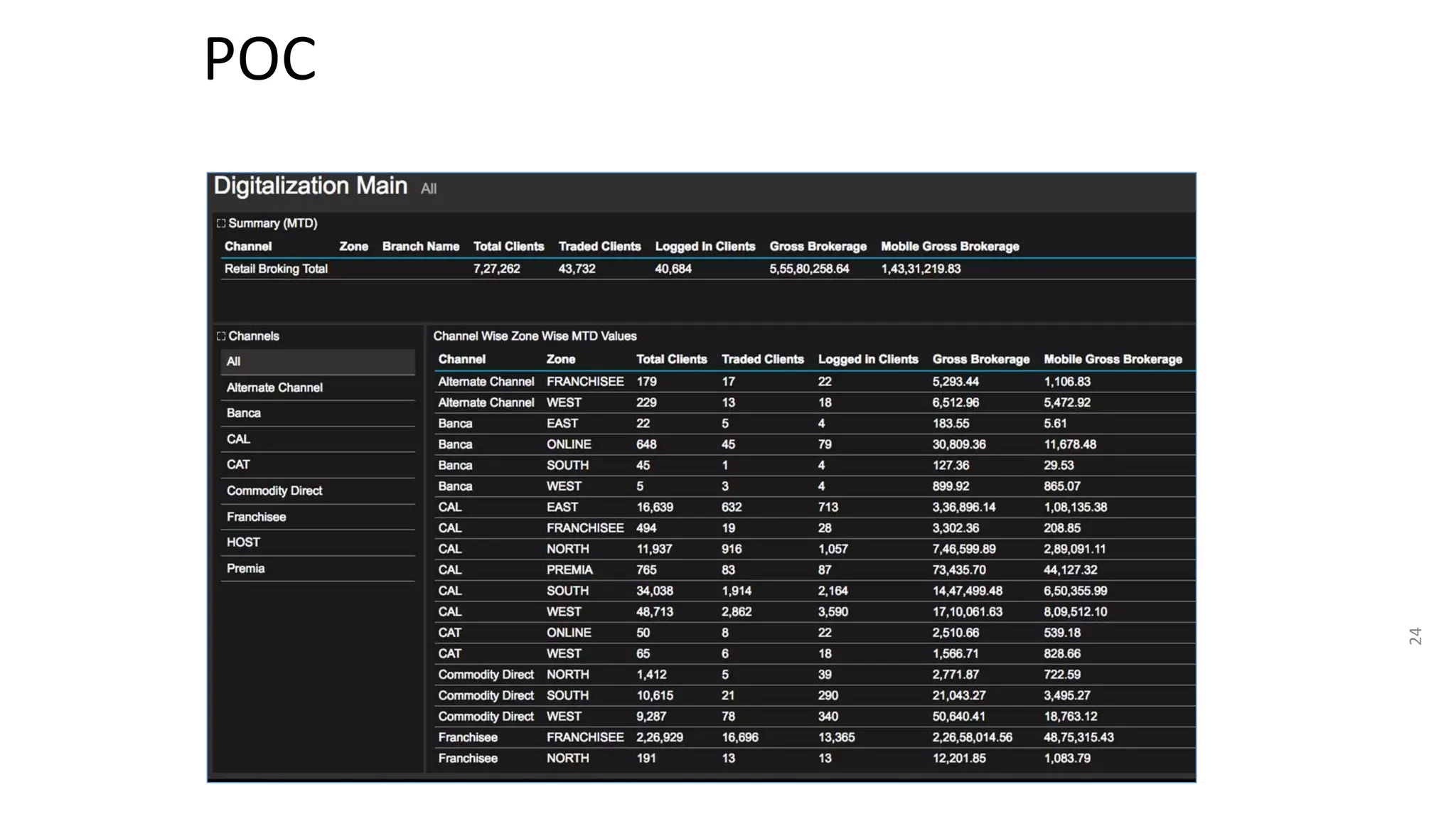
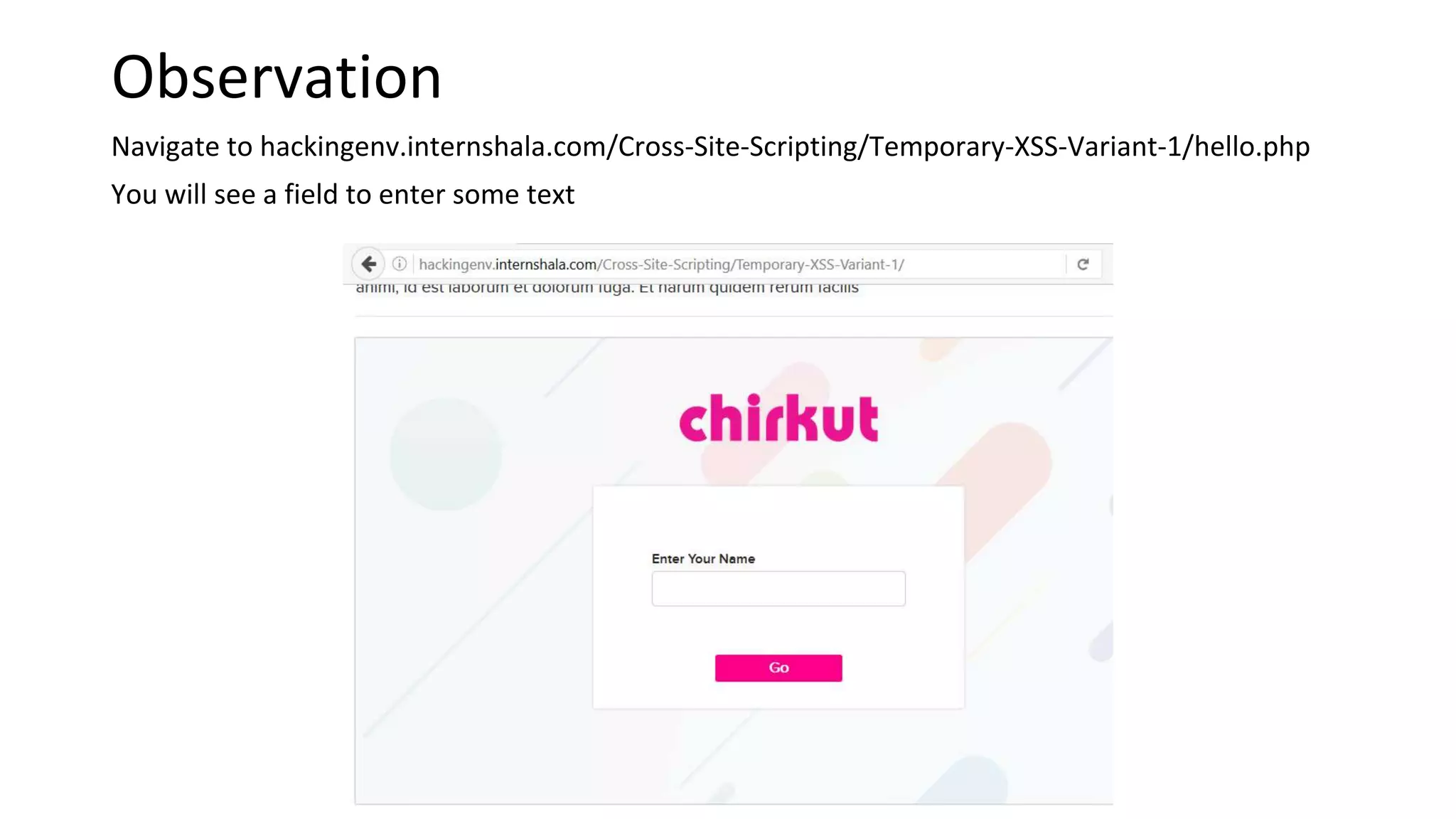
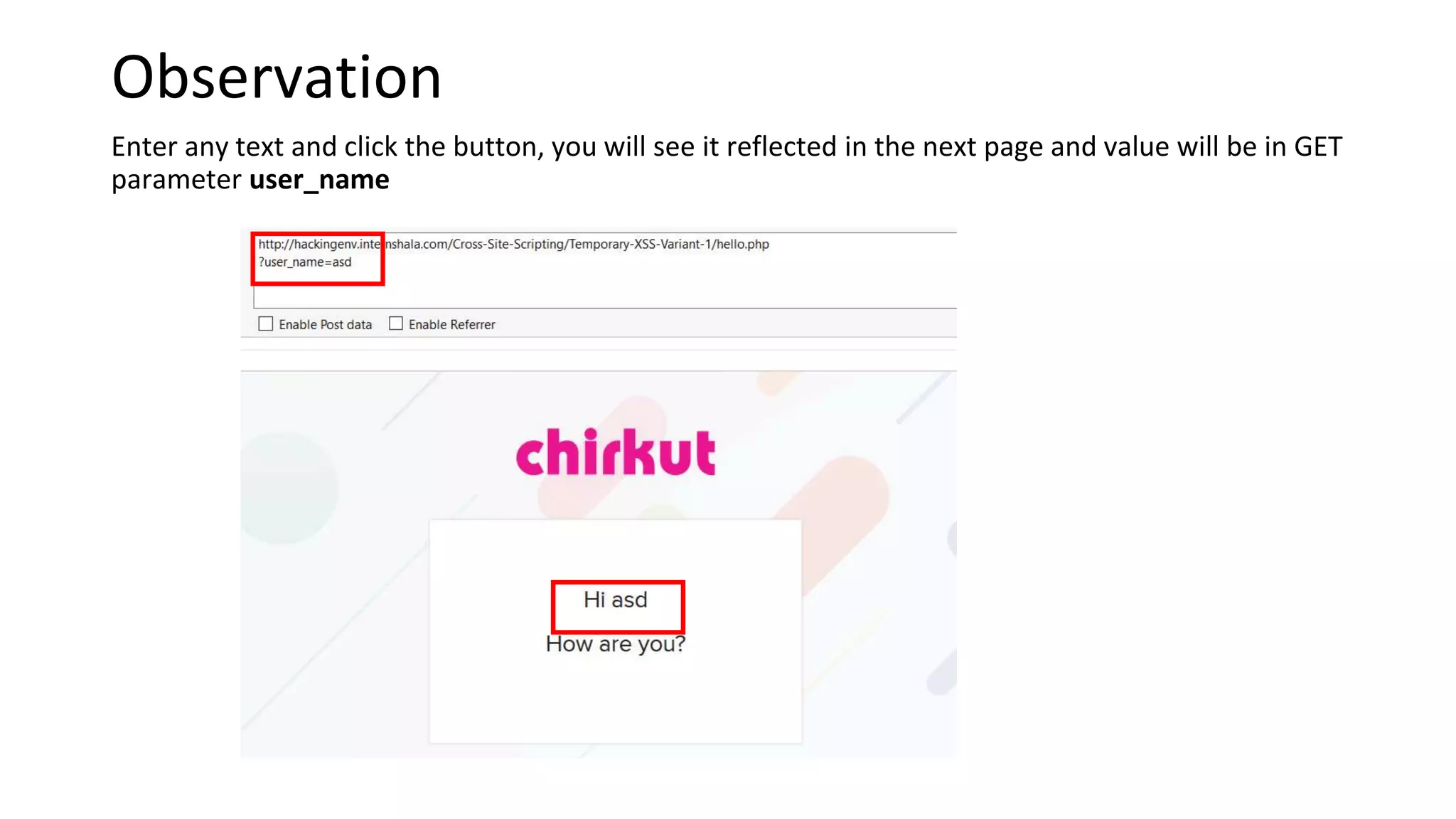
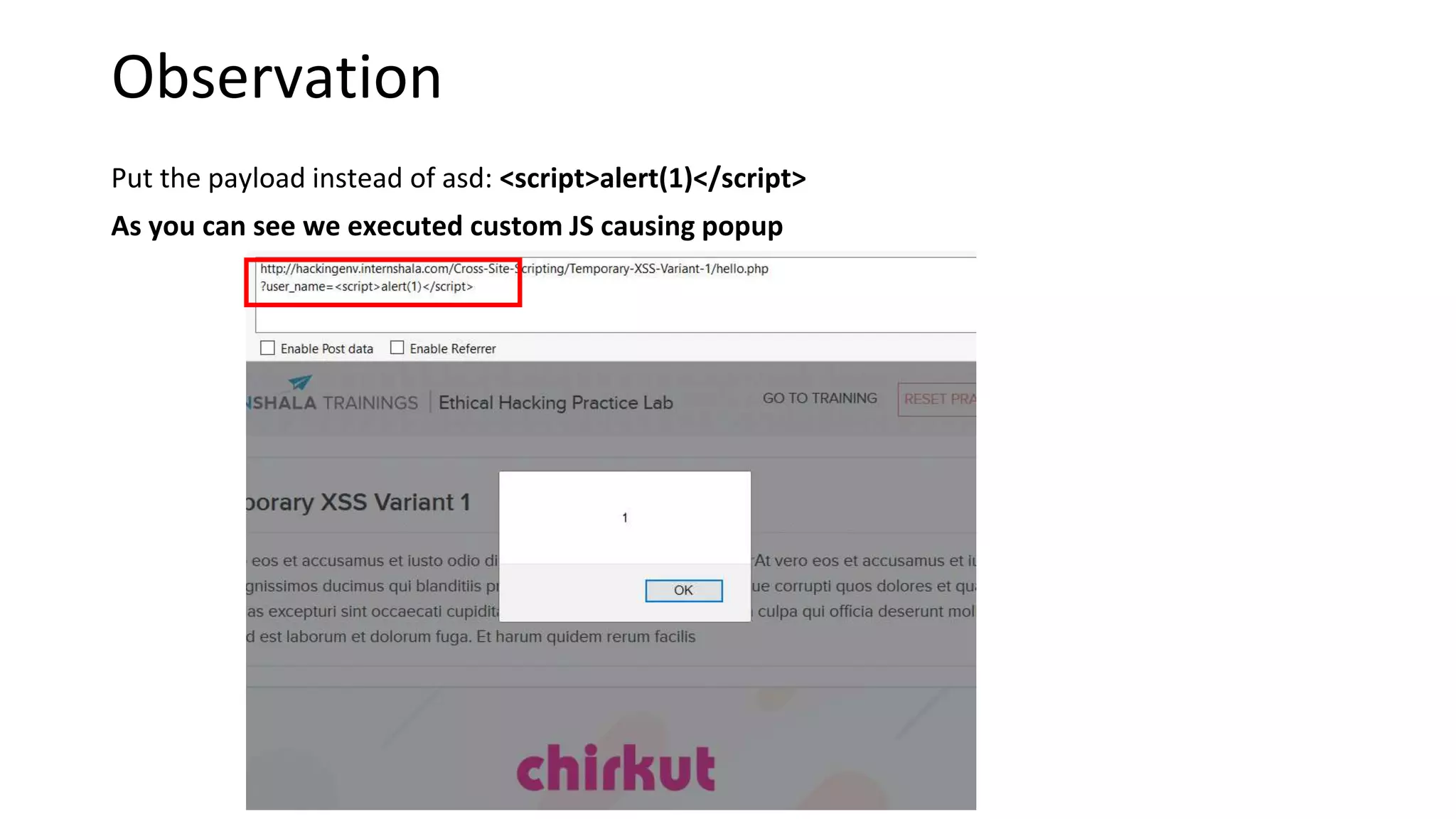
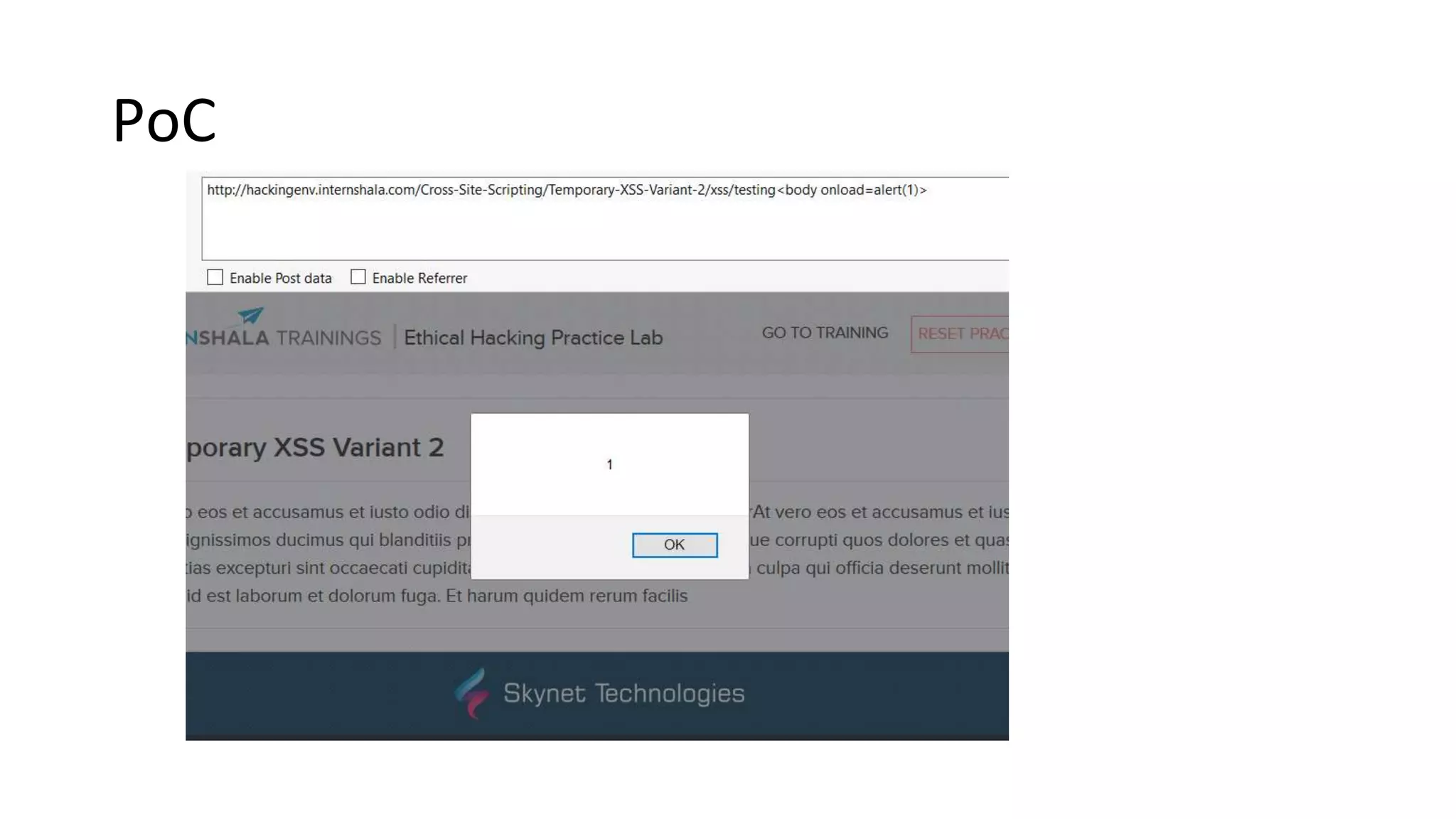
