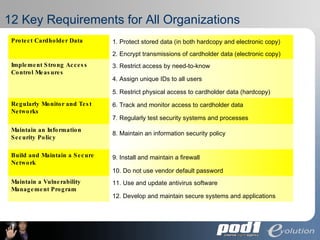
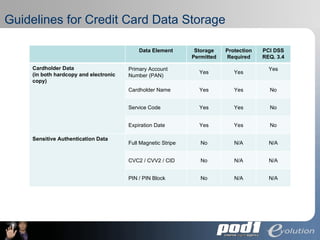
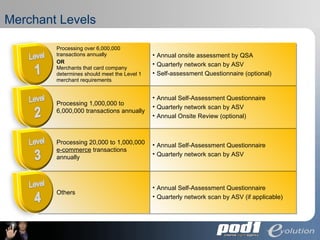
The document discusses PCI Data Security Standards for merchants. It outlines the 12 key requirements of PCI compliance including protecting cardholder data, access controls, monitoring networks, maintaining security policies and vulnerability management. Merchants of different levels have different validation requirements to comply with PCI DSS. Evolution Security Systems provides PCI compliance services like gap analysis, remediation assistance and certification to help merchants achieve and maintain compliance.