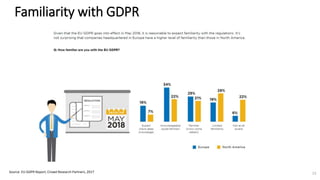
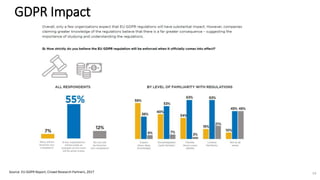
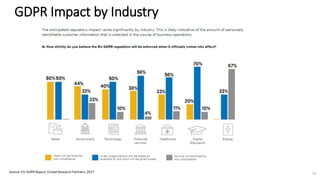
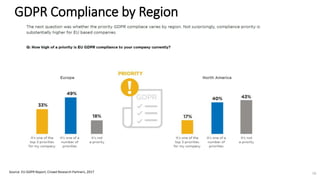
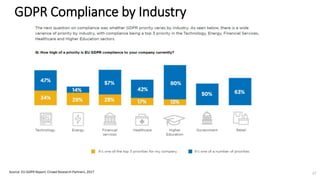
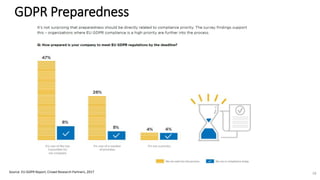
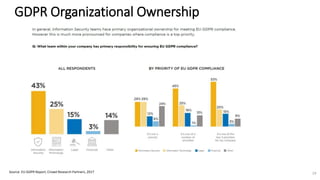
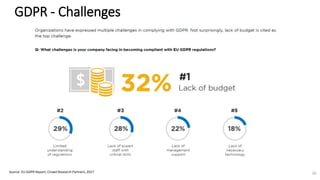
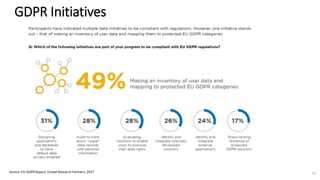
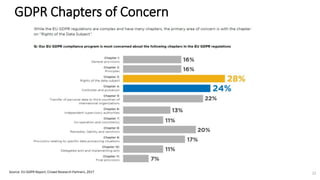
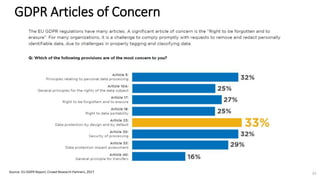
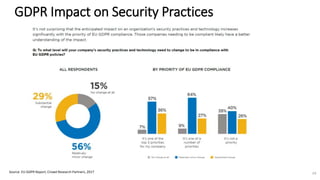
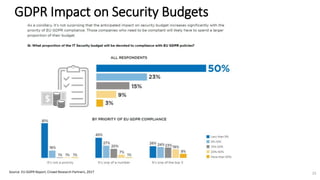
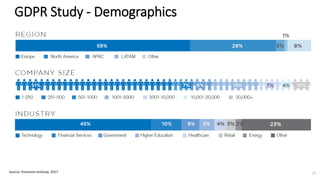
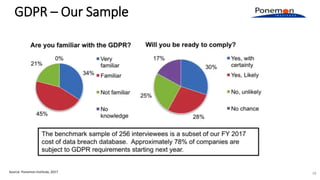
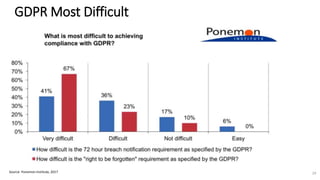
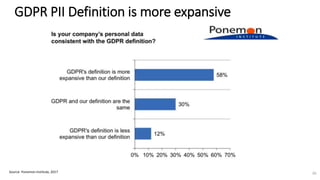
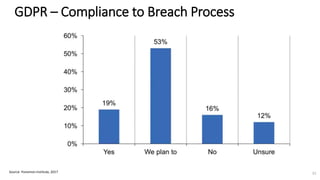
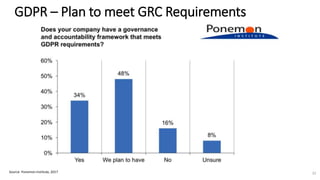
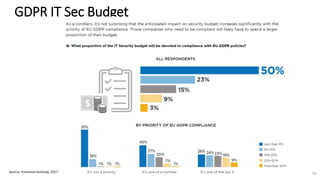
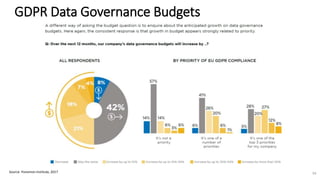
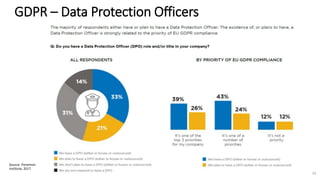
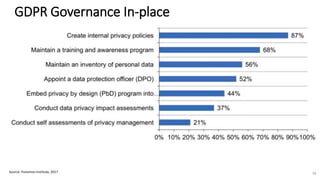
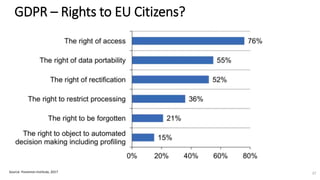
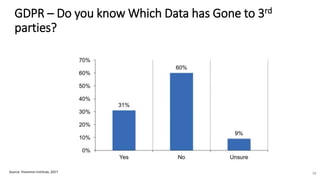
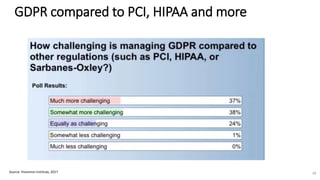
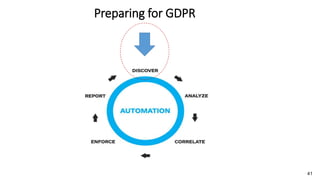
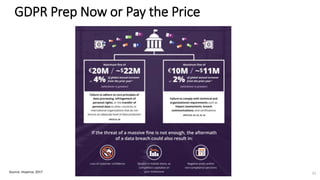
A recent PwC survey of U.S. companies revealed that GDPR compliance has become a top priority, with 54% of executives indicating it's their leading data protection focus. Notably, many companies are significantly increasing their budgets for GDPR preparations, with 77% planning to spend at least $1 million. Additionally, there is a notable shift towards adopting binding corporate rules for data transfer and a reconsideration of U.S. companies' presence in Europe due to GDPR risks.