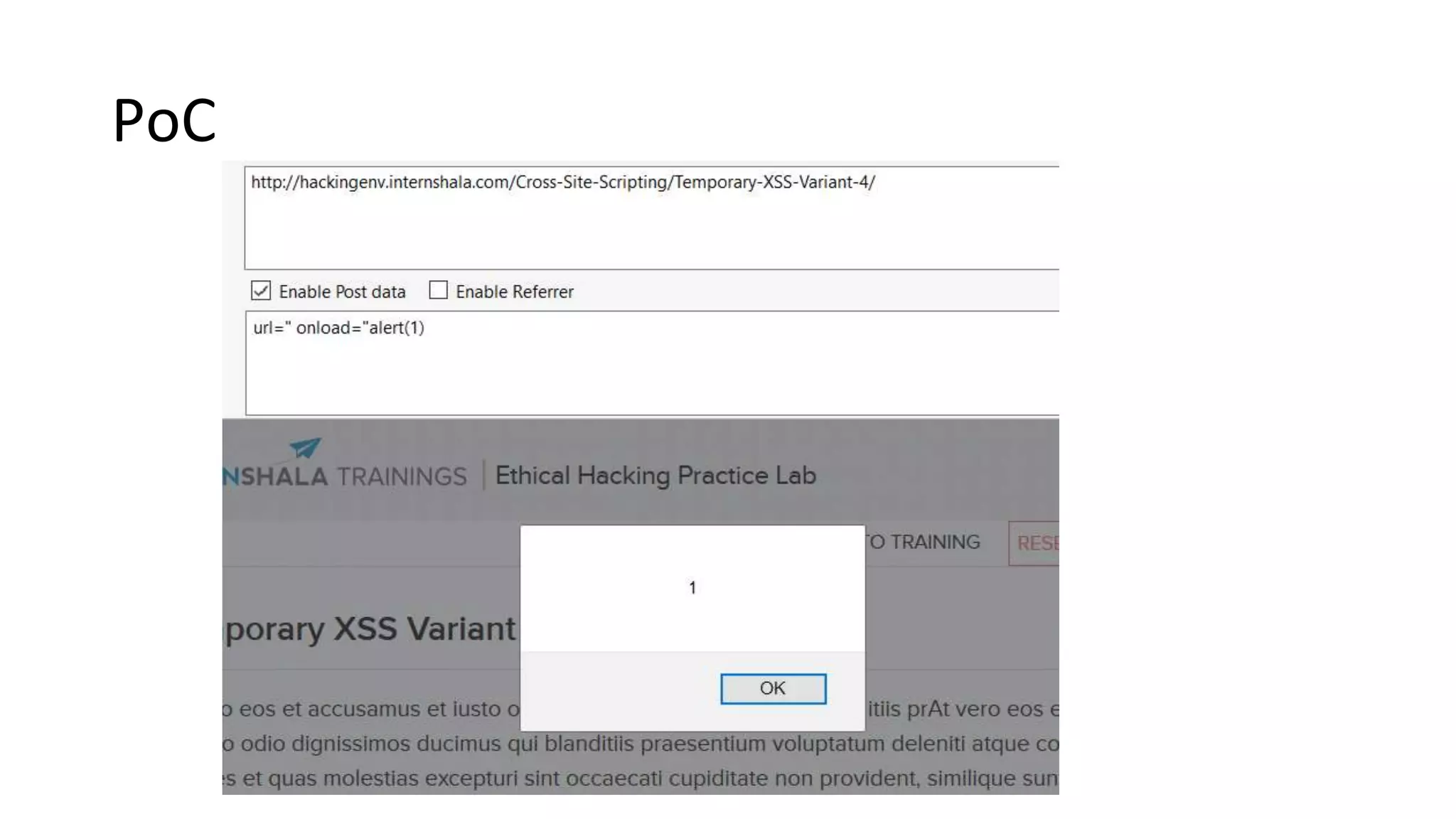
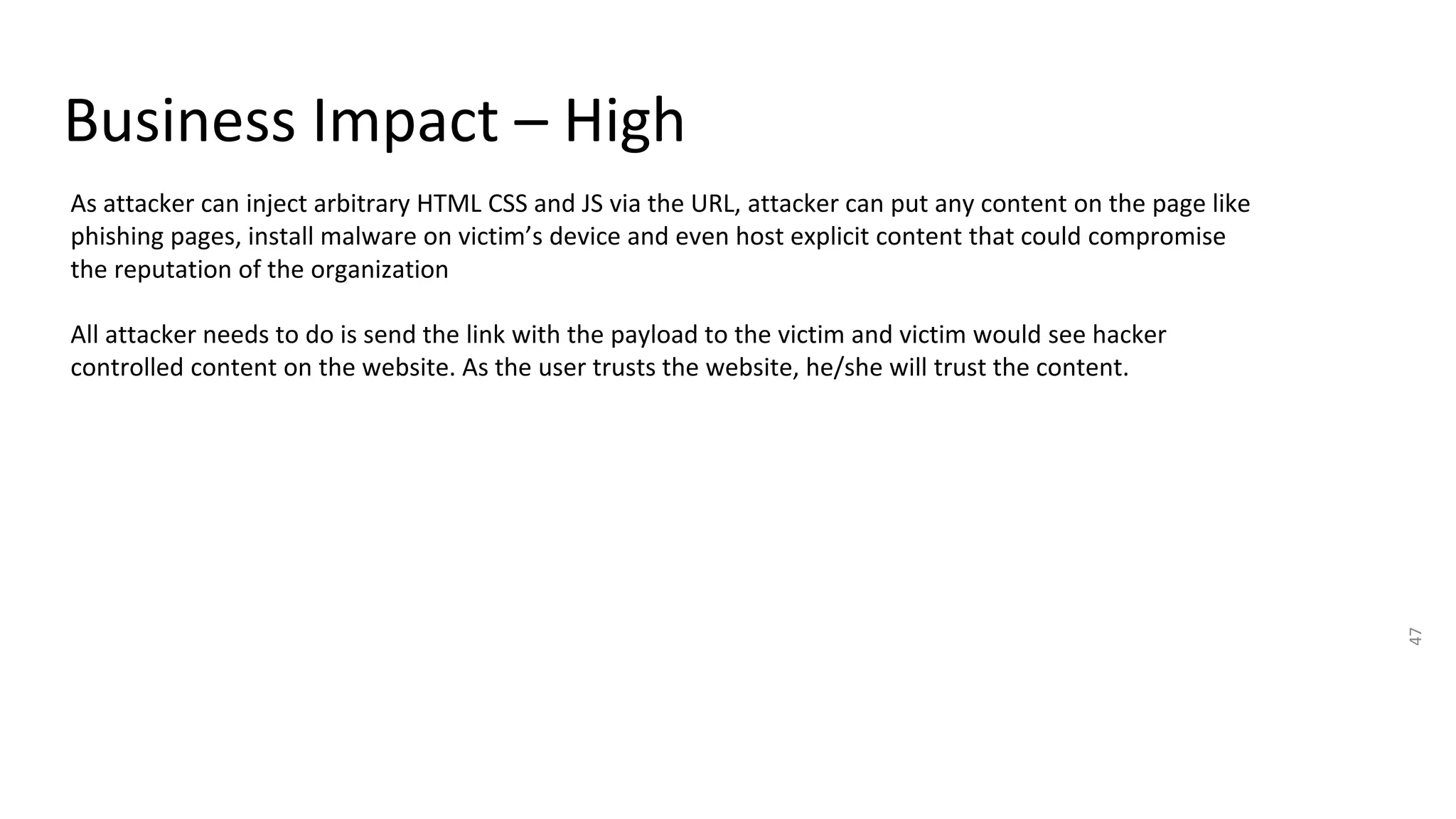
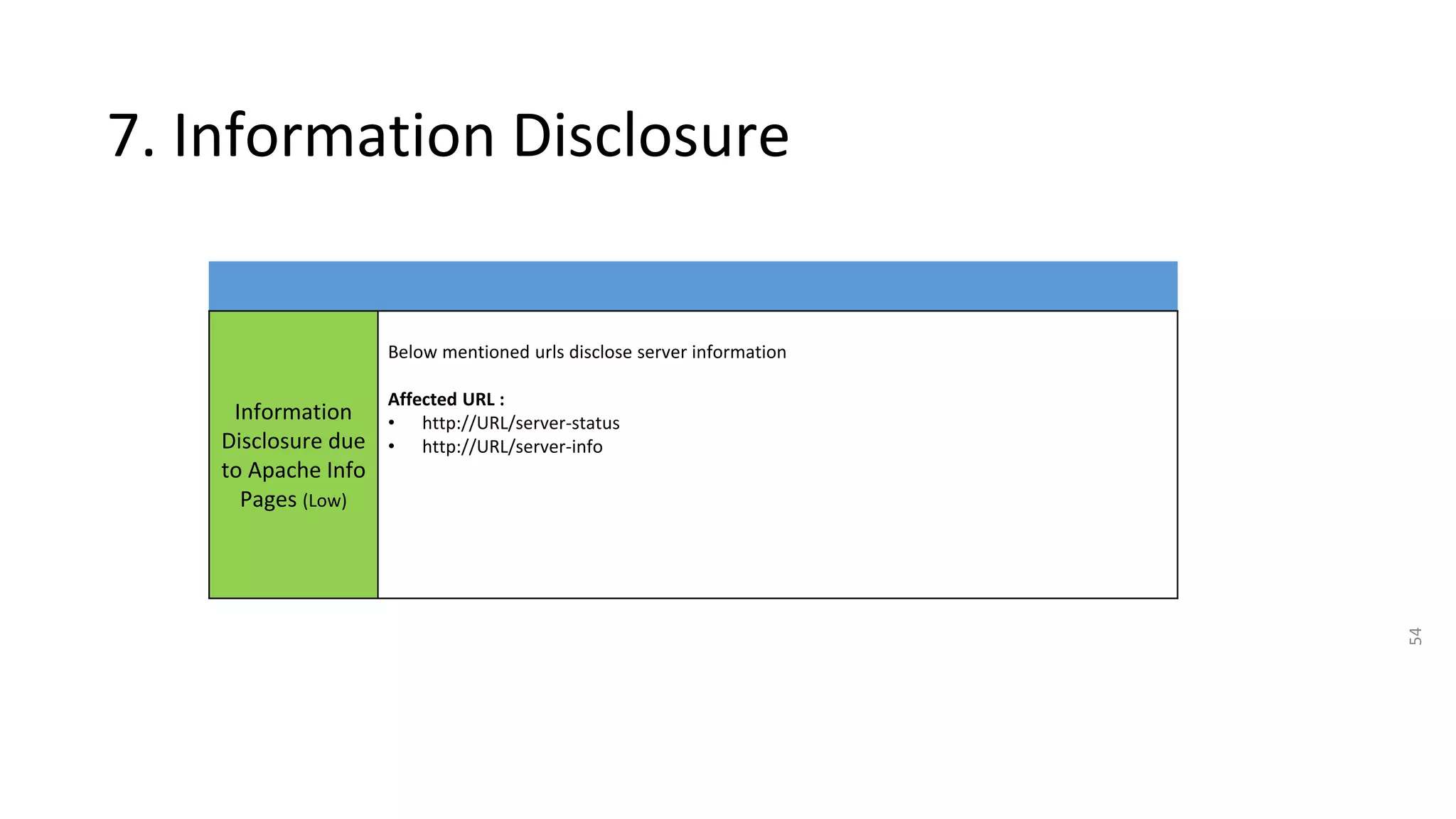
The document summarizes the results of a security assessment of a web application. It finds that:
