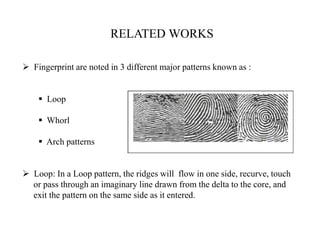
This document summarizes a survey on enhancing and developing countermeasures for fingerprint authentication systems. It discusses common spoofing attacks and errors in fingerprint systems. It also reviews related work on fingerprint patterns and features. Methods to enhance fingerprint matching include thinning ridges, segmenting regions of interest, and extracting ridge contours. The document also discusses hardware-based and software-based liveness detection techniques to prevent spoofing, such as analyzing perspiration and texture. The goal of the survey is to improve fingerprint authentication performance and security by addressing vulnerabilities.












![REFERENCES
[1] K. Cao, E. Liu, L. Pang, J. Liang, and J. Tian. Fingerprint matching by
incorporating minutiae discriminability. In Intl Joint Conference on
Biometrics (IJCB), pages 1–6. IEEE, 2011.
[2] A.Nagar, H. Choi, and A. K. Jain. Evidential value of automated latent
fingerprint comparison: an empirical approach. IEEE Transactions on
Information Forensics and Security, 7(6):1752–1765, 2012.
[3] M. Martinez-Diaz, J. Fierrez, J. Galbally, and J. Ortega-Garcia. An
evaluation of indirect attacks and countermeasures in fingerprint
verification systems. Pattern Recognition Letters, 32(12):1643–1651, 2011.
[4] A. K. Jain, Y. Chen, and M. Demirkus. Pores and ridges: High-resolution
fingerprint matching using level 3 features. IEEE Transactions on Pattern
Analysis and Machine Intelligence, 29(1):15–27, January 2007.](https://image.slidesharecdn.com/confpaperslide-181016044906/85/Fingerprint-Analaysis-14-320.jpg)
![[5] T. Matsumoto, H. Matsumoto, K. Yamada, and S. Hoshino. Impact of
artificial gummy fingers on fingerprint systems. In Electronic Imaging,
pages 275–289. International Society for Optics and Photonics, 2002.
[6] H. Cho, K. Choi, J. Kim, "Fingerprint matching incorporating ridge
features with minutiae", Information Forensics and Security IEEE
Transactions on, pp. 338-345, June 2011.
[7] Maltoni, D. Maio, A. K. Jain, and S. Prabhakar. Handbook of fingerprint
recognition. Springer Science & Business Media, 2009.
[8] B. Han, C. A. Marciniak, and W. C. Westerman. "Fingerprint sensing and
enrollment", US Patent App. 14/244,143.Apr. 3 2014.](https://image.slidesharecdn.com/confpaperslide-181016044906/85/Fingerprint-Analaysis-15-320.jpg)
