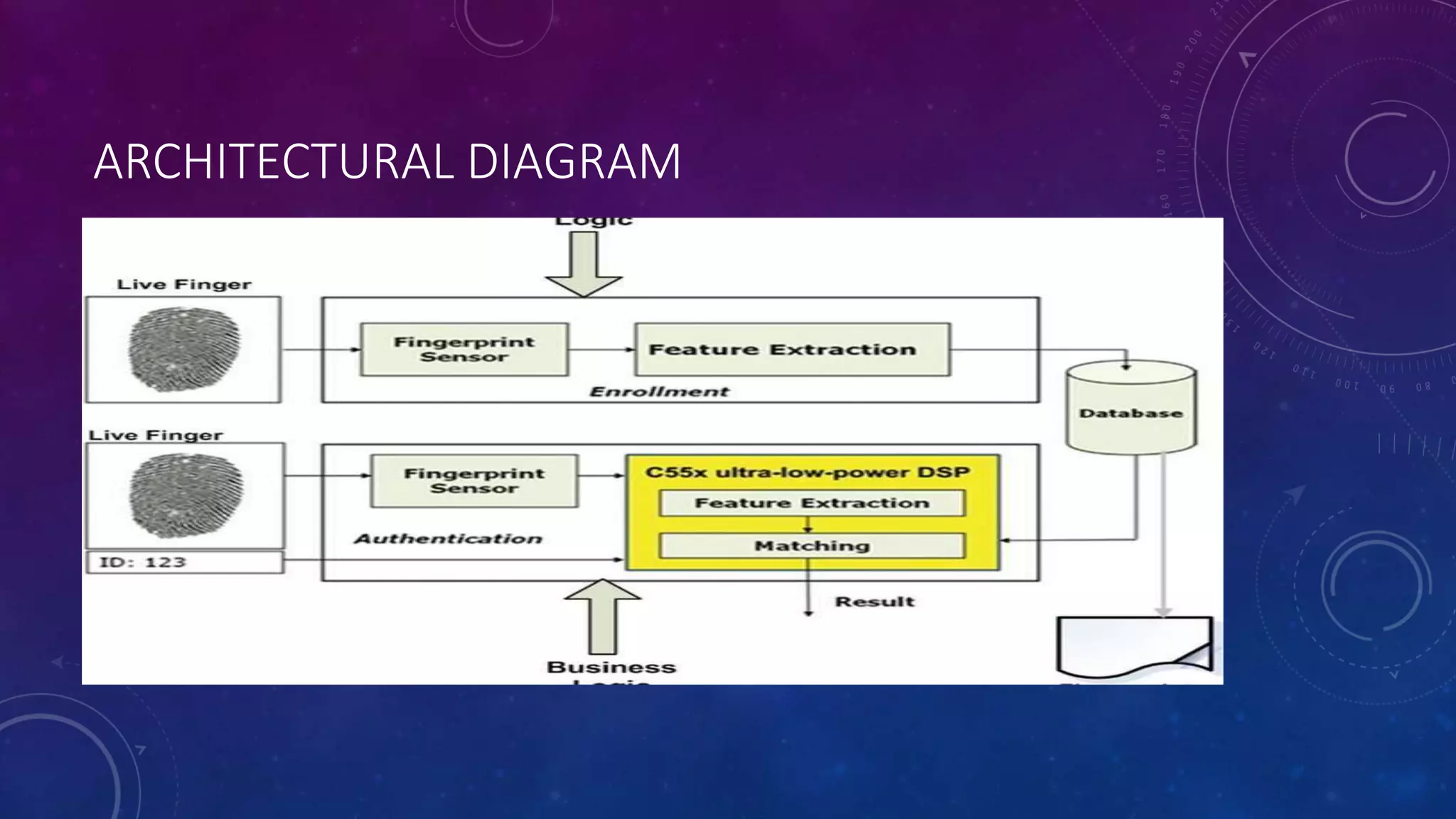
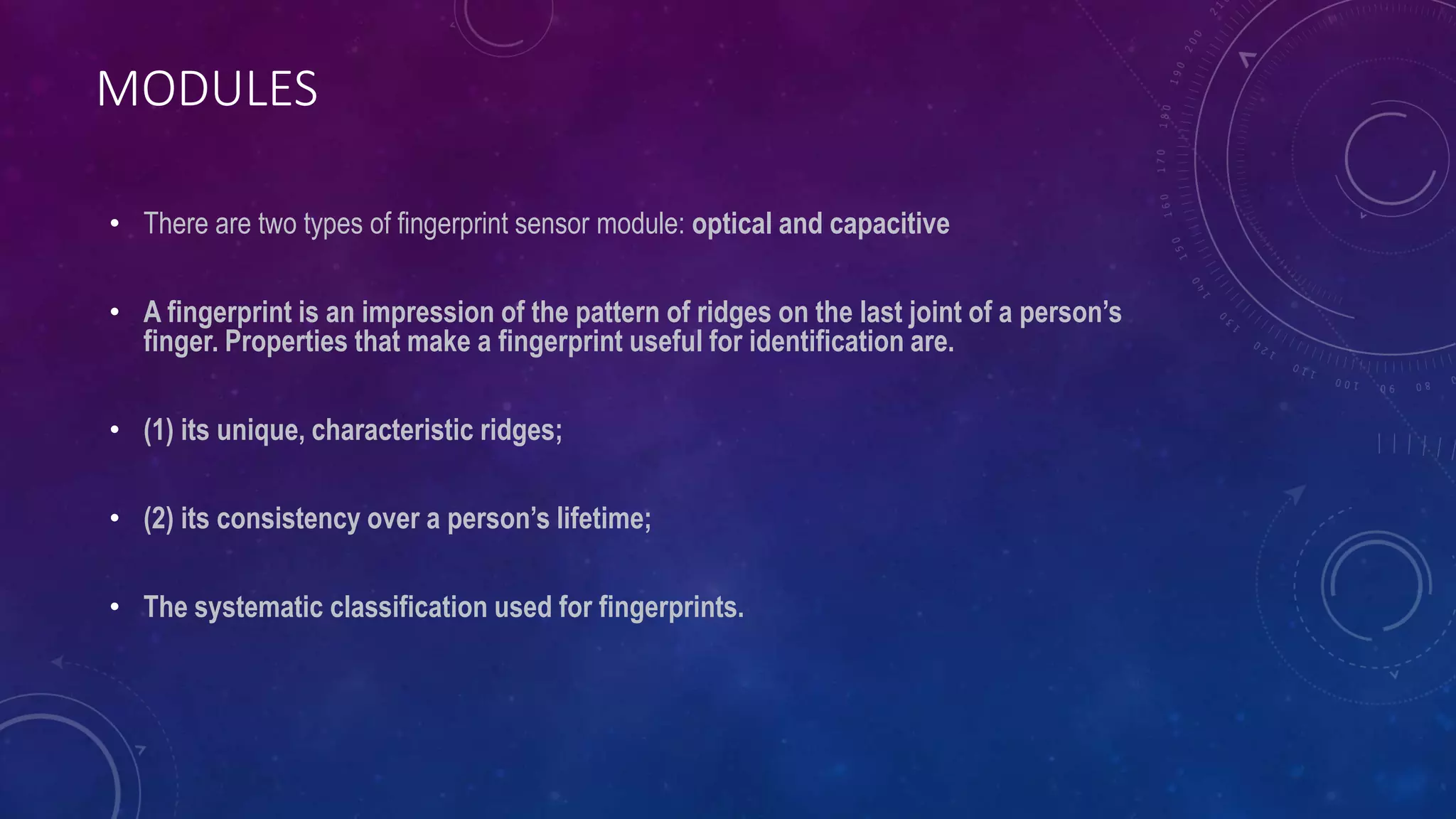
This document discusses a proposed system for storing fingerprint biometric data on blockchain to provide more secure authentication. Currently, biometric data is stored in centralized databases controlled by a single authority, making it vulnerable to attacks. The proposed system would decentralize storage of fingerprint templates using blockchain and InterPlanetary File System (IPFS) to address these security issues. If implemented, the system could provide safe and convenient identification using biometrics while protecting users' fingerprint data.