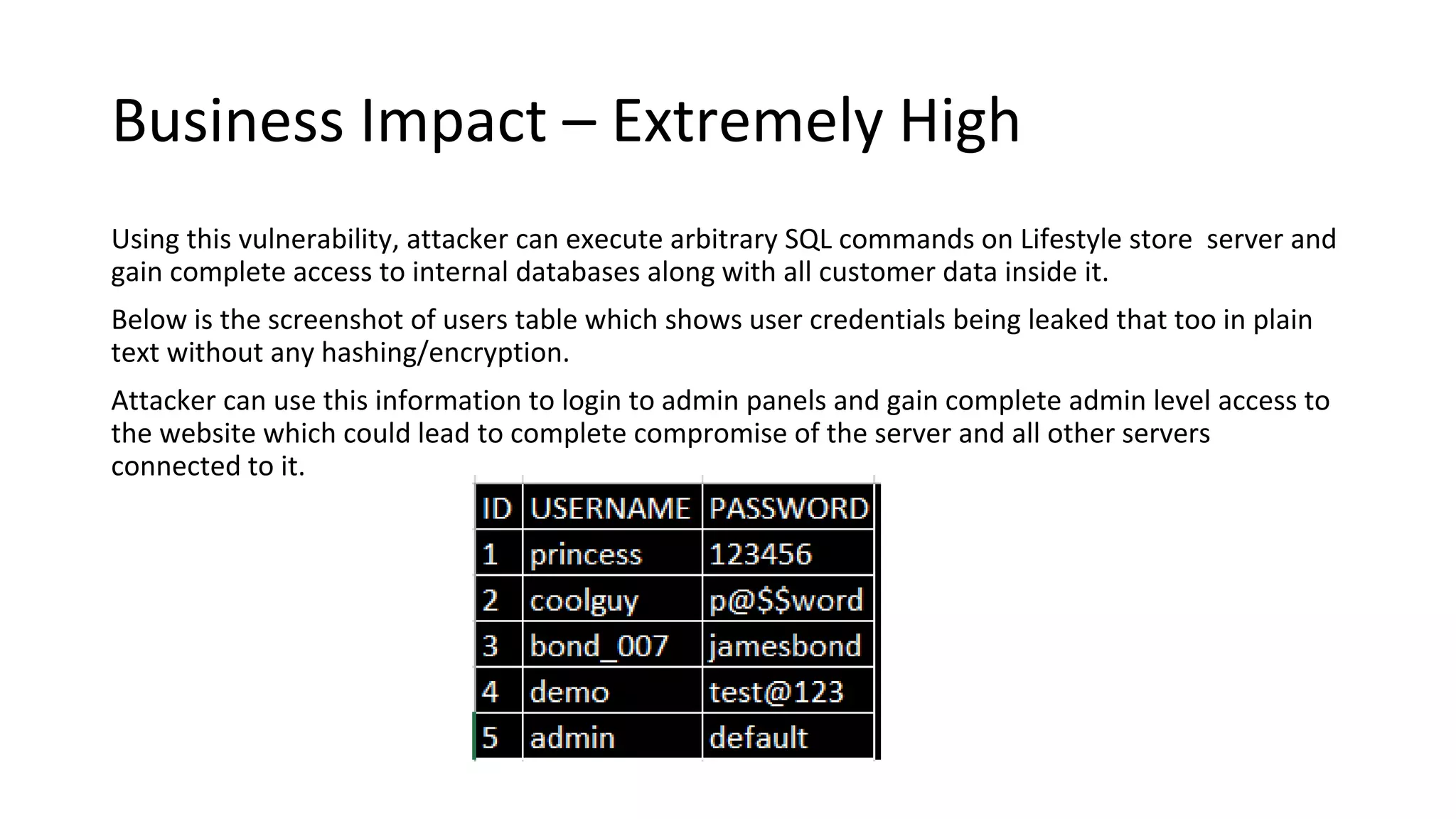
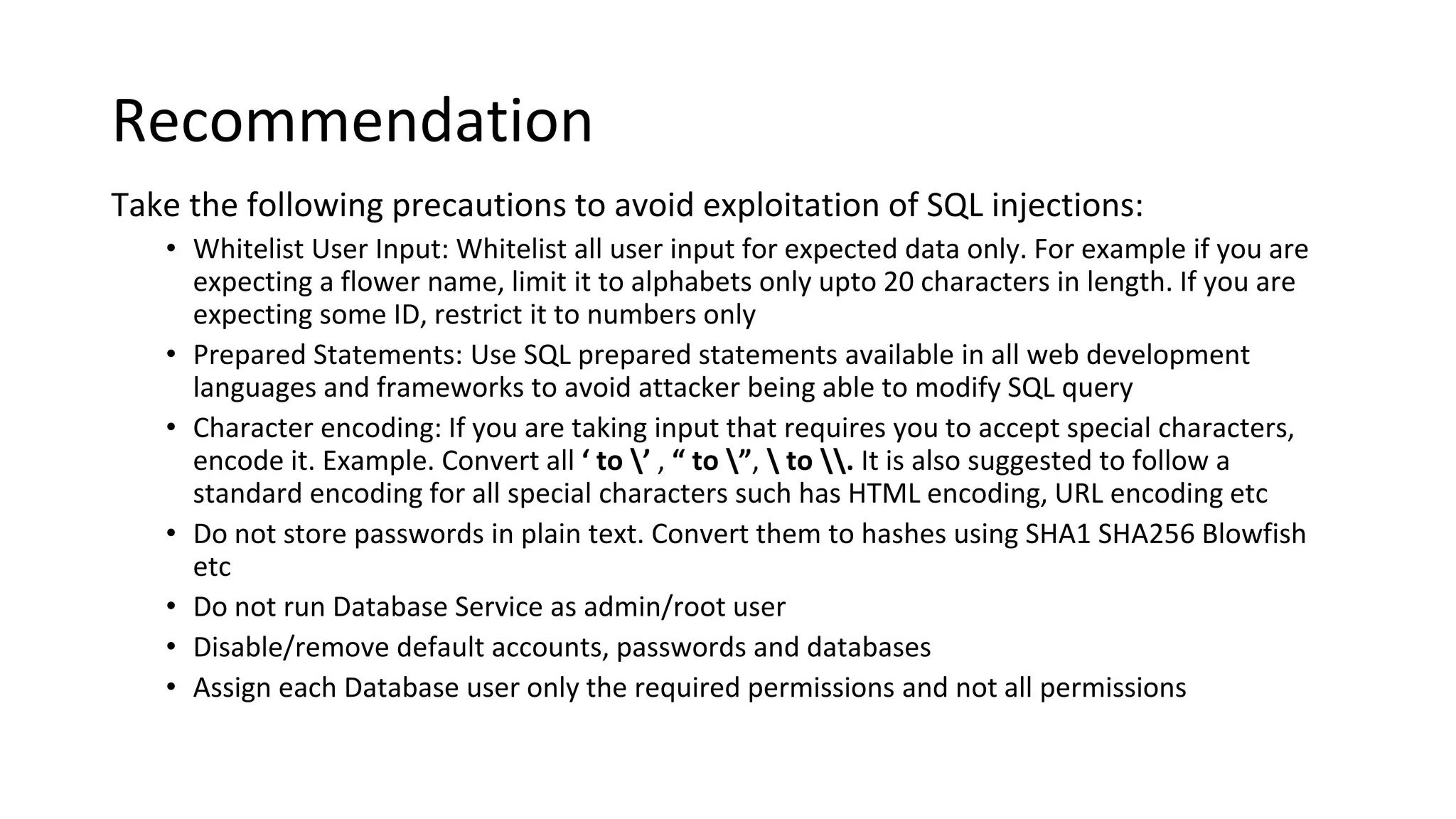
1. The application is extremely vulnerable due to SQL injection flaws that allow attackers to steal all database records and take control of the server.
