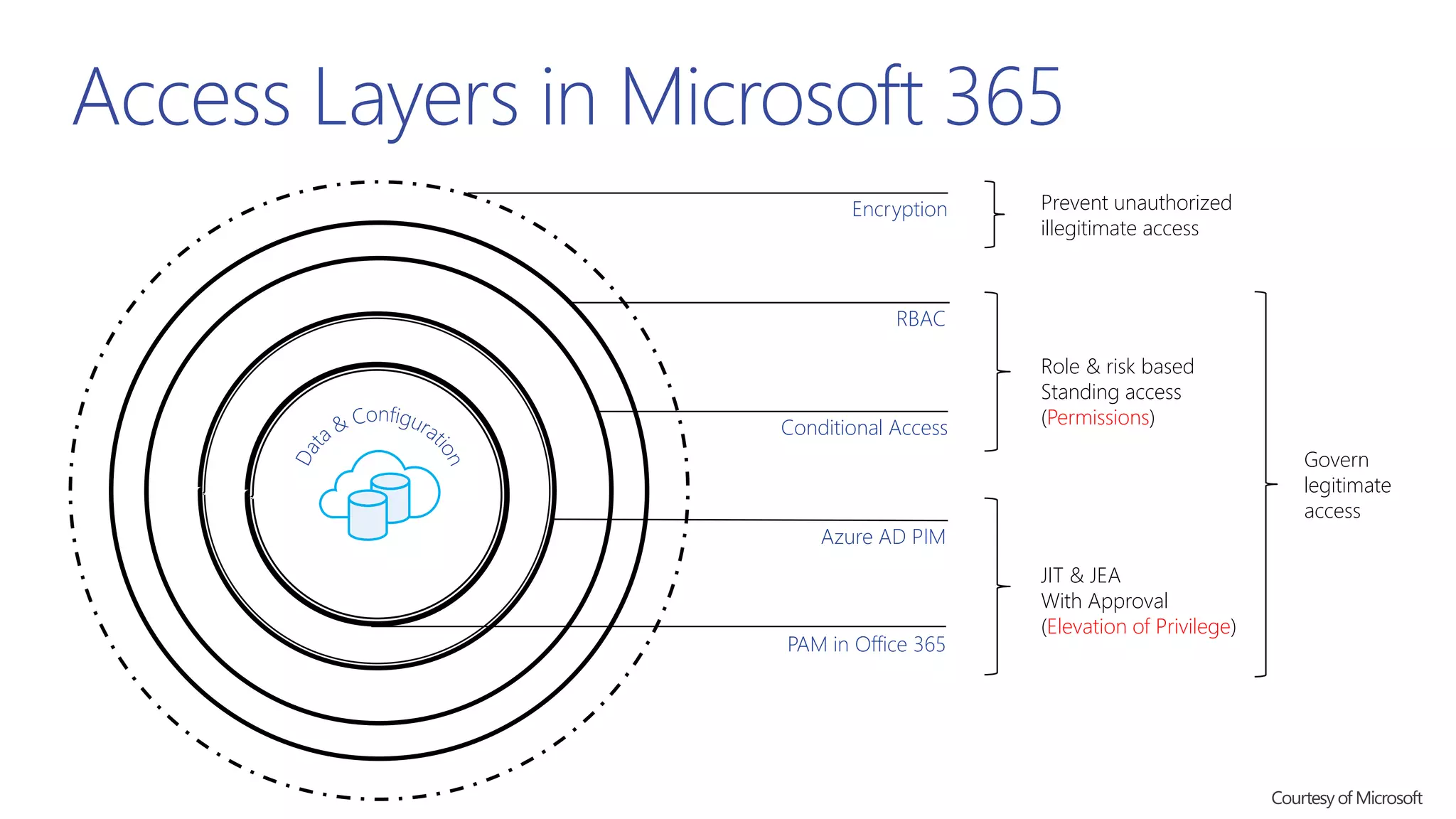
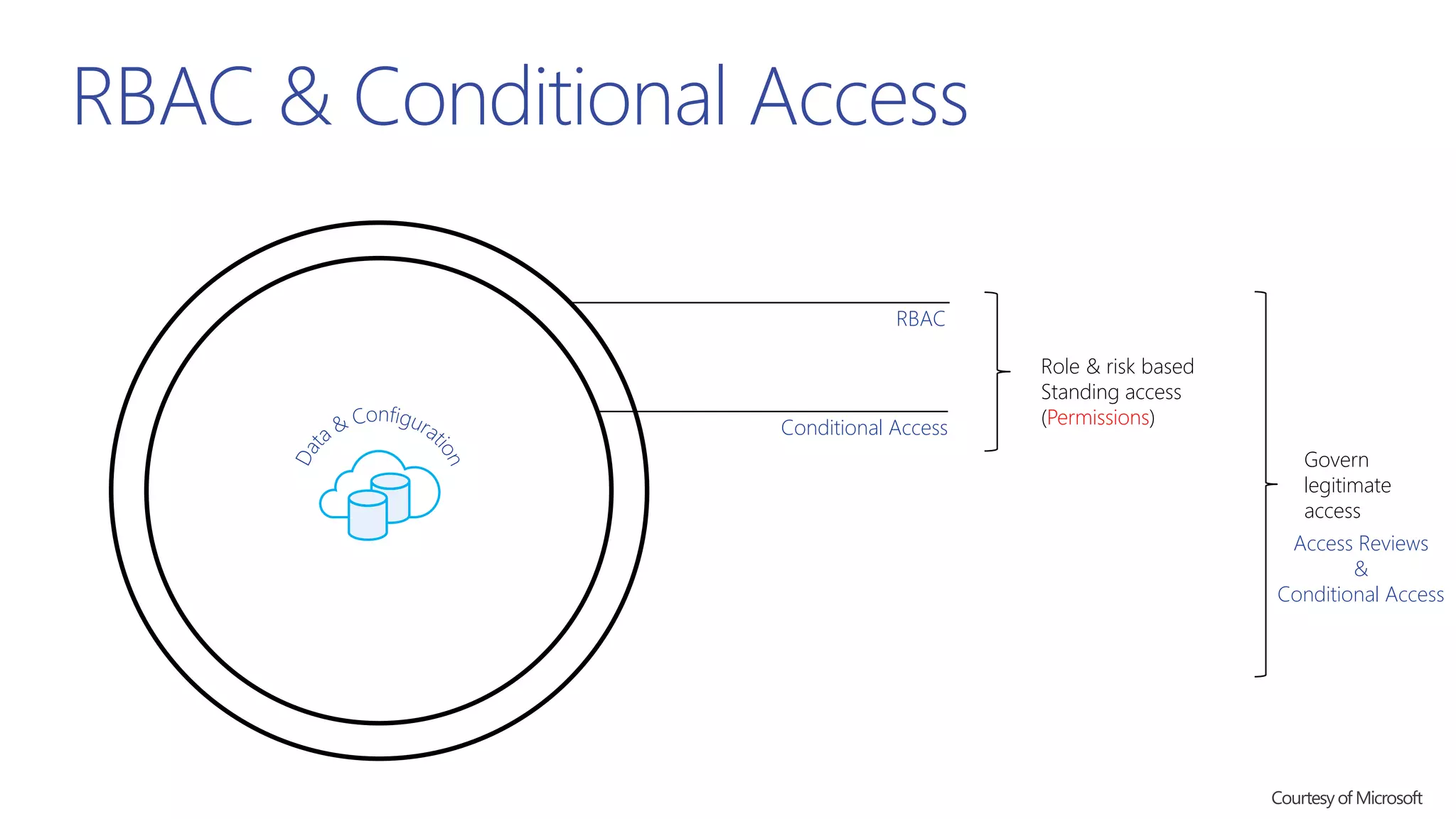
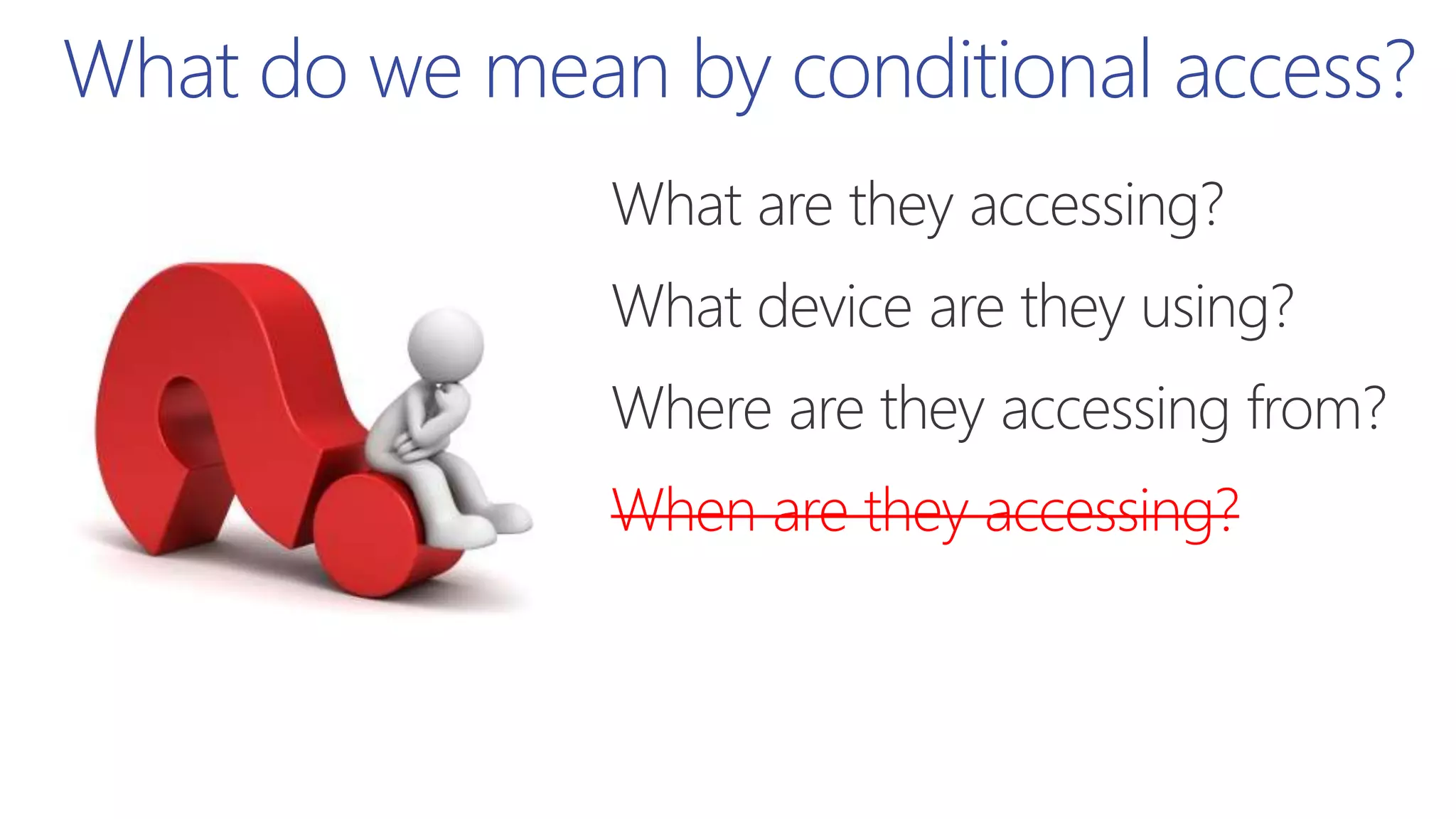
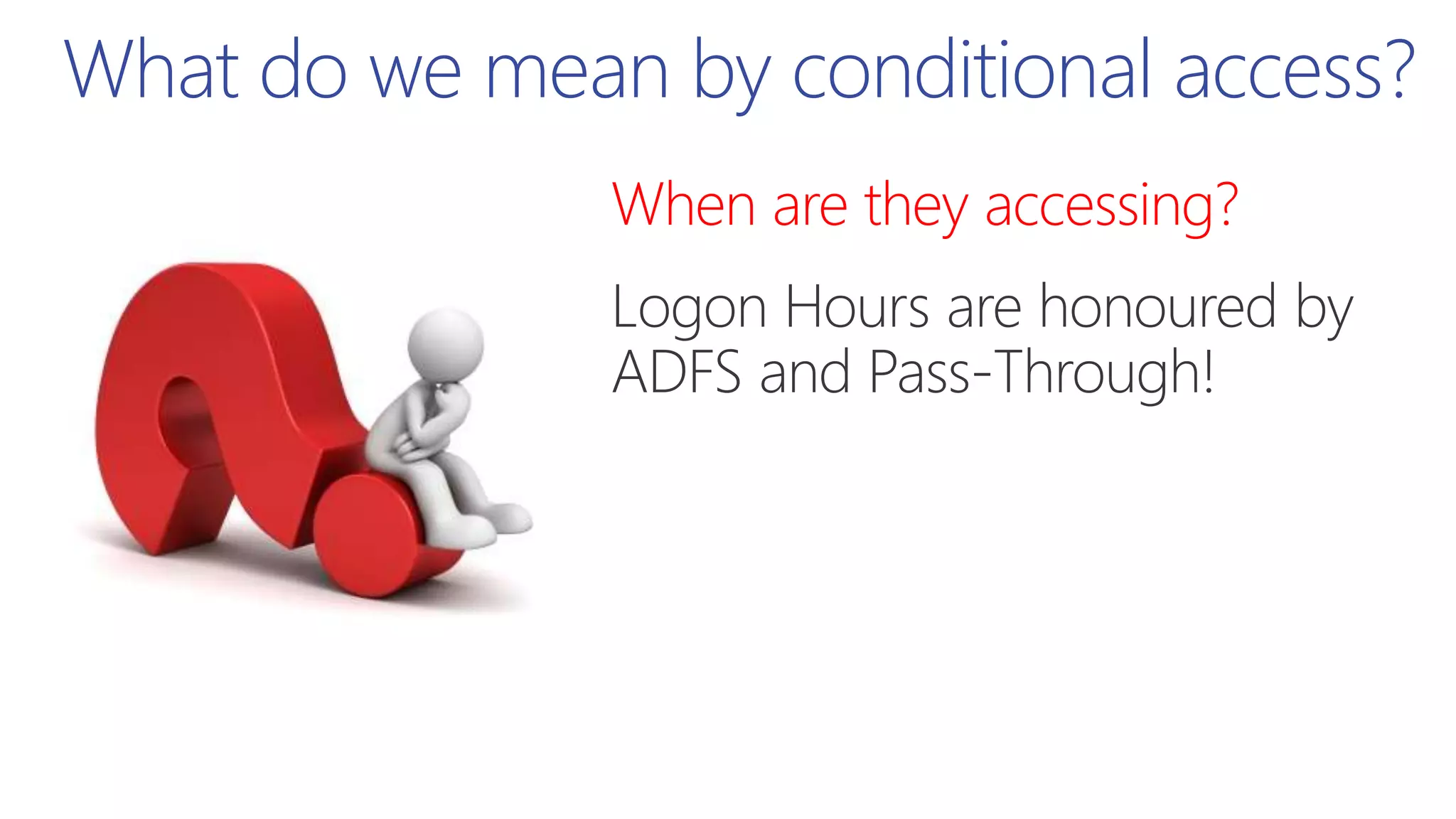
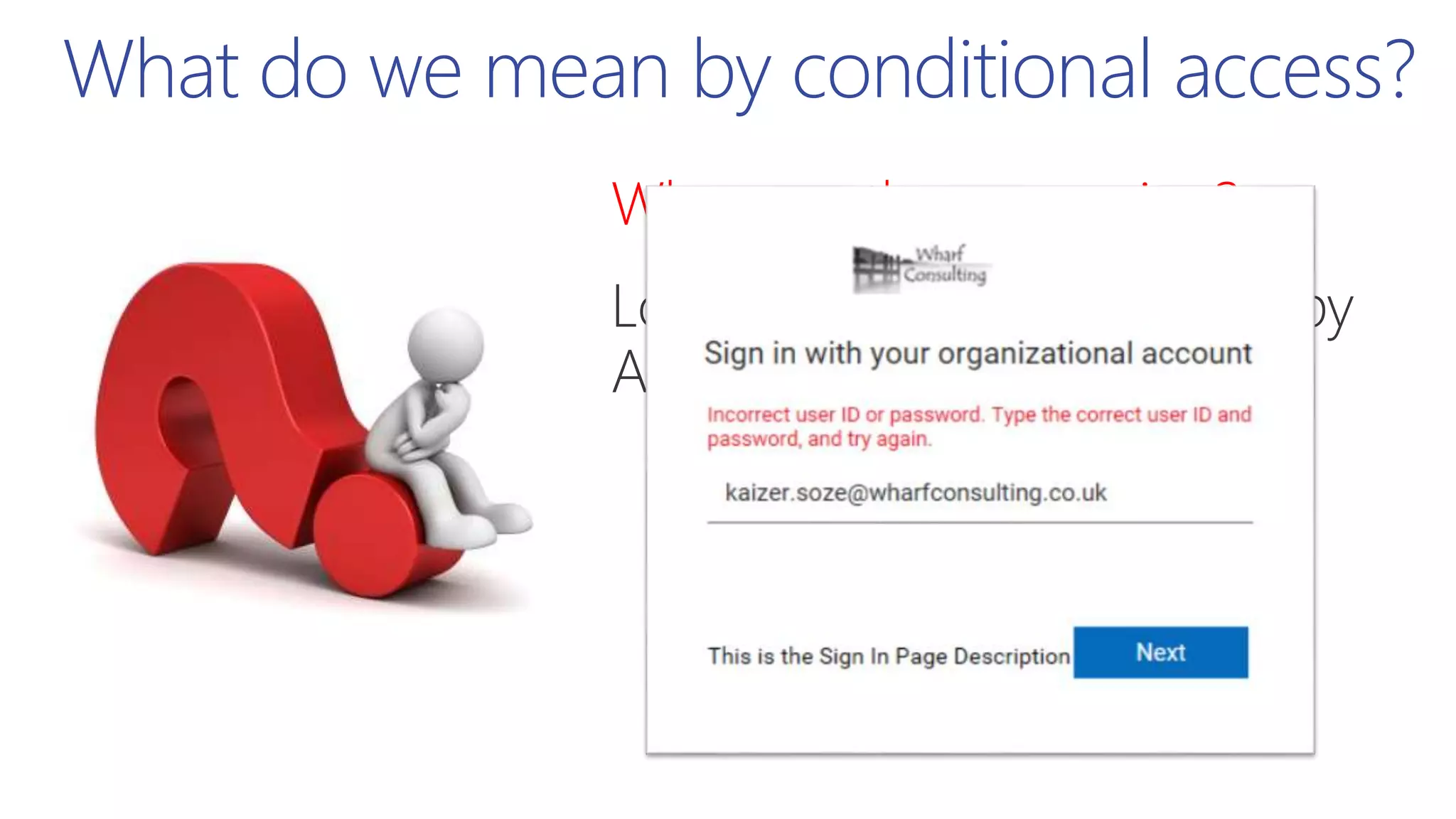
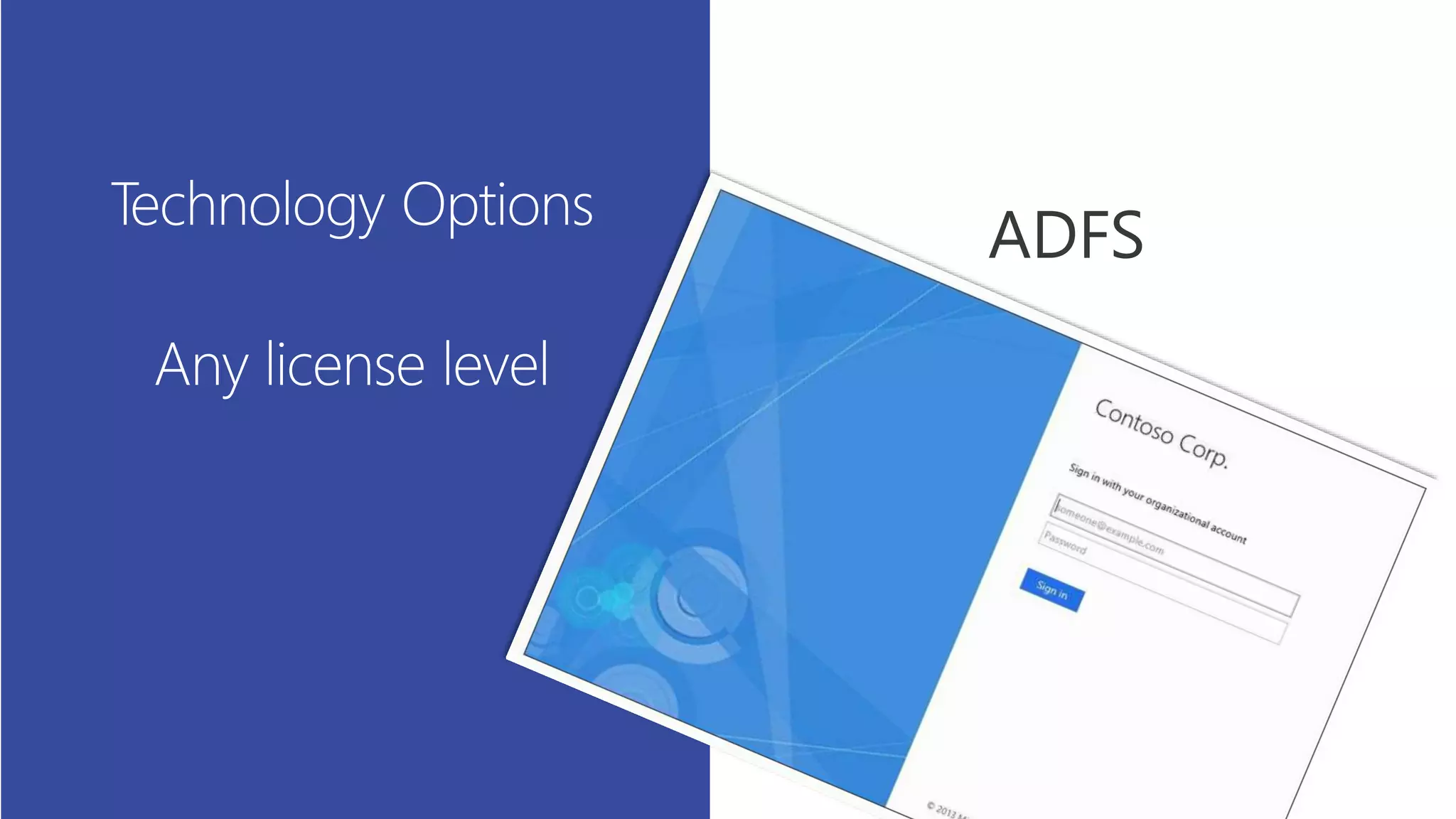
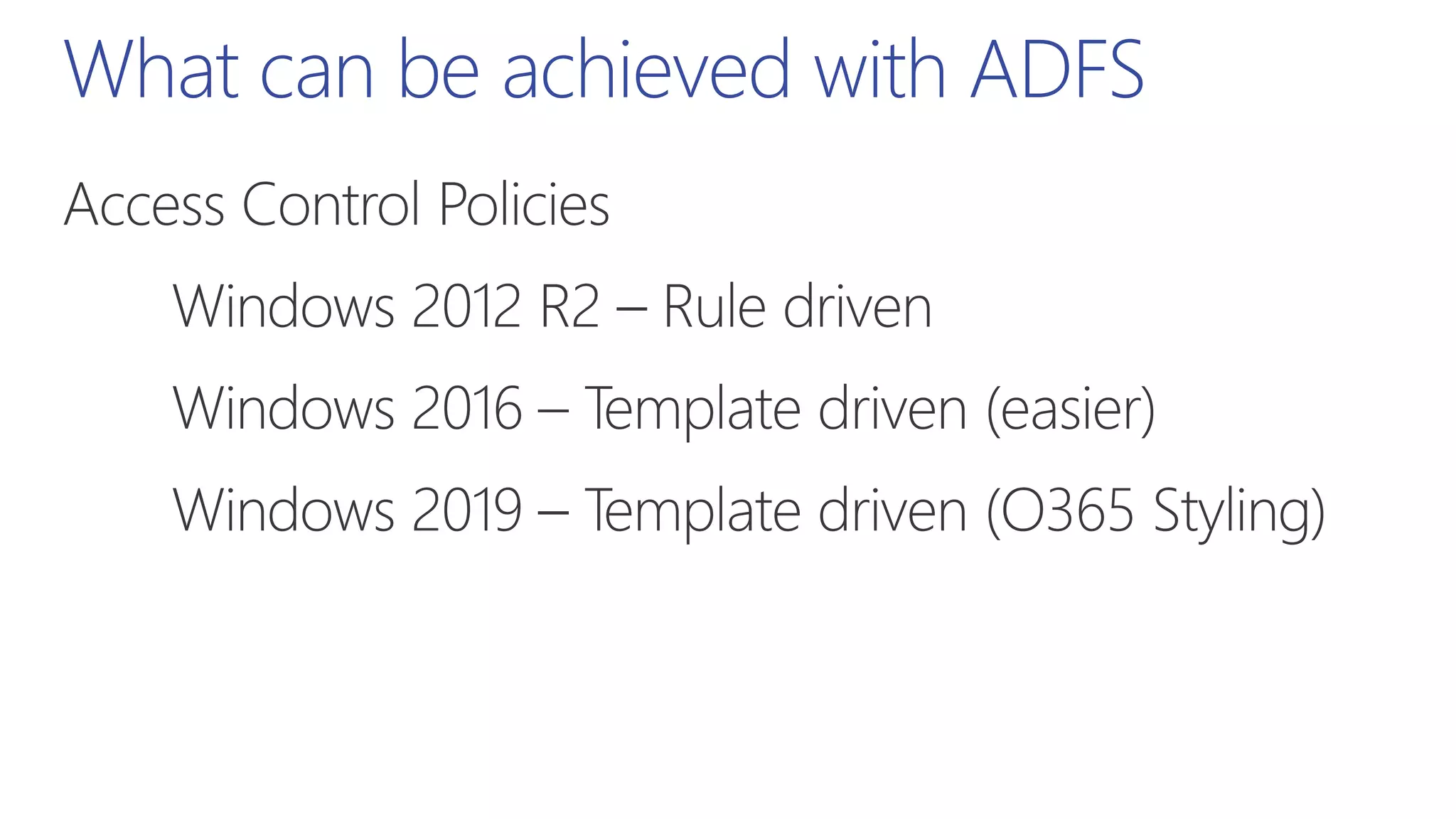
