Embed presentation
Download to read offline


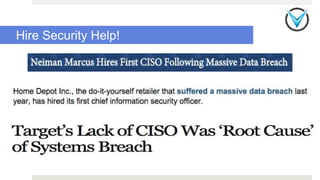
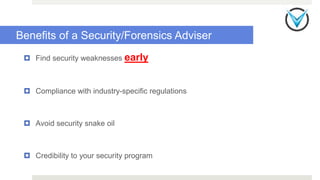



The document discusses essential security measures for startups, emphasizing the importance of proactive security and compliance to protect corporate data from insider threats and breaches. Key recommendations include hiring security experts, encrypting communications, and creating a culture of security awareness among employees. The author also urges better practices in investigations and application designs to prevent security issues.








