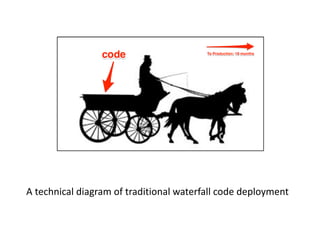
The document discusses building a modern security engineering organization. It describes how the world has changed with near-instantaneous code deployment and increased developer access to production systems. It advocates for adopting a culture of continuous monitoring and transparency around security issues. The document provides recommendations for incentivizing communication between security and development teams and for implementing access restrictions in a way that does not remove capabilities. It also discusses using bug bounties and attack simulations to increase the cost for attackers.