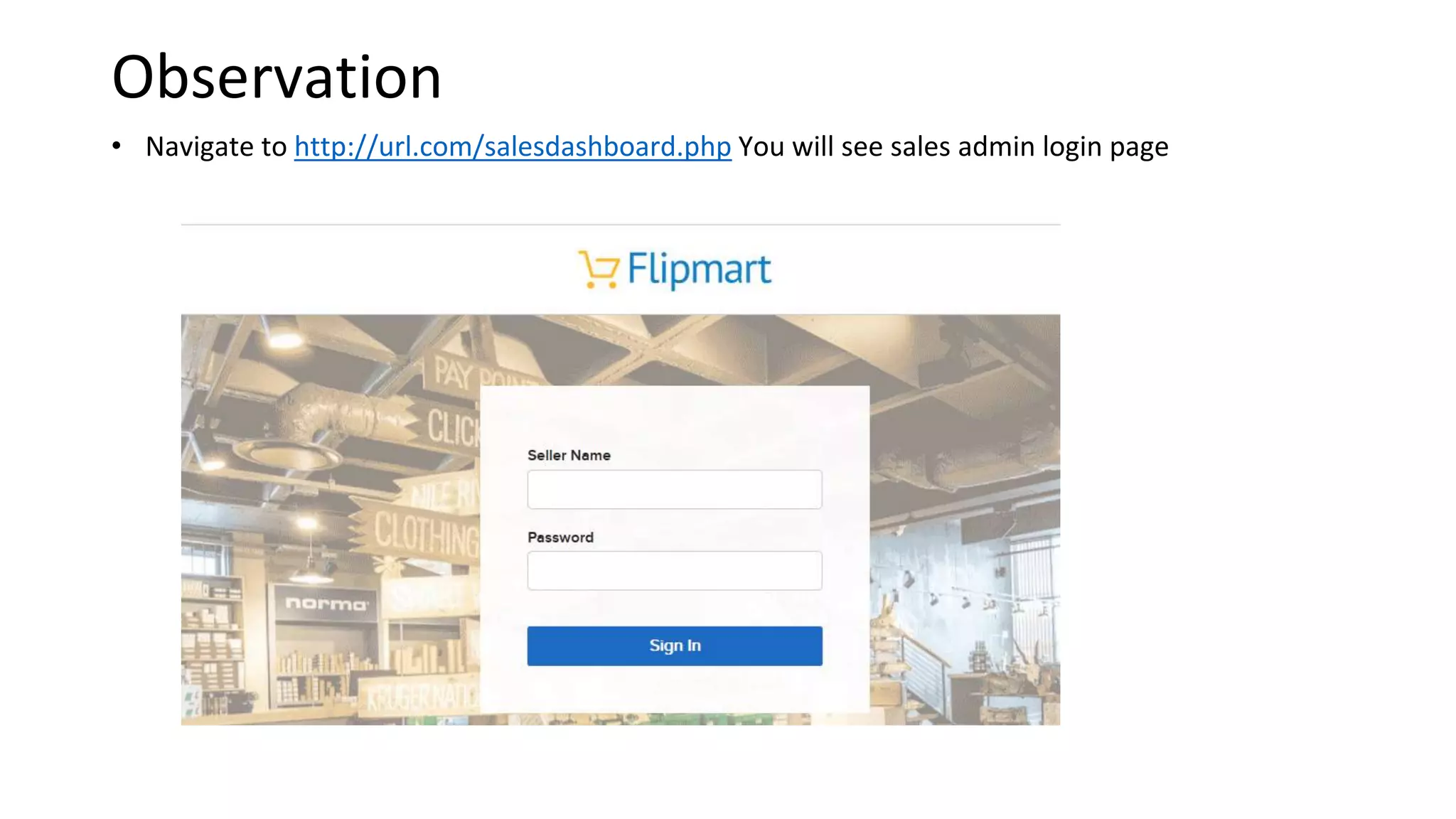
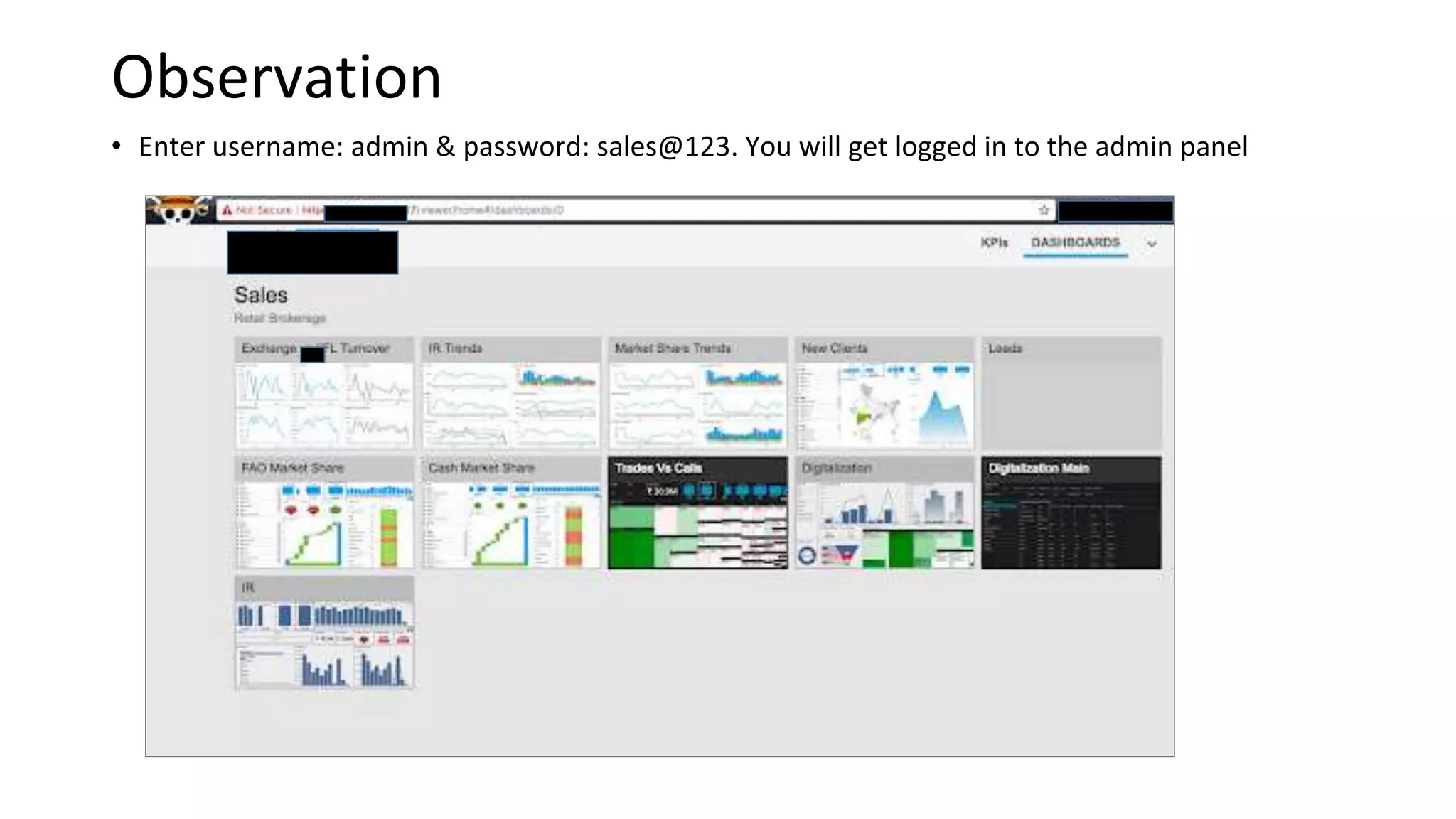
2. Weak and default passwords provide access to critical areas like sales dashboards and admin panels.
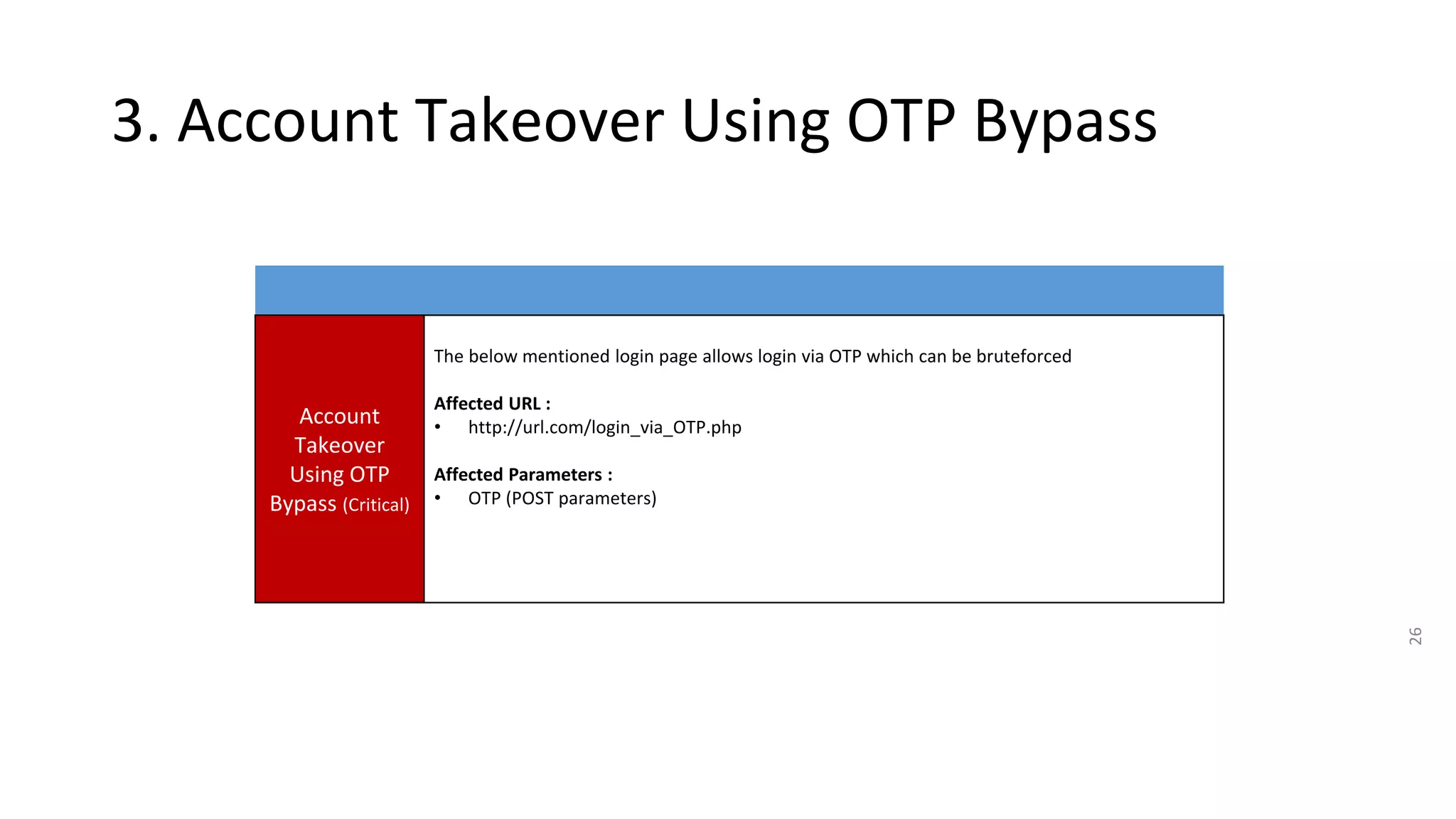
