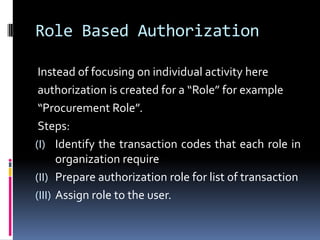
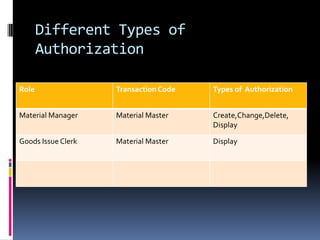
This document discusses managing security in ERP implementations. It identifies several types of ERP security issues, including network security, system access security and role authorization, and data security. It describes strategies for activity-based and role-based authorization in ERP systems. It also discusses data security technologies like data masking, which conceals sensitive data in test environments. Role-based authorization assigns authorization to roles, while activity-based authorization assigns transaction code sets. Data masking algorithms like shuffling, hashing and substitution can enhance data security.