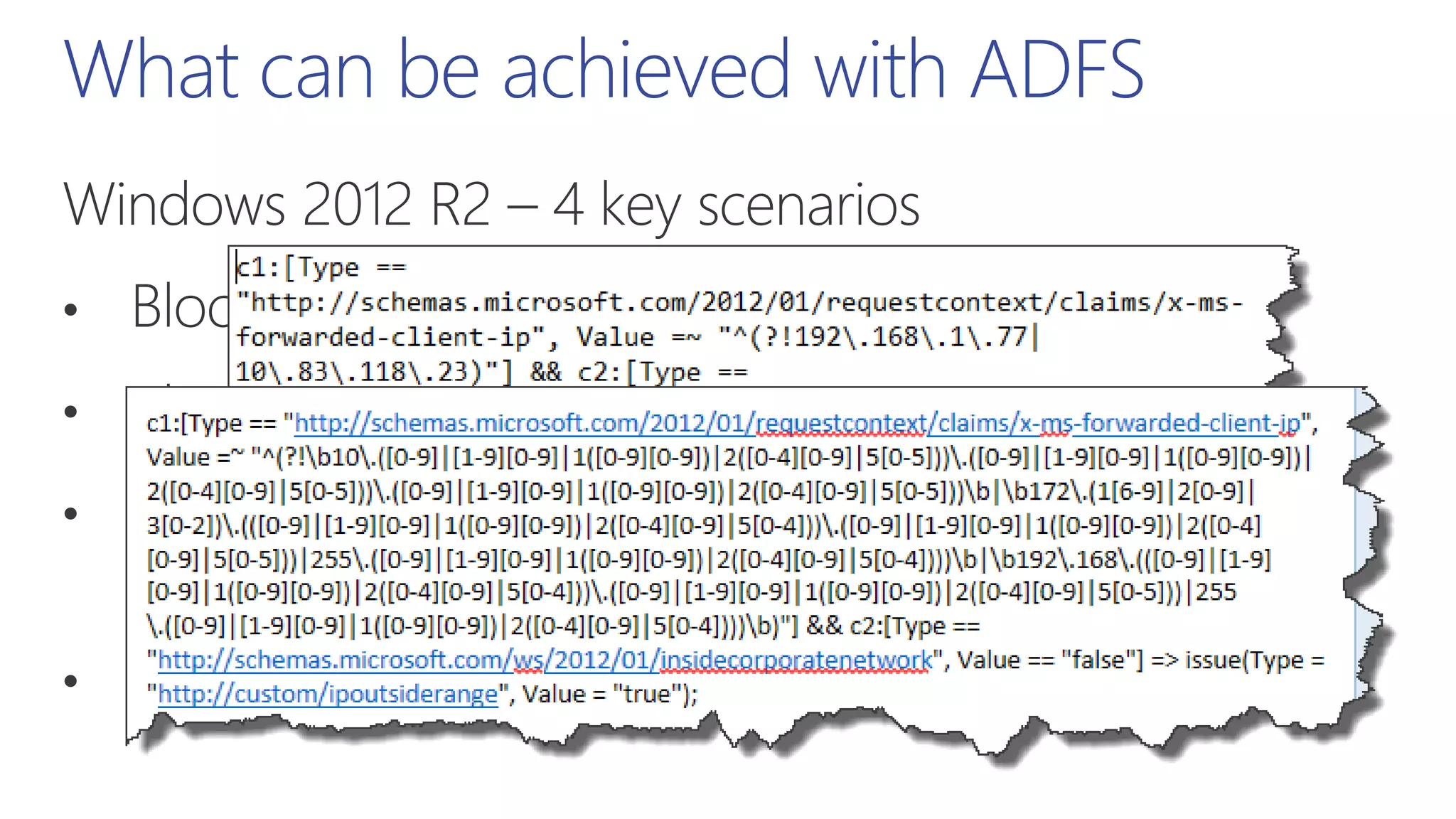
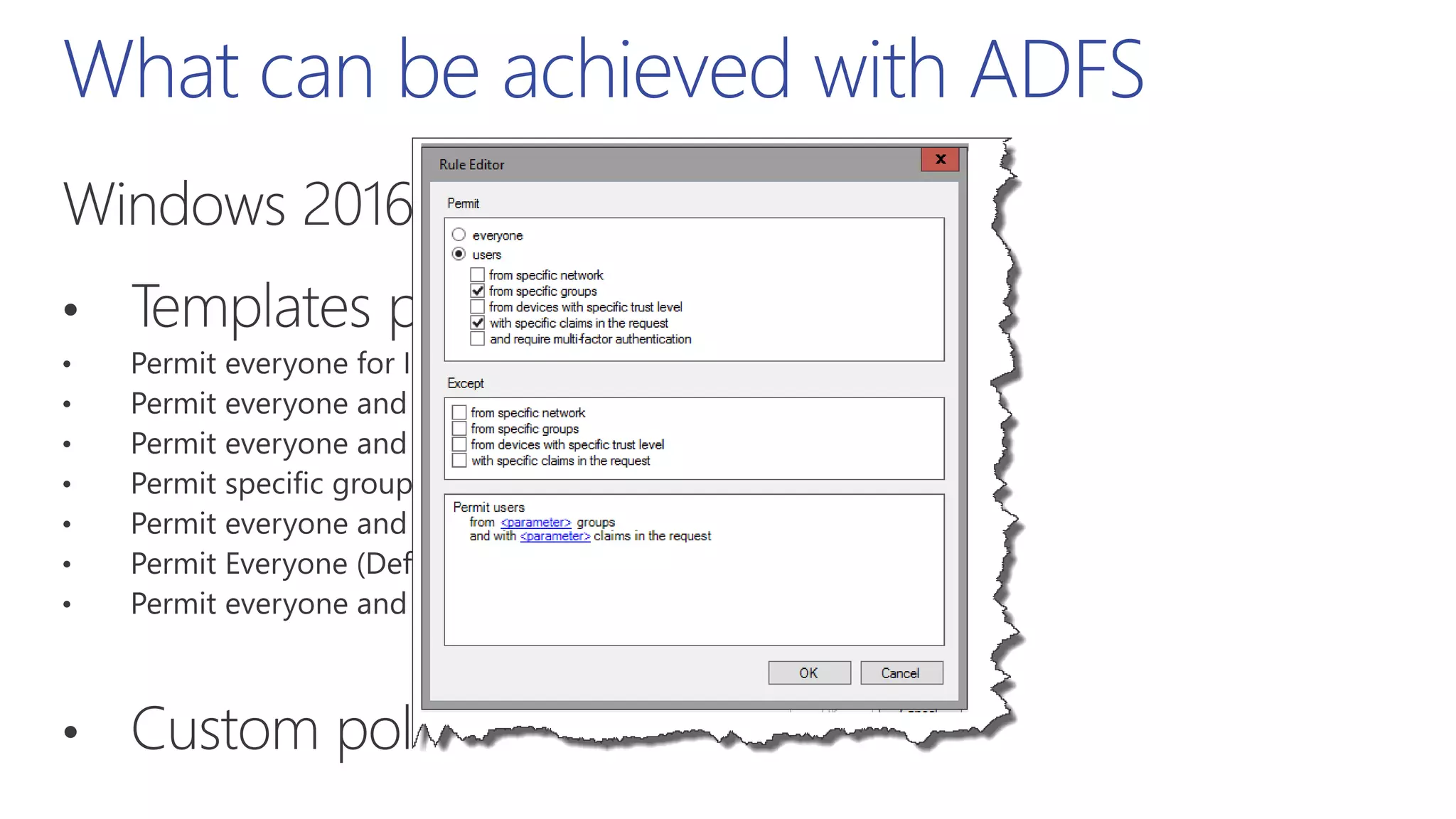
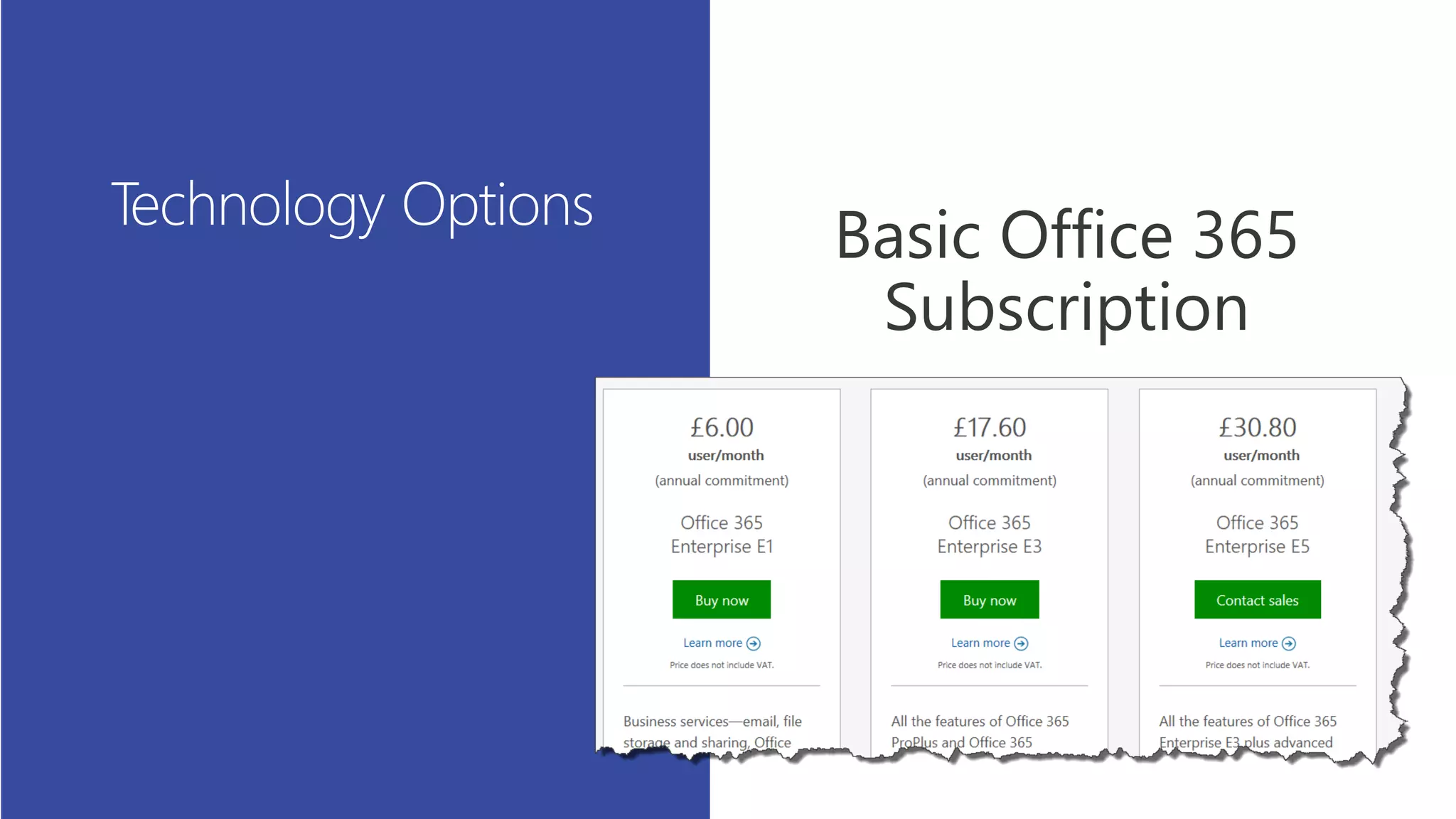
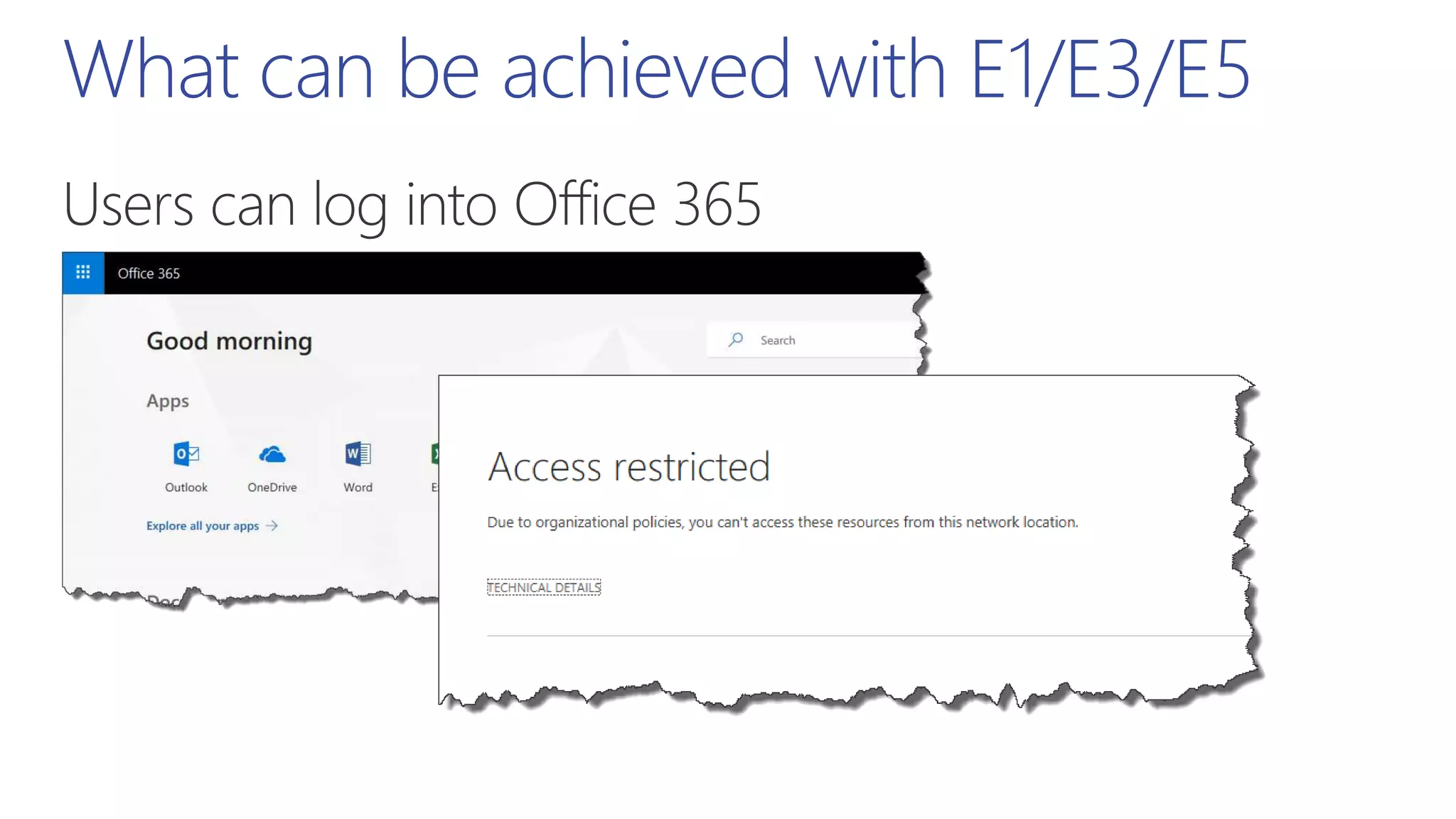
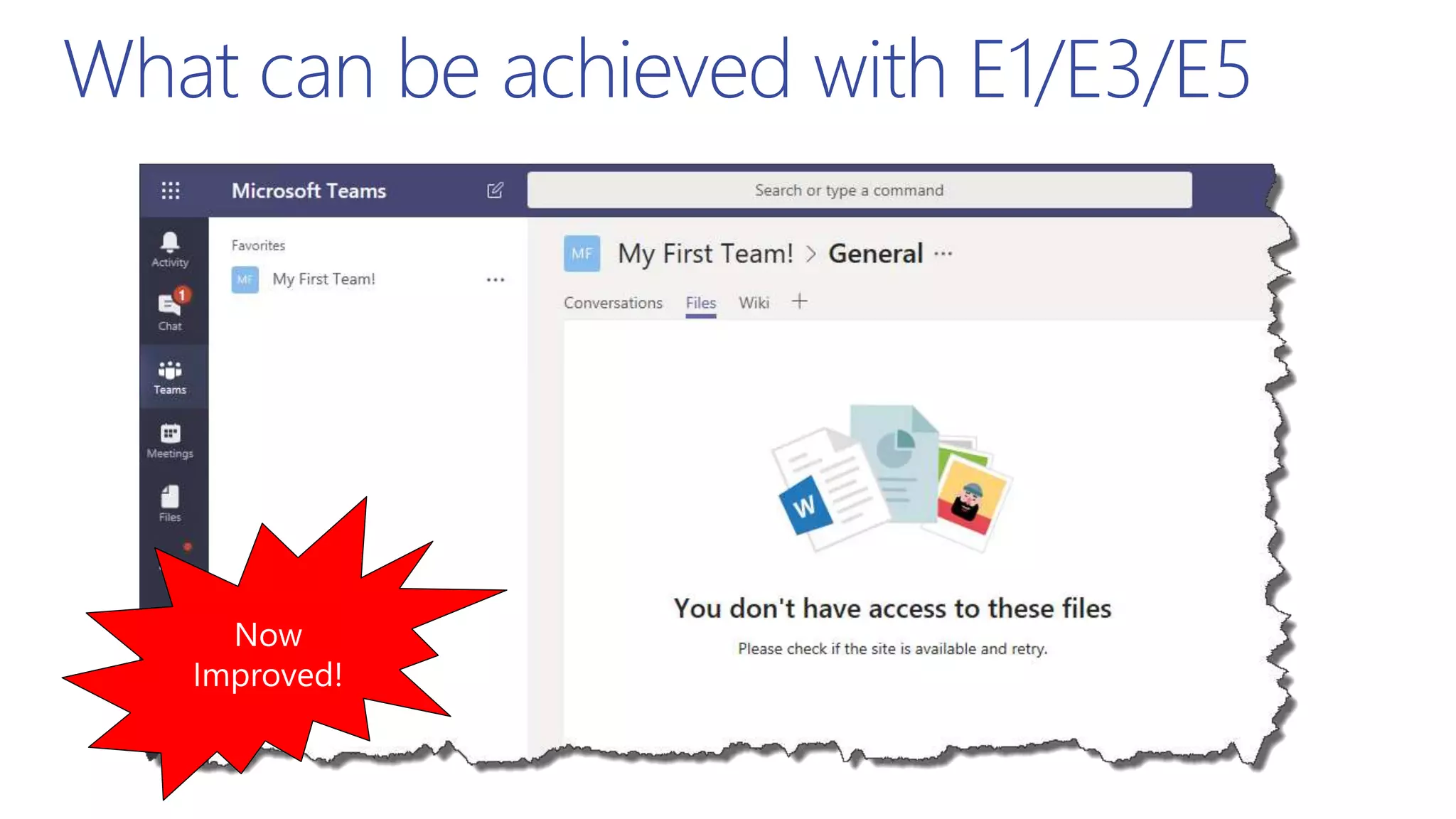
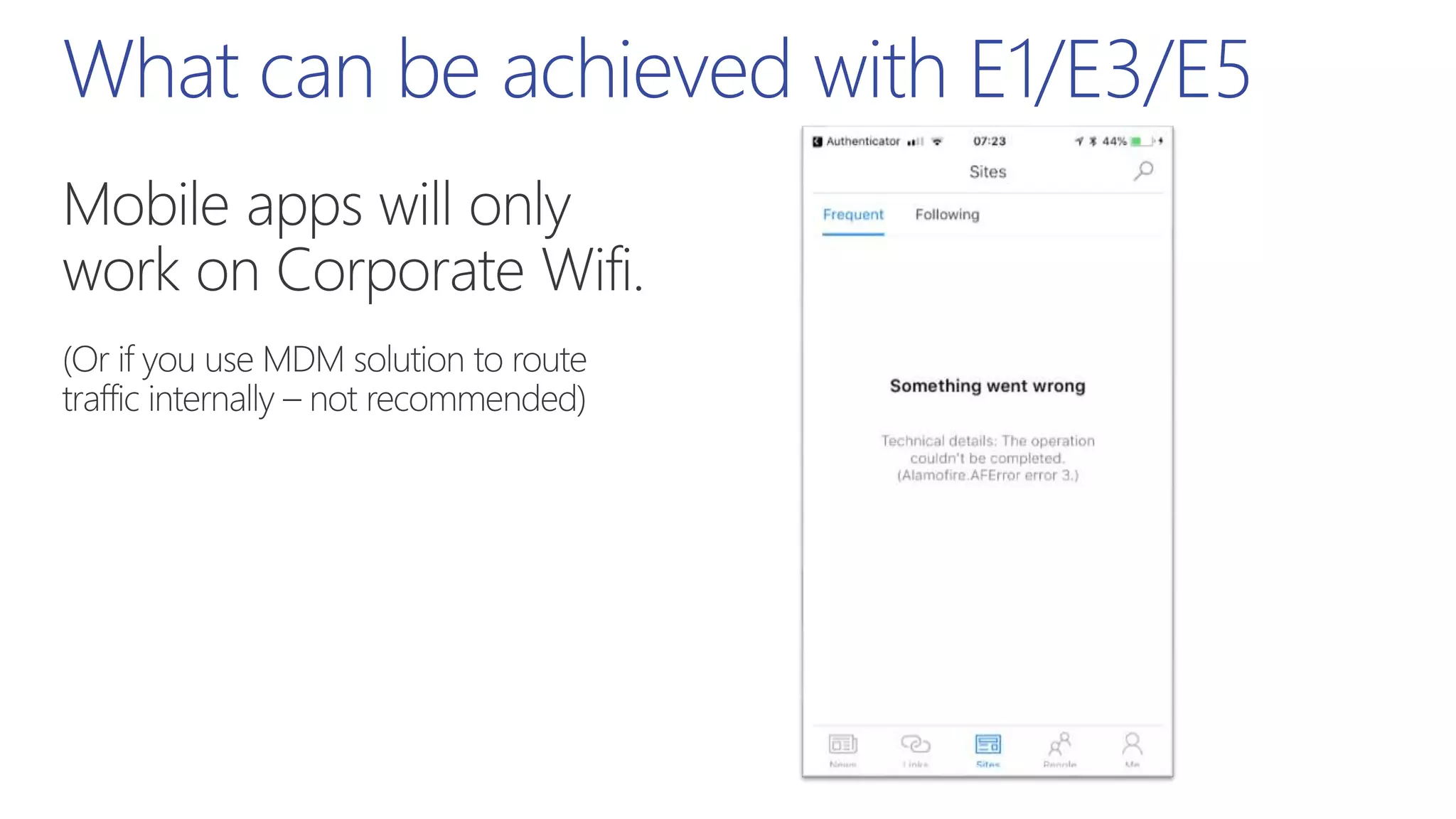
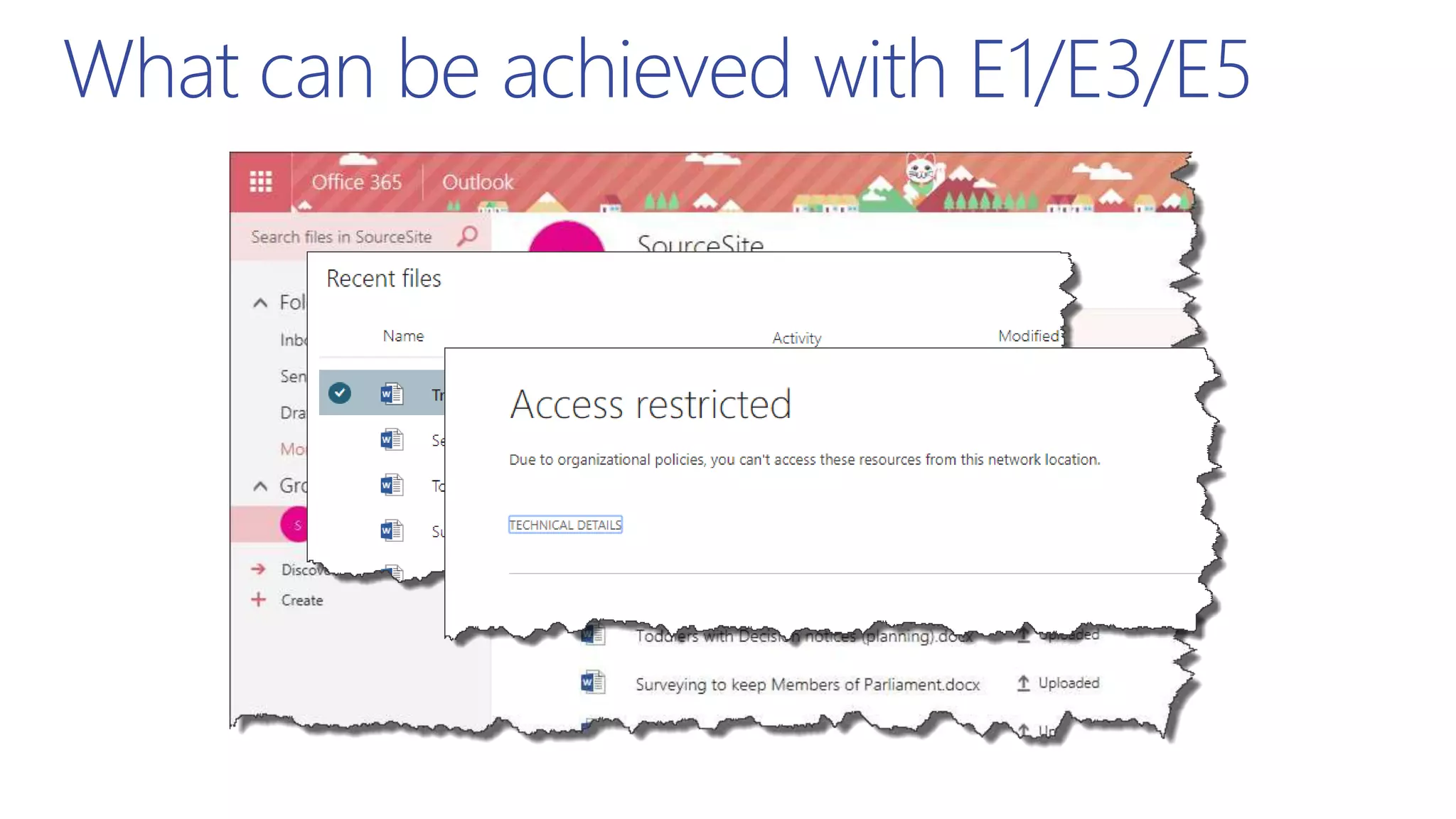
