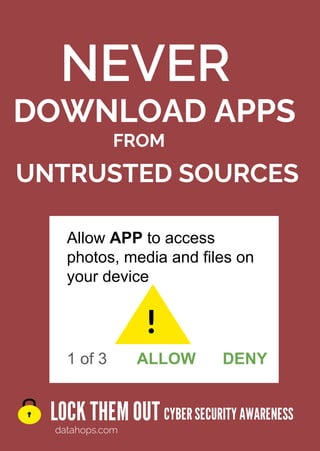
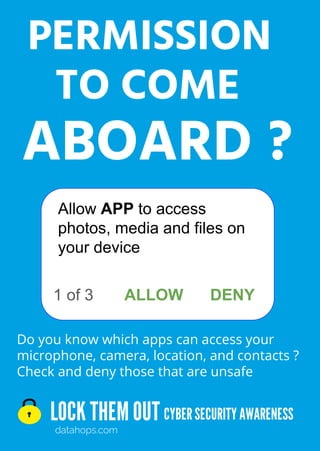
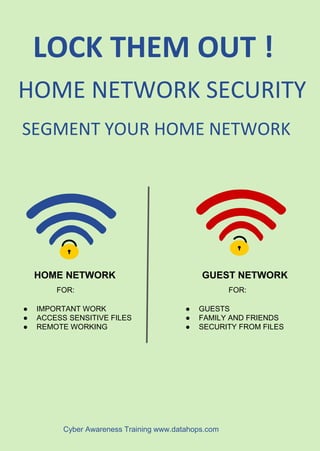
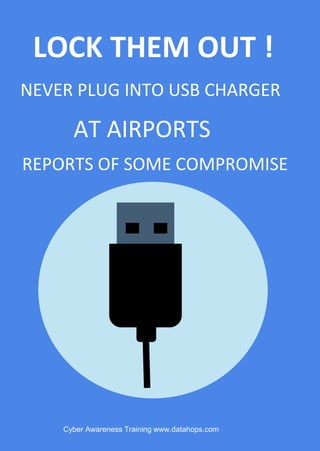
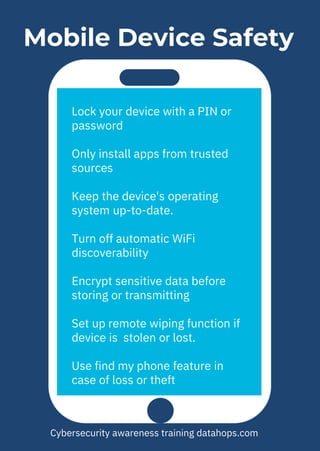
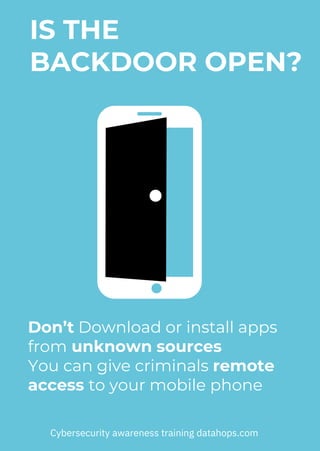
The document provides cybersecurity awareness tips emphasizing the importance of securing devices, keeping software updated, and avoiding unknown sources for USBs and apps. It highlights practices such as using encryption, regularly backing up files, and not leaving devices unattended to protect sensitive information. Additional advice includes safeguarding company intellectual property and using password management for enhanced security.