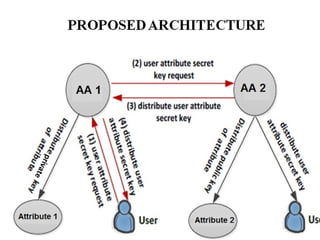
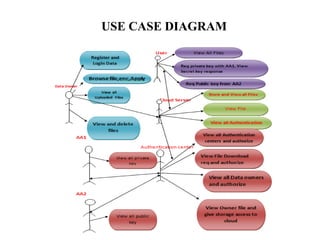
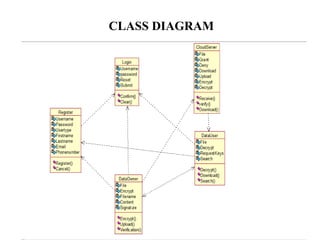
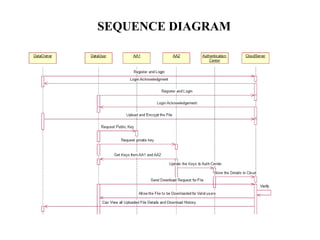
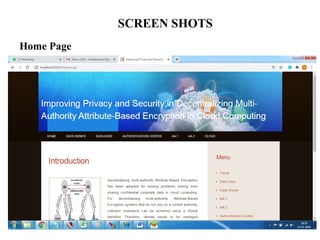
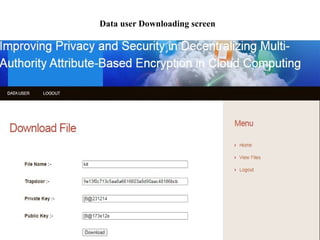
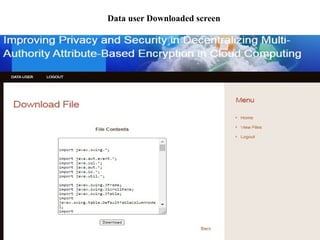
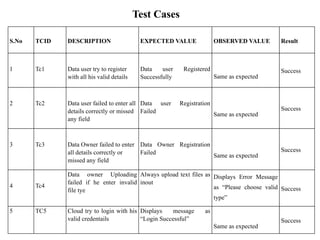
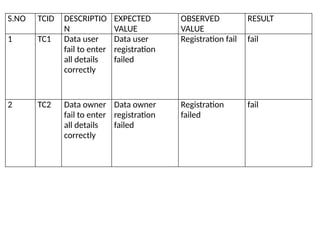
The document proposes a decentralized data storage system using attribute-based encryption to enhance security in cloud environments, addressing the limitations of existing centralized systems. It introduces a global identifier and multi-authority model to facilitate secure access and management of sensitive data. The proposed scheme demonstrates improved efficiency and data protection through encrypted storage and key management for users accessing cloud data.