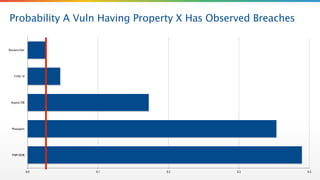
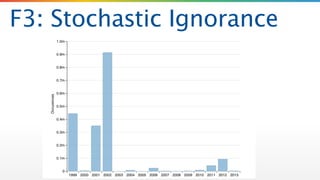
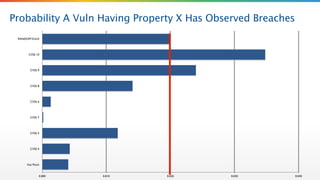
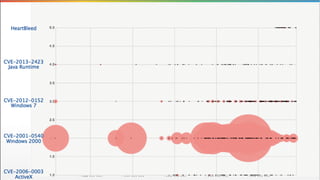
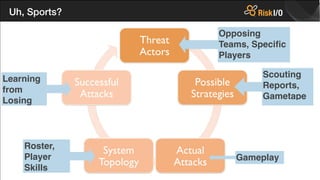
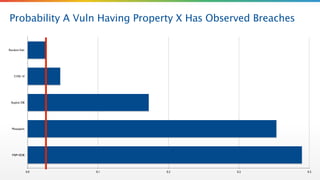
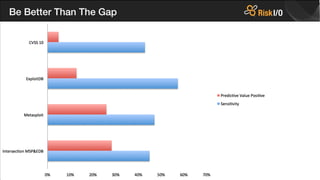
The document critiques the Common Vulnerability Scoring System (CVSS) and suggests that it fails to accurately assess risk due to empirical and analytical shortcomings. It emphasizes the need for better data-driven approaches to remediation, focused on the most risky vulnerabilities rather than relying solely on standardized scoring systems. The author advocates for a comprehensive understanding of vulnerabilities, including their practical implications and the necessity of adapting to changing attacker tactics.