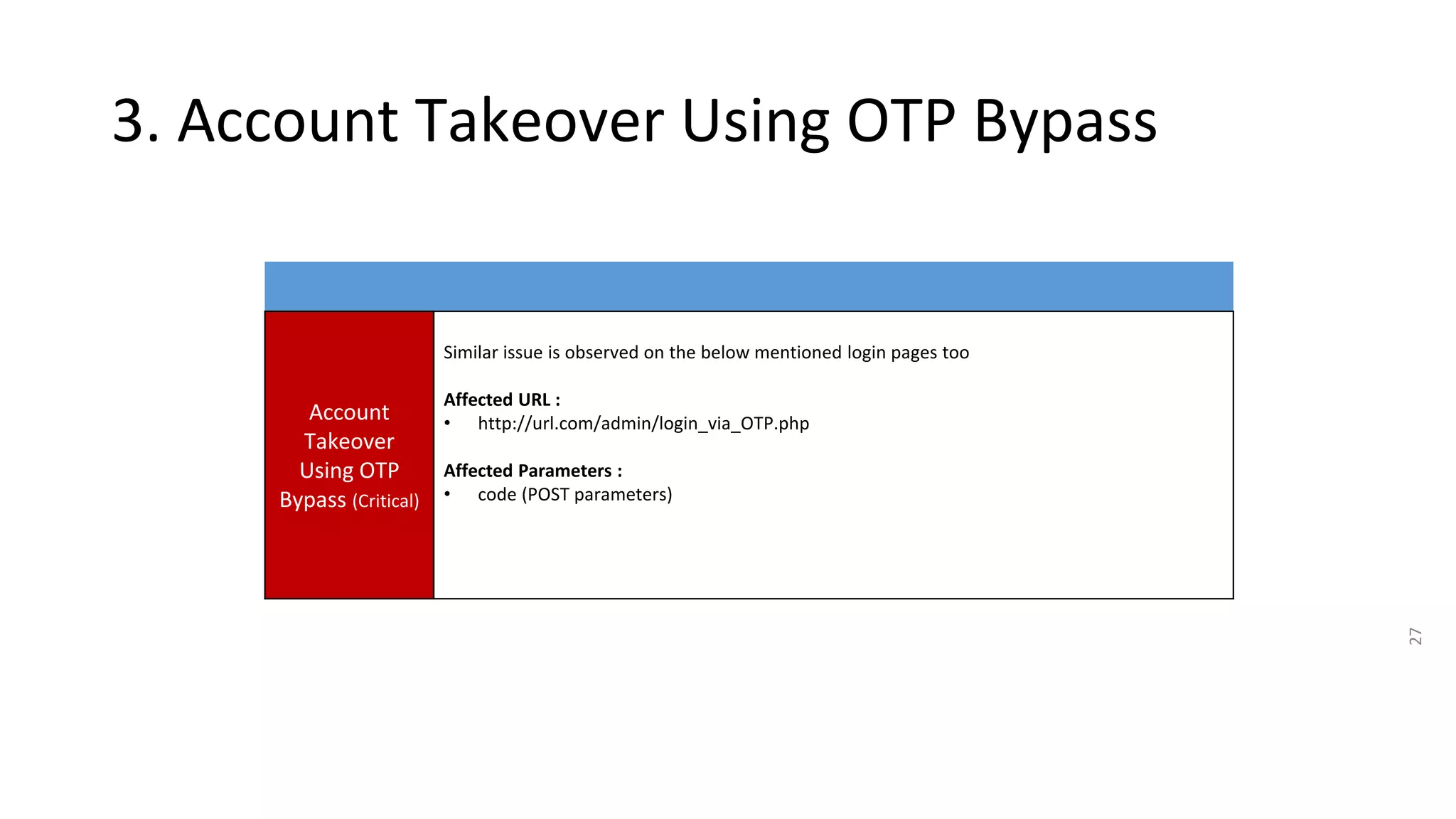
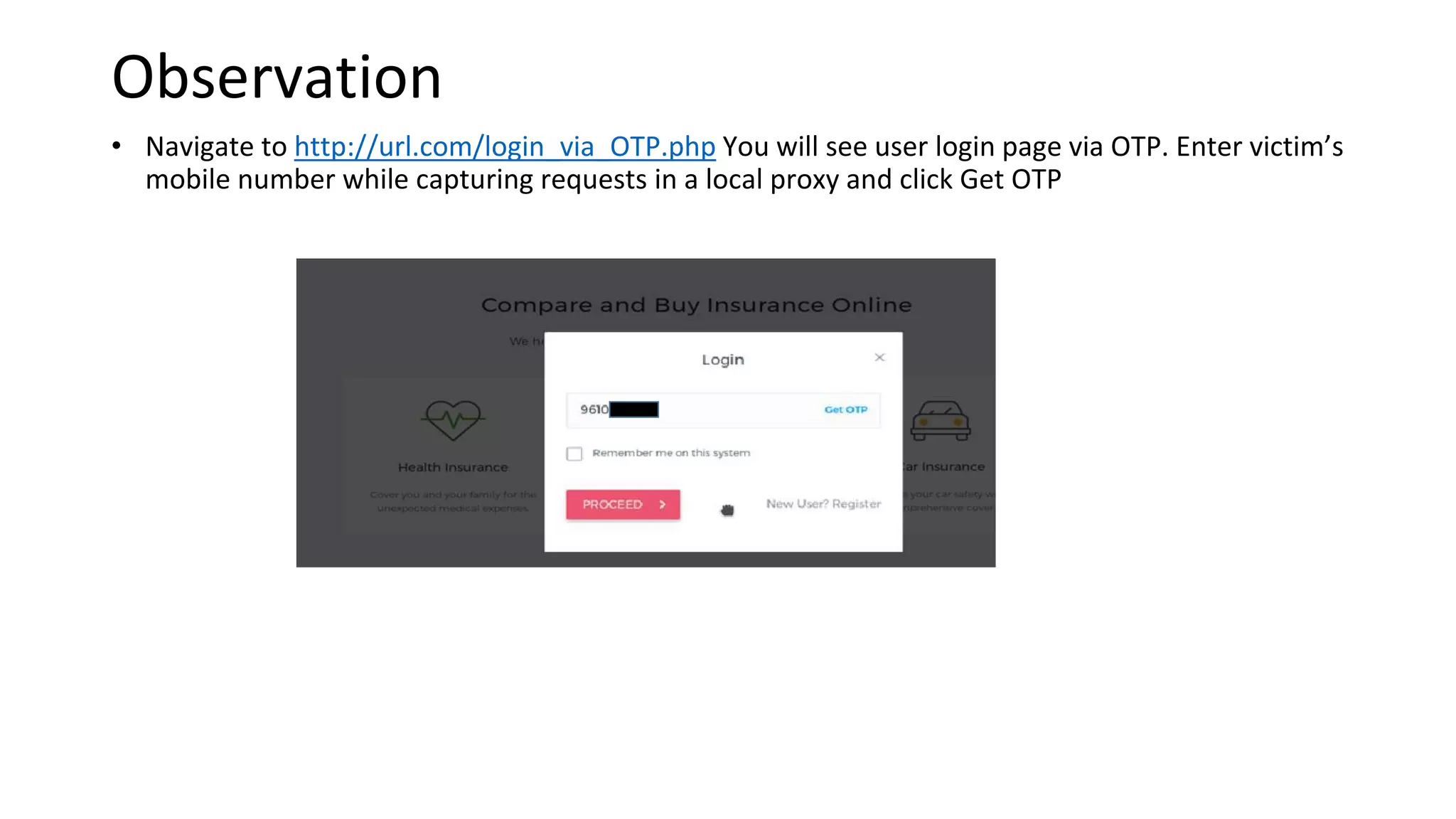
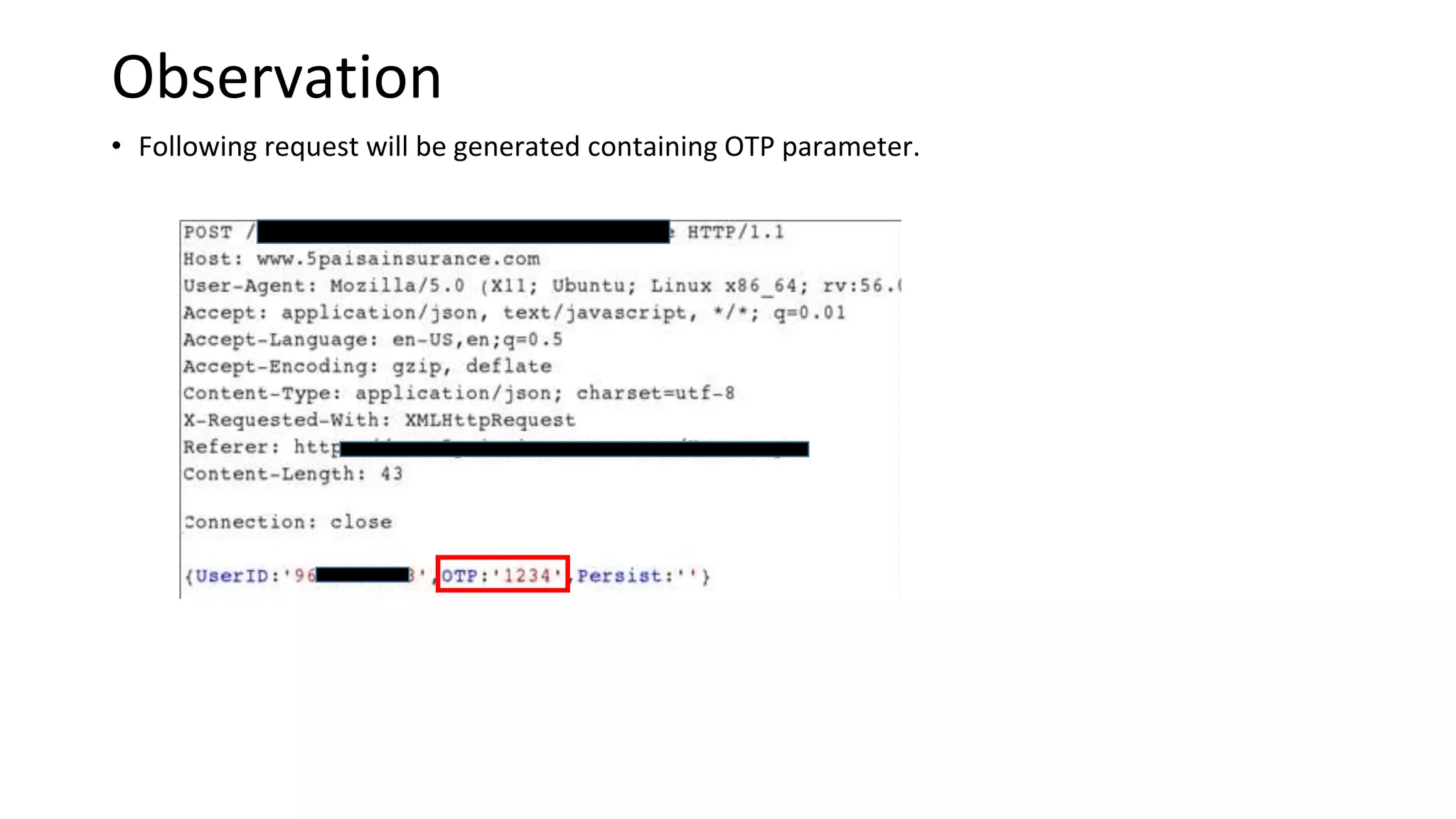
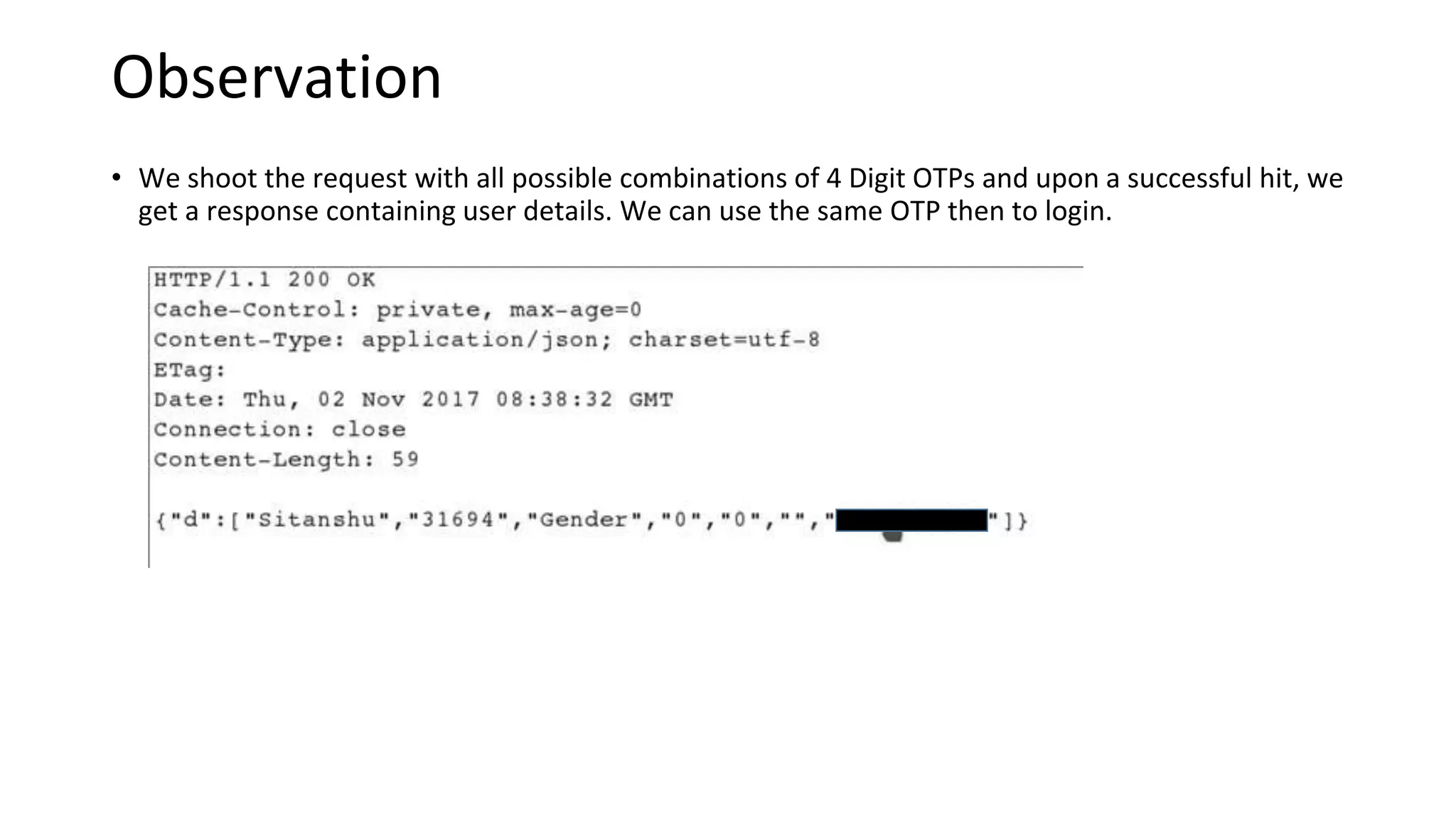
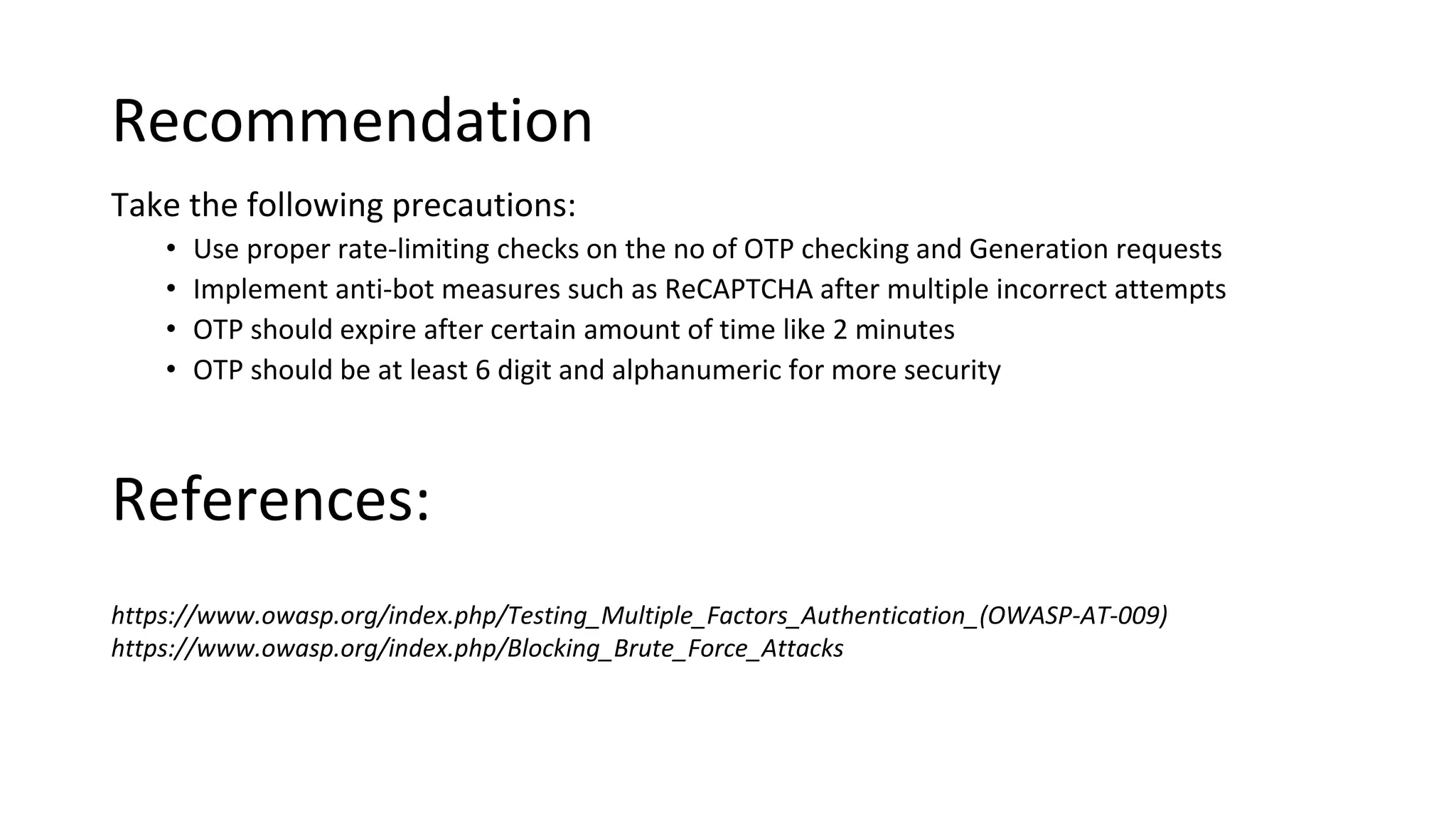
