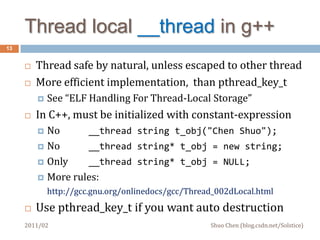
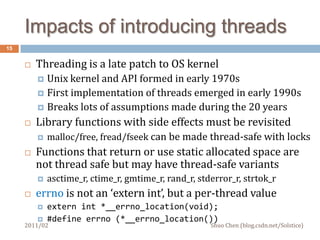
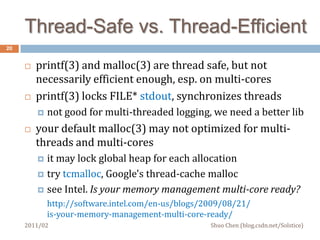
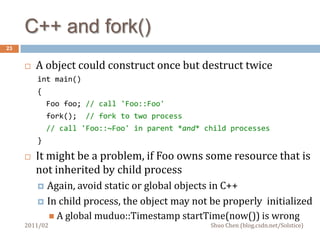
This document discusses challenges in multithreaded system programming in C++. It covers topics such as thread safety of libraries, RAII and fork(), signals and threads, and operating file descriptors in threads. The document is intended for C++ programmers familiar with threads and aims to explain interactions between threads and system calls/libraries to avoid common issues.




![An asynchronous worldNever assume the sequence of events without proper synchronization.Knows happens-before relation, memory visibility, etc.The effect of an interaction between two [thread]s must be independent of the speed at which it is carried out. --- Brinch Hansen 19732011/02Shuo Chen (blog.csdn.net/Solstice)6](https://image.slidesharecdn.com/multithreading-110707080452-phpapp01/85/Essentials-of-Multithreaded-System-Programming-in-C-6-320.jpg)