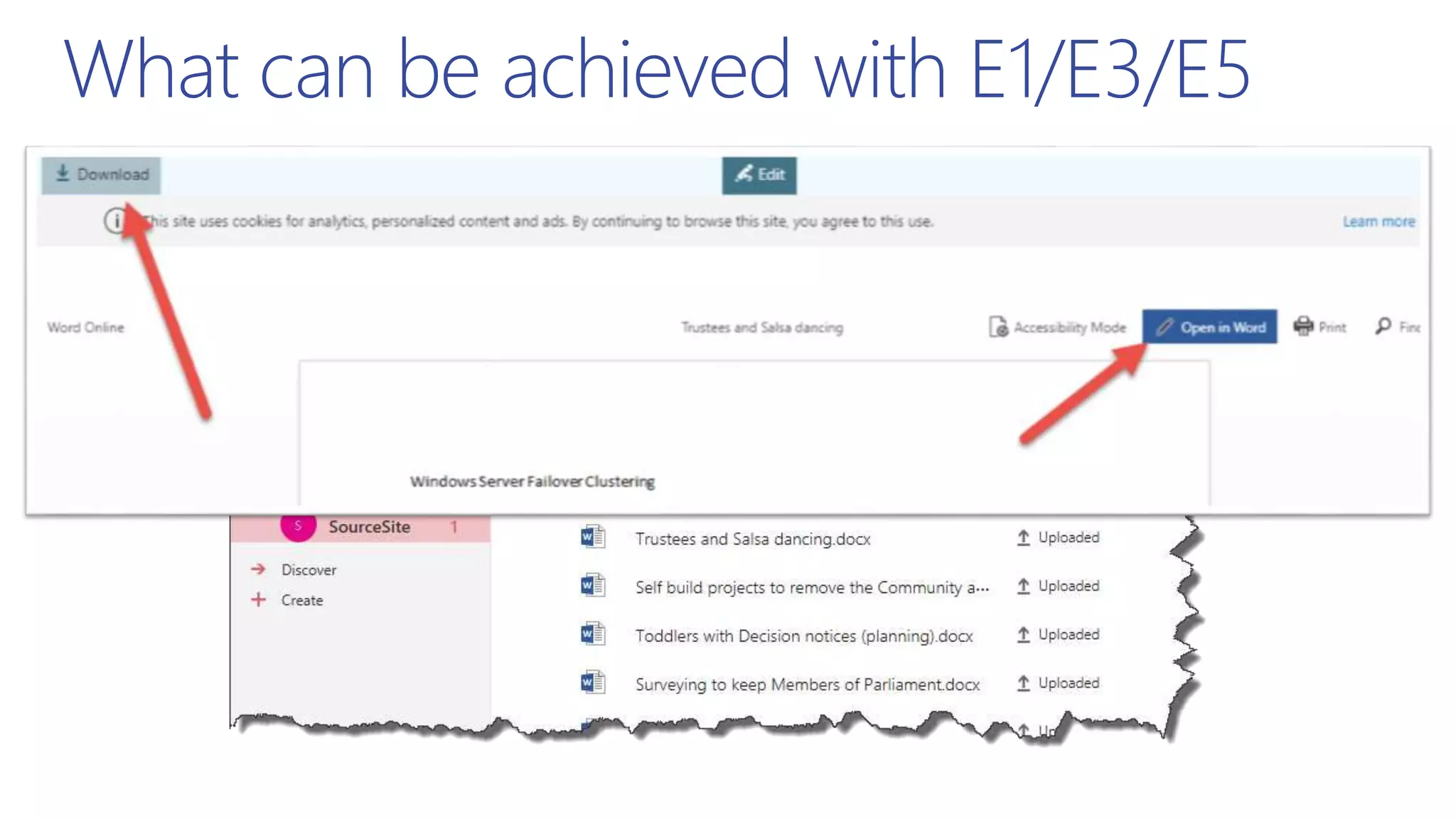
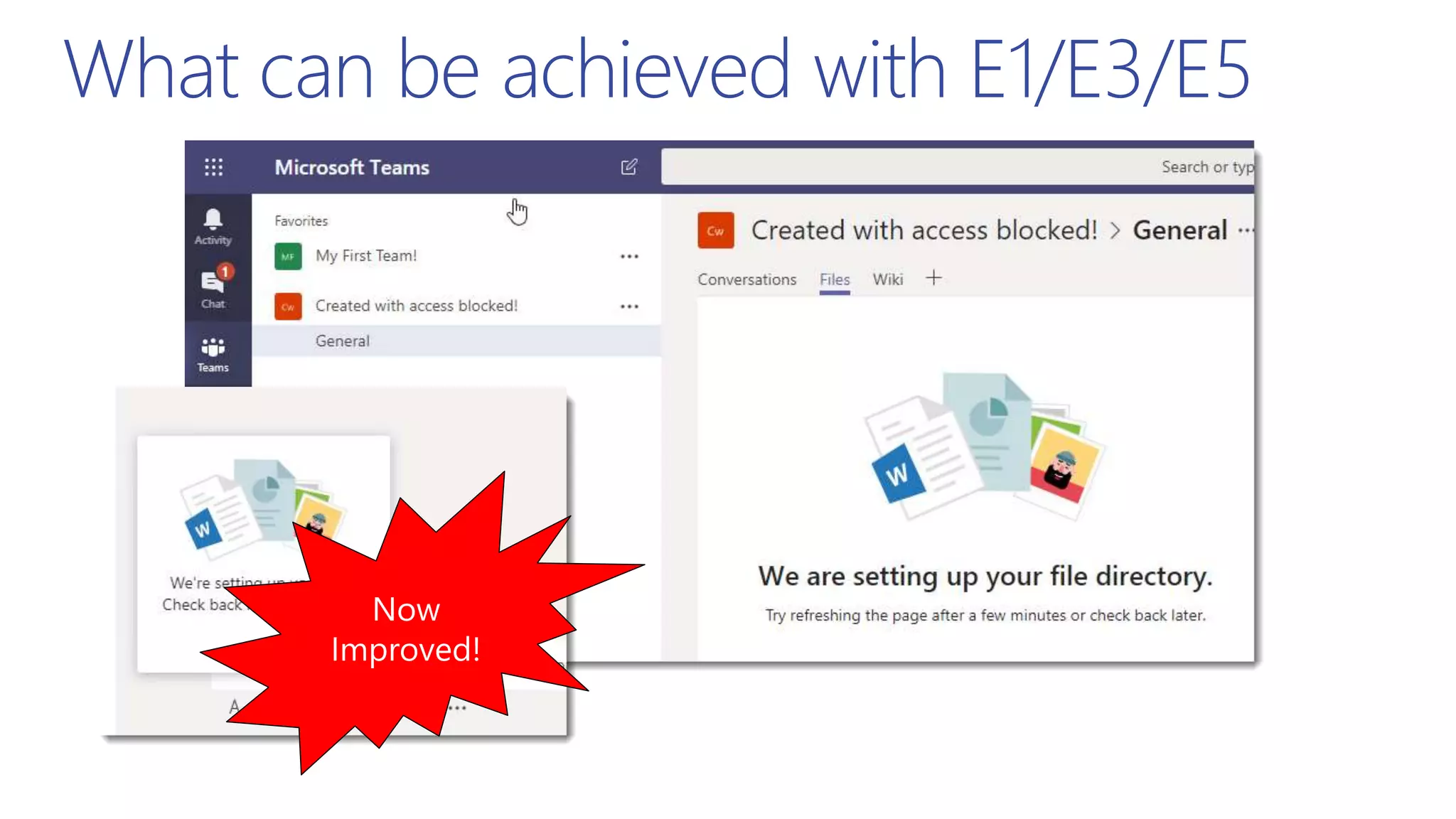
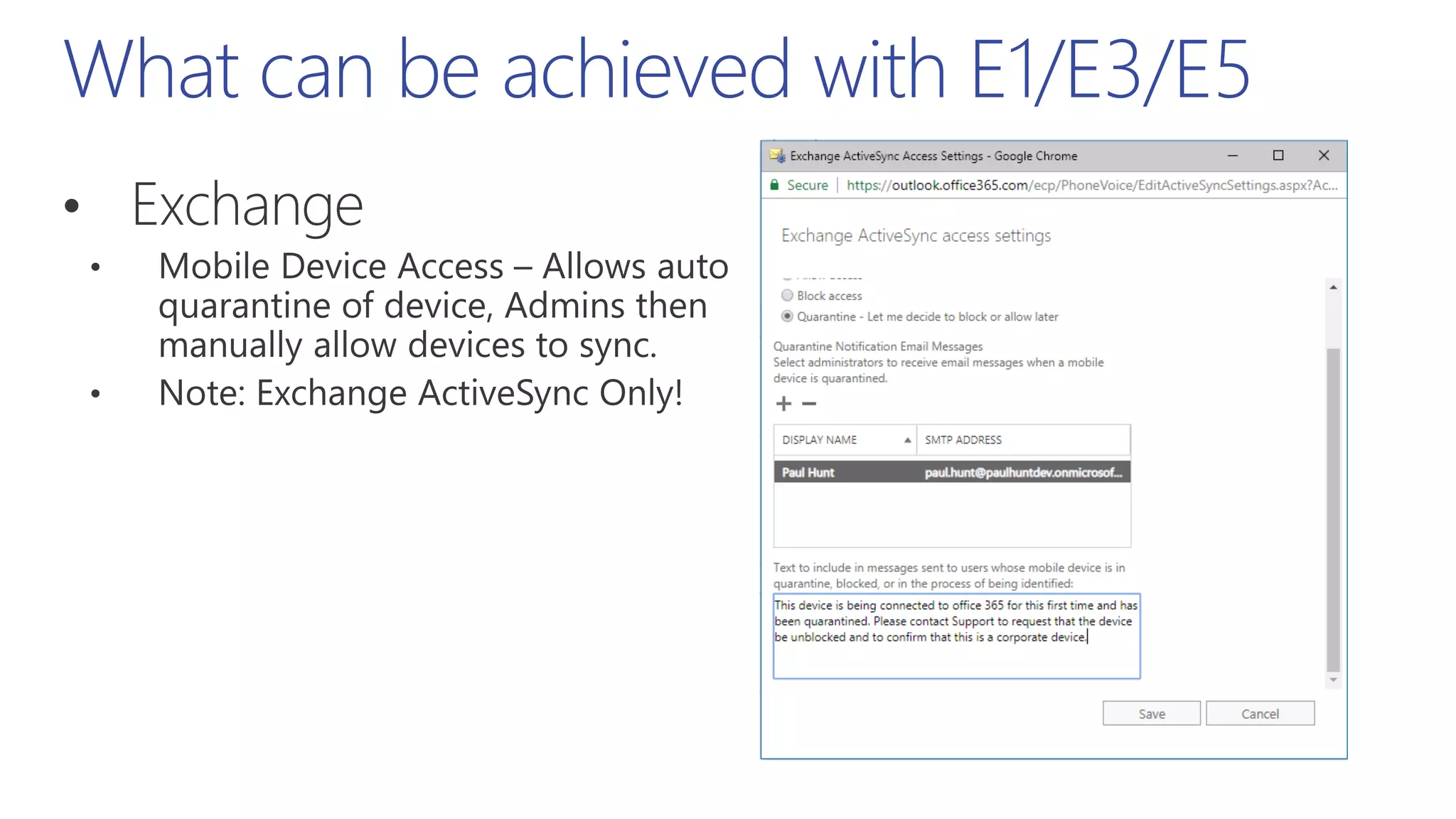
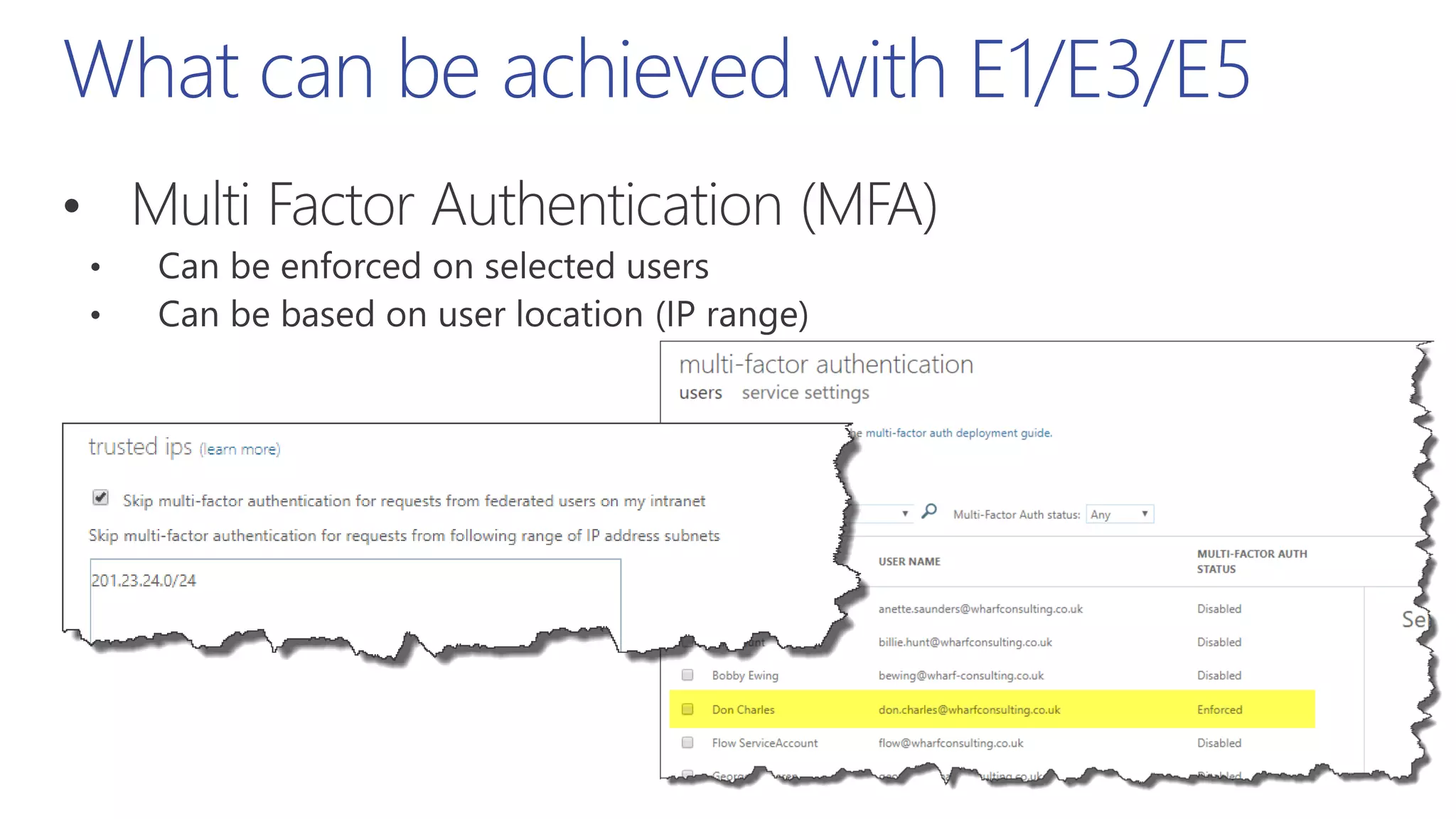
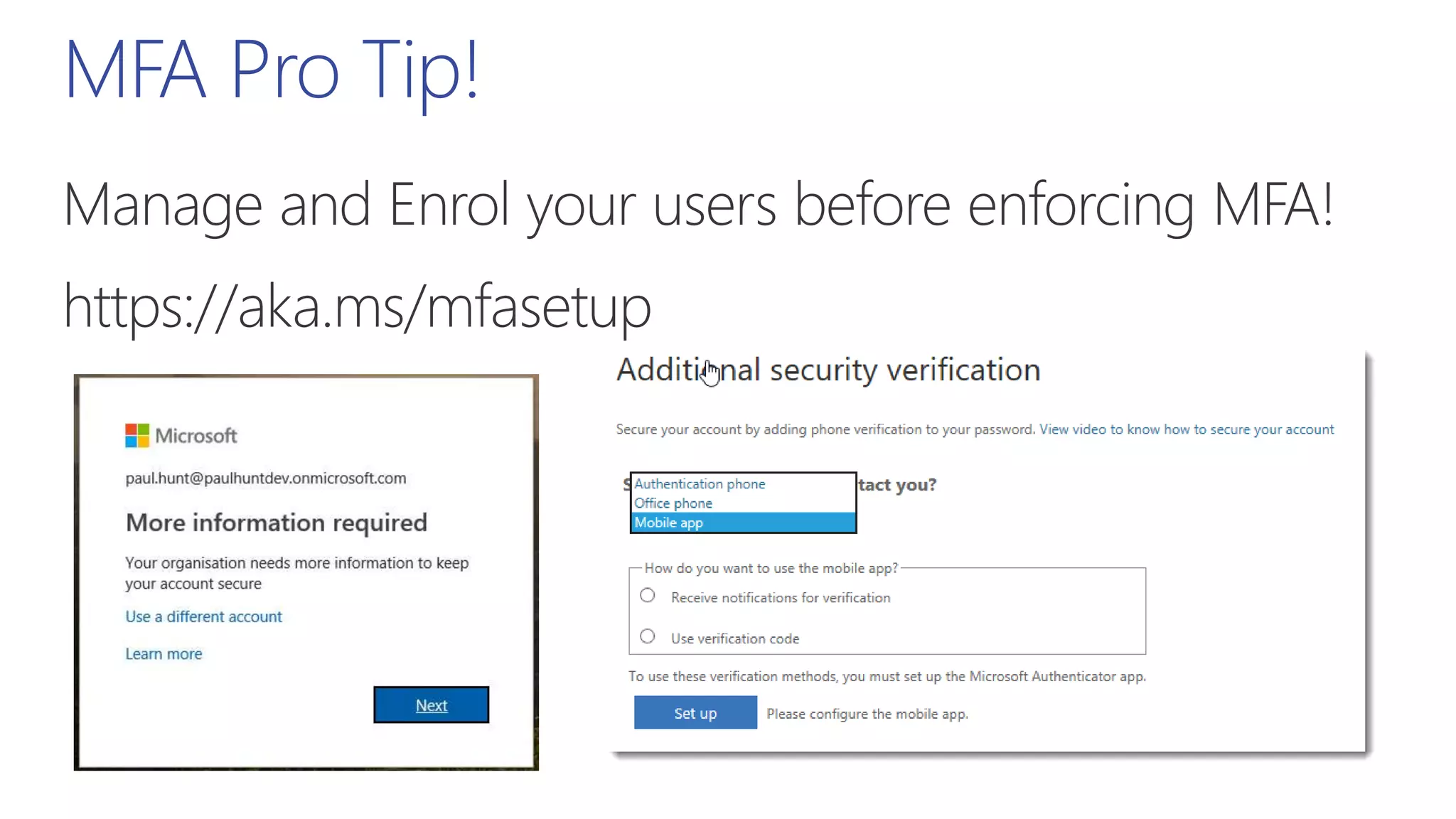
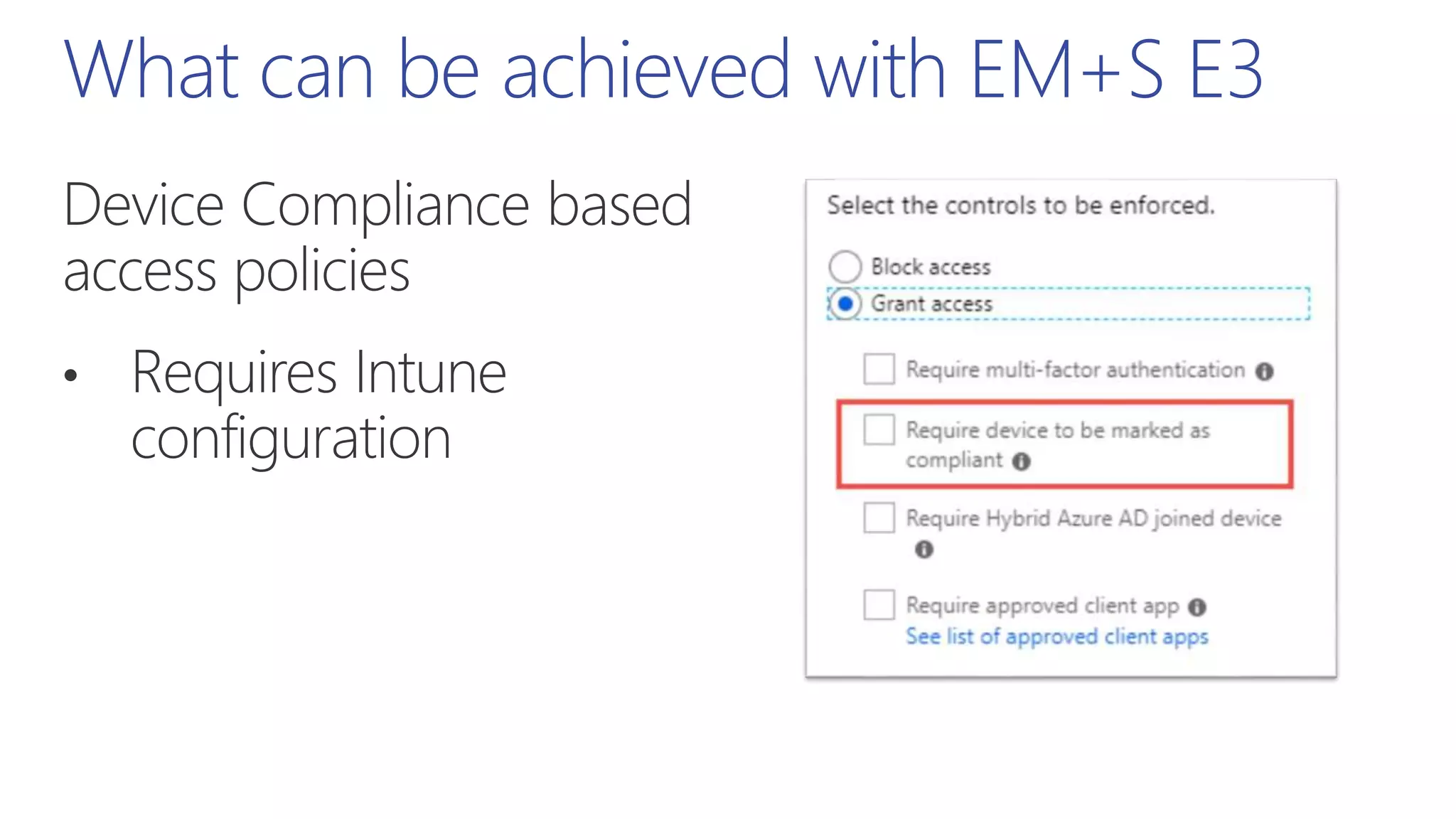
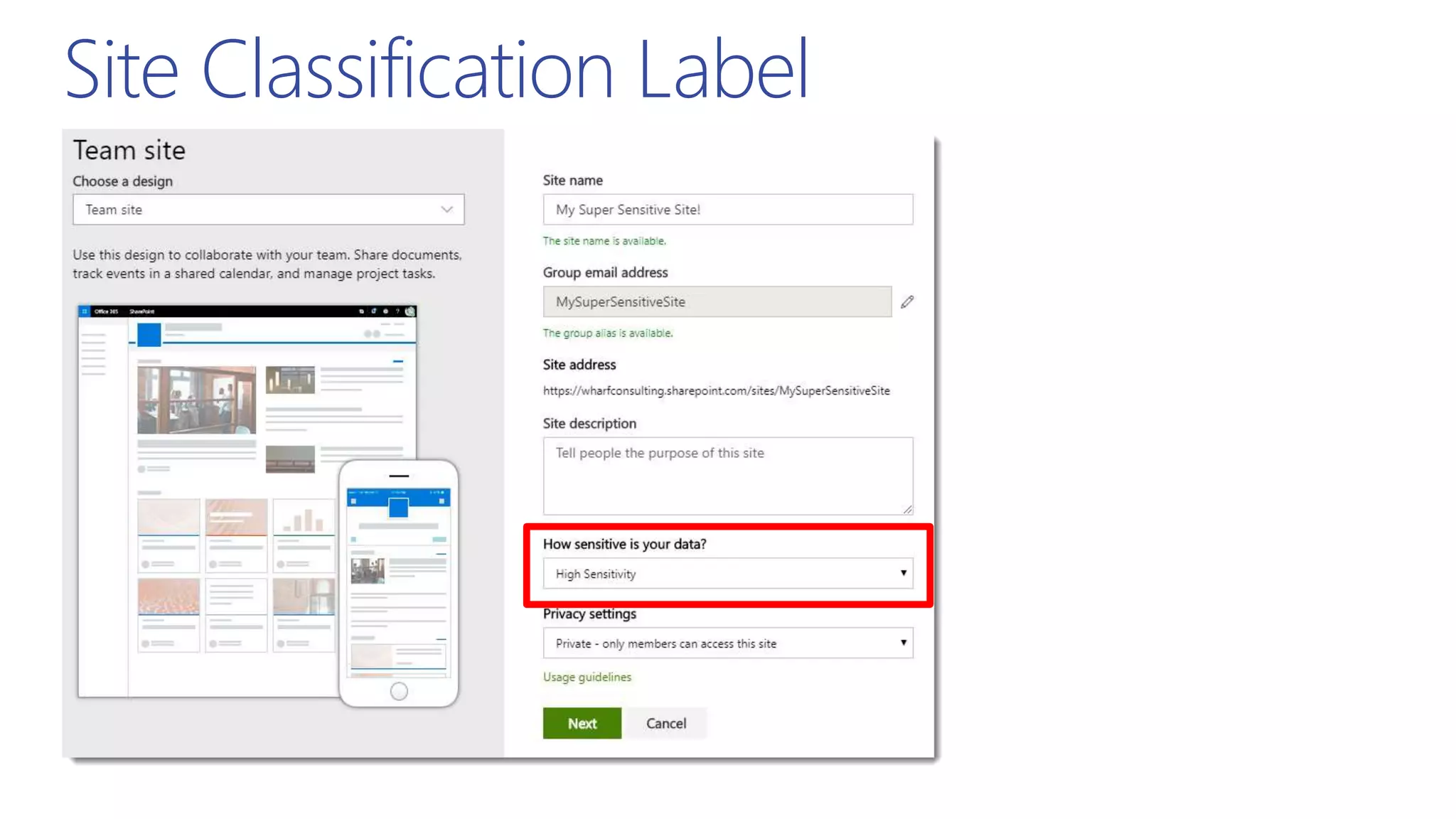
