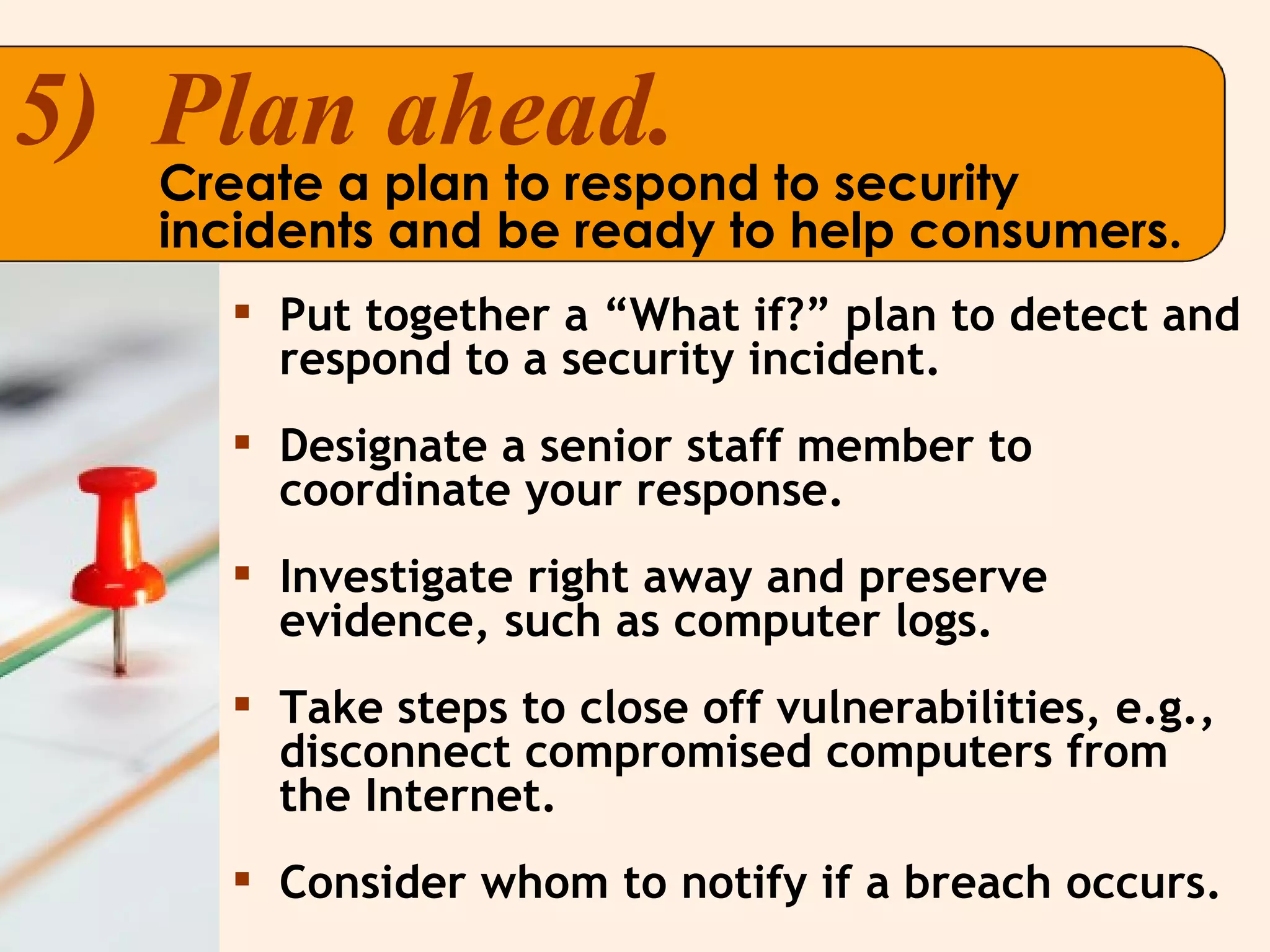
The document provides guidance for businesses on protecting personal information and complying with information security laws. It recommends that businesses take stock of the information they have, scale it down to only what is needed, lock or protect the information, properly dispose of what is no longer needed, and plan ahead for how to respond to security incidents. The document outlines key laws around information security and provides tips and resources for businesses.