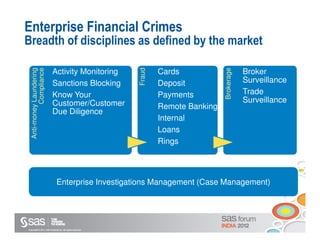
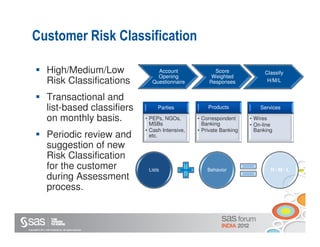
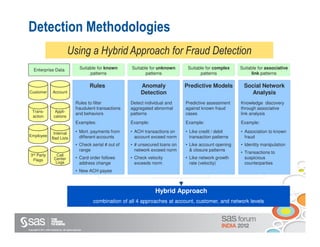
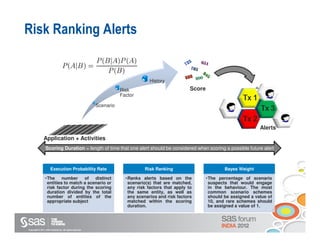
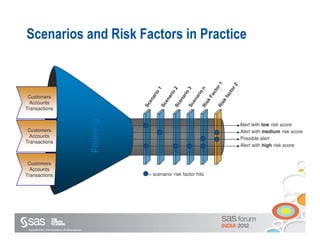
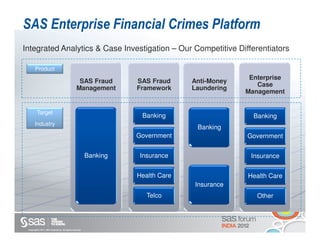
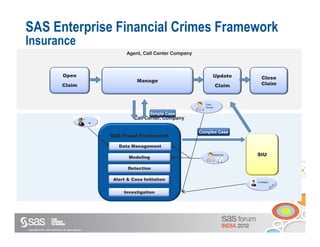
The document discusses enterprise fraud management and the importance of detecting fraud early through various methodologies, including transaction monitoring and alert management. It highlights top fraud types and outlines strategies for effective fraud detection and prevention, emphasizing data quality and integrated analytics. Additionally, it touches on the need for banks to have well-publicized whistle-blowing mechanisms and sophisticated technology to manage financial crimes.