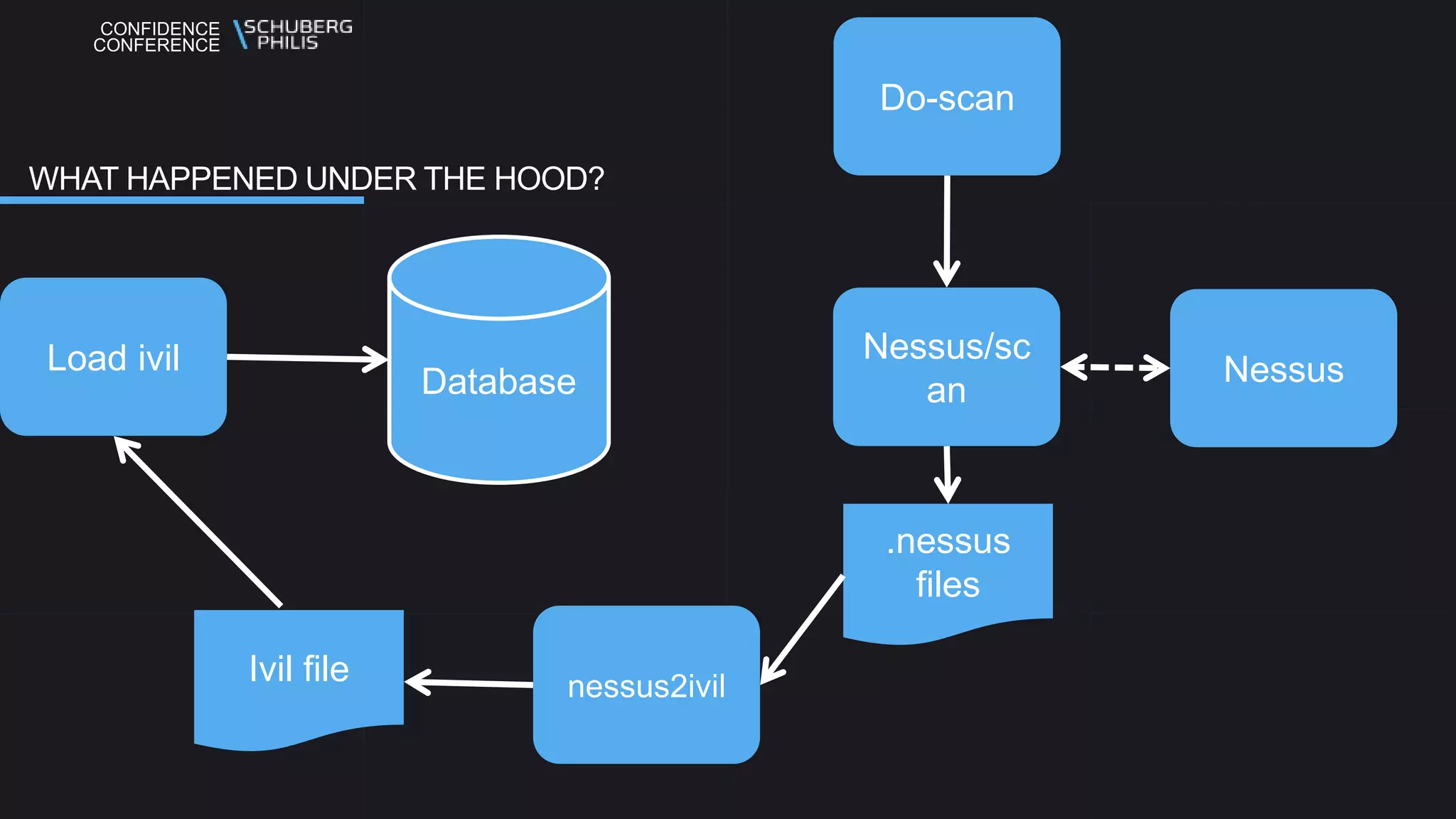
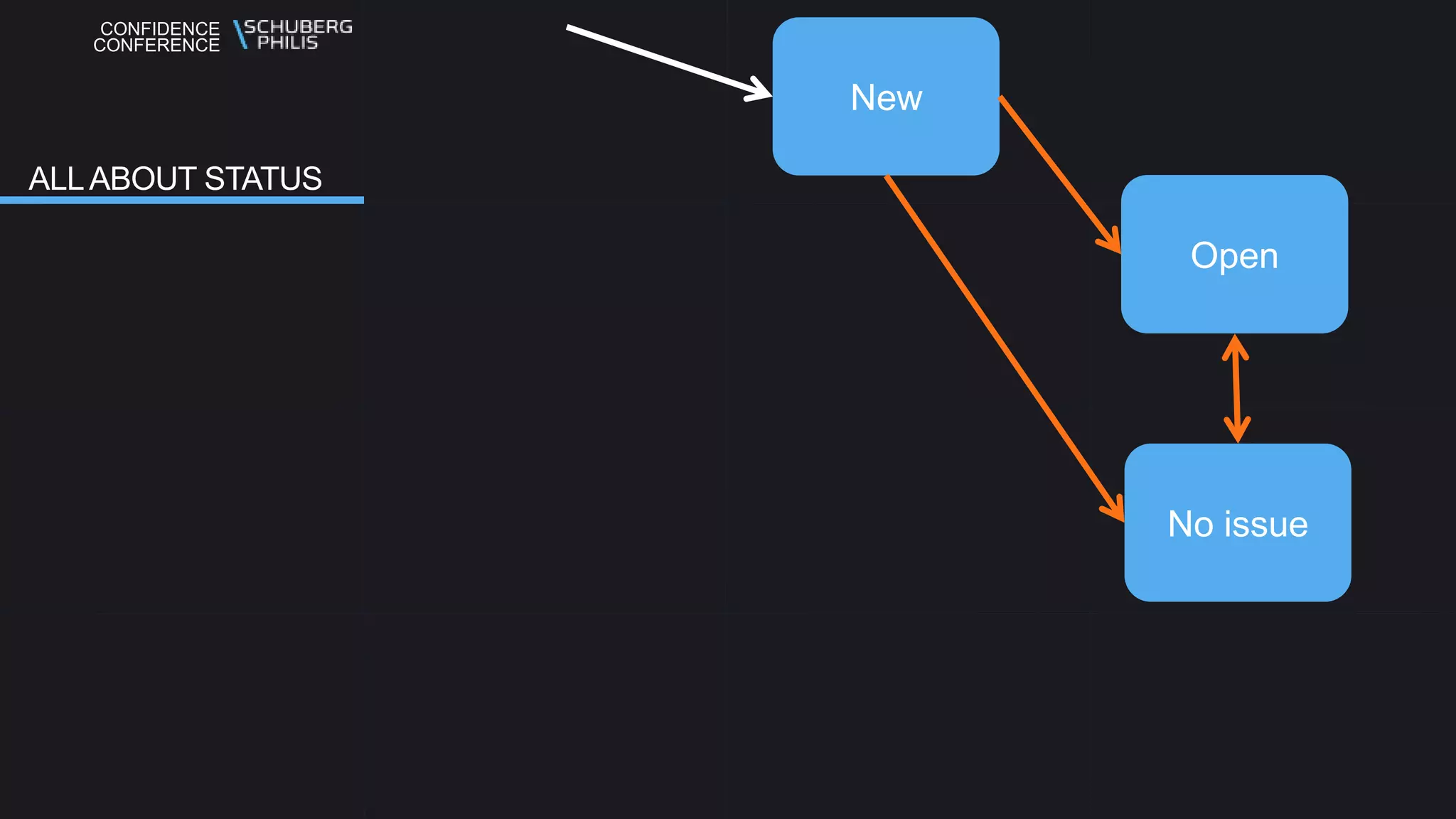
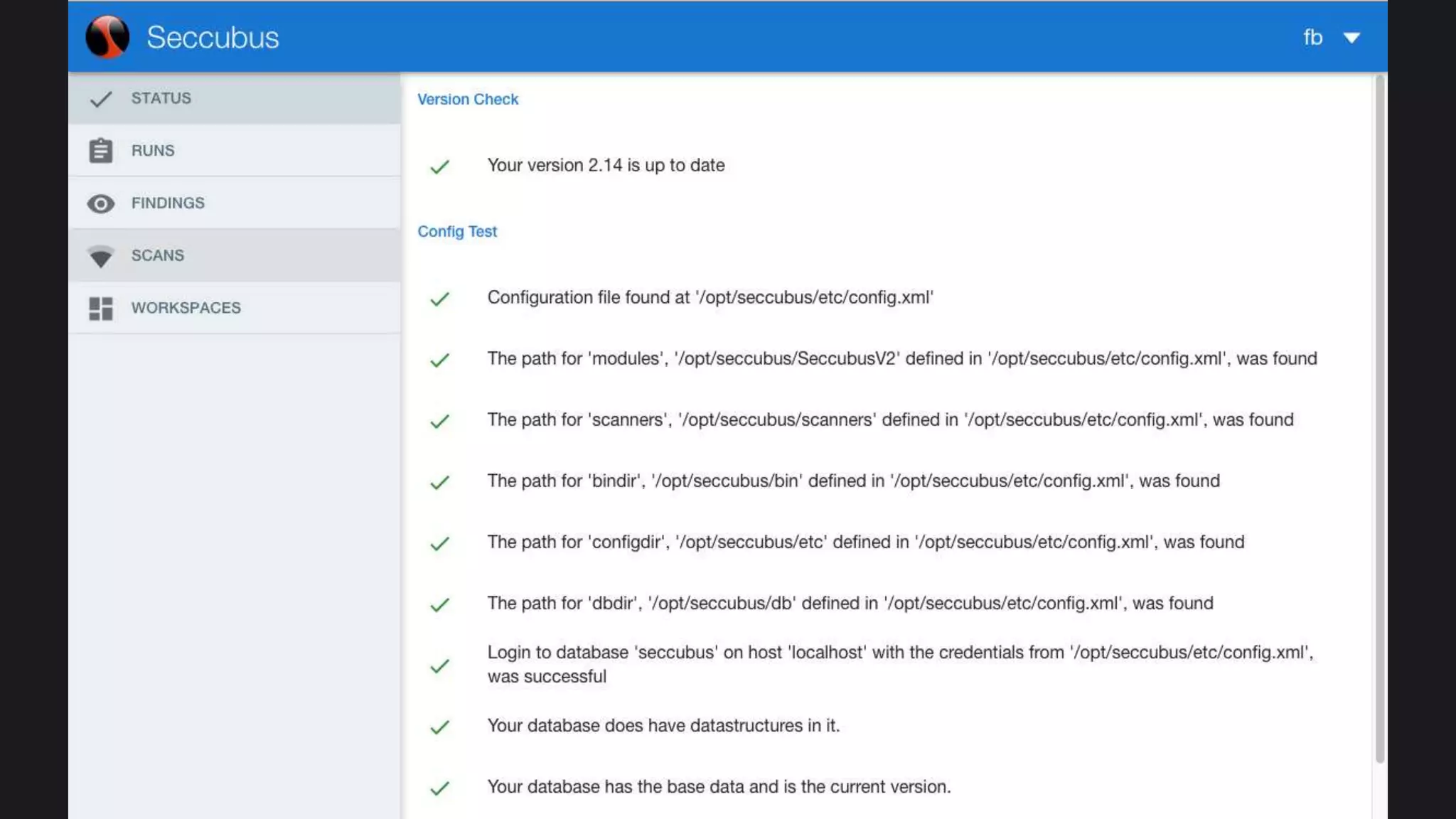
