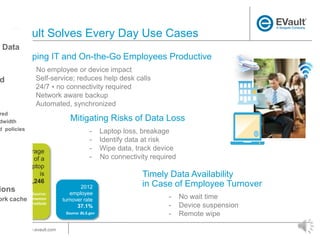
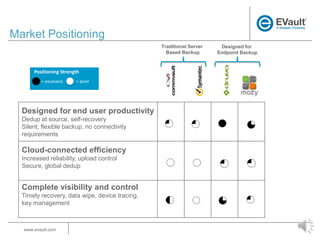
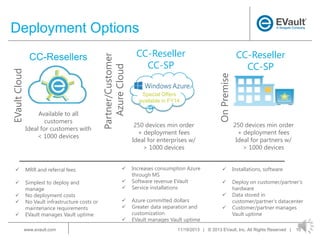
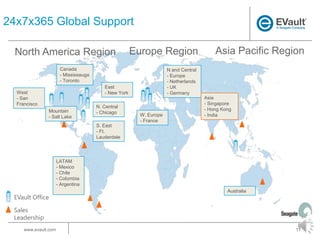
EVault provides endpoint data protection solutions to back up and recover data from laptops. It offers a turnkey, cloud-based backup and recovery solution that protects data on laptops from loss or unavailability. EVault has a global presence with offices worldwide and over 43,000 customers. It supports over 15,000 data recoveries per month and has a 98% customer satisfaction rate.