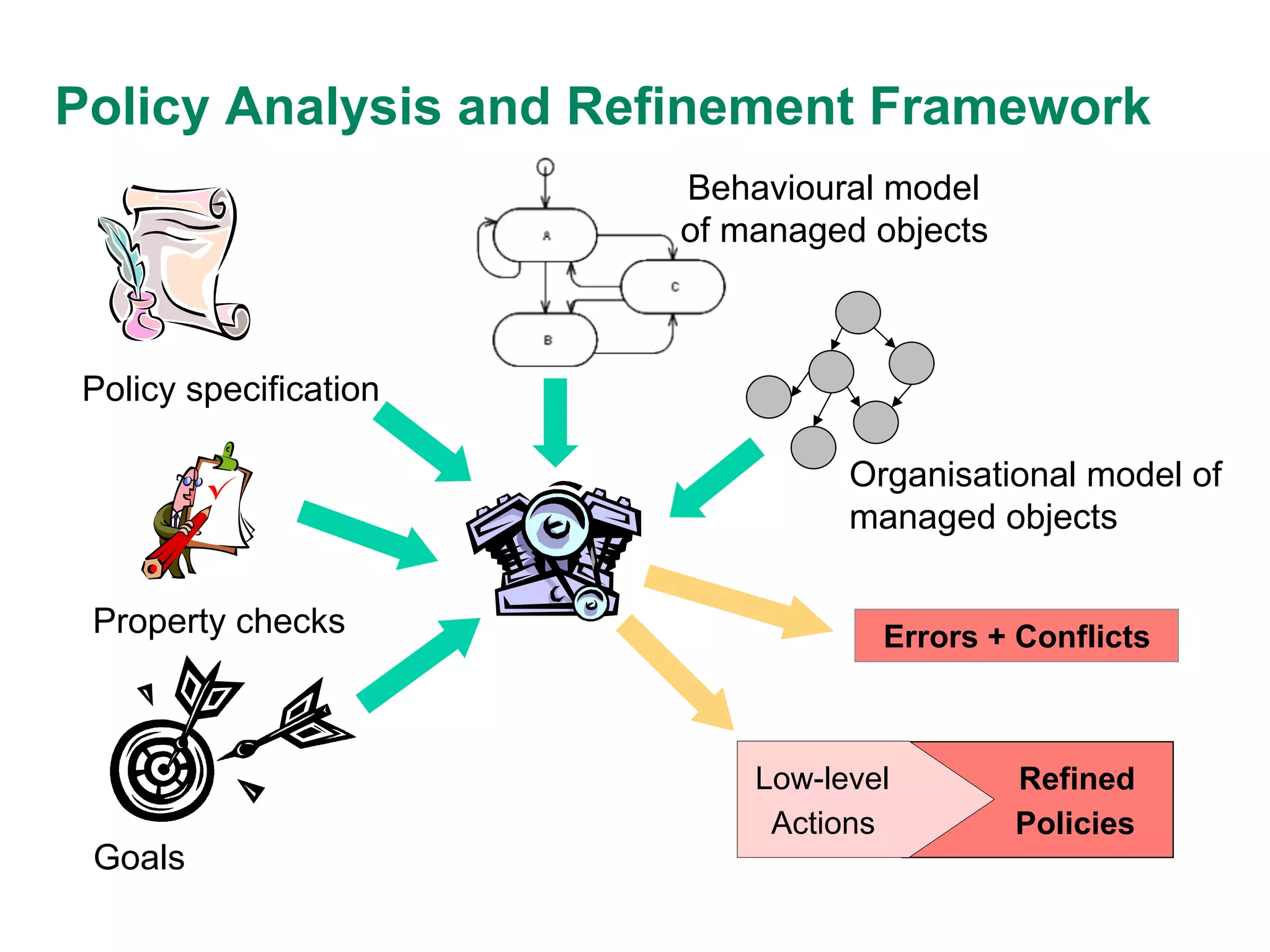
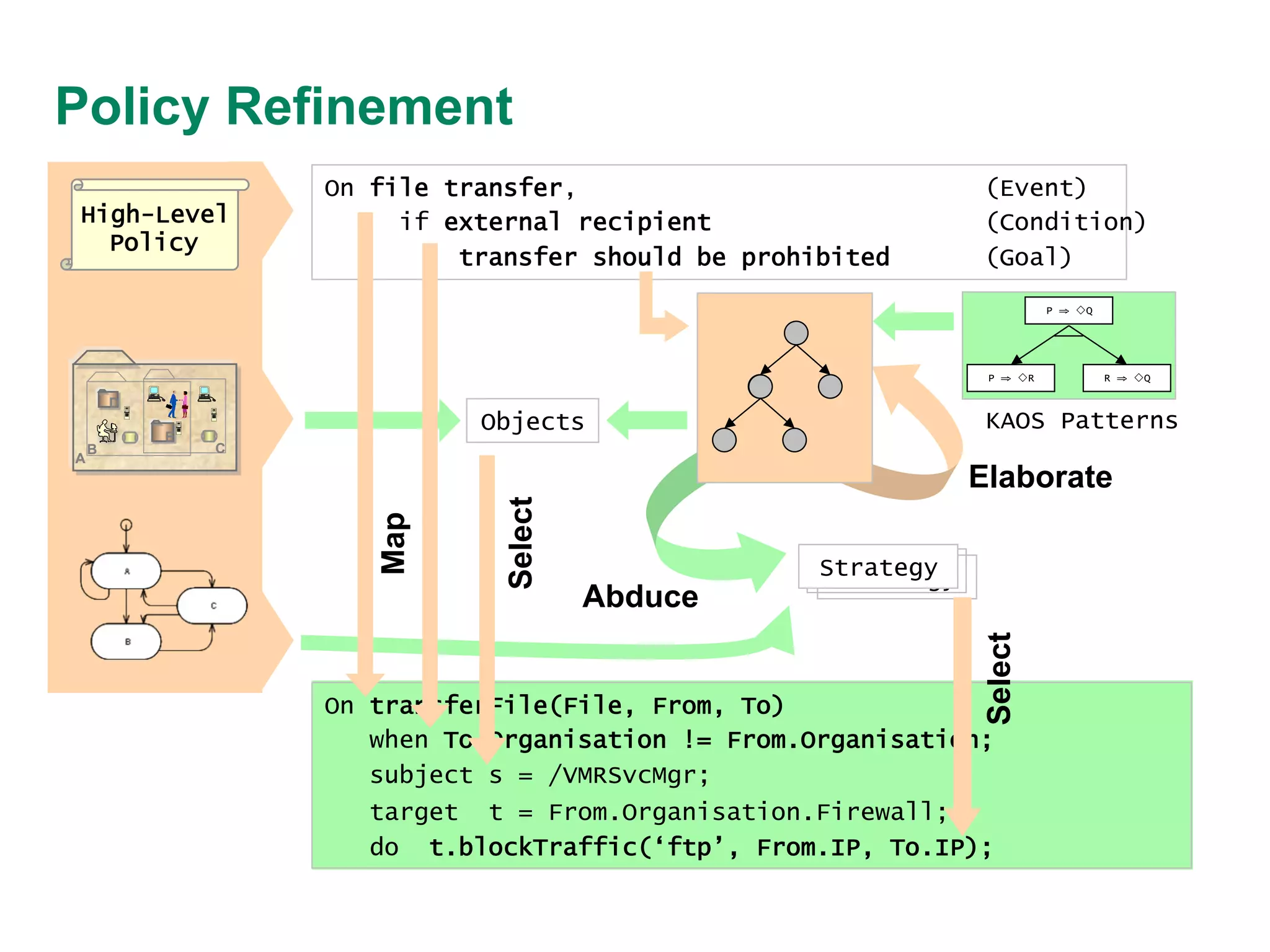
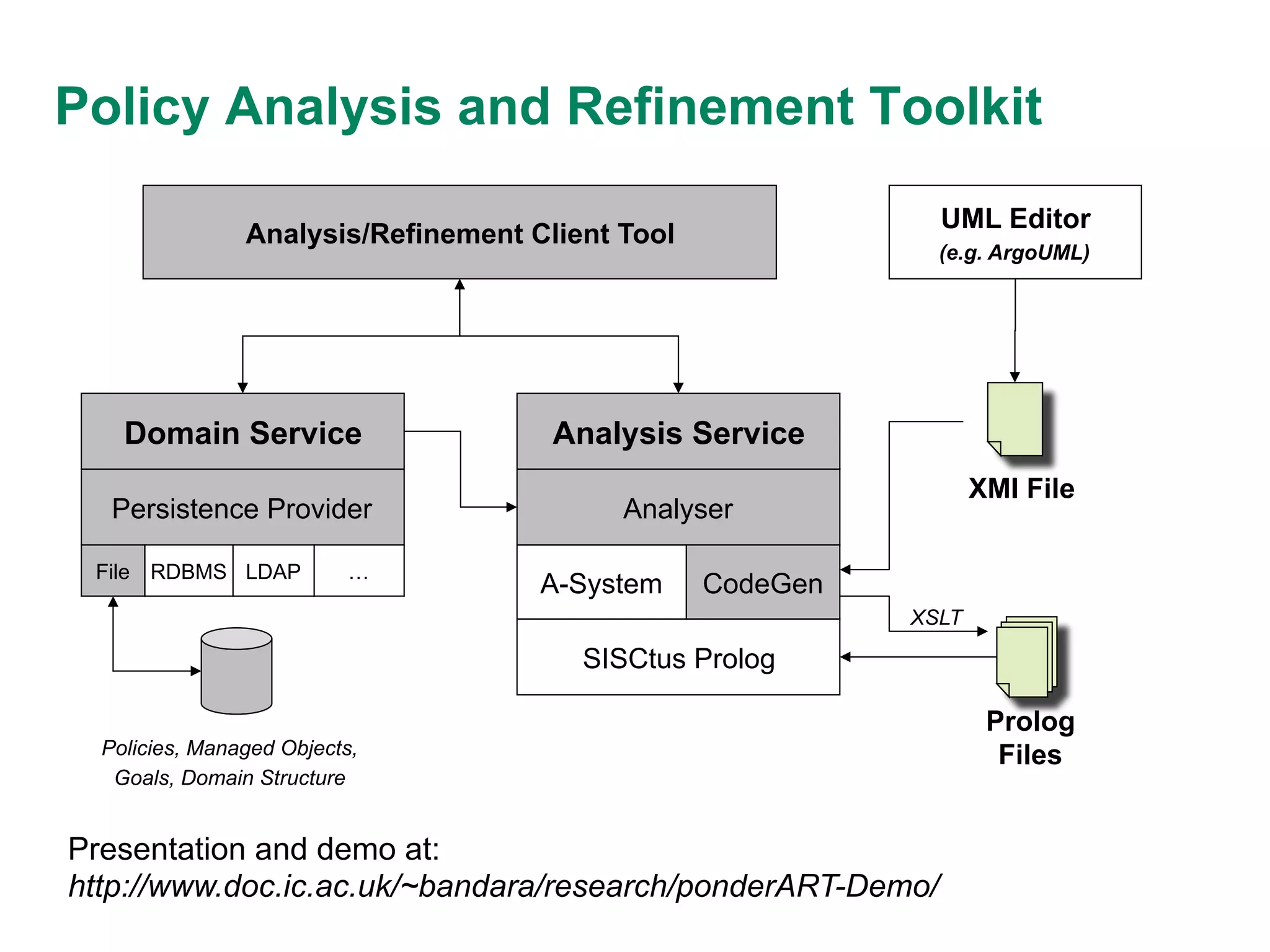
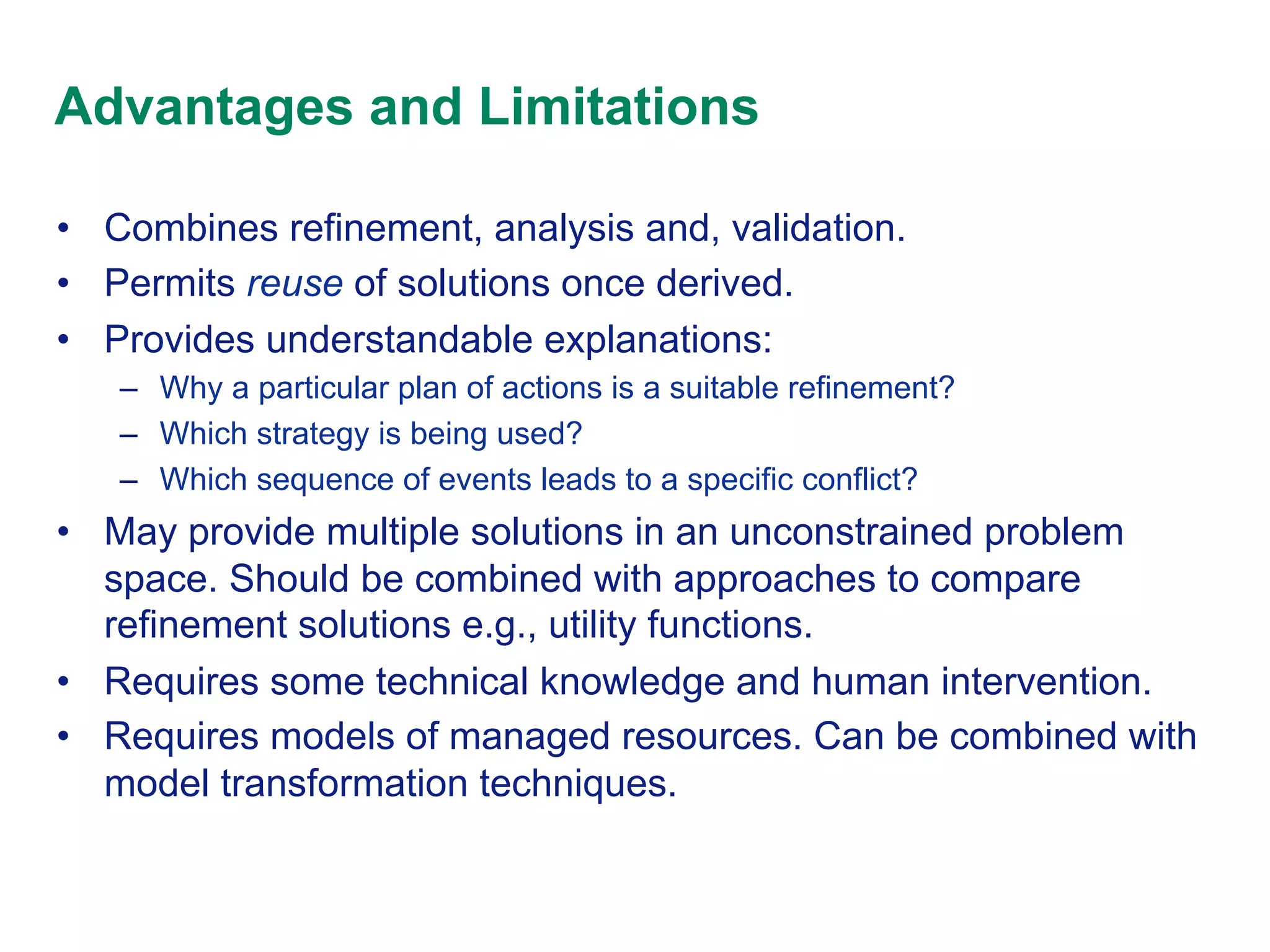
