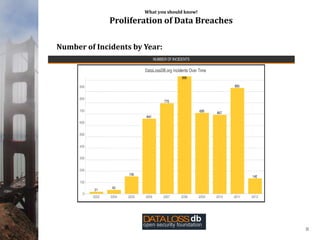
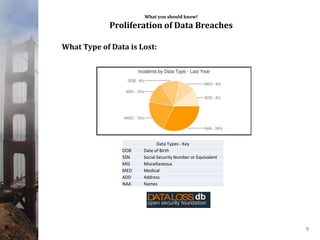
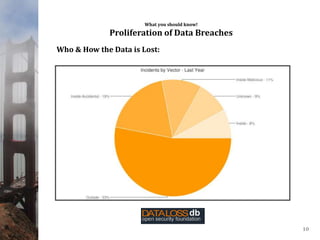
This document provides an overview of data privacy for governmental organizations. It discusses what data privacy is, the risks associated with it such as identity theft, and common laws around data privacy including California state laws. It recommends that organizations take an inventory of their data, develop privacy policies and training, and ensure proper system monitoring and controls. The document emphasizes being proactive on data privacy issues.