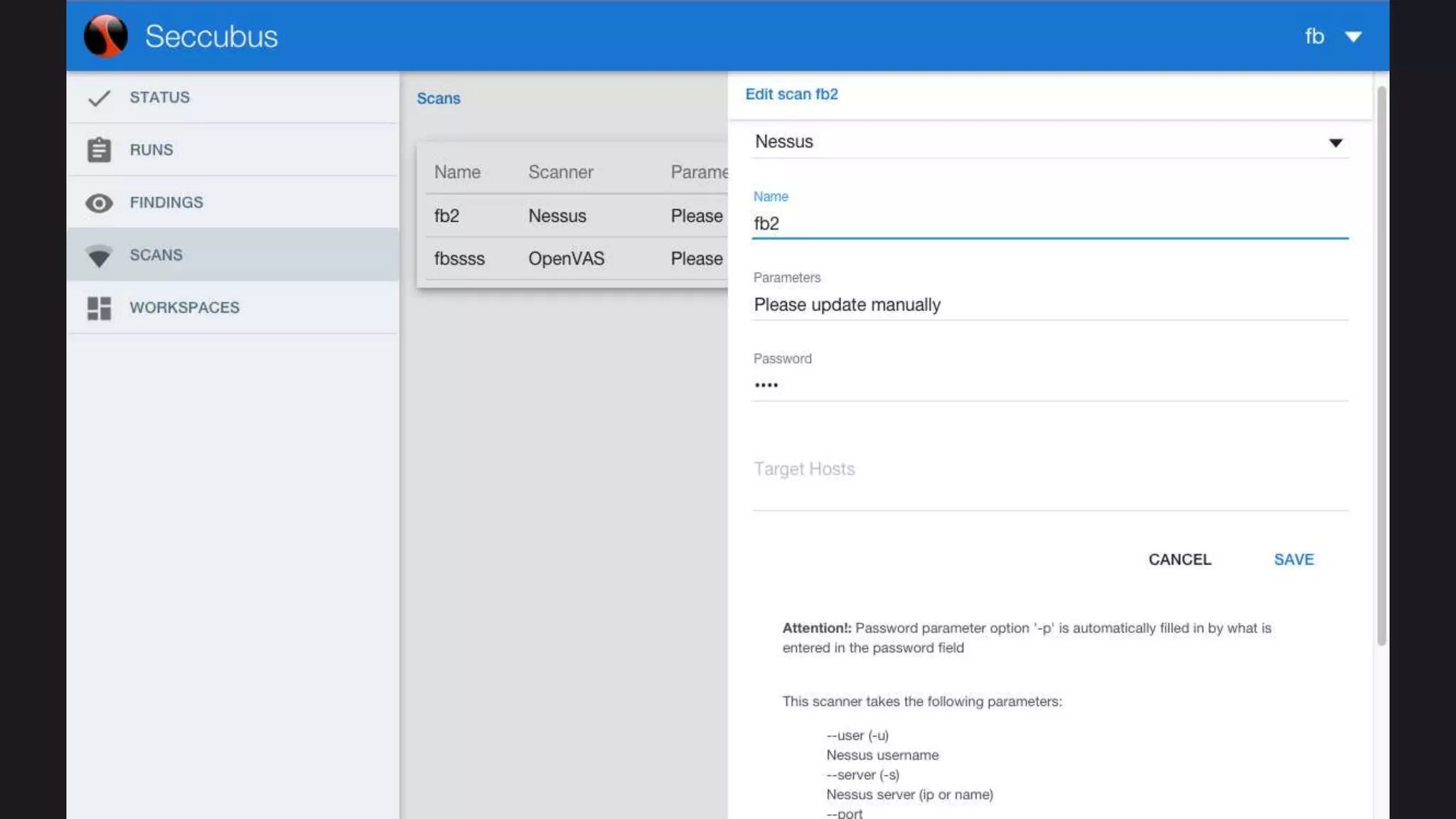
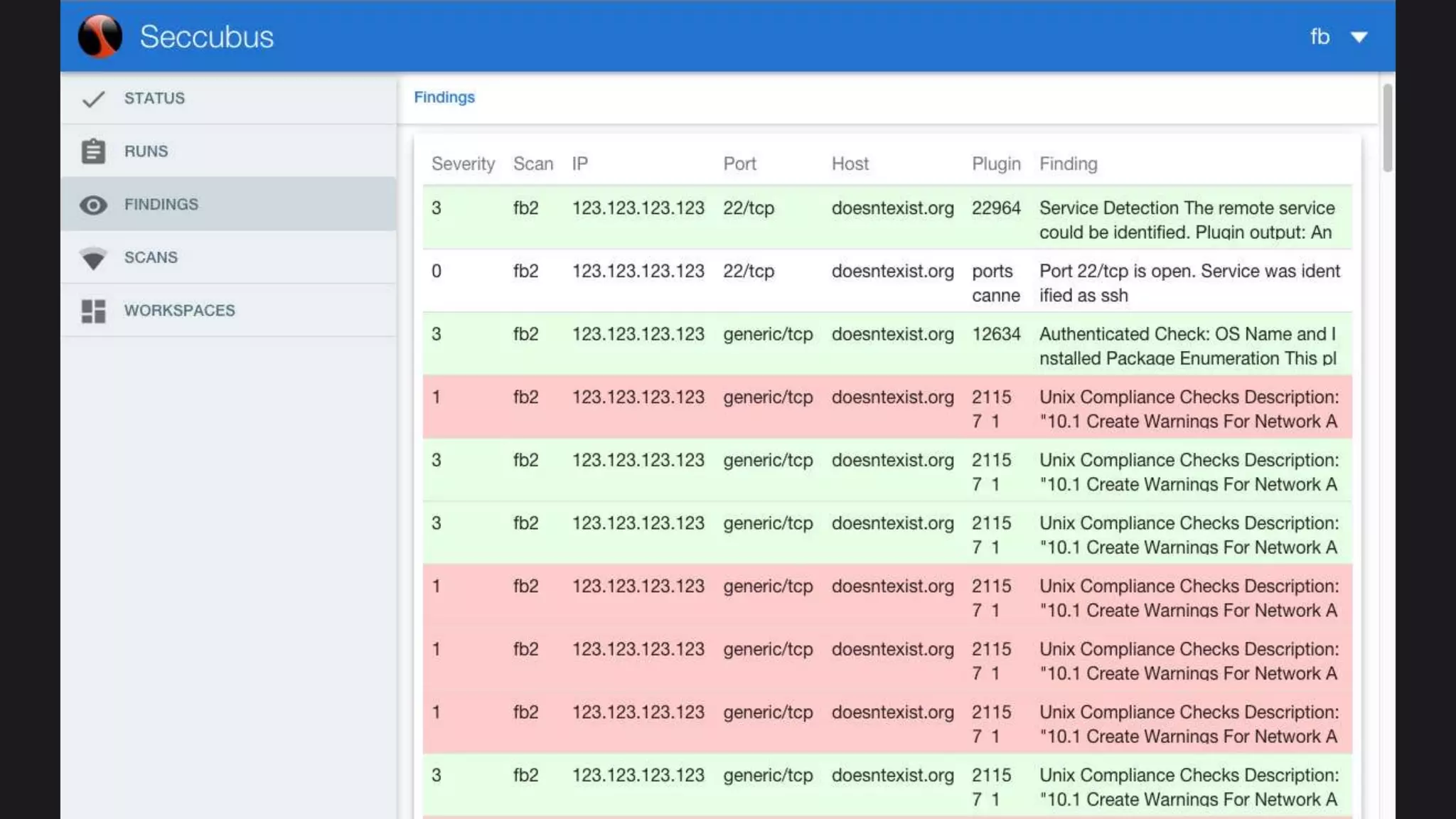
The document discusses the Seccubus project, initiated to streamline vulnerability scanning and analysis in security operations. This project aims to reduce false positives and automate reporting to enhance efficiency and integrate with continuous delivery workflows. The presentation highlights the development of Seccubus over six years, emphasizing its evolution and features that aid security professionals in managing vulnerabilities effectively.