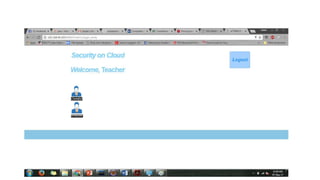
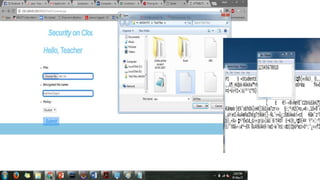
The document presents a project on enhancing cloud security through Attribute-Based Encryption (ABE) to ensure secure authentication. It discusses the limitations of ABE, including inefficiency and expensive decryption, and proposes an improved version with outsourced decryption and verifiability. The project also outlines the implementation of ABE algorithms and presents future scope for a multi-user attribute system in cloud environments.

![• As cloud is widely used for remote access
of information as well as transfer of
information geographically, so there is a
great need of making cloud even more
secure.
• Attribute Based Encryption can help in
increasing the security on cloud.
• ABE is a public-key based one-to-many
encryption that allows users to encrypt
and decrypt data based on user attributes.
Fig 1:Cloud Services[4]](https://image.slidesharecdn.com/finalppt-170611205010/85/Authentication-on-Cloud-using-Attribute-Based-Encryption-2-320.jpg)


![• The concept of ABE was first proposed by Amit Sahai and Brent Waters[1]
Sahai and Waters gave two concepts
1. IBE: Concept uses Biometric Identities.
2. Attribute based Encryption: Encrypt a document to all users that have
certain set of attributes.
Contd…](https://image.slidesharecdn.com/finalppt-170611205010/85/Authentication-on-Cloud-using-Attribute-Based-Encryption-5-320.jpg)
![Although ABE concept is very powerful and a promising mechanism, ABE systems suffer mainly from
two drawbacks:
• Non-efficiency.
• proposal was much expensive decryption.
Fig 2: ABE scheme[4]
OR](https://image.slidesharecdn.com/finalppt-170611205010/85/Authentication-on-Cloud-using-Attribute-Based-Encryption-6-320.jpg)
![In order to reduce the cost of Decryption Lia[2] suggested to outsource the
majority of actual data without revealing private key.
Considering a new requirement of ABE with outsourced decryption: Modifying
the original model of ABE with outsourced decryption proposed by Green to
include verifiability.
A concrete ABE scheme with outsourced decryption and proved that it is secure.
Lin[3] proposed an algorithm that provided a decryption algorithm for ABE,
whose computational time and cost was half as that of traditional decryption
algorithm of ABE.
Contd…](https://image.slidesharecdn.com/finalppt-170611205010/85/Authentication-on-Cloud-using-Attribute-Based-Encryption-7-320.jpg)
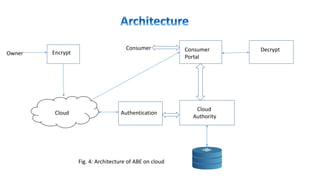
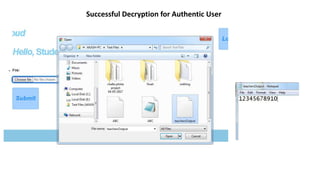
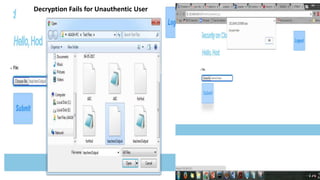
![If receiver wants to download the file, they have to send request to cloud proxy server.
When proxy server will verify receiver then server will ask for transformation key. This
key will be generated through the attributes of receiver.
Transformation key is used for transforming cipher text into simpler cipher text.
Now simpler cipher text is send to receiver who decrypt simpler cipher text into plain text
using receiver secret key.
Fig:3 System Architecture[2]](https://image.slidesharecdn.com/finalppt-170611205010/85/Authentication-on-Cloud-using-Attribute-Based-Encryption-8-320.jpg)







![Fig 4: Comparison with other technique[6]](https://image.slidesharecdn.com/finalppt-170611205010/85/Authentication-on-Cloud-using-Attribute-Based-Encryption-24-320.jpg)

![[1] A. Sahai and B. Waters, “Fuzzy identity-based encryption,” International
Association for Cryptologic Research, Springer,2005.
[2] J. Lai, R. H. Deng, C. Guan, and J. Weng, “Attribute-based encryption
with verifiable outsourced decryption,” IEEE Trans. Inf. Forensics Security,
vol. 8, no. 8, pp. 1343–1354, Aug. 2013.
[3] Suqing Lin, Rui Zhang, Hui Ma, and Mingsheng Wang,“Revisiting
Attribute-Based Encryption With Verifiable Outsourced Decryption“, IEEE
Transactions On Information Forensics And Security, Vol. 10, No. 10, Feb
2016](https://image.slidesharecdn.com/finalppt-170611205010/85/Authentication-on-Cloud-using-Attribute-Based-Encryption-27-320.jpg)
![[4] http://cloudcomputingvilla.com/how-does-cloud-computing-work/
[5] http://ualr.edu/sxyu1/cloud.htm
[6] P.Madhubala, Dr.P.Thangaraj ,” Comprehensive and Comparative Analysis of
Cryptographic Solutions in Cloud,” International Journal of Innovative Research in
Computer and Communication Engineering, Vol. 2, Issue 10, October 2014
[7] Eric Zavattoni, Luis J. Dominguez Perez, Shigeo Mitsunari, Ana H. S´anchez-
Ram´ırez, Tadanori Teruya, and Francisco Rodr´ıguez-Henr´ıquez, ”Software
implementation of an Attribute-Based Encryption scheme,” IEEE Transactions on
Computers, May 2015](https://image.slidesharecdn.com/finalppt-170611205010/85/Authentication-on-Cloud-using-Attribute-Based-Encryption-28-320.jpg)