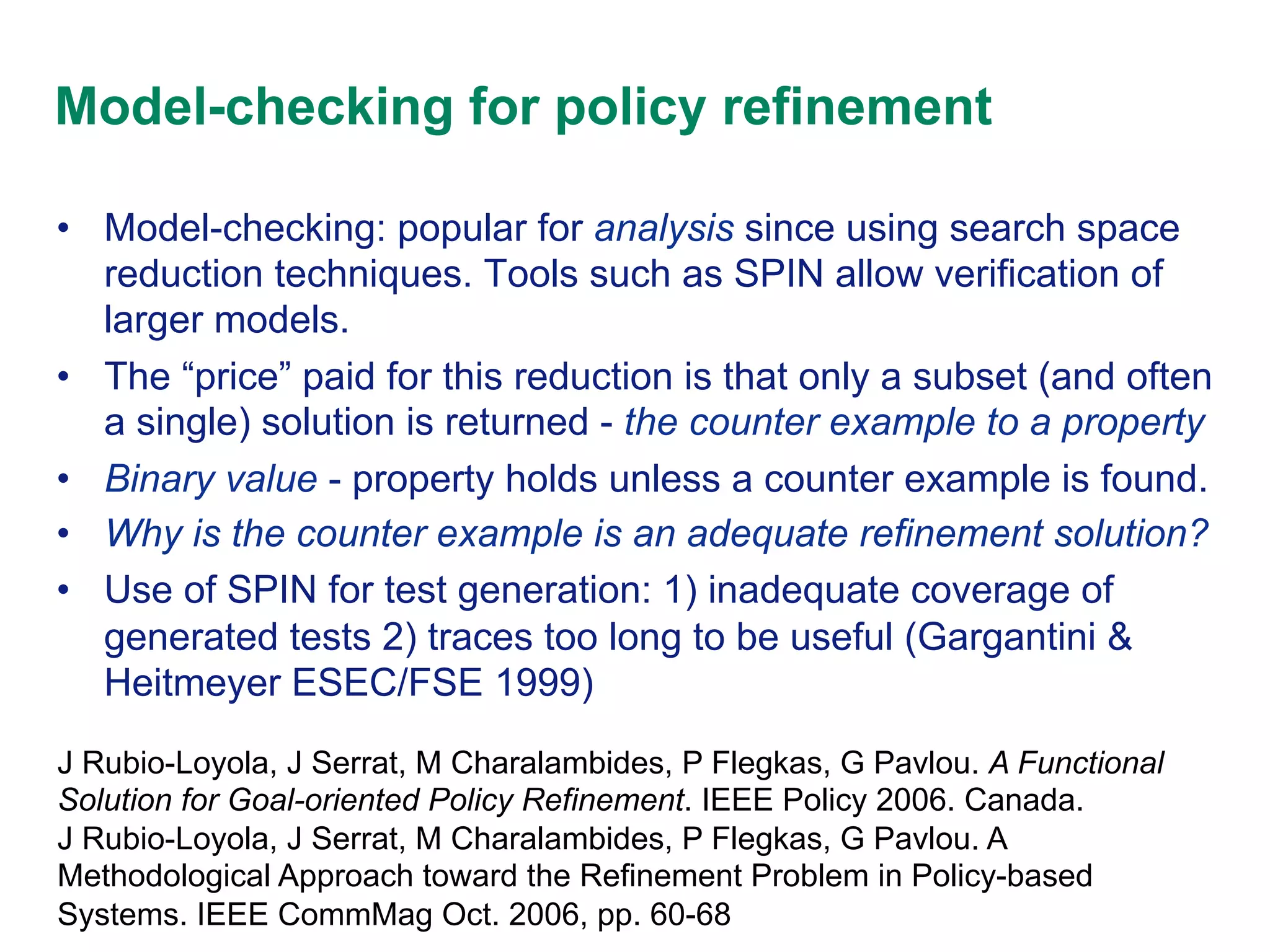
This document discusses an approach to policy refinement and analysis using goal decomposition, abductive reasoning, and formal representations of policies and managed objects. The approach involves decomposing high-level goals into refined policies using patterns, and applying abductive reasoning to derive policy elements and ensure consistency during refinement. Formal models of policies, goals, and managed objects are used to enable analysis, validation, and detect conflicts. The approach provides explanations for refinement and analysis results. The document also discusses limitations and comparisons to other policy refinement techniques.