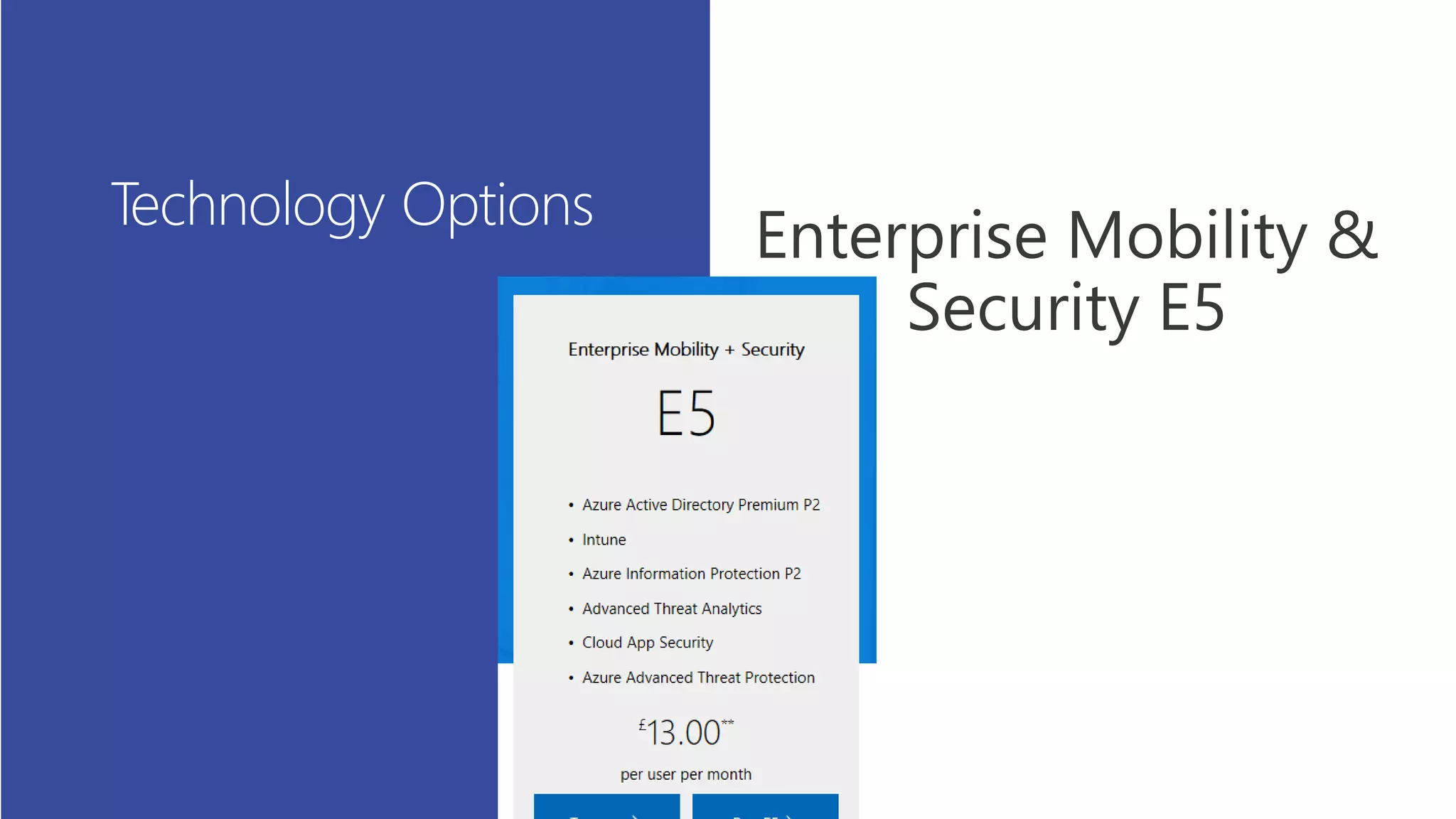
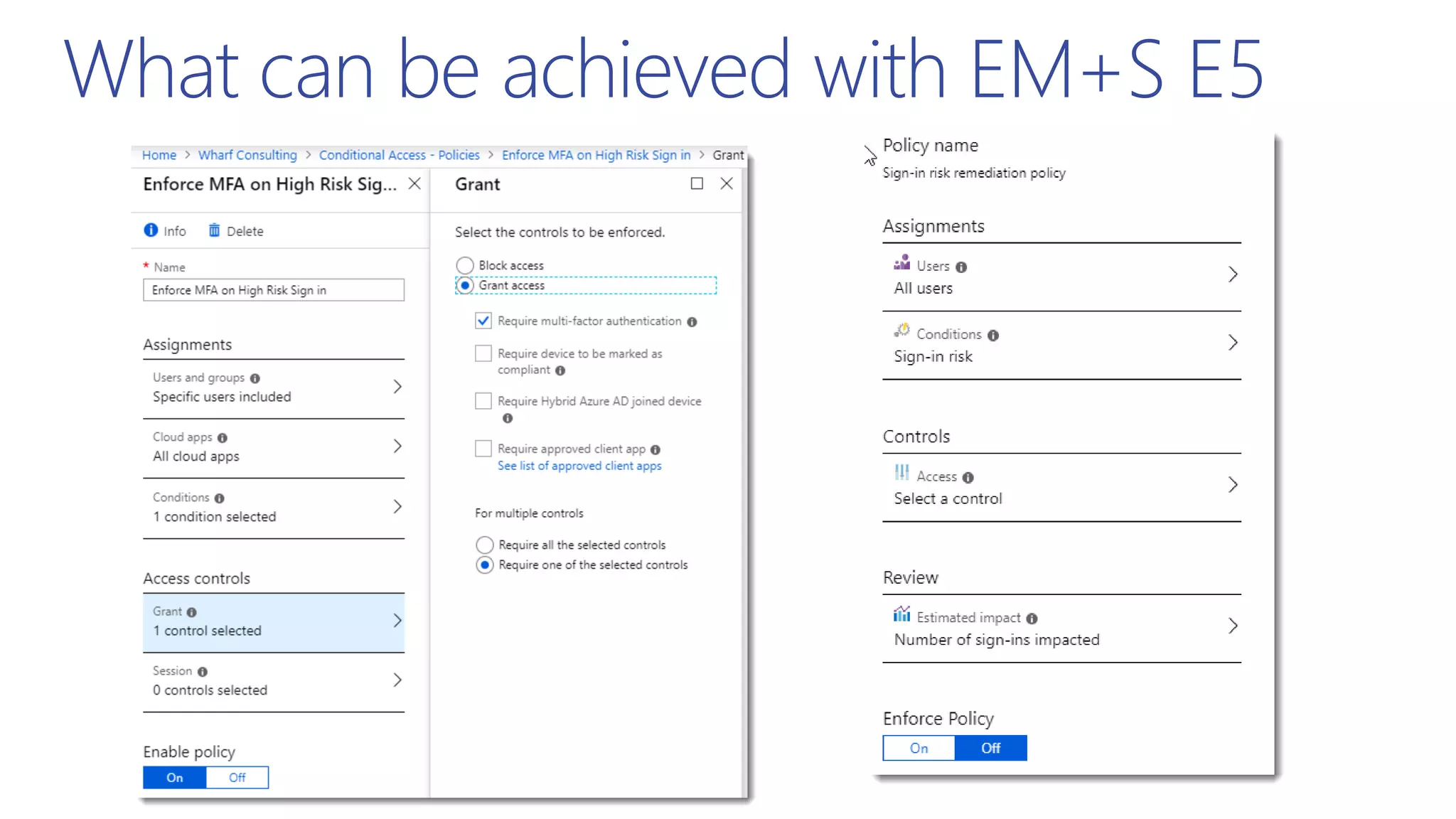
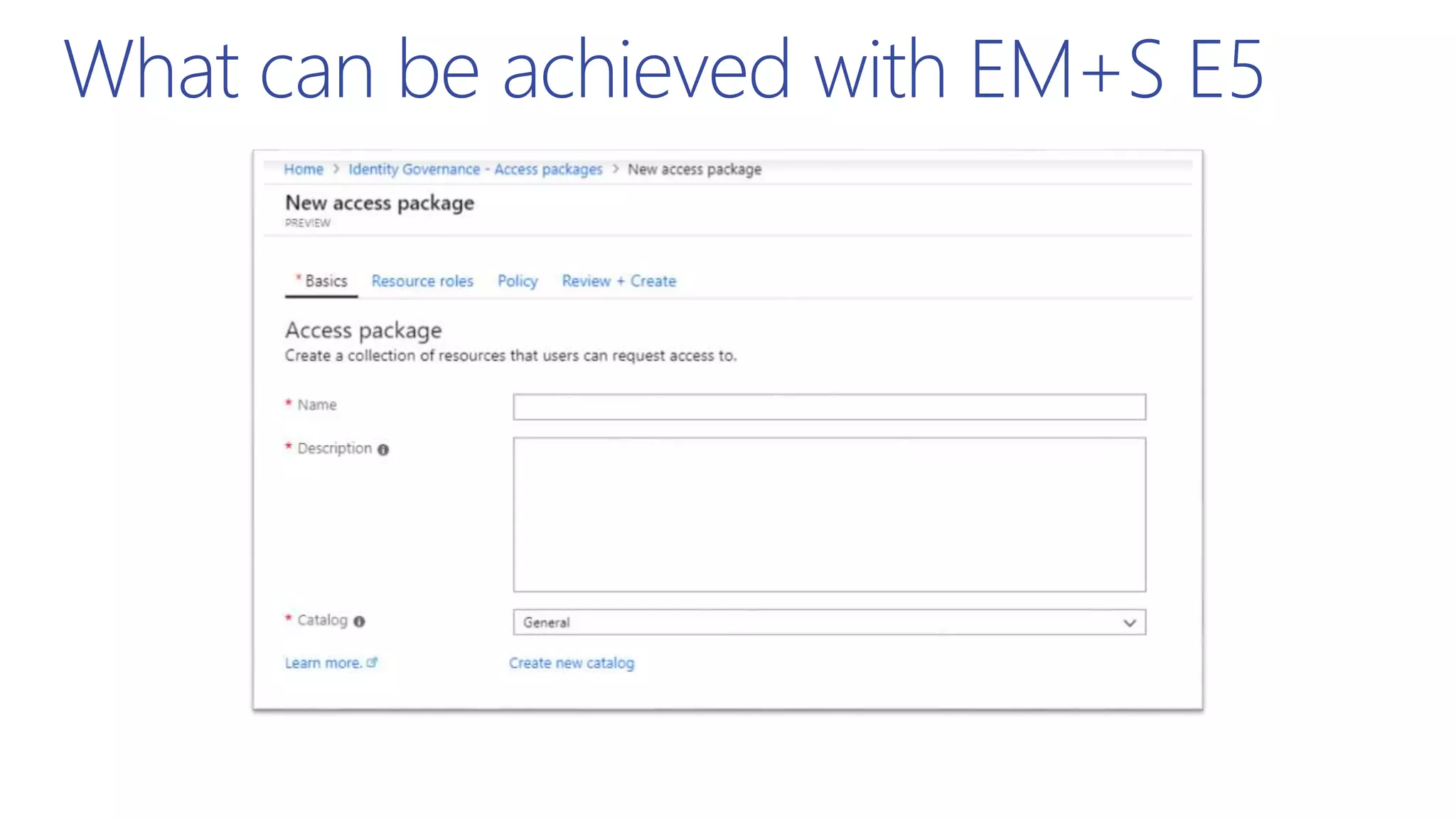
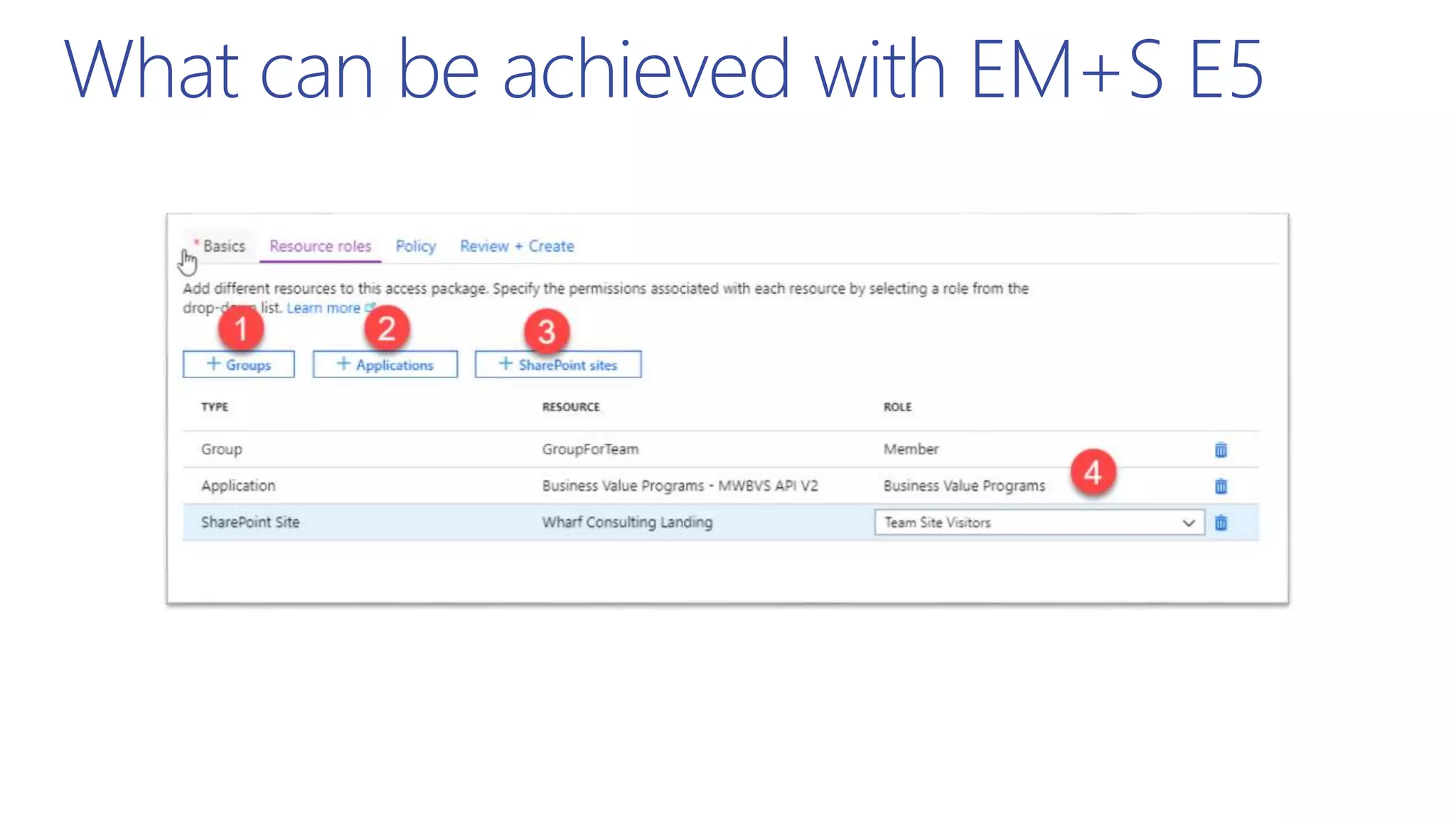
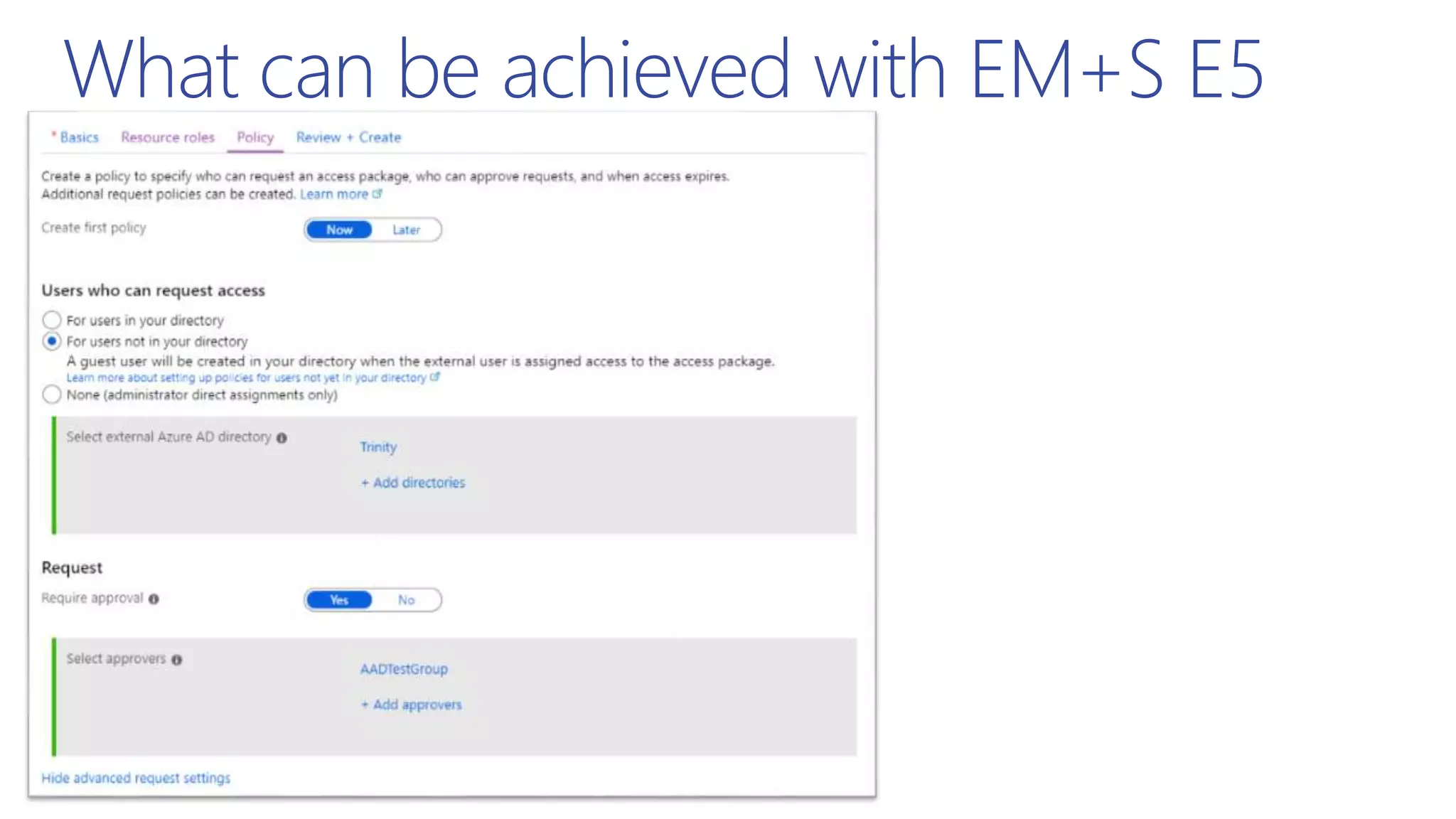
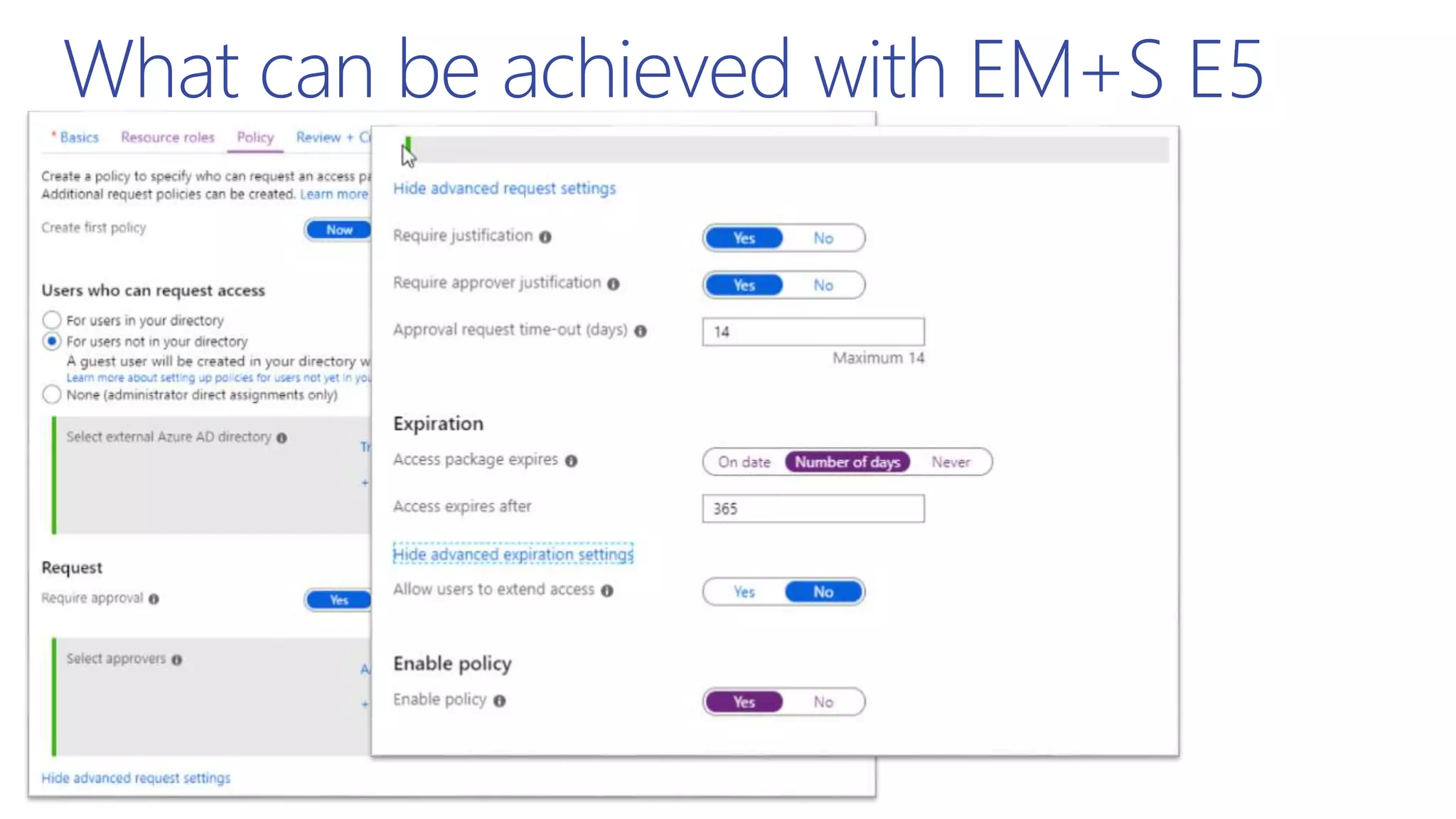
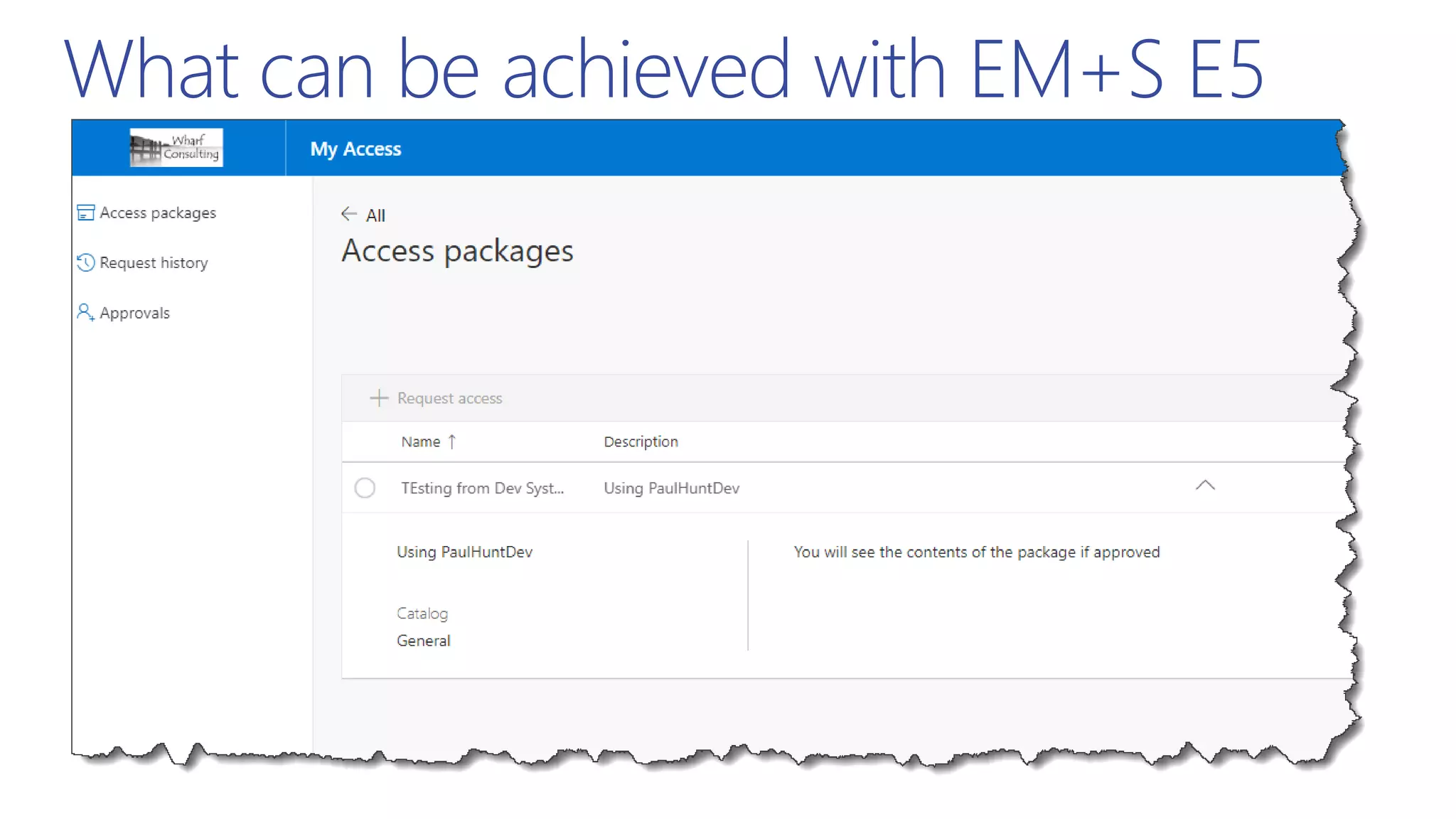