3. OTP bypass flaws allow account takeover by bruteforcing OTP codes.
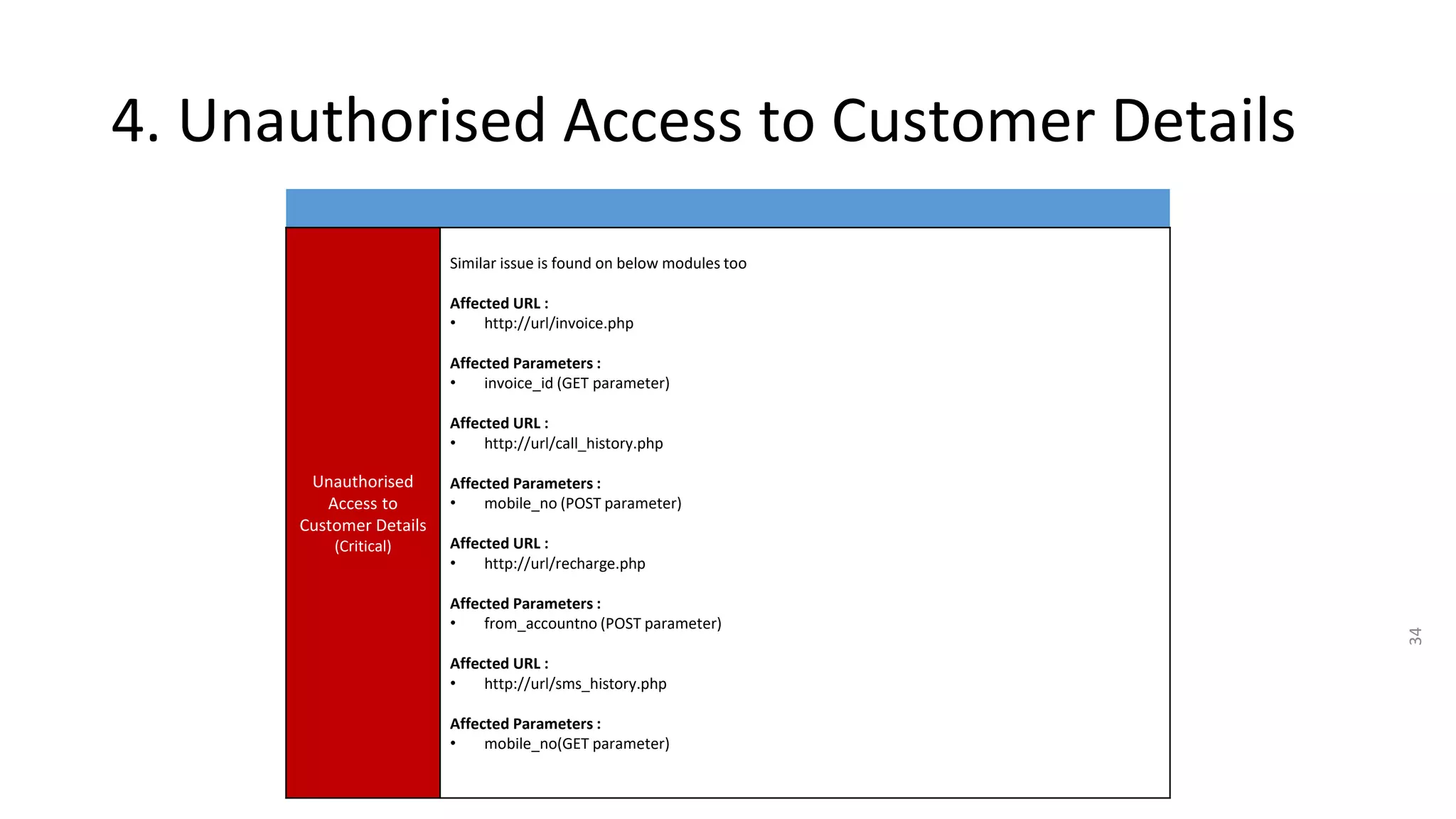
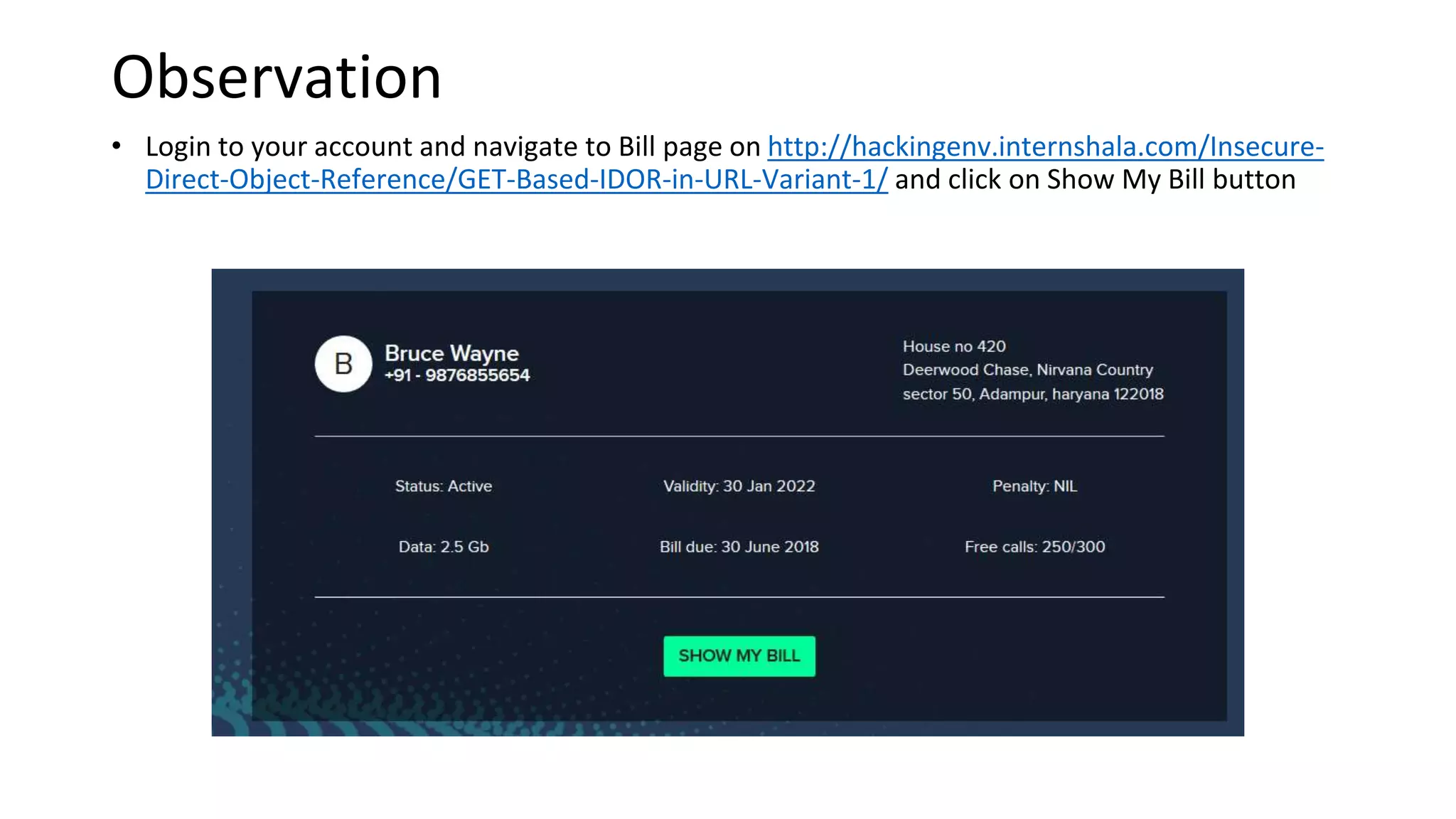
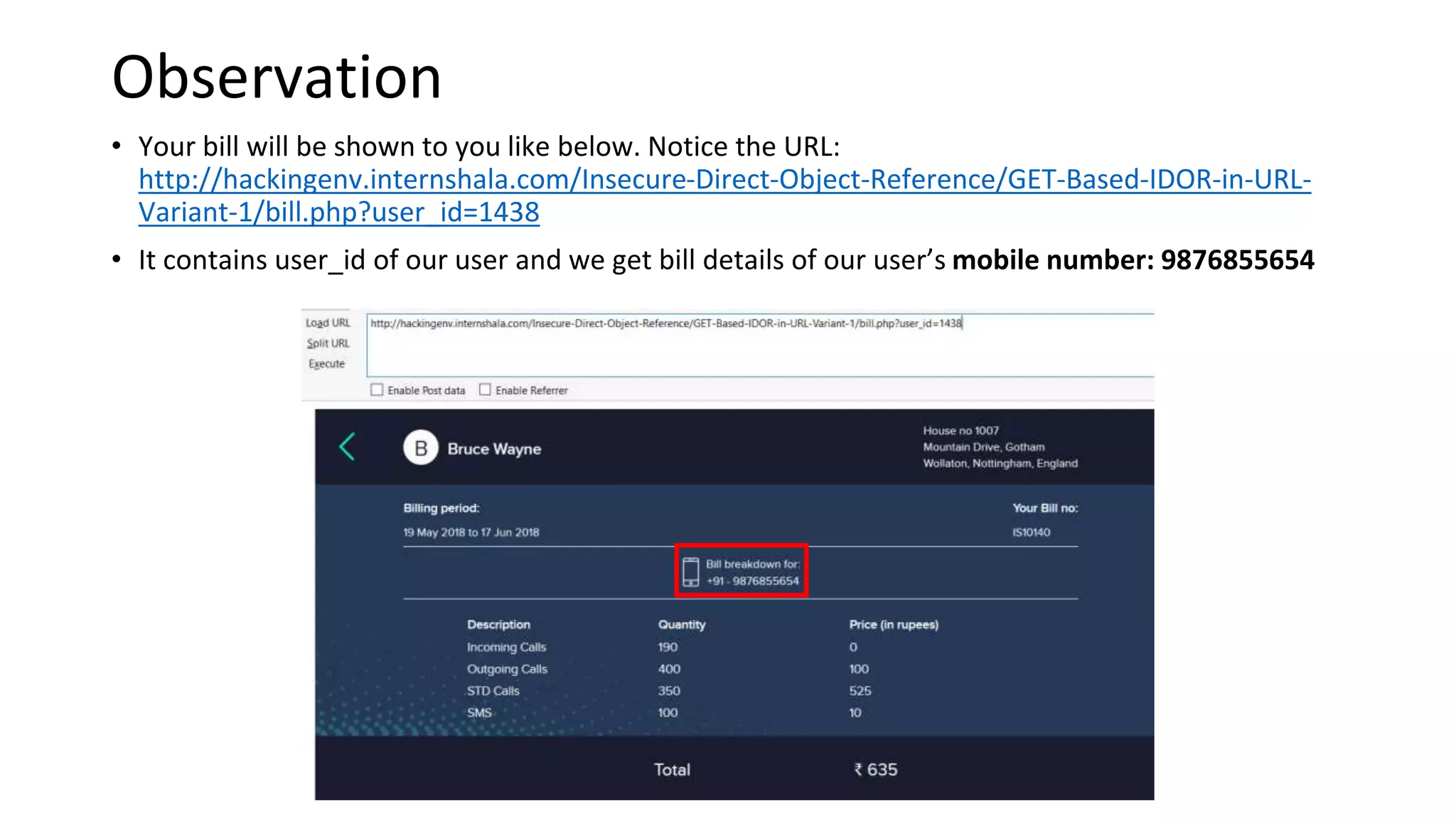
