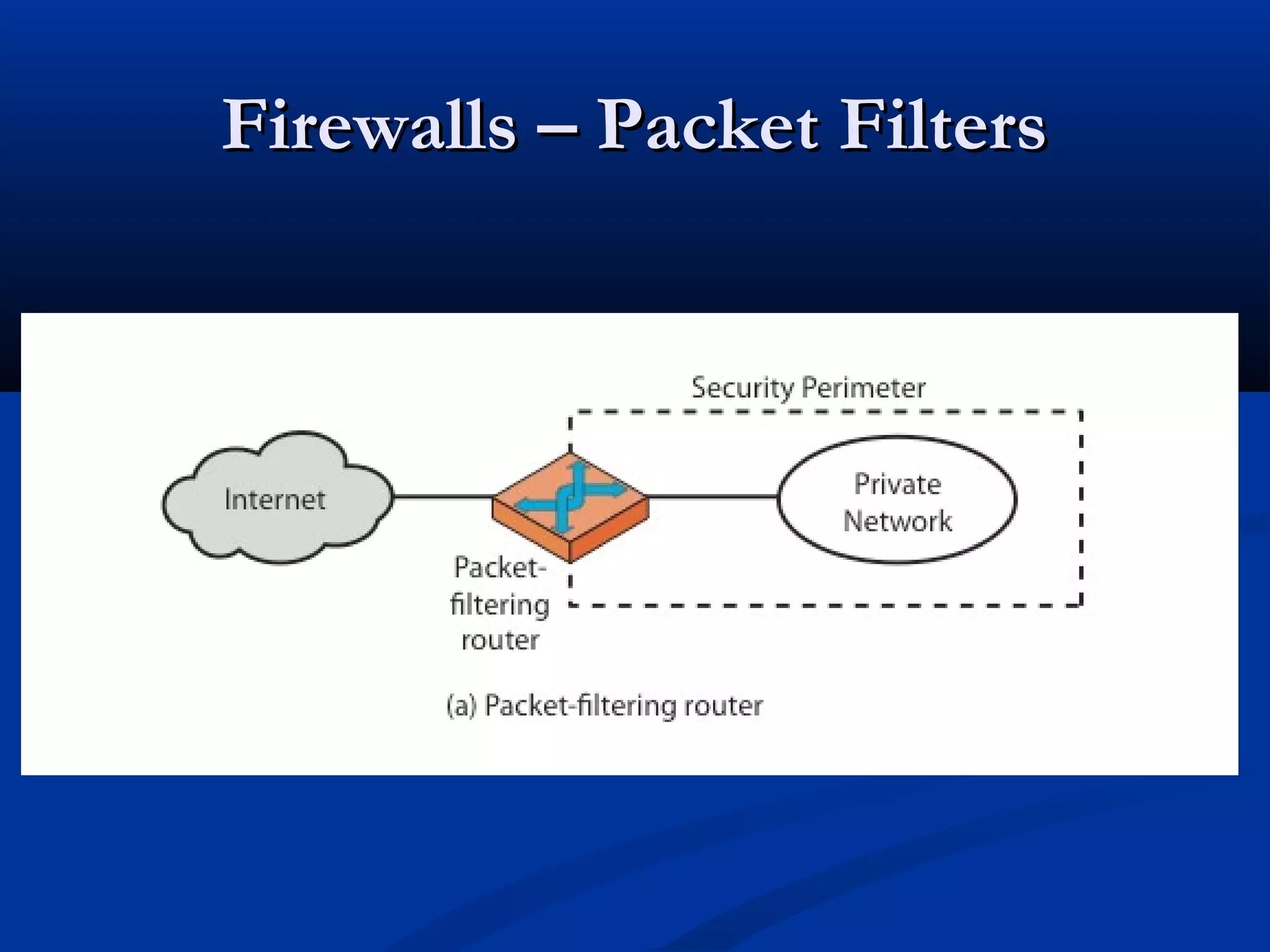
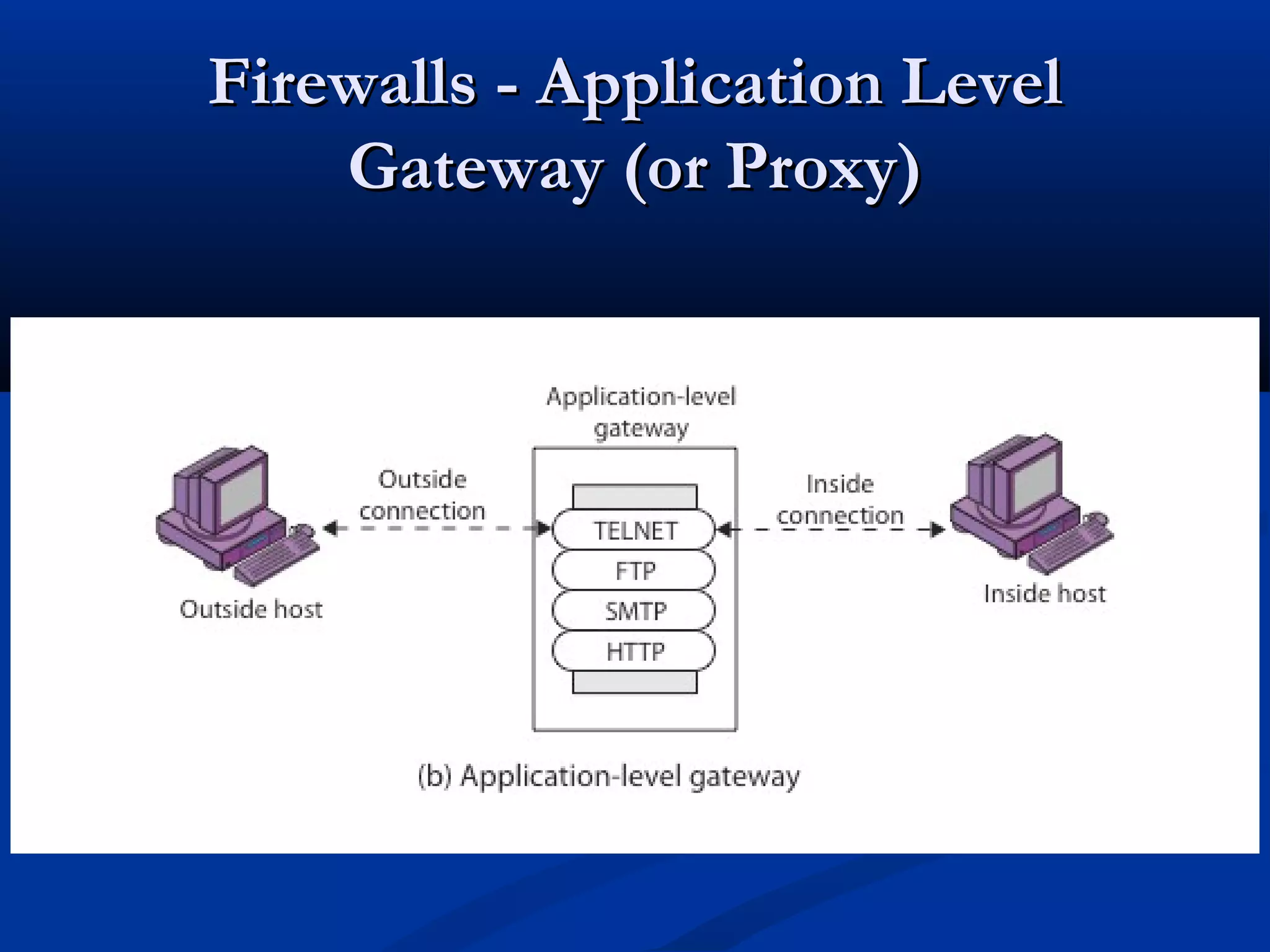
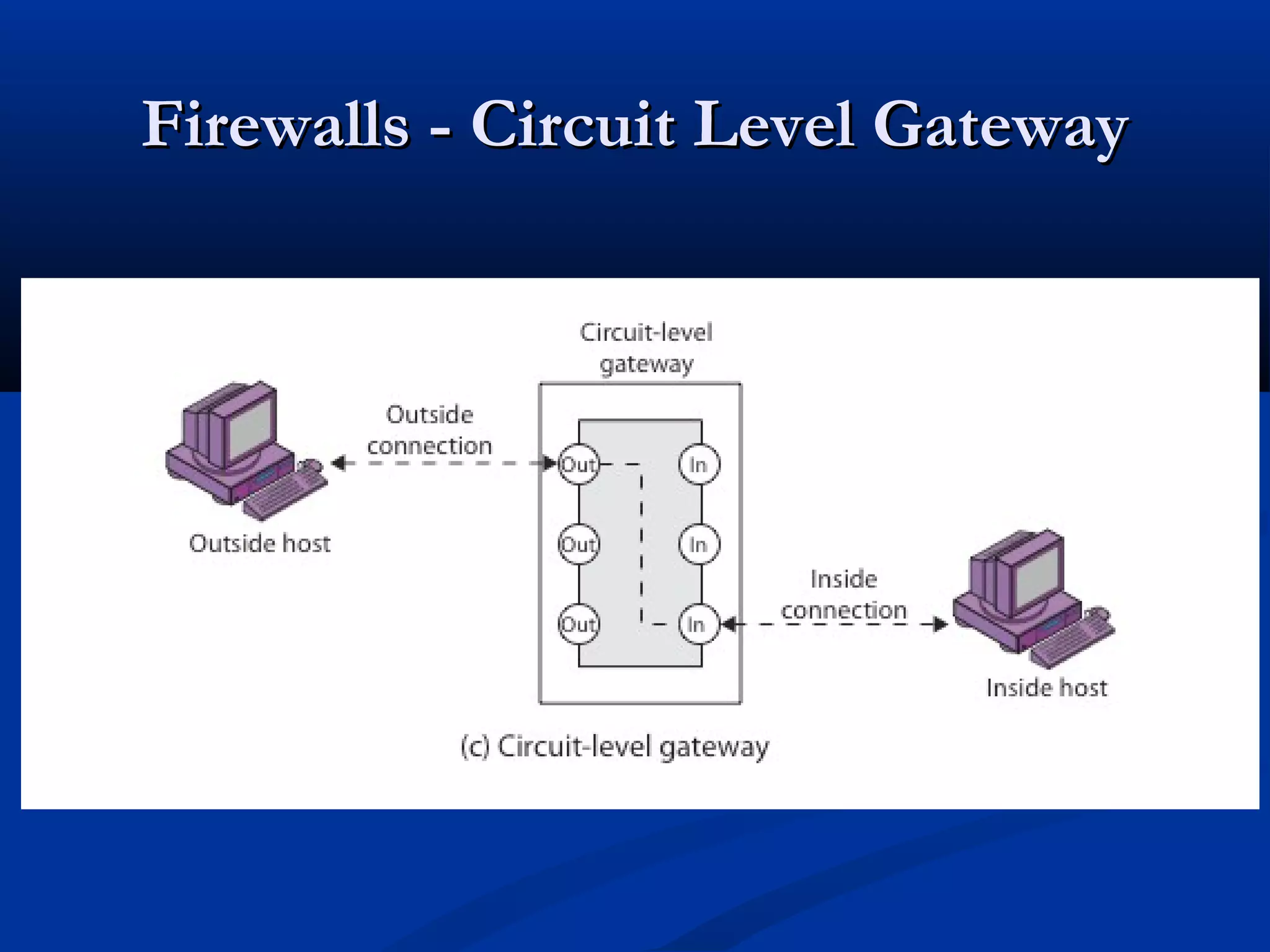
A firewall is a choke point that controls and monitors interconnects between networks with differing trust levels. It imposes restrictions on network services to only allow authorized traffic and can implement alarms for abnormal behavior. Firewalls are classified based on the protocol level they control, including packet filtering, circuit gateways, and application gateways. Packet filtering firewalls filter network packets based on their header values.