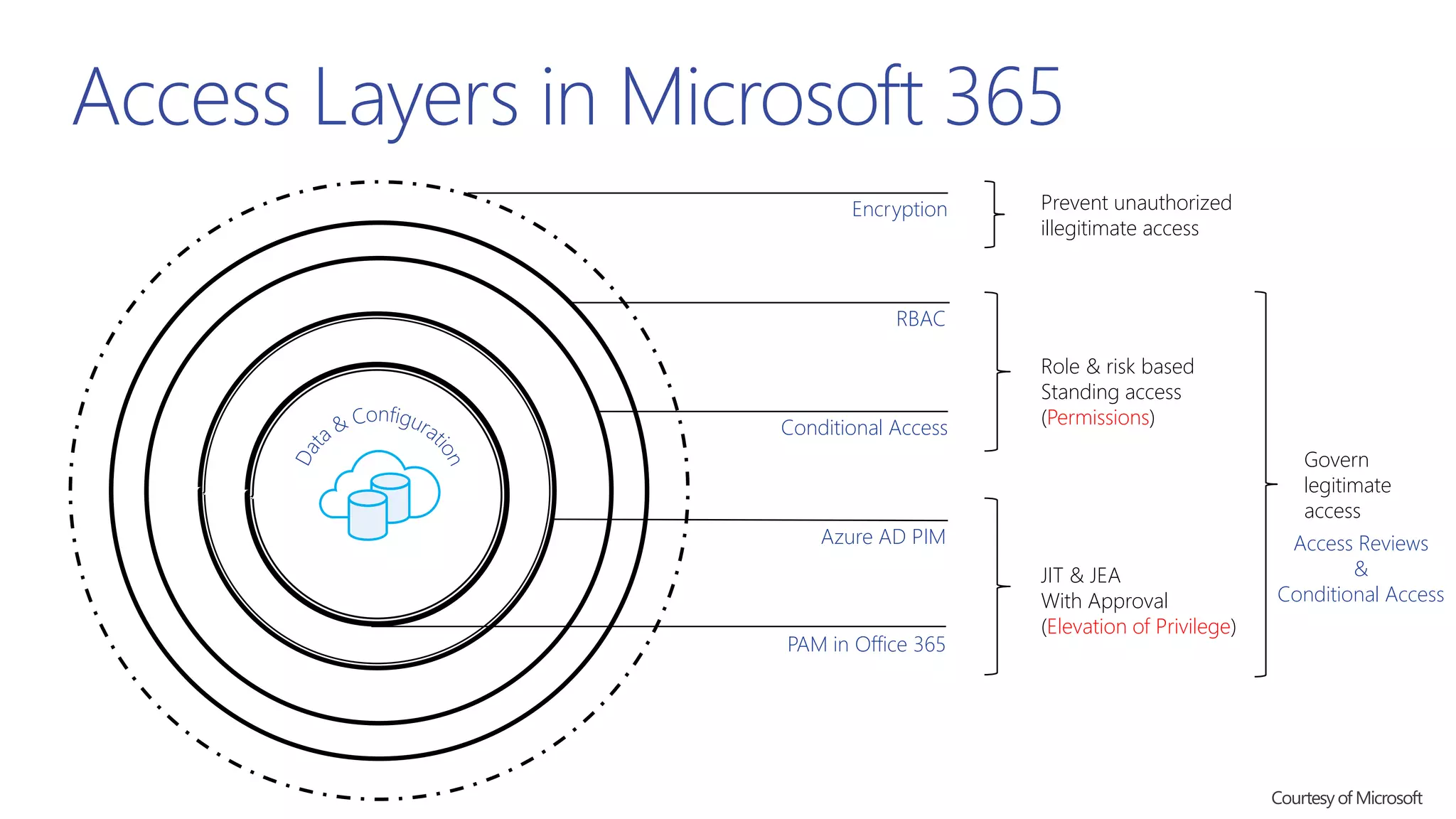
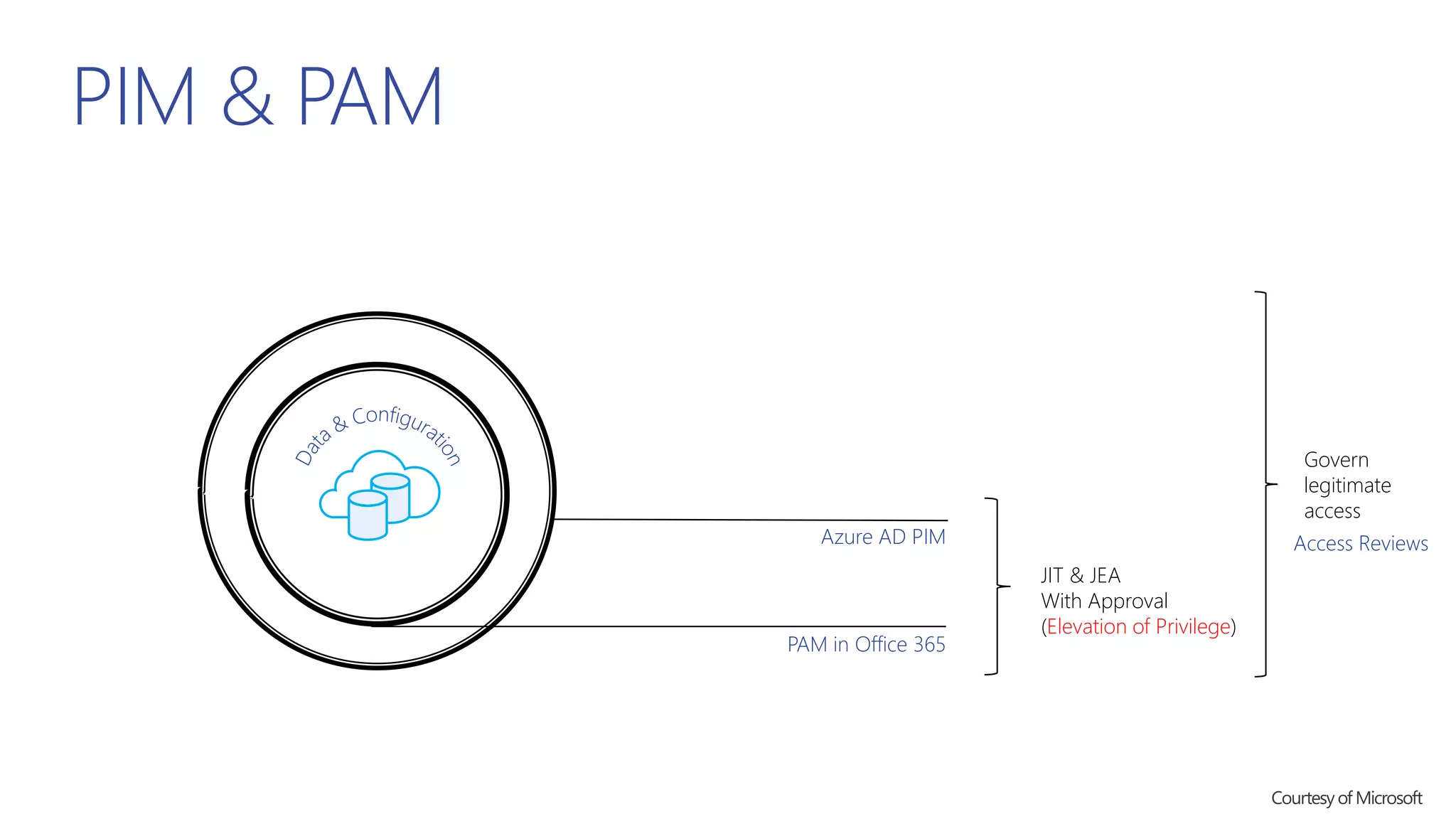
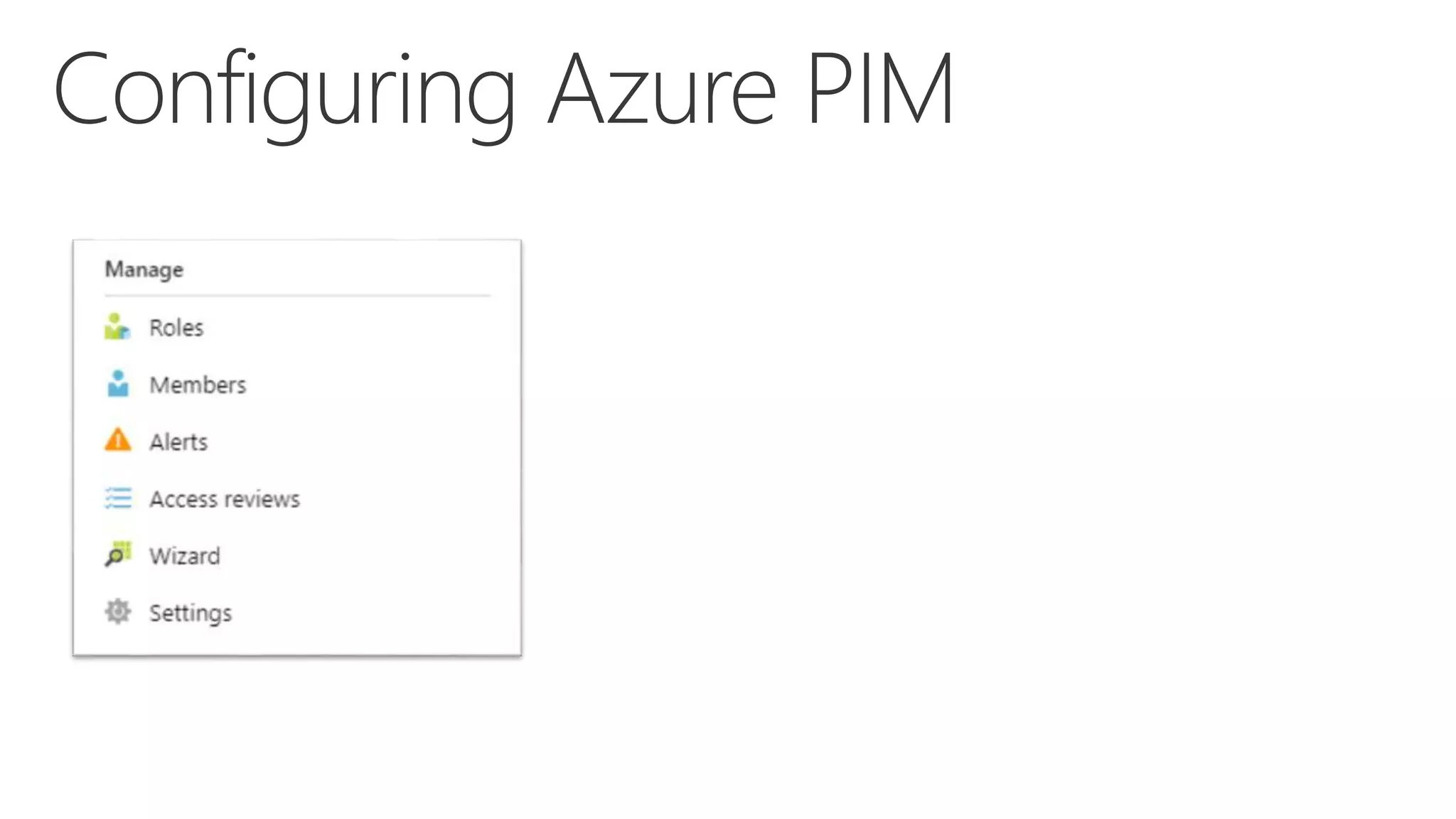
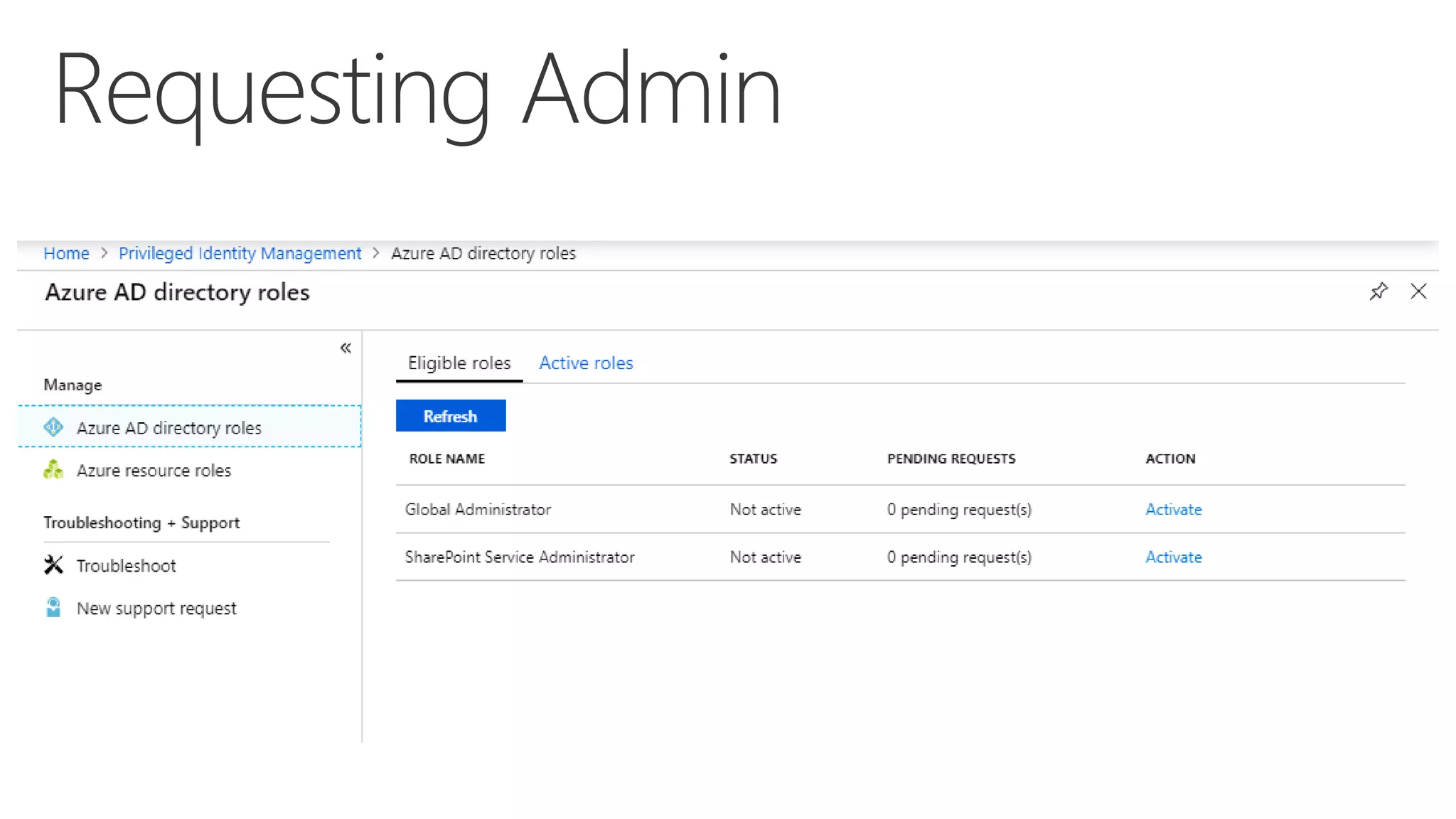
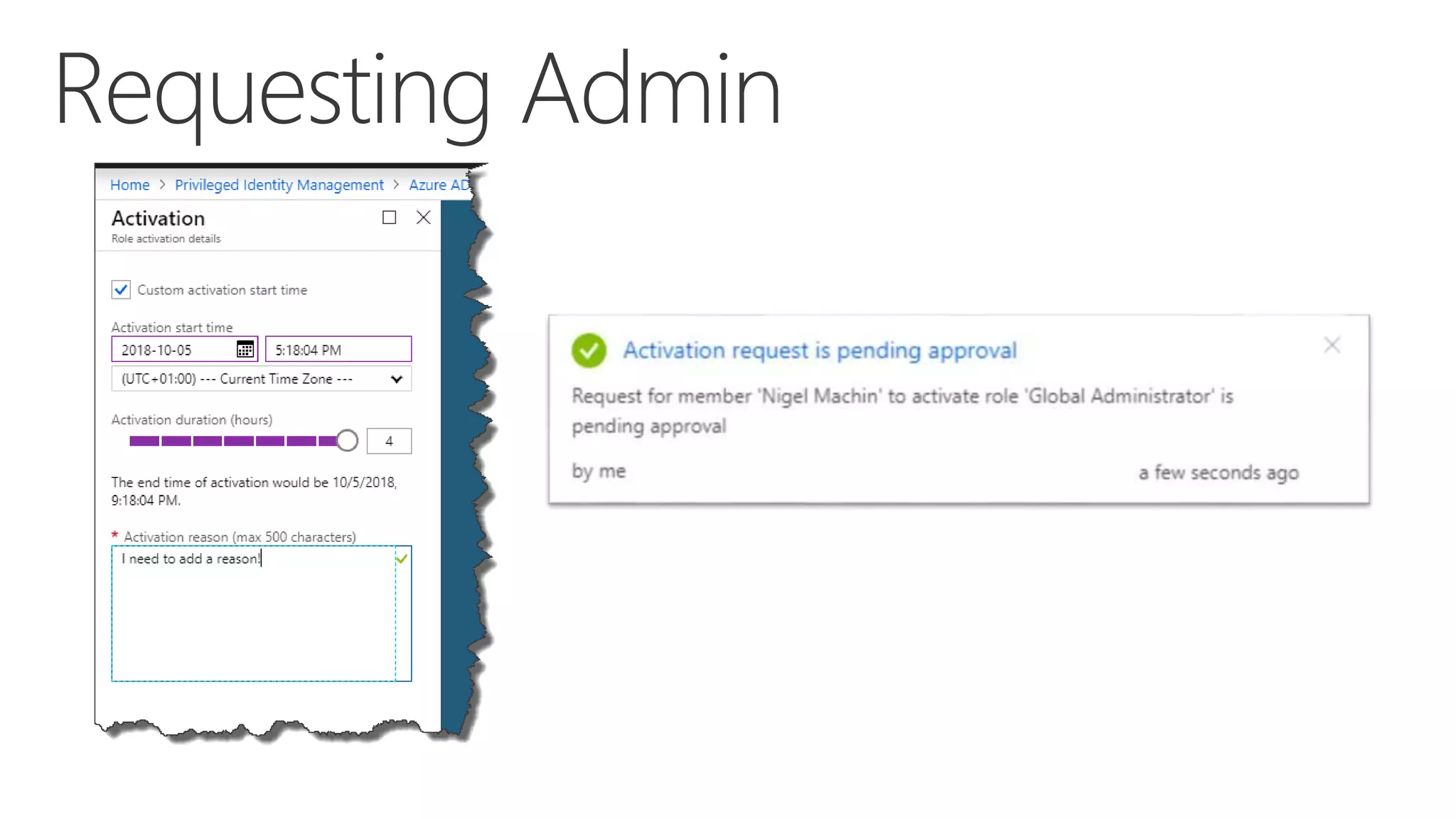
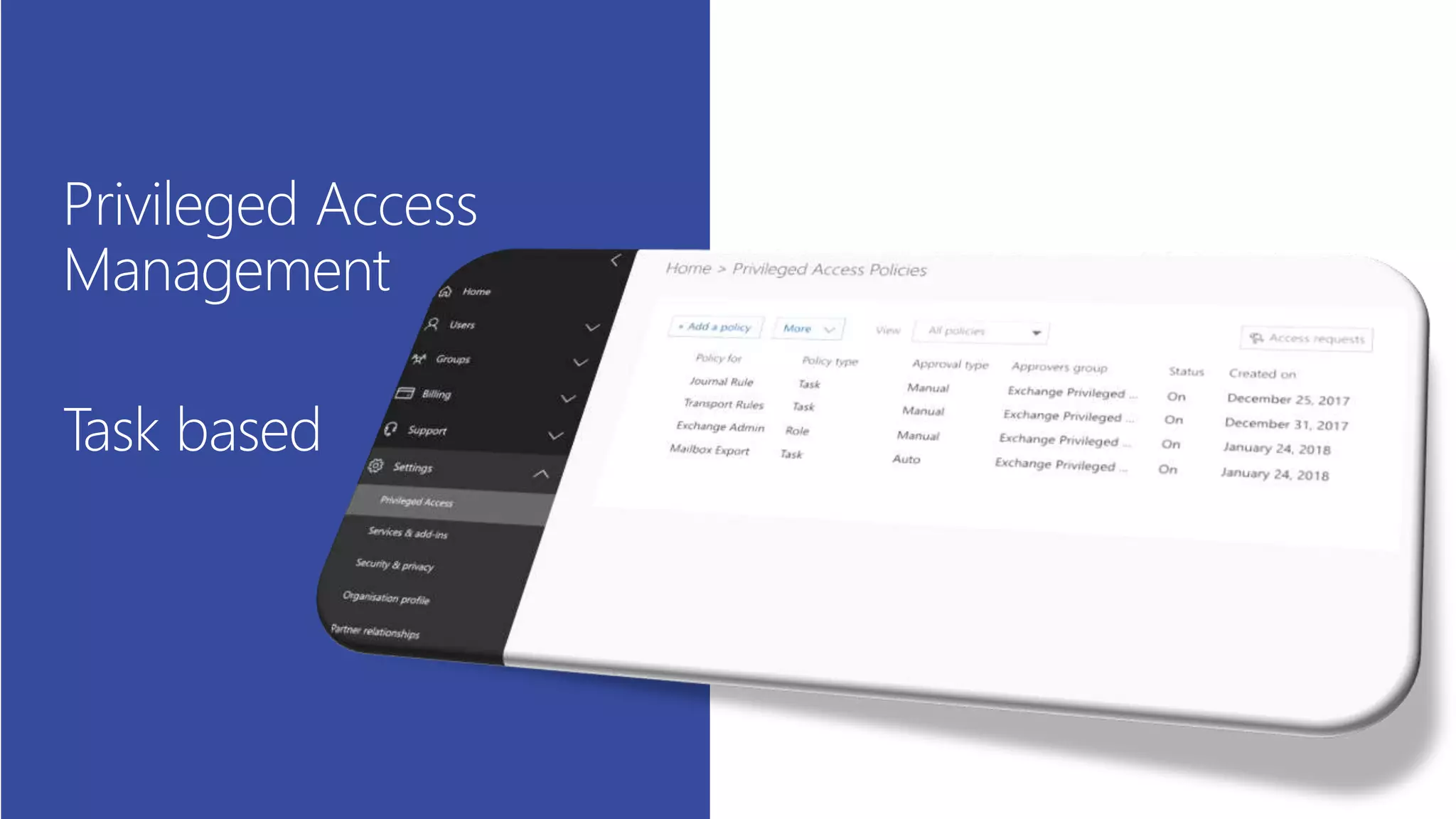
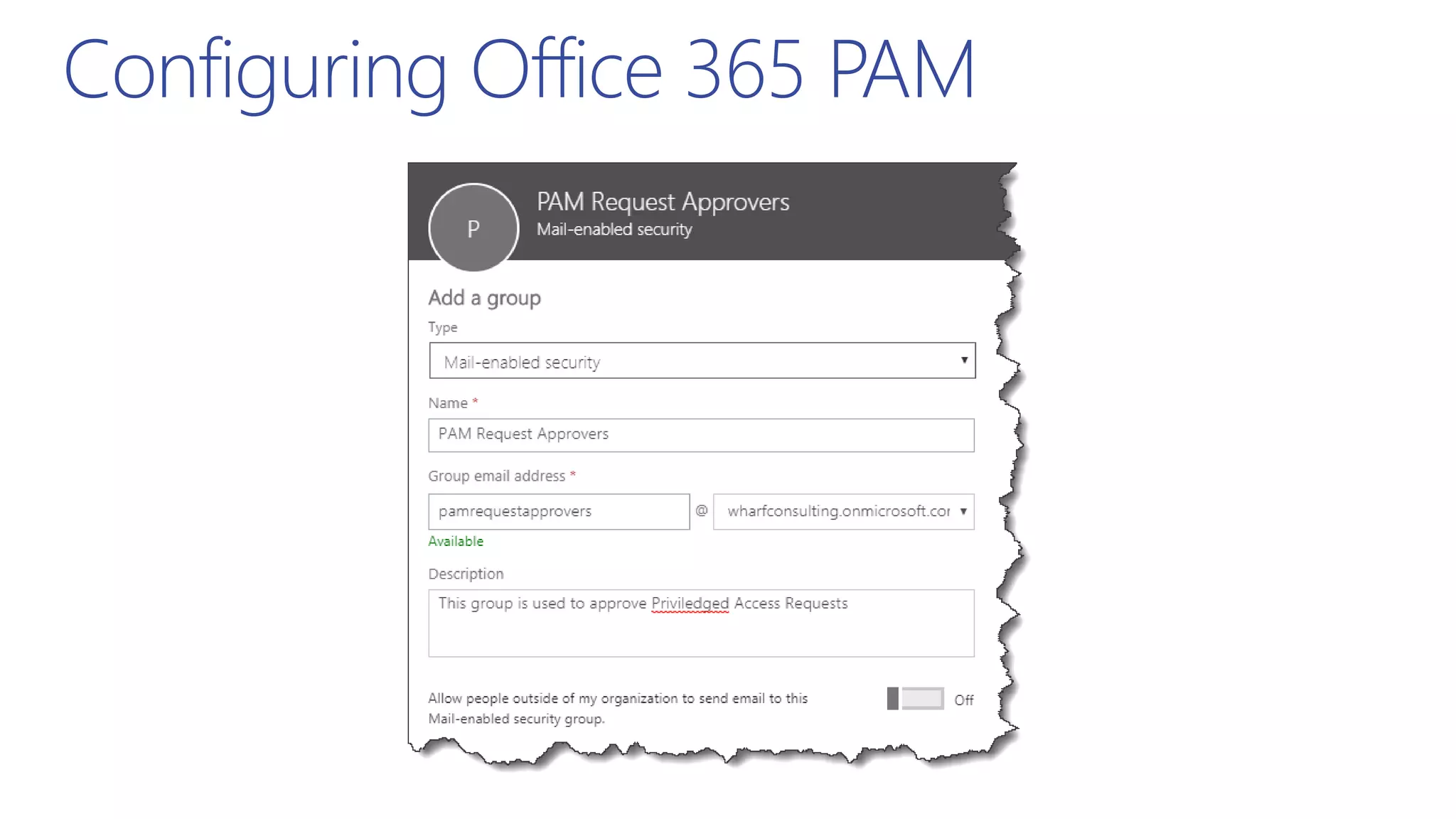
