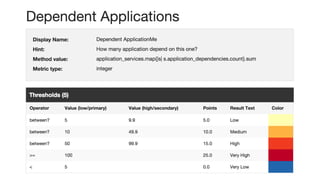
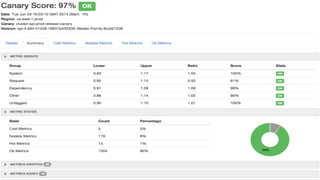
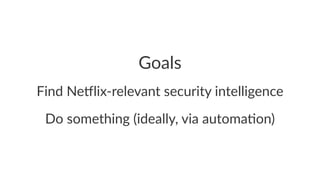
This document discusses various techniques for improving security automation and visibility, including discovering and inventorying assets, prioritizing risks, performing multi-layer security testing, monitoring configurations, discovering and handling security intelligence, and refining security signals and response. Key recommendations include tailoring discovery to the rate of change, considering data normalization, using risk prioritization as an input not a law, avoiding certain conversations, leveraging security testing pyramids, recognizing a continuum of configuration safety, developing an intelligence taxonomy, and starting small with signal refinement and response automation.