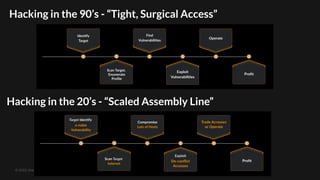
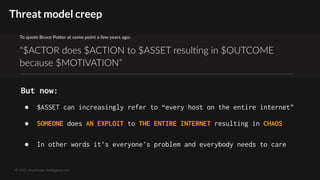
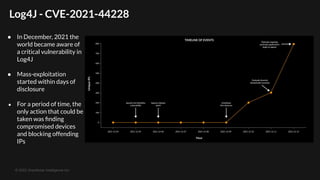
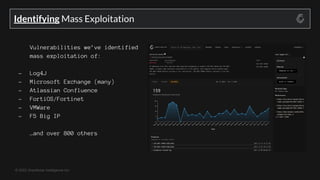
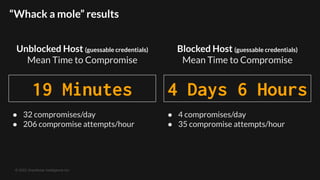
The document discusses the increasing threat of 'mass exploitation' in network hacking, characterized by attackers leveraging known vulnerabilities to compromise multiple systems before defenders can respond. It emphasizes the need for a proactive defense strategy, utilizing distributed honeypot networks to provide early warnings and situational awareness. The conclusion highlights that as mass exploitation worsens, quick responses and preemptive blocking of malicious IPs are crucial to minimize damage.