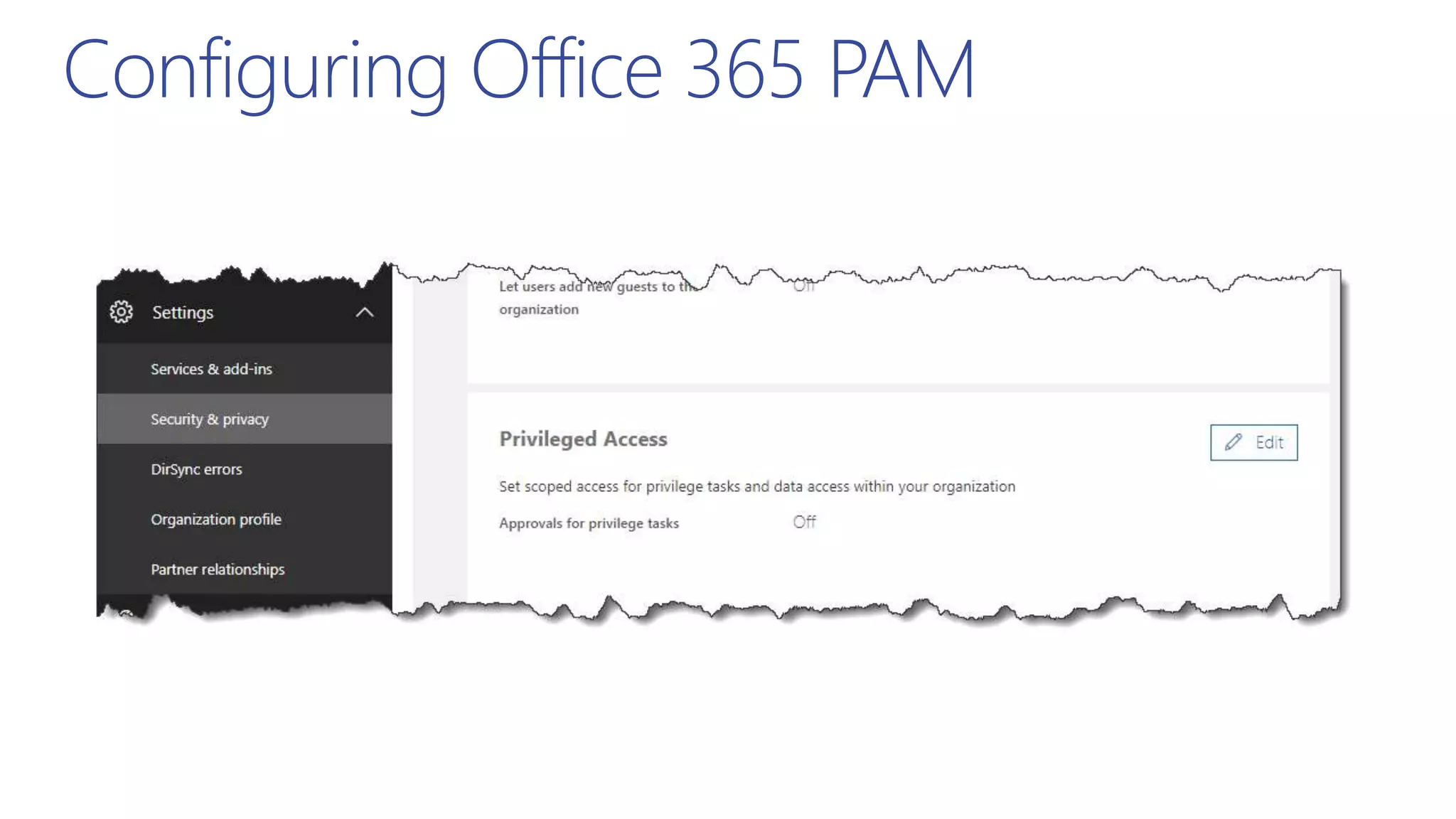
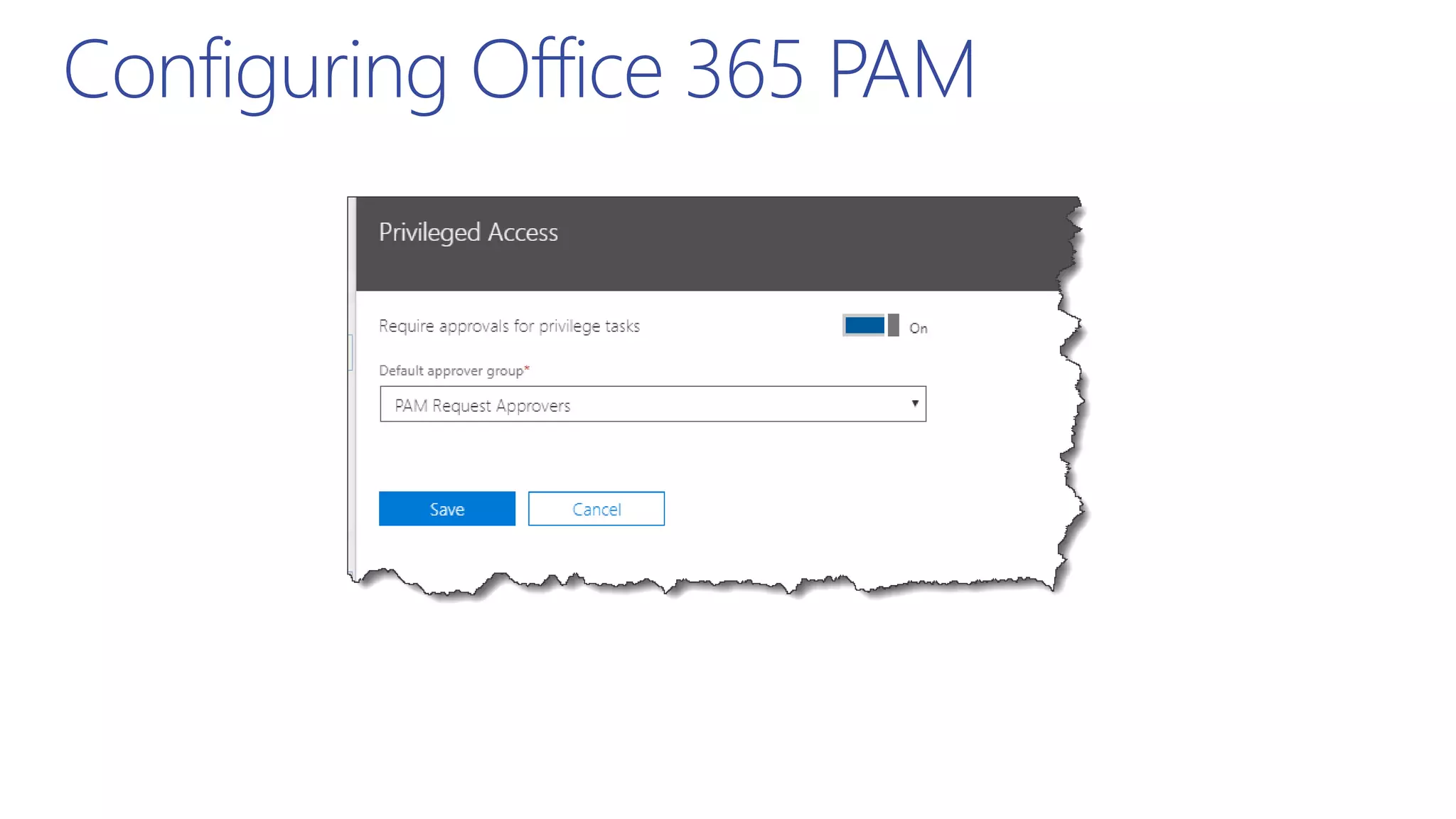
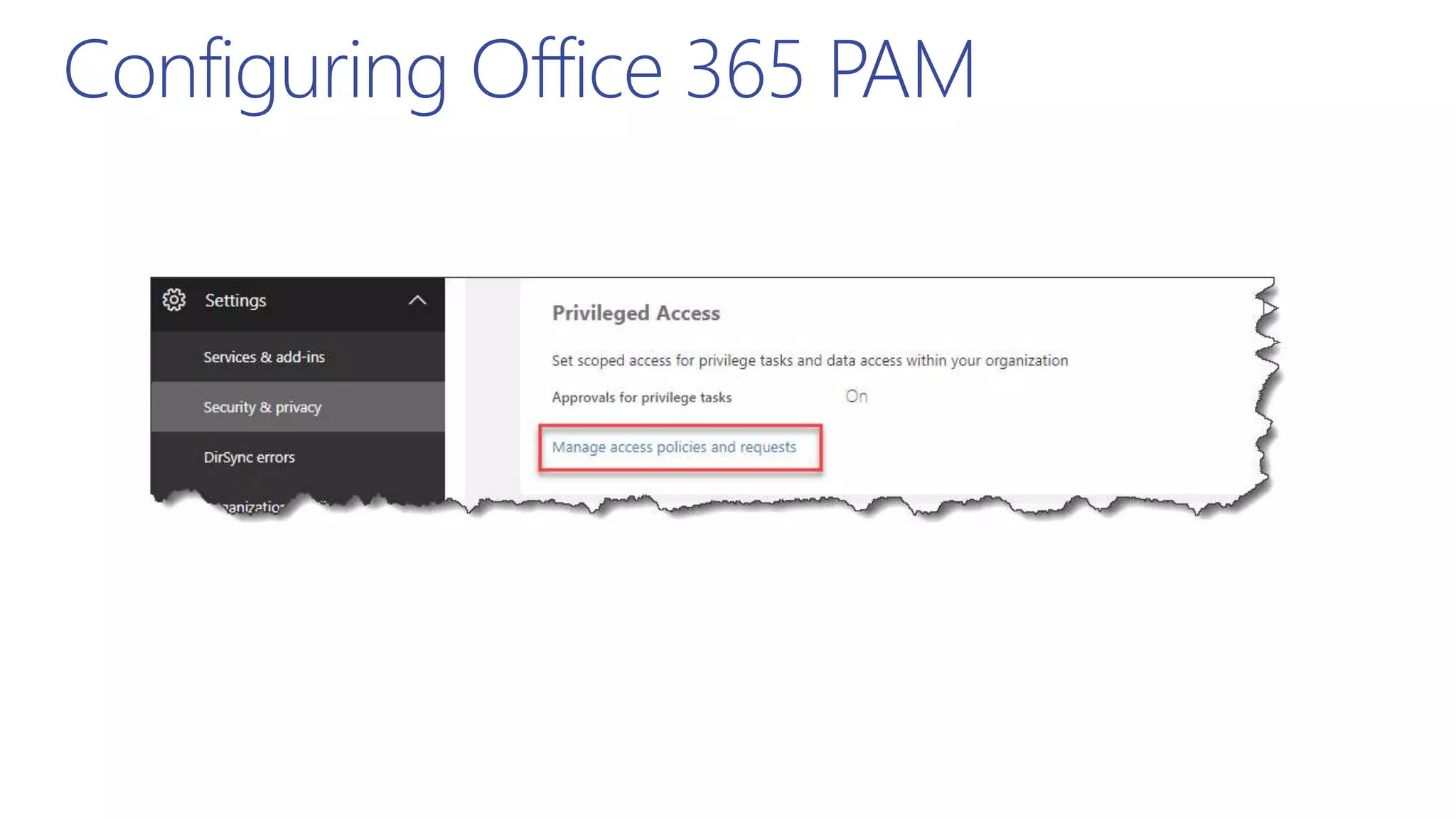
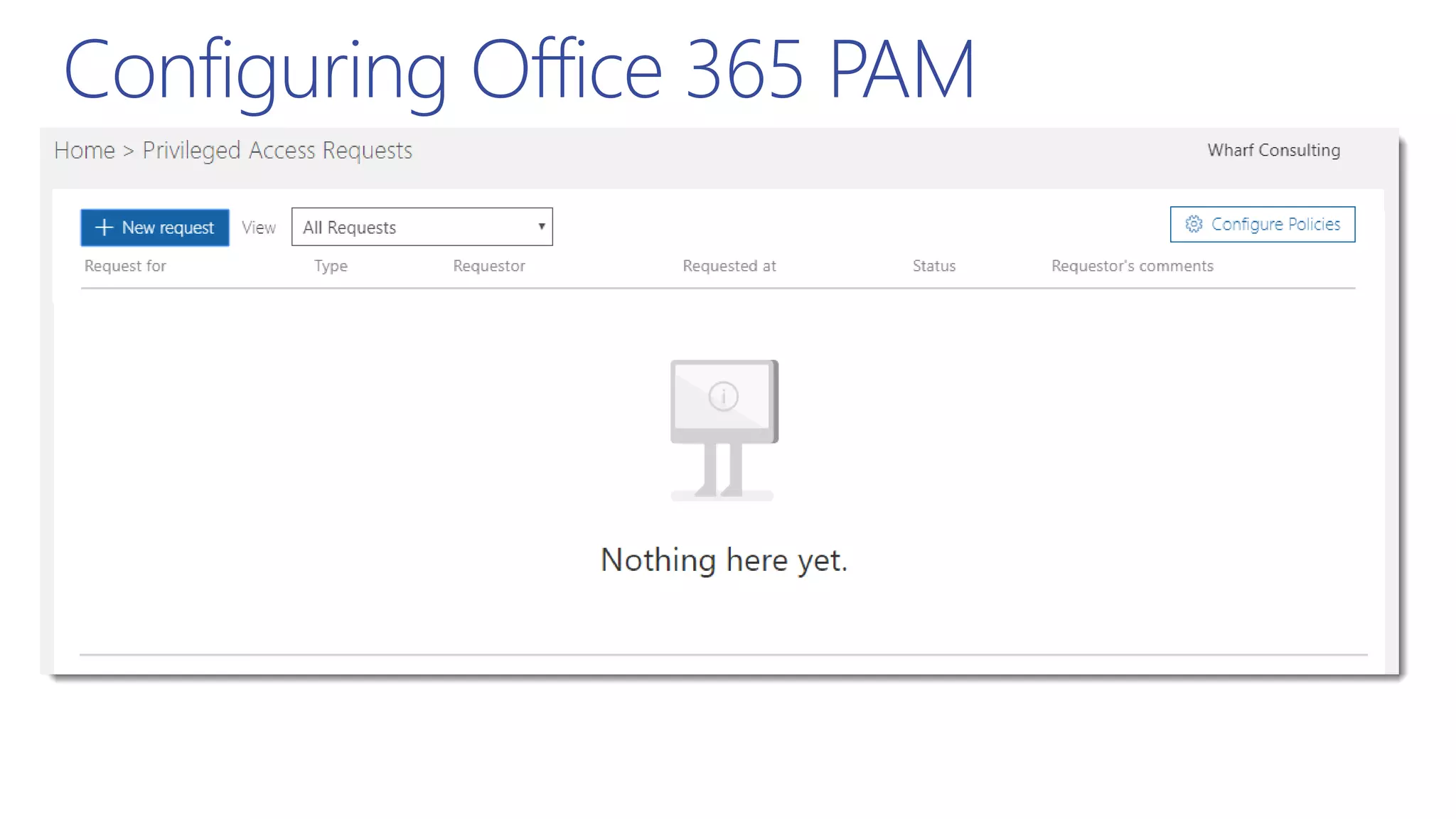
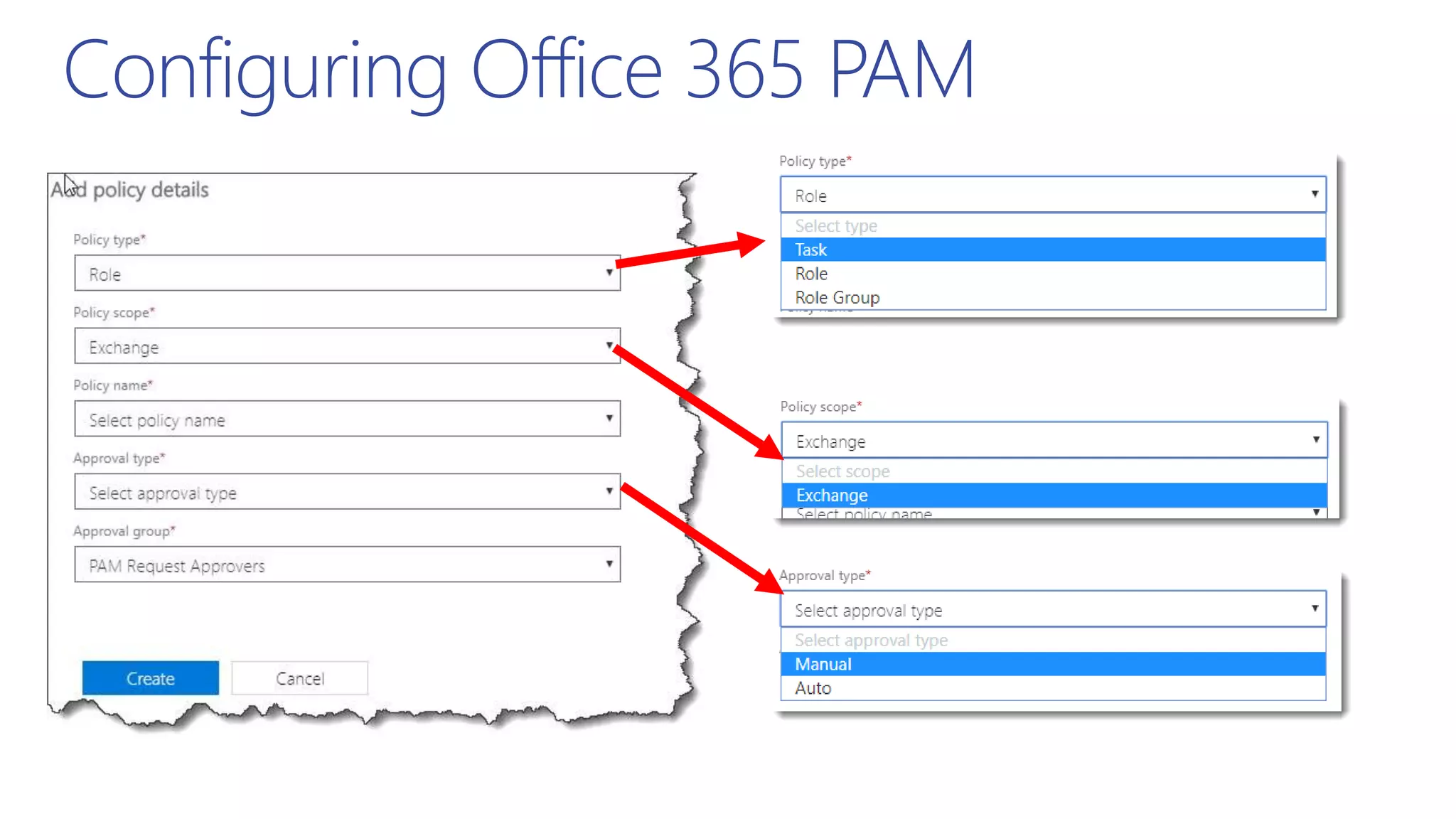
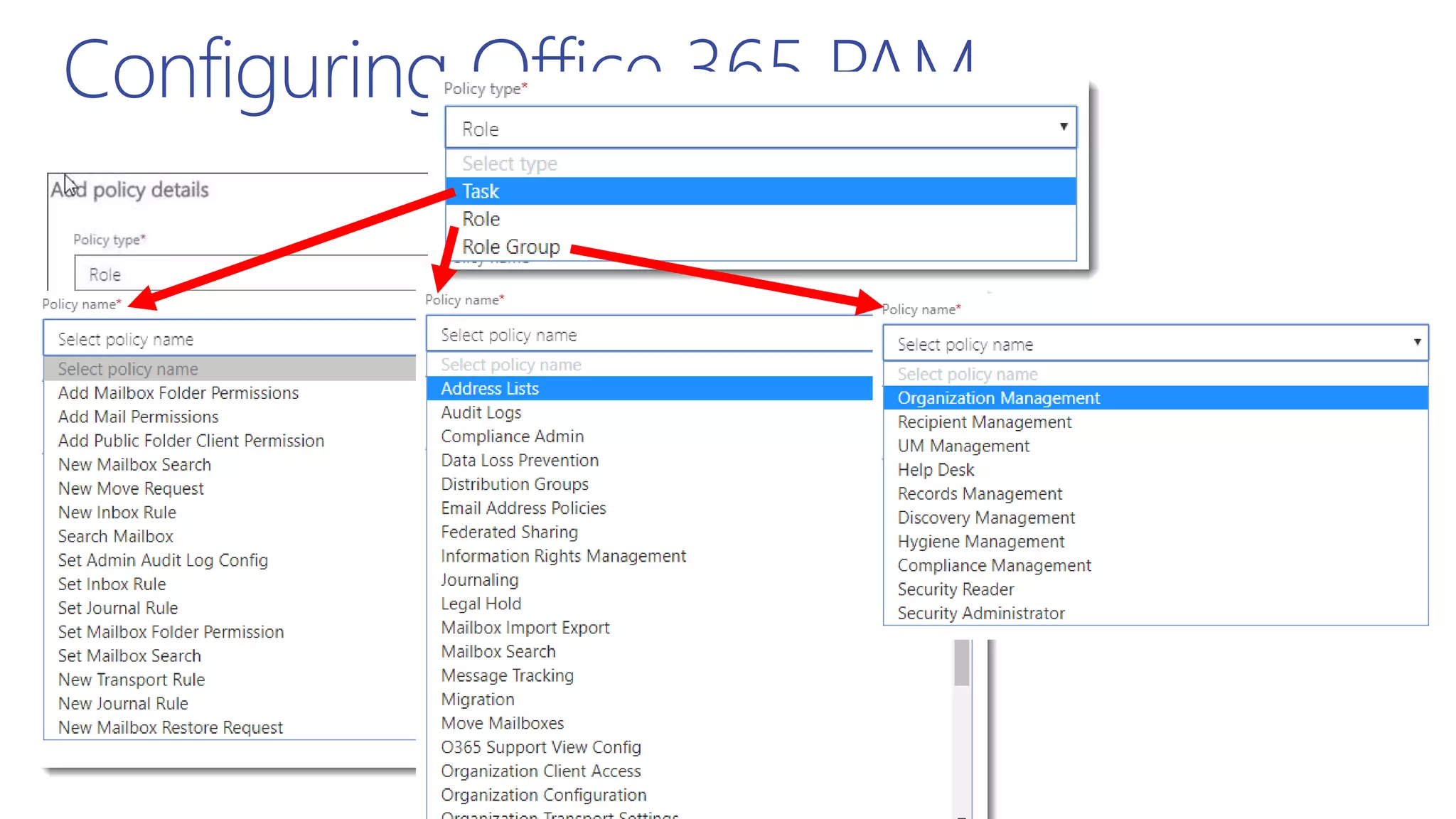