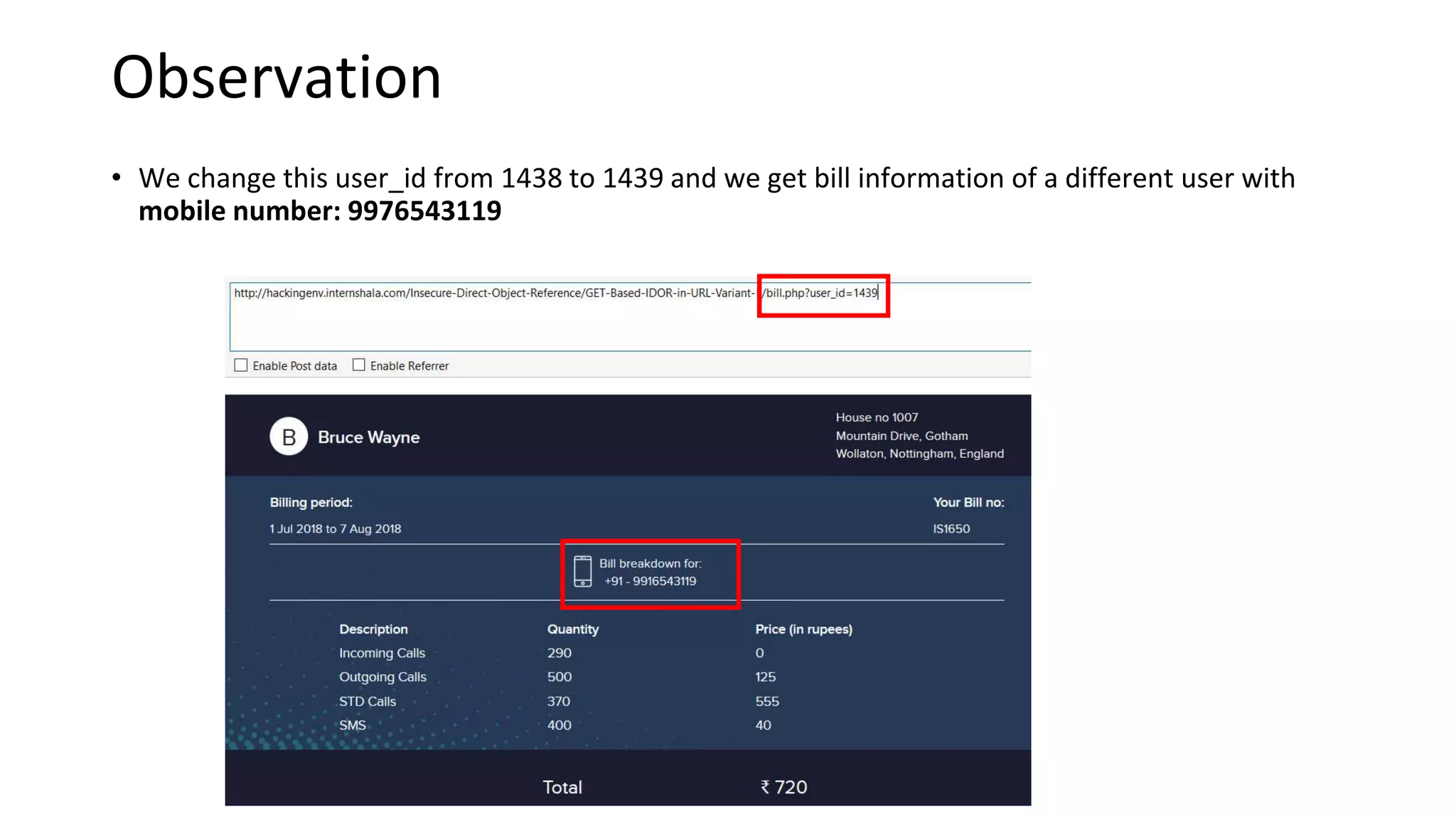
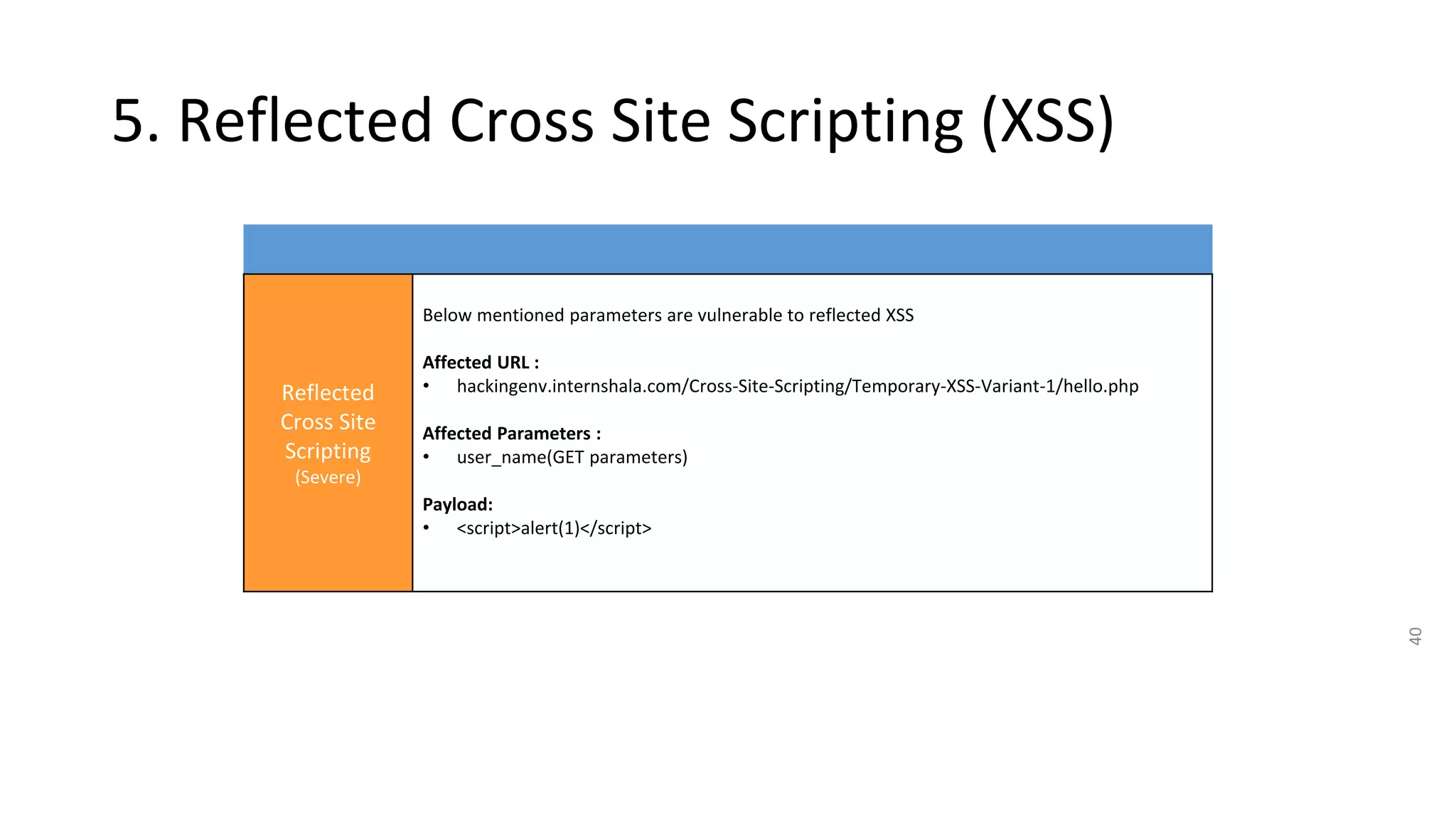
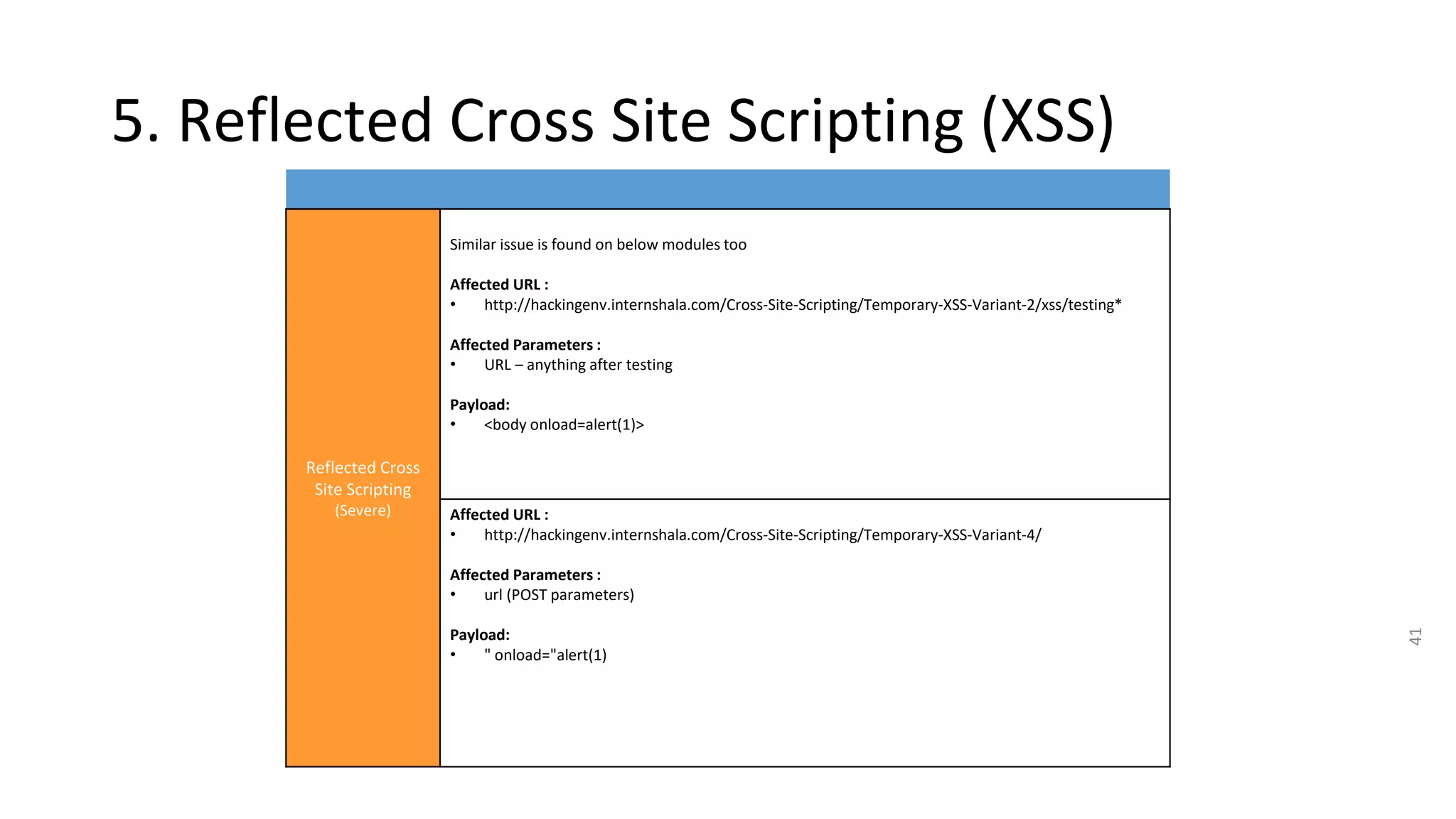
4. IDOR vulnerabilities allow unauthorized access to sensitive customer information like bills, invoices, call history and SMS logs.
The report provides details of vulnerabilities found, potential business impacts, and recommendations to address each issue. It concludes the application needs to address SQLi, weak passwords,