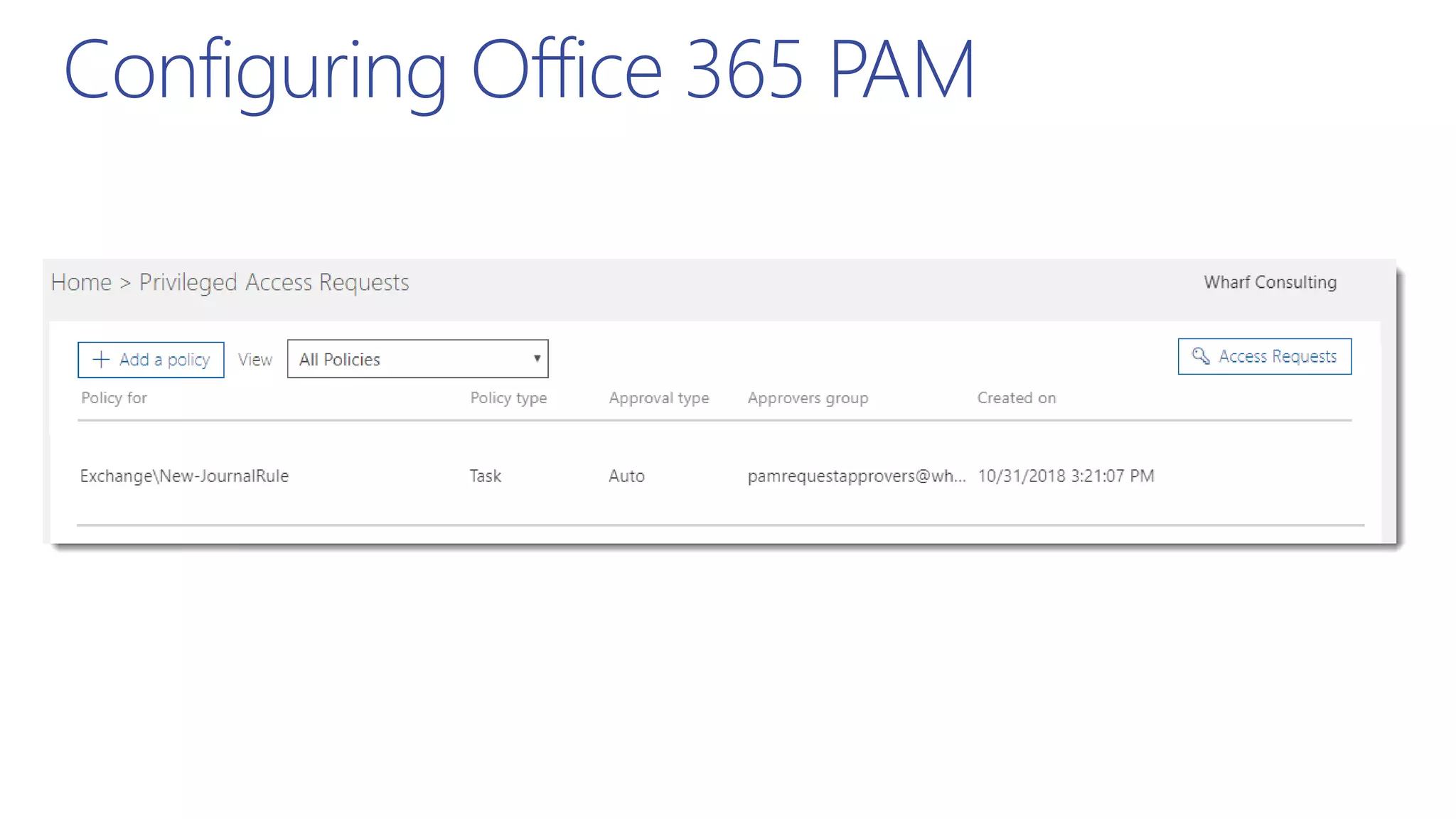
This document summarizes a presentation about exploring conditional access to content in Office 365. It discusses authentication versus authorization, and what conditional access means. It outlines the different access layers in Microsoft 365 including encryption, role-based access control, conditional access, and Azure AD privileged identity management. It compares the capabilities of privileged identity management and privileged access management. Finally, it provides information on configuring